Creating an Incident Response Plan
Previously, when cybersecurity incidents were relatively rare, the response was seen as a separate set of activities treated by a separate team. However, this model no longer reflects the current cybersecurity landscape. Today, incidents occur more frequently, cause far more damage, and recovery takes weeks or even months. Hence, incident response should be seen as a continuous cybersecurity risk management process integrated across organizational operations, people, and processes.
The latest iteration of NIST SP 800-61, rv. 3 identifies six steps of an effective incident response plan. These steps include Govern, Identify, Protect, Detect, Respond, and Recover. The NIST incident response plan is distinguished by its structured approach, emphasizing preparedness, risk management integration, thorough documentation, and continuous improvement.
SANS Institute also outlines six incident response steps. These include Preparation, Identification, Containment, Eradication, Recovery, and Lessons Learned. The incident response plan template reflects the common guidelines that would help to arrange a living and effective incident response plan. Yet, an effective incident response plan should also reflect the organization’s unique environments and technological capabilities.
Relying on the widely recognized standards and best practices, we offer a step-by-step guide on how to create an effective incident response plan:
- Define your legal frames. Identify the key incident response guidelines required by relevant laws, regulations, and standards such as NIST, HIPAA, and PCI DSS. These guidelines highlight essential business requirements like response times and recovery strategies, forming the foundation for your incident response planning.
- Perform a security risk assessment to pinpoint and address immediate vulnerabilities in your security framework.
- Establish your incident response team and their roles and detailed responsibilities at all stages of incident response.
- Define what a security incident is. Clearly define what events are considered security incidents, their severity, etc. For example, a single non-functional workstation can be viewed as a minor security incident, whereas sensitive customers’ data being stolen is definitely a high-priority incident.
- Implement security monitoring tools and systems. Evidence of incidents can come from log files, error messages, or intrusion detection systems. These tools may reveal abnormal network traffic from specific hosts, unexpected entries in system logs, etc.
- Establish short-term and long-term containment measures. Short-term measures, like disconnecting affected systems or powering down routers, would limit the damage as soon as possible and limit the incident before it gets worse. The long-term measures, in turn, would allow organizational operations to continue. These include removing accounts and/or backdoors left by attackers on affected systems, installing security patches, and doing other work to limit any further escalation.
- Establish a clear incident communication procedure so the key staff, like management or system administrators, have enough time to gather evidence and prepare for the next steps. For example, users may be required to call the help desk to report unusual behavior on their system. Establish a list of authorities to whom you need to report incidents in your organization.
- Establish documenting procedures so the responders can document everything that they are doing and be able to answer Who, What, Where, Why, and How questions. E.g. take a forensic image of the affected system(s) during the incident to preserve evidence, document users’ step-by-step activities, etc.
- Prepare recovery strategies for different situations. These may include implementing regular backups of all critical data ensuring that backups are stored securely and separate from the primary network. Setting targets for how quickly key systems and data must be restored after an incident is also necessary. For example, determine how much downtime is acceptable before operations must be back online to avoid significant impact.
- Refine your incident response plan using insights from past incidents. After managing an incident, review it thoroughly to enhance your IRP with better strategies, procedures, and scenarios.
Automating your Incident Response Plan
Incident response automation significantly enhances an organization’s ability to respond swiftly and efficiently to cybersecurity threats. Automated systems can quickly analyze incoming data, identify anomalies, and trigger predefined responses, such as isolating compromised systems or blocking malicious IP addresses, without the need for manual intervention. This allows security teams to focus on higher-level analysis and strategy development rather than being bogged down by routine tasks.

There is a striking correlation between data breach cost and the use of automation tools. In fact, the more organizations use automation, the lower their average breach costs. The average data breach cost for organizations without automation is $1.88 million higher compared to those leveraging automation tools.
Furthermore, automation ensures consistency in response efforts, applying the same procedures each time an incident occurs. This not only improves the effectiveness of the response but also helps in compliance with regulatory requirements by maintaining detailed logs of actions taken during incidents. Using automation in incident response planning is an incoming trend. Threat detection and response technologies, along with IR planning, are the 2 most popular areas of security investment. The focus of the top 2 investment areas was on detecting suspicious incidents and threats and responding to them more quickly.
How SpinOne helps
Looking for automated tools to reinforce your incident response plan activities?
Try SpinOne – an all-in-one SaaS security platform that enhances organizations’ incident response planning by streamlining data protection and recovery processes. The core functions of SpinOne include:
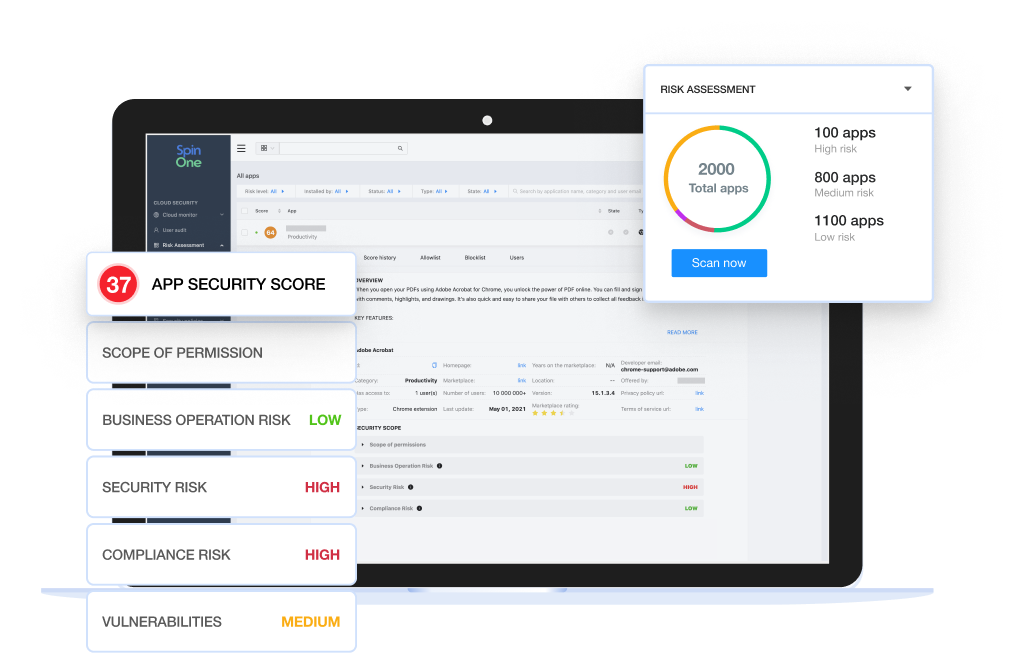
Identify risky extensions and applications
- Inventory and gain visibility of all SaaS apps and browser extensions that have access to your critical SaaS data
- Leverage 24/7 continuous monitoring and ongoing risk assessment to get complete visibility into potential business, security, and compliance risks of each application and browser extension
Protect your SaaS environment
- Allowlist or blocklist risky applications or browser extensions to prevent unauthorized access
- Identify and manage misconfigurations, security drifts, and compliance breaches within your SaaS applications through automated detection and response.
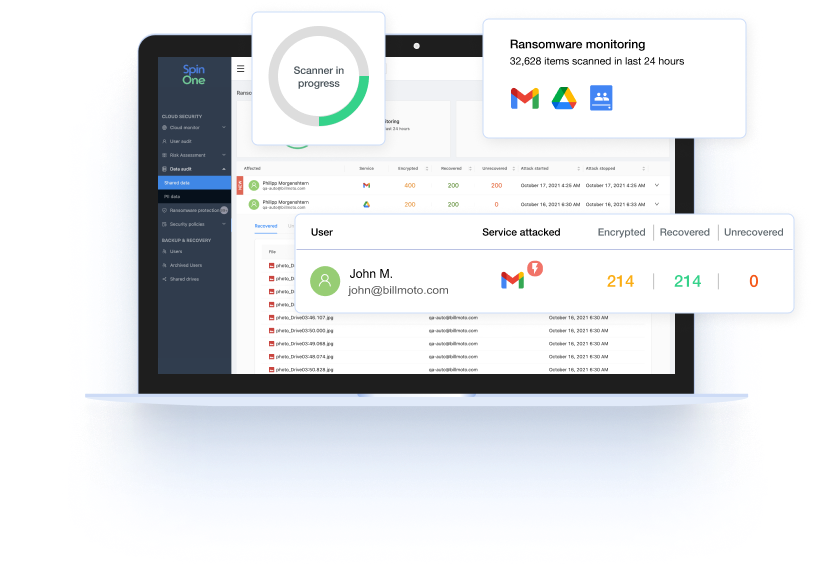
Respond to threats in real time
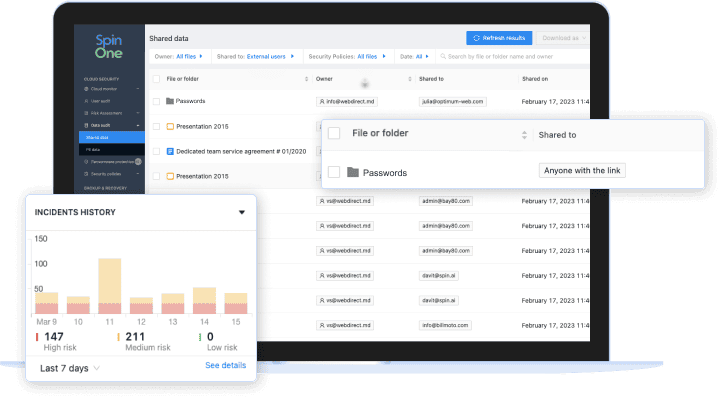
- Get complete visibility on data exposure by monitoring files shared outside or inside your organization – and change access and ownership of files through automated policies.
- Stop an attack in progress – SpinOne blocks the source of a ransomware attack by revoking API access to the malicious application, immediately stopping the spread and reducing the impact of a cyberattack.
Recover critical data immediately
- Meet your RTO and reduce potential business downtime from 21 days to 2 hours.
- With Spinbackup’s automated, 1x, or 3x daily backups, you can ensure all your data is quickly and accurately recovered.
To learn more about fortifying your Incident Response Plan with SpinOne, try it free for 15 days.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...