FBI and CISA Alert (AA22-249A): Why Backups are Not Enough Anymore
With the growing threat of ransomware and the recent attacks by the Vice Society criminal group on education institutions, the Federal Bureau of Investigation (FBI), in conjunction with the Cybersecurity & Infrastructure Security Agency (CISA), recently posted an alert to education organizations (Alert AA22-249A). In this post, we are reviewing FBI and CISA Alert (AA22-249A).
It describes the immediate threats posed by Vice Society and other ransomware groups. It also detailed mitigations organizations need to implement to bolster their cybersecurity protections against modern ransomware threats. Let’s look at these and how institutions can protect their on-premises infrastructure and cloud SaaS assets.
Ransomware is more dangerous than ever before
Unfortunately, the plague of ransomware for organizations worldwide has only gotten worse. Ransomware groups are using more sinister tactics than previously. In addition, more resources are available for attackers wanting to delve into the world of ransomware attacks. Ransomware attacks have evolved in frequency, scope, and severity from the early days of encrypting files found on a PC, with attacks now affecting businesses every 11 seconds.
Ransomware groups have started using a new tactic called double extortion, helping secure ransom payments from organizations with even good backups of their data. So how does double extortion work? Double extortion is an evolution of the typical ransomware business model. Instead of demanding a ransom for decrypting data encrypted by ransomware, attackers require a ransom payment to prevent data leaks of critical data.
Backups are no longer enough
With the new double extortion technique, backups are no longer enough to protect organizations from the ravages of a ransomware attack. However, since the attacker’s first move is to exfiltrate data before encrypting it, the data leak threat has generally already been secured before the actual encryption of critical data begins.
Backups only protect businesses from the encryption of data, not the exfiltration process. Even if there are rock-solid backups of business-critical data, attackers already have the data in their possession to launch the data leak threat. Either way, they have the upper hand once the attack progresses to the point of data exfiltration.
In the world of modern ransomware attacks leveraging double extortion, backups are not enough to mediate the threat posed. Organizations must leverage a multi-layered approach to cybersecurity to help bolster their security posture. While we are not minimizing the value and importance of backups as part of a well-balanced and architected security strategy, you don’t want to have a false sense of security by having backups. More is needed to protect your critical data and assets.
Google Workspace Backup Solution Comparison Table
View our competitive pricing chart
*Contact Us for current pricing.
Recommendations contained in FBI and CISA Alert (AA22-249A)
CISA and FBI security recommendations as part of Alert (AA22-249A) included many aspects of a robust cybersecurity protection strategy. However, we will focus on preparing for cyber incidents section of the recommendations contained in the Alert. Note the following recommendations:
- Maintain offline backups of data
- Ensure data is encrypted and immutable
- Review the security and access of third-party vendors
- Implement policies to enforce using only sanctioned applications and remote access solutions
- Document and monitor external remote connections
- Implement a recovery plan
1. Maintain offline backups of data
A cornerstone best practice in the world of backup strategies is the 3-2-1 backup model. The 3-2-1 backup model recommends at least (3) copies of your data, stored on (2) different types of media, with at least (1) copy stored offsite. This best practice model helps to spread risk over several different backup mediums and locations, so the likelihood of losing all copies of your data is exponentially small.
The recommendation to maintain offline data backups is good since it aligns with the different media types and offsite copies. In addition, if your data is stored on another media type and stored offsite, it provides strong protection against the “reach” of ransomware, making it unlikely to be affected.
2. Ensure data is encrypted and immutable
This point is an important one. It is vital to remember that production data contained in backups is production data. It means backups need to be protected as production data is protected. Data encryption is one of the basic ways to protect critical and sensitive data from falling into the wrong hands.
When production backups are created, you want to ensure the solution you are using to back up your data encrypts the data backups. It is also important to encrypt data in flight and at rest. Data encryption in flight encrypts the data as it flows across the network. However, don’t assume that encrypting the data once it lands in the backup storage location is enough. A skilled hacker can eavesdrop on network traffic and potentially steal data as it travels to its destination backup target.
Therefore, encrypting data as it travels across the network and when it reaches its storage location is critically important for proper cybersecurity and ensuring data is protected from attackers. Depending on the backup location, many cloud storage providers offer immutability for data storage.
When the immutability flag is set on cloud storage, it prevents any changes to the data. Depending on the configuration of the immutability flag, it can even prevent administrators from making changes. This feature helps protect data from attack as it prevents ransomware processes, as it does users, from changing the data, including encrypting it.
3. Review the security and access of third-party vendors
Reviewing the security of third-party vendors is an essential part of solid cybersecurity. Organizations, including educational institutions, must remember they are only as secure as the third-party vendors integrated with their systems.
For example, when you think about the security implications of the SolarWinds supply chain attack, businesses using the compromised SolarWinds Orion system were breached by malicious code. It emphasizes how easily a significant security breach of a third-party vendor software solution can compromise critical data.
It is a crucial point to remember in cloud Software-as-a-Service (SaaS) environments like Google Workspace and Microsoft 365, where users can integrate thousands of third-party cloud apps into the environment with only a few clicks. Unfortunately, this action can happen without a proper risk assessment and can lead to insecure or malicious software having access to sensitive cloud data. Therefore, educational institutions and others must perform proper risk assessments of third-party vendors, applications, and cloud SaaS apps to ensure data is adequately protected.
4. Implement policies to enforce using only sanctioned applications and remote access solutions
In addition to performing risk assessments, they must use the right technical solutions to enforce governance and policy-driven security protection. Unfortunately, only suggesting what they should do to end users is not enough to protect data. Organizations must implement effective policies and governance at a technical level to protect sensitive data.
Policy-driven security provides security automation that allows organizations to create “guardrails” for what end-users can and can’t do and which software they can install. Using policy-driven security enforcement for cloud SaaS environments is also critical to the overall security of modern hybrid cloud infrastructure.
5. Document and monitor external remote connections
Adequate monitoring enables organizations to find anomalous network connections and threat actors attempting to compromise external network resources. However, manual monitoring efforts by SecOps professionals are not enough. The sheer size and scope of data, resources, and threat signals exceed what humans can effectively identify.
Using artificial intelligence and machine learning solutions, organizations can allow computer-based solutions to create baselines of normal activity and easily spot network connections, traffic, and other activities outside of what is considered normal behavior. In addition, AI and ML-based solutions are excellent at performing mundane tasks such as log filtering and monitoring that humans are not so good at doing.
In addition, organizations must take note of who they are sharing data with and what applications may allow data sharing. This concern is especially true with cloud SaaS environments that make sharing data outside the organization extremely easy, along with third-party cloud SaaS apps that can easily expose data.
6. Implement a recovery plan
How does an organization recover critical data after a ransomware attack? Furthermore, how do they ensure they proactively stop any malicious leaking of data and malicious processes related to an attack? A recovery plan helps to detail the steps involved in recovering critical data following an attack. In addition, it allows institutions to understand the criticality of various data sets and prioritize data recovery in the proper order.Organizations must have a recovery plan as it helps to recover from a disaster as quickly as possible. However, any outage can lead to lost revenue, tarnished brand reputation, and even result in compliance violations with legal and financial consequences. Additionally, without an established and agreed upon recovery plan following a disaster such as a ransomware attack, uncertainty, and the unknown can drastically increase the time to recovery.
Protect your cloud SaaS data with SpinOne
As mentioned, one of the most challenging aspects of ensuring data governance, protection, and cybersecurity is protecting data living in cloud SaaS environments. Organizations, including educational institutions, are migrating their data in bulk to cloud SaaS environments housed in Google Workspace or Microsoft 365. Many make the mistake of migrating their data to cloud SaaS environments with little understanding of the steps needed to protect and secure their data.
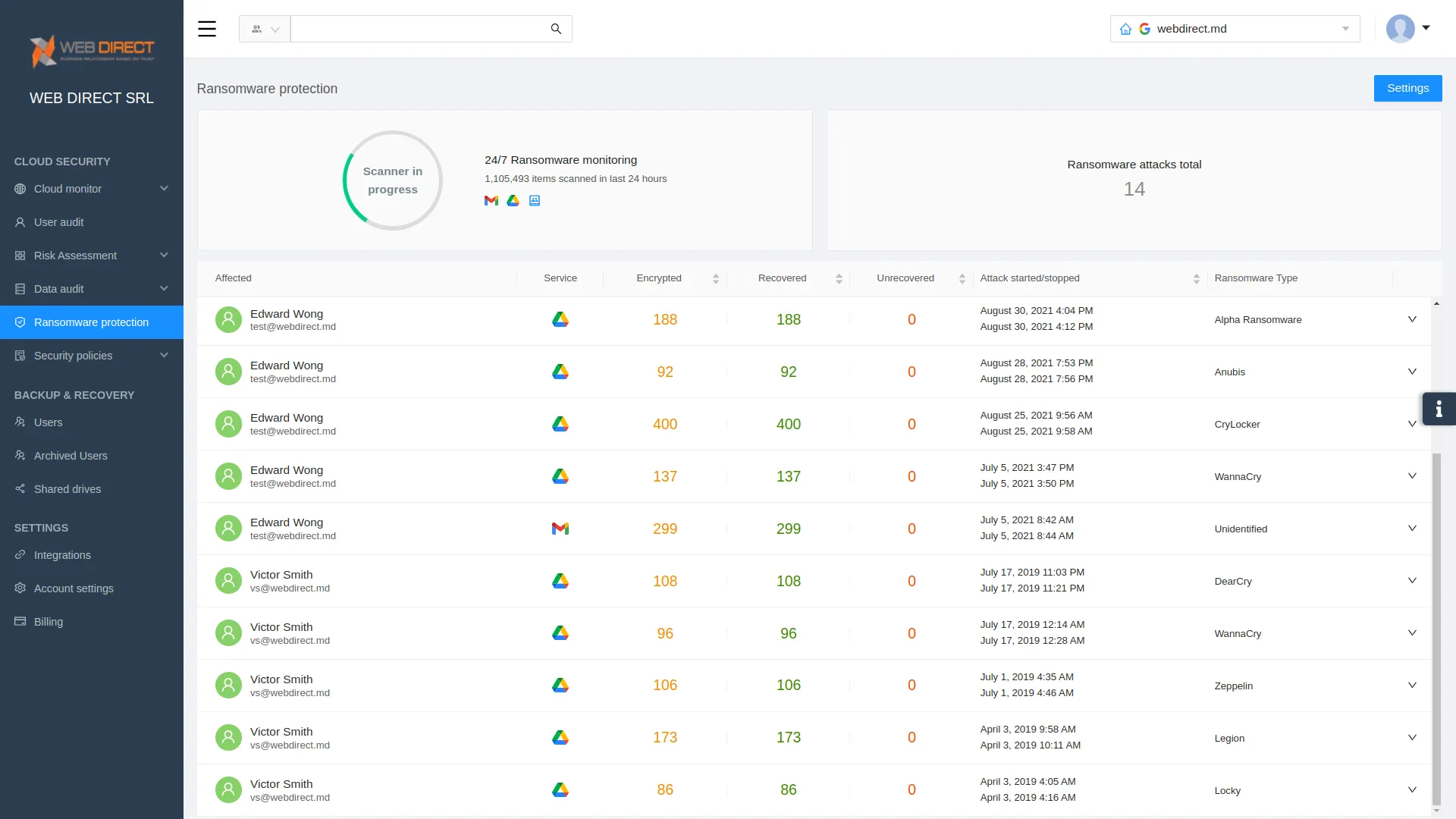
SpinOne is a modern data protection and cybersecurity solution providing next-generation capabilities, including artificial intelligence (AI) and machine learning (ML). It provides a proactive ransomware recovery solution that monitors the environment for any signs of an attack and immediately remediates the threat when detected. It does this with a 5-step approach, using cybersecurity automation to detect, contain, and remediate the threat.
When ransomware is detected, SpinOne reacts swiftly and decisively:
- SpinOne monitors cloud SaaS environments for signs of ransomware 24/7/365
- If ransomware is detected, SpinOne blocks the ransomware source at a network level
- It automatically isolates assets affected by the ransomware attack
- SpinOne automatically restores affected files to the latest backed-up version (configurable)
- It immediately notifies IT admins on incidents in real-time
- SpinOne Provides granular SaaS security policy orchestration, customizable for your organization
In addition, the SpinOne solution enables organizations to align cloud SaaS data protection and security with the best practices outlined by CISA and the FBI. Note the following best practices and how SpinOne allows organizations to align with these:
- Maintain offline backups of data – SpinOne stores backups in separate cloud storage locations with no user-session or file system that ransomware or other threats can attack. It also allows businesses to choose which cloud storage environment is used to align with existing business technology partners.
- Ensure data is encrypted and immutable – SpinOne uses the latest security protocols to encrypt data in flight and at rest, securing data backups end-to-end.
- Review the security and access of third-party vendors – SpinOne provides automated risk assessments of third-party cloud apps. What would take hours for trained SecOps professionals takes only minutes with the Spin solution. In addition, it maintains a catalog of cloud SaaS apps with the associated risk scores, allowing admins to build powerful policies based on risk scores and which apps are allowed for use in the environment.
- Implement policies to enforce using only sanctioned applications and remote access solutions – Leveraging the automated risk assessments, organizations can leverage the cybersecurity automation capabilities of SpinOne to provide rock-solid governance of cloud SaaS apps. It also provides clear visibility of what data is shared in the organization, both internally and externally.
- Document and monitor external remote connections – On top of the real-time visibility it provides, SpinOne provides reporting capabilities, allowing admins to increase their awareness and visibility of remote connections and data sharing. Additionally, SpinOne captures and logs detailed information about remote connectivity to the cloud SaaS environment, providing detailed auditing from the cloud SaaS environment and SpinOne-specific information.
- Implement a recovery plan – SpinOne leverages next-generation cybersecurity for cloud SaaS by leveraging artificial intelligence (AI) and machine learning (ML). It automates your recovery plan in the cloud by proactively kicking into action when ransomware is detected, remediating malicious activity, and protecting your critical data.
If you would like to speak with a Spin Solution Engineer to discuss how SpinOne can help you meet your ransomware protection challenges, click here to book a demo: Request a Demo of SpinOne
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...


