Data Loss Prevention: What Is DLP and Why Is It Important?
The world has become inseparately reliant on digital tools to help run daily business operations, making cyberattacks and data leaks a lucrative and disruptive threat to your business.
Attacks and data losses have gotten so bad that 98% of organizations are partnered with at least one third-party vendor that has suffered a data breach in the last two years, and cyberattacks using stolen or compromised credentials have increased 71% year-over-year since 2023.
With these hard truths in mind, a reliable data loss prevention (DLP) strategy should be an integral part of any business aiming to safeguard their and their client’s intellectual property and confidential information while complying with industry data protection regulations.
Cyberattacks, data breaches, or even accidental exposures can result in massive financial losses, reputational damage, legal repercussions, and operational disruptions that can put your clients and bottom line in serious peril. And the more sophisticated these threats become, the greater the risks will be to your organization.
But with the modern DLP strategies we will discuss below, you can help your organization mitigate these risks, protect critical information, and maintain business continuity.
What is Data Loss Prevention (DLP)?
Data loss prevention (DLP) refers to tools and techniques used to prevent a business’s and its client’s sensitive data from being leaked, misused, or lost during a cyber attack or accidental exposure.
An effective DLP strategy will monitor data (manually or, ideally, automatically through a DLP solution) at multiple levels, including endpoints, networks, and cloud storage, to ensure that data is not accidentally or intentionally exposed to unauthorized parties.
DLP strategies can address a range of concerns, from accidental data exposure to cyberattacks and internal threats. Today’s IT landscape is complex, internal and external threats are ever-present and constantly evolving, so DLP tools must be versatile and thorough enough to provide the necessary level of protection to keep your data safe.
How Does DLP Work?
The most successful Data loss prevention strategies will utilize several layers of security to protect your critical data – combining user activity monitoring, encryption, and access control mechanisms.
Automated DLP solutions, usually provided by a third-party vendor, use predefined policies established by the user to track and detect sensitive information. They are typically far more secure than manually tracking data across environments and devices and will automatically enforce rules that prevent unauthorized access, sharing, or transfer of data.
These solutions operate across three main areas, data in use (data an employee is working with), data in motion (data that is being shared across networks), and data at rest (data stored on devices and servers).
A DLP solution inspects all this data in real-time, checking for keywords and items that signal sensitive information (like social security numbers) and then either encrypting or restricting access based on the user’s criteria. It will also monitor for unusual activity, like large data downloads of confidential material, and take preventive action. It will then create an IT ticket to log for further investigation.
These preventive measures, and automated reactions, come together to create a robust automated security system that ensures the safe storage of your critical data.
Types of Data Threats in DLP
There are various types of data threats that organizations need to defend against when it comes to DLP. These threats may originate from either a deliberate attack on your network by either internal or external players, or through an accidental leakage through personal devices or improper procedure. Below we have listed out some of the most common data breach threats to keep an eye out for: :
Accidental Data Exposure: It is possible that employees will unintentionally share or upload sensitive information to an unsecured platform, putting it at risk for a data breach. This can happen if an employee sends confidential information to the wrong email address, or uploads it to an unencrypted server.
Malicious Insider Threats: Employees or contractors who have access to sensitive data may intentionally leak or misuse it for personal gain or malicious reasons, possibly as retaliation or for a bribe they were offered. They may then download data to their personal device to share it publicly, potentially harming the business’s reputation and finances.
External Attacks (Cyberattacks): Hackers commonly use techniques like phishing, malware, or ransomware to steal sensitive data. Phishing emails, for example, may mislead an employee to provide login credentials to someone outside the company.
Unauthorized Data Sharing: Employees may share sensitive data with third parties without following security protocols or procedures. Sharing sensitive data without encryption with a third-party vendor is one way you can be put at risk for a data leak.
Data Leakage via Cloud Applications: Misconfigurations in cloud services can also expose sensitive data to unauthorized or unwanted users. A misconfigured cloud storage bucket that allows public access to confidential files, for example, would leave you open to a security breach.
Mobile Device and BYOD Risks: Unsecured personal devices used for work are a common oversight that can lead to data loss or exposure. It can be very easy for employers to misplace company phones and laptops that contain sensitive information and are not properly secure, or to store data on a personal device outside the company’s network. Theft and loss can then lead to a significant loss of sensitive data with very little effort.
Weak Authentication and Access Control: And simply having poor access controls or weak authentication can allow unauthorized individuals to access sensitive data. If your company has easy-to-predict or common passwords, you may be at risk of a data breach.
DLP solutions that monitor, detect, and mitigate these types of threats by enforcing data security policies are irreplaceable tools when it comes to securing your data. Automation allows you to effortlessly discover your security holes and track unusual behavior, allowing you to prevent your breaches before they happen.
5 Reasons Your Enterprise Needs Data Loss Prevention
Data loss is inevitable. People make mistakes, applications malfunction, and cybercriminals are constantly looking for vulnerabilities in the security perimeter of businesses. This can lead to multiple negative implications and risky situations for a company, but efficient data loss prevention software can stop most of the incidents and minimize the outcomes of the rest.
Below we have listed some of the most common disruptions a date beach can cause, and why companies begin adopting DLP as one of the guiding principles of their IT security:
- Business Continuity: Losing important data can disrupt business operations, halting productivity and costing revenue. Effective DLP ensures that your business can recover quickly from incidents and maintain continuity.
- Reputation Management: A data breach can severely damage an organization’s reputation. Customers, partners, and investors may lose trust, resulting in lost business opportunities.
- Legal Penalties: Non-compliance with data protection laws, such as GDPR or HIPAA, can result in hefty fines and legal consequences. DLP helps organizations adhere to these regulations.
- Prevent Permanent Data Loss: Corporate espionage or targeted attacks may result in the permanent deletion of sensitive information. DLP helps prevent the irreversible loss of critical data.
- Cost Savings: The financial impact of data breaches can be immense. Investing in a DLP solution can help avoid the costs associated with data recovery, legal fees, and lost business.
If you feel that your business may be at risk of a data breach through any of the above-listed risks, seriously consider strengthening your security with a DLP solution. Many businesses cannot afford the burdens carried with severe data loss, and a single hack could send your operations into a tailspin.
And while automated solutions will be your best bet against data breaches, there are also some standard best practices you can follow to help prevent any critical data loss.
Data Loss Prevention Best Practices
This section discusses critical enterprise DLP practices. It is important to combine as many of these practices as possible to make sure your data loss prevention is efficient and can withstand modern cyber threats.
Backup
Backup is a must-have practice for data loss prevention for both on-prem and cloud environments. An efficient backup solution works automatically and requires minimal manual control from the IT team.
Is backup enough for data loss prevention?
Some organizations think that having a backup is enough for data loss prevention. However, we think it’s an erroneous approach for the cloud DLP for the following reasons:
- 57% of backup compromise attempts were successful in 2023, meaning that attackers were successful in impacting the recovery operations of over half their victims.
- Recovery in the cloud takes more time than for the on-prem solutions. This is especially true for ransomware attacks.
- Ransomware, man-in-the-middle, and zero-day attacks often include data leaks. And it is preferable to prevent them rather than exclusively rely on backup.
Data Retention Policies
Google Workspace, Microsoft 365, and certain third-party tools have functionality for data retention (the protection of certain files from deletion and editing). Here’s how it works in Microsoft 365. An Admin creates a data retention policy for a certain type of files (files with a particular word in the name or belonging to a certain organization). Every time such a file is edited or deleted, Microsoft 365 creates its copy and stores it in a separate location. Keep in mind that the file takes up the user’s storage space. To uncover this copy, Admins need to use a special search which makes the recovery process harder.
User and Data Behavior Monitoring
Monitoring data behavior also helps improve data loss prevention. Admins can detect and investigate whenever a record (file, folder, or email) is deleted, edited, or removed from the trash. But it’s next to impossible to carry out manually within a large organization where hundreds of files are edited and deleted on a daily basis. That’s why this is usually an automated function within third-party DLP solutions.
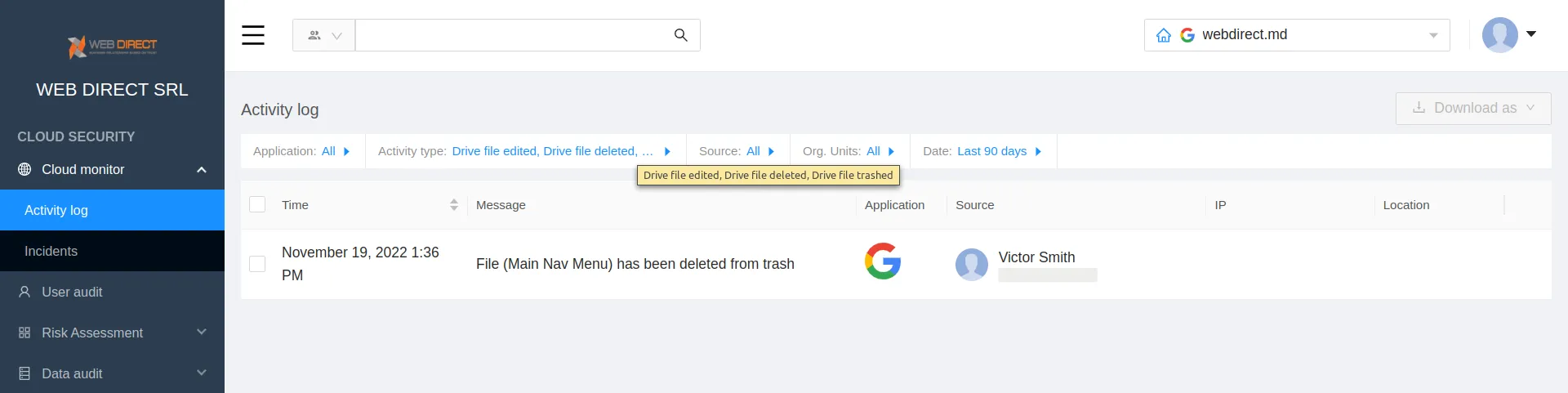
User behavior monitoring is similar to data behavior monitoring. Only it focuses on detecting suspicious behavior of certain users and enables companies to identify employees that carry out man-in-the-middle attacks.
Shadow IT Control
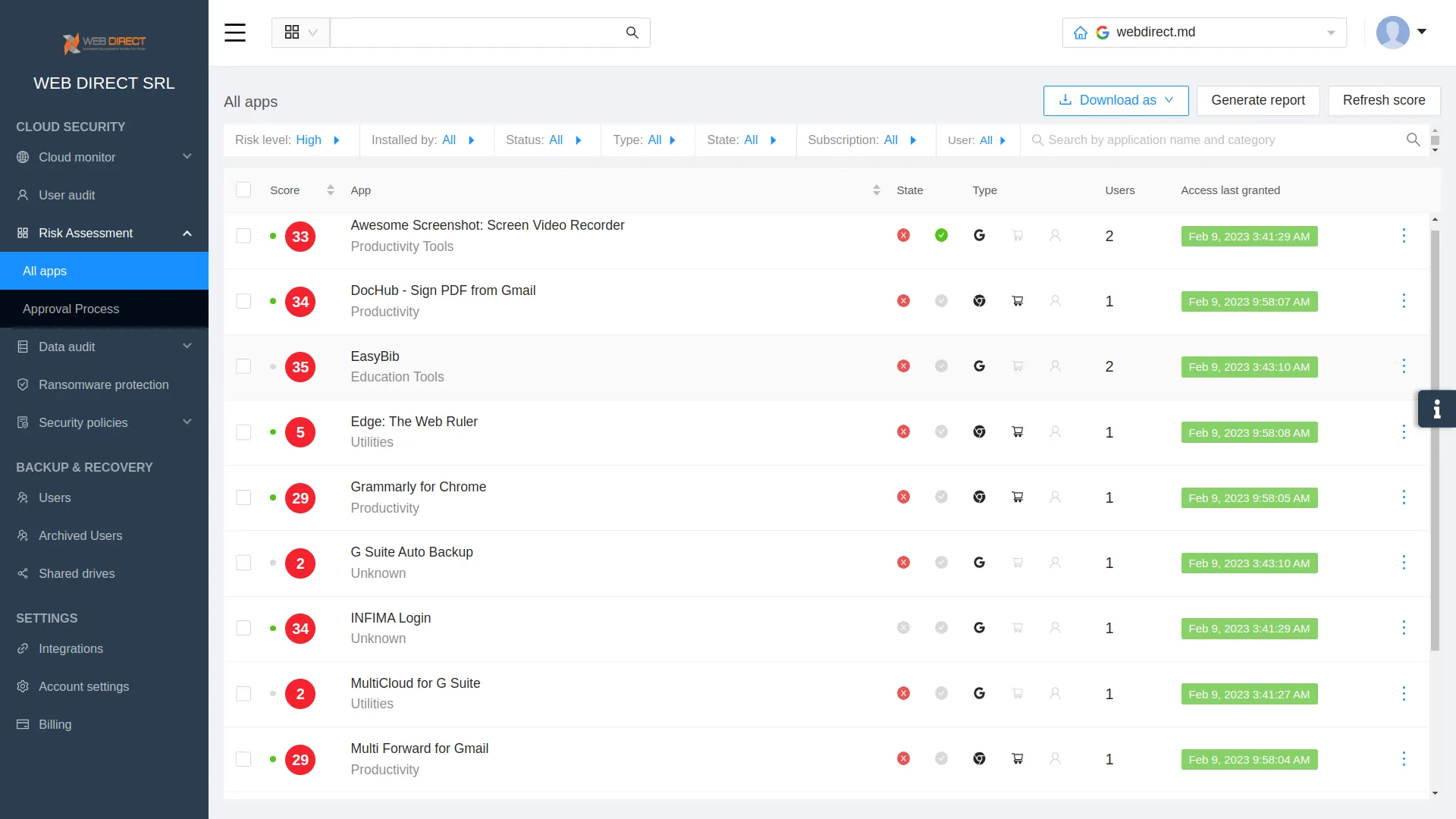
This practice helps prevent data loss in zero-day attacks. It is important for companies to identify potentially dangerous applications with editing permissions and revoke their access to sensitive data. This DLP program requires proper application risk assessment and, if done manually, can take several weeks. Tools like SpinOne have app detection and evaluation functionality and can do this task within seconds.
Ransomware Protection Software
Some ransomware protection tools can stop ransomware at the very beginning of an attack preventing it from decrypting the entire corporate data. Note, however, that most anti-ransomware tools usually wait for the end of the attack and only then start recovery from backup. In the case of cloud data, this process can take weeks or even months due to API limitations. Another type of ransomware protection uses historical data to identify the ransomware and get the key from their database. Unfortunately, ransomware is the most actively evolving type of malware, so chances are high that an organization will be hit with a new type. The best anti-ransomware tools use data behavior analysis to spot cloud ransomware, identify the application that causes the attack, and revoke its access to your data.
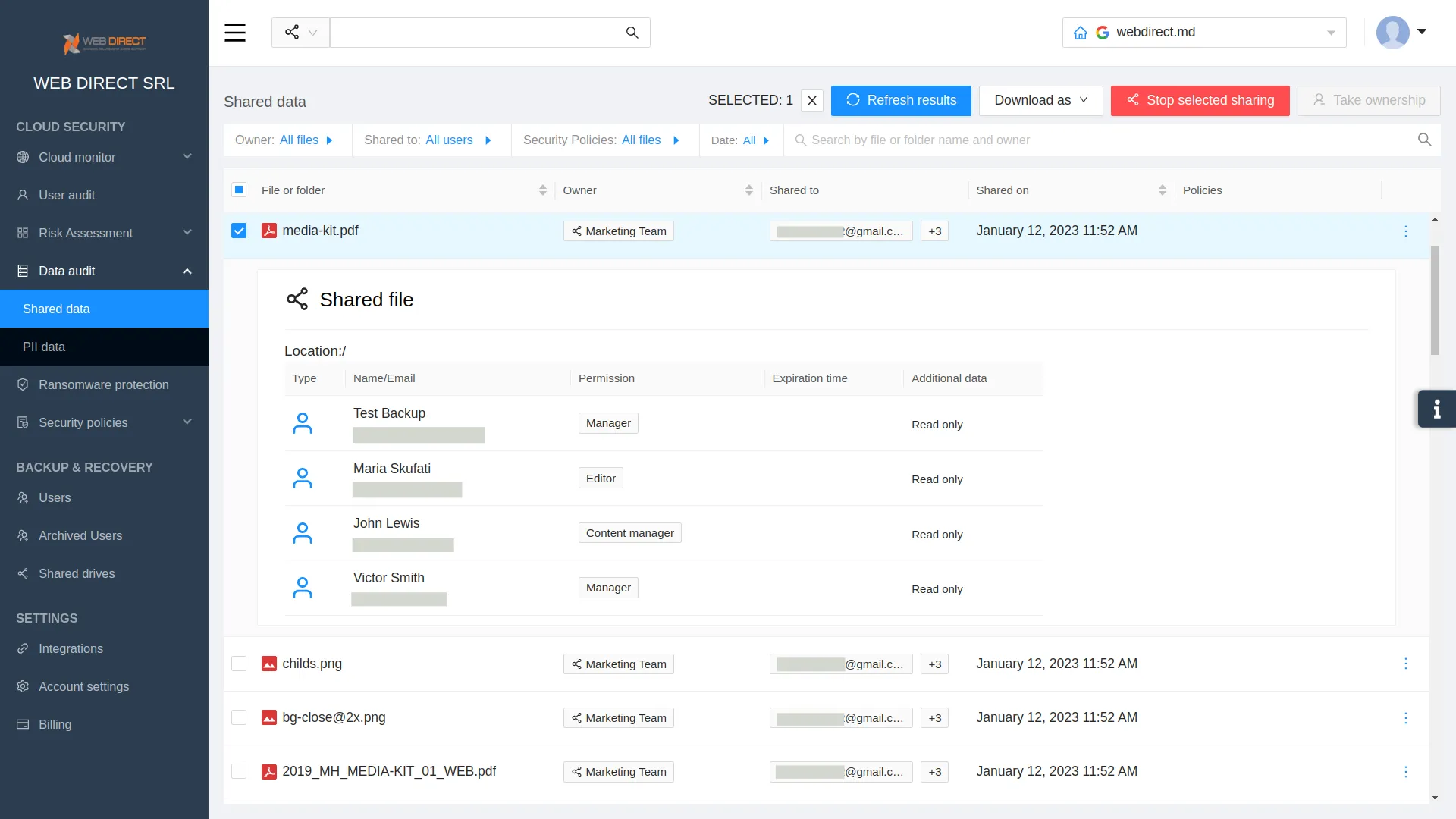
Sharing Control
Sharing control can significantly enhance data protection. Admins of cloud collab tools need to make sure that files containing sensitive data have proper sharing settings. This practice includes the detection of unauthorized sharing and immediate change of the settings.
Adopting a DLP Solution
For large enterprises managing vast amounts of sensitive data, manual DLP practices are not enough. Automated DLP solutions are crucial tools when it comes to implementing comprehensive data protection strategies and ensuring your and your customer’s data security. Solutions like SpinDLP offer advanced features such as 24/7 ransomware detection, shadow IT discovery, and automated data retention policies to protect against modern cyber threats.
By adopting a robust DLP solution, organizations can automate data monitoring, enforce security policies, and minimize the risk of data breaches, ensuring their sensitive information remains secure.
Data loss prevention is essential for safeguarding the data that forms the backbone of any organization. A well-implemented DLP strategy provides a multi-layered defense against a variety of data threats, protecting not just the company’s data, but also its reputation and future.
Get in contact with our sale team for a free demo here.
FAQ
How does Data Loss Prevention work?
DLP detects potential hazardous events in the system. Next, it can stop them or notify the user that their actions can lead to data loss. It also can notify the Admin about the incident.
What are the common types of data loss incidents?
The common types of data loss incidents include accidental deletions, ransomware, zero-day attacks, and unauthorized access.
What are the potential consequences of data loss for businesses?
The potential consequences of data loss for businesses include business termination, revenue loss, reputational loss, client churn, lawsuits, etc.
What are the key benefits of implementing a DLP solution?
The key benefits of implementing a DLP solution include avoiding data loss and its consequences (e.g., downtime, financial losses, legal fines, etc.). IT can also help you strengthen your overall security.
How can Data Loss Prevention help organizations comply with data protection regulations?
Many countries have laws that mandate the retention of certain data (e.g., employee records). Losing this information is considered non-complines and subject to legal fines.
What are some challenges in implementing a DLP program? I
The challenges in implementing a DLP program include finding the necessary tools, keeping up with compliance regulations, and having the necessary talents.
Is Data Loss Prevention only applicable to large organizations?
No. Just as any business can lose data, companies of any size can implement DLP.
What are some best practices for effective Data Loss Prevention?
The best practices for effective Data Loss Prevention are data discovery and management, data monitoring, app risk assessment, ransomware prevention, regular data backup, and automation.
Can Data Loss Prevention protect against insider threats?
Yes. Malicious insiders can delete or falsify your data. Without efficient DLP, these incidents will remain unspotted and uncorrected.
Are there any limitations or drawbacks to implementing a DLP solution?
DLP solutions can slightly impact the productivity of business employees. However, there’s always a trade-off between comfort and security.
What is the role of employee training and awareness in Data Loss Prevention?
Employee training and awareness can help employees avoid insecure behaviors and thus improve Data Loss Prevention.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...

