Google Workspace 2-Step Verification and Two-Factor Authentication
Similar to two-factor authentification, Google Workspace 2-Step Verification provides additional protection for your Google Workspace. These methods are necessary to prevent your original account from being hacked. Learn what these methods are, how to use them and what’s the difference between them.
Why is Two-step Verification Important for Google Workspace Security?
Two-step verification – represents two steps to protect logging into your account. The first step you make is when you enter your standard login and password. Then you make the second step – when you add another type of password into your account, using a one-time password (OTP). This password has six digits and is generated every 30 seconds.
In this way, if somebody stole your login and password, the second password is impossible to see, because it is different every minute.
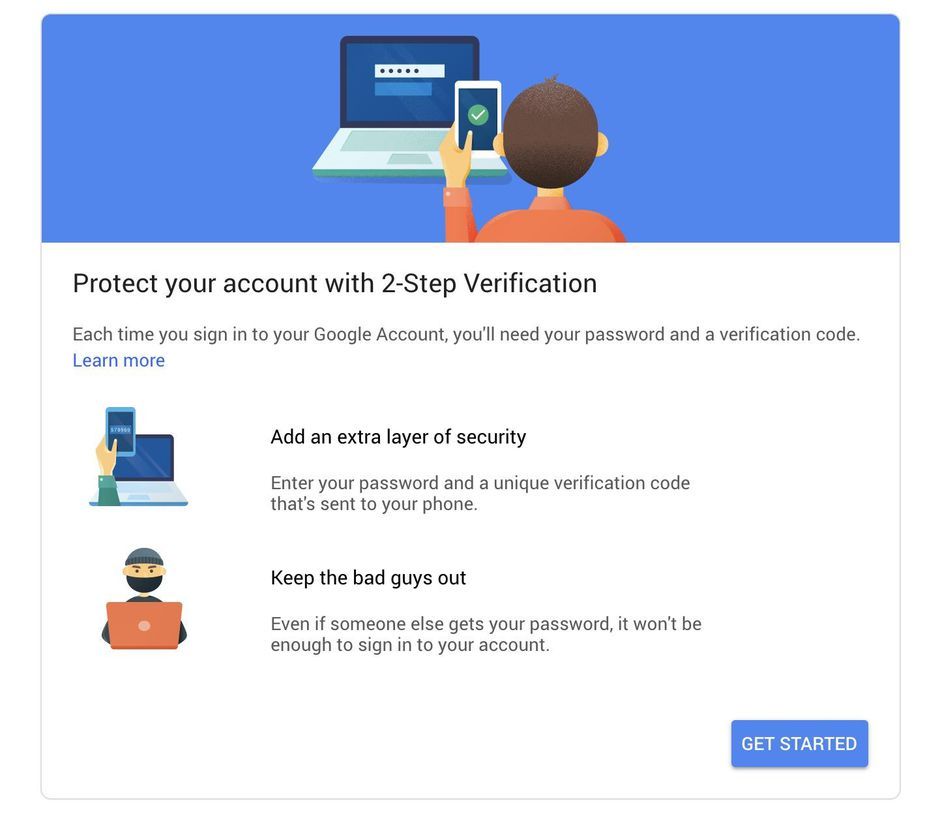
The important point is that the activation of two-step verification in your Google account doesn’t mean that you do not need to activate it in your SpinOne account. Two-step verification is obligatory for each service you use. This is one of the admin’s responsibilities to set up this function.
Difference between Google Workspace 2-Step Verification and Two-Factor Authentication (2FA, MFA)
Two-step verification is the one you need for checking your identity when you enter your account from different devices or you login from a new one.
Two-factor authentication (or multi-factor) means that to get into your account you need to enter 2 or more different types of authentications. It doesn’t matter whether you enter from the same location or from a variety of locations, you need to go through this set of steps all the time. So the point is if you successfully run the first authorization step, the second one will set off automatically.
And you will also use additional devices for generating digit code from a custom QR code or take a SMS with a one-time password or email authorization. All these things can be the second factor of authentication. This helps to eliminate the risks of being hacked.
Generally, these protection methods use the same tools, but the main difference lies in their purposes.
How Two-step Verification Enhances Google Workspace (G Suite) Security
To deploy it you need to use your phone or tablet.
- Sign in to your SpinOne account.
- Click the ’My Account’ link on the left toolbar.
- Click the ‘Enable 2-Step Verification’ button to activate this option.
- Upload/Install Google Authenticator app on your device: iOS app, Android app, BlackBerry.
- Scan QR code on the left side of the window.
- A note will be added in the Google Authenticator app, that every 30 seconds generates a digit code.
- Please enter this 6 digit code in the authorization field and confirm.
Why do you need to use Google Authenticator?
Solution OTP (one-time password) is simple in implementation, necessary to enhance the security of your Google Workspace environment, and does not require additional costs. There are 20 different client implementations of the Time-based One-time Password Algorithm (TOTP), such as Authy, 1Password, Google Authenticator, and others.
You can use Google Authenticator on Android, iPhone, or Blackberry, and it works even if you don’t have an Internet connection or mobile service. Also, you can tune Google Authenticator for multiple accounts on one device or for one account on multiple devices.
Was this helpful?
Latest blog posts
Cyberhaven: Latest Research Reveals 8 Additional Compromised Extens...
Spin.AI’s latest research has uncovered 8 additional compromised browser extensions, used by 1.1 million users...
Managed Service Provider Best Practices in Data Backup and Disaster...
Highlights the importance of a robust data backup and recovery program provided by Managed Service...
Exposing the Hidden Risks of Browser Extensions: Cyberhaven’s...
Today’s digital landscape is under attack like never before. Threat actors are looking for the...





