Disney’s Slack Data Breach: Lessons for Enterprise SaaS Security
Recently, Disney was the target of a high-profile breach in which a hacker group was able to compromise the internal Slack archive of the environment. Let’s take a close-up look at the breach, what happened, and the lessons learned from the incident that can help other enterprise organizations improve their security posture when using SaaS apps like Slack.
What happened?
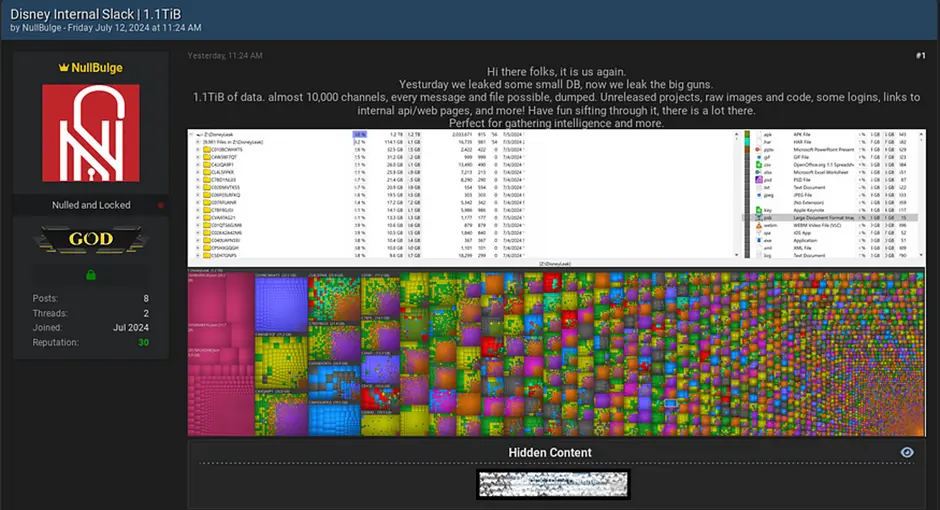
First, what happened with the hack that resulted in over 1.2 TB of Disney’s private Slack data being compromised? The hacktivist group “NullBulge” claimed responsibility for the data leak. The group appears to be motivated by advocating for artists they feel are being threatened by the likes of AI and artist contracts that are less than beneficial to the artists themselves. They cited Disney’s handling of artist contracts and the use of AI-generated content as their motivations for the attack.
The hacker group breached nearly 10,000 Slack channels that included sensitive information and exposed unreleased project information, images, source code, credentials, and internal communications between teams.
How was the breach carried out?
NullBulge was able to infiltrate the Disney network and steal the treasure trove of Slack data via a compromised endpoint of one of the Disney developers. The hacktivist group says the developer installed a compromised video game mod that allowed them to gain access to the network.
What types of data were stolen with the Slack data leak? The leaked data includes data that goes all the way back to 2019. The Slack conversation data includes discussions on ad campaigns, studio technology, and many other internal details. Also, the exposed Slack communications disclosed future project descriptions, plans, and financial data.
Source: Cybersecurity News
Security insights that come from the breach
There are many takeaways from the breached Disney Slack environment. Note the following:
- Insider threats and risky behaviors – The successful hack of the Slack environment highlights the dangers of insider threats and risky behaviors by end users. A breach of this scope comes down to a malicious video game mod that was downloaded by a developer. It helps to emphasize the fact that user behaviors, activities, app installations, and access to sensitive information need to be monitored and properly vetted for security.
- A data leak can have tremendous scope – The Disney data leak has as its scope over 1.2 TB of data that was compromised. The enormity of this type of data leak is broad. It affects many different departments and likely will lead to financial damage.
- Various motivations – Hacker groups do not operate on a single motive. Different groups have different motivations, including social, economic, or political factors. The motives add to the complexity of defending critical data from attack and must be weighed into modern defensive strategies.
- History repeats itself – The Disney hack is very similar to the 2014 Sony Pictures hack. In that attack, hackers released sensitive internal data that caused widespread disruption to Sony. It shows that large corporations in the entertainment industry are not immune to cyber-attacks and are often the target of various hacker groups.
- Malicious and risky apps are a problem – Often, hackers get a foothold in an environment due to a risky or outright malicious app downloaded and installed by an end-user. In this case, a developer downloaded a seemingly harmless game mod that turned out to be a malicious backdoor to the environment, leading to 1.2 TB of data being stolen. Organizations must have controls in place to block risky apps and perform continuous risk assessments of SaaS apps in their environment.
How enterprise organizations can prevent similar data breaches
There are many lessons that can be learned in the post-mortem of the Disney Slack breach. To help prevent similar cyber attacks in their environments, organizations should implement the following security measures:
- Multi-factor should be standard – Modern organizations need to implement and use very strict access control protocols. Multi-factor authentication should be the standard and default authentication to access every critical and sensitive system, including SaaS environments.
- Regular security audits and risk assessments – Security audits need to happen frequently. Also, continuous risk assessments of apps and integrations in the environment must be a part of the overall cybersecurity strategy. Organizations need to use modern cybersecurity solutions that provide security automation to perform automated risk assessments. Manual assessments are no longer good enough to find unseen risks.
- Cybersecurity training for employees– Regular cybersecurity training for employees should be part of the foundation of an enterprise organization’s security strategy. Employees need to be able to recognize phishing attempts and understand the critical importance of protecting their login credentials from theft.
- Insider threats – These types of threats can be posed by users who intentionally try to compromise organization security or those who inadvertently or accidentally do so. Either way, the risks are the same. Again, modern cybersecurity solutions that use artificial intelligence (AI) and machine learning (ML) can flag anomalous activities and any behaviors that are out of the typical pattern of everyday use. Such activities may include unusual bulk downloads of data, unusual failed logins, or shadow IT.
- Encryption – Make sure critical or sensitive data is encrypted. Encryption should be implemented both in-flight and at rest to ensure the data is always unreadable to unauthorized individuals, both when it is being communicated across the network and when it is stored on disk.
- Incident response automation – When a security breach happens, organizations must respond quickly. Using incident response automation is a critical component of modern cybersecurity strategies. For example, if a ransomware attack occurs, having automated solutions that can remediate the attack automatically can drastically reduce the recovery time objective (RTO). This is especially true for SaaS platforms that may throttle data restores from third-party backup solutions.
How SpinOne Can Help
SpinOne is a comprehensive modern cybersecurity solution that helps to protect your SaaS data. It uses modern artificial intelligence (AI) and machine learning (ML) to perform continuous risk assessments, recognize insider threats, and shadow IT, and it can automatically remediate ransomware attacks.
It can help protect against the vulnerabilities exposed in the Disney breach. Note the following capabilities of the SpinOne solution:
- Access visibility to SaaS platforms – The SpinOne solution provides visibility to data access and activities in the cloud, including user activities and behavior, and visibility to shadow IT operations
- Abnormal download detection – One of the powerful components of SpinOne’s data protection solution is advanced algorithms that can detect abnormal downloads in the environment. This includes abnormal data exports, which may indicate malicious data exfiltration, such as what happened in the Disney breach.
- Policy-driven security – SpinOne uses policy-driven cybersecurity automation. Organizations can set the metrics for policy rules, such as reputation scores for SaaS apps or browser extensions that users are allowed to download and install
- Backup and recovery – Third-party backups of SaaS environments are necessary to make sure your data is protected from loss, either due to cloud outages, hardware failures, or malicious activity. SpinOne provides efficient incremental backups of cloud SaaS environments. Admins can choose which cloud the backups are housed in so they can align with 3-2-1 backup best practices and any compliance or data governance requirements they need to uphold.
- Automated incident response – SpinOne provides automated incident response capabilities. It provides one of the lowest SLAs for data recovery of SaaS environments due to ransomware attacks at 2 hours. This is due to the automated response capabilities it provides. Spin automatically implements the following:
- It continuously scans for the signs of a ransomware attack
- If an attack is detected, it blocks the source of the ransomware attack
- SpinOne then scans the environment for any data affected
- Any affected data is automatically restored from the last good data backup (configurable)
- Admins are automatically notified of the attack and recovery operations
By leveraging these modern SaaS security features offered by SpinOne, organizations can enhance their cybersecurity posture and make sure they are protected against breaches like the one experienced by Disney.
Wrapping up
This latest breach affecting Slack data and Disney helps organizations worldwide appreciate that threat actors are targeting businesses regardless of size. It shows that cyberattacks are likely when proper controls are not in place to prevent users from downloading risky software. With today’s SaaS environments full of third-party apps and browser extensions that integrate with cloud data, enterprises must have visibility to and control over these third-party apps. In addition, continuous risk assessments are needed even with trusted apps, as these may change over time.
SpinOne is a next-generation SaaS security platform that helps organizations mitigate risk and increase compliance. It also ensures seamless business continuity and data recovery in case of accidental or intentional data loss. Learn how SpinOne can safeguard businesses from data loss and improve your cybersecurity strategy. Request a demo today.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...
Data Loss Prevention Techniques for 2025 and Beyond
It’s painstakingly clear that data loss is a major challenge facing businesses today. Our experts...
What is SaaS Security? Challenges & Best Practices
Businesses increasingly rely on Software as a Service (SaaS) for increased efficiency, collaborativeness, and scalability....


