Security Risks of Using Google Add-Ons
Google add-ons were introduced in 2014 as a way to bring additional functionality to Google Docs and Sheets by installing plugins published by third-party developers.
Add-ons can be browsed and installed directly from within Google Workspace by clicking the “Add-ons’ tab in the main menu of any document you’re working on. The fact that these add-ons are so easy to install and seem to be officially approved by Google may lull users into a false sense of security that they are as safe as using Google Workspace itself, but in fact, third-party add-ons can introduce new security risks into your organization.
What are Google Add-Ons and Why Use Them?
Add-ons extend the native functionality of Google Docs and Sheets and can help to increase the productivity and efficiency of document creation, add functionality such as electronic signatures, and improve opportunities for collaboration and communication within Google Workspace.

Some examples of the most popular add-ons for 
- EasyBib – automatically cites books and journals and generates a bibliography
- Table of contents – automatically create a clickable table of contents in the sidebar
- Easy accents – add accents from a sidebar when typing in another language
- Openclipart – browse and insert free clipart images from directly inside your document.
Some add-ons for 
- Flubaroo – automatically grades multiple-choice assignments
- Remove duplicates – easily remove duplicate data in spreadsheets
- YetAnotherMailMerge – create email campaigns in Gmail, format, and send based on data in Sheets
- Save as Doc – convert a Google Sheets spreadsheet into a Google Document
Without the functionality that these add-ons provide, it may take significantly more time and effort to perform certain tasks when using Google Workspace. However, it is sensible to be cautious about how many add-ons are installed and be aware of the permissions that each add-on requests, particularly in a business setting.
Security Risks of Google Add-Ons
When you install a Google Docs add-on or a Google Sheets add-on, it will request several permissions for accessing your Google Workspace data and Google apps. These may include:
- Full access to all your Google Drive files
- Create new documents
- Edit existing documents
- Share documents with others
- The ability to send email as you
- Connect to external services to read and write data
- Run the application while you are not present
- View, manage, and permanently delete your email
- View and manage your contacts
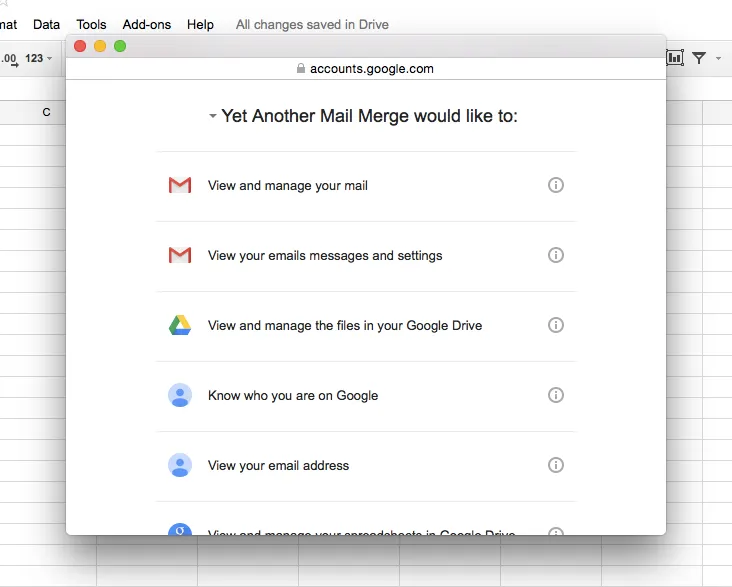
There are probably very few people that you would trust to have complete control over your Google Workspace data including the ability to read and delete all of your documents and Gmail messages, copy any information to an external source, and send messages on your behalf. However, this is exactly the access you are granting when you approve permissions for some Google add-ons.
Once a third-party add-on has been granted access permissions, it will retain them until the permissions are manually revoked. This means that add-ons that have not been used for several years could still have access to sensitive corporate information.
Insecure add-ons that have access to corporate data could potentially cause a serious data breach or data loss by accessing or deleting files without your knowledge. It is also very difficult to control add-ons that employees install on their own devices and this is of particular concern for high-level employees who have access to sensitive data (as the add-on will also be able to access this data).
How to Reduce Security Risks of Google Add-Ons
Let’s explore how to reduce the security risks while using Google add-ons. Allowing unlimited and unmonitored installation of Google add-ons is a recipe for disaster, so the first defence step in any organization should be to develop a policy for the use of add-ons within Google Workspace and make sure that employees are trained in the importance of following this policy.
Many organizations have success with issuing a list of officially approved apps and add-ons and this can help to reduce the number of insecure third-party add-ons that are installed, but it is unlikely to stop it completely (as staff may choose to ignore the security policy or simply be unaware of it).
When assessing add-ons for suitability and security, particular care must be taken to ensure that the permissions requested by the add-on are required for its functionality, and that the add-on provides sufficient benefit to the organization to be worth the increased security risk.
Using monitoring software such as Spinbackup Google Workspace Cyber Security Solution with 3rd-Party Apps Audit can greatly reduce the risk of data breaches through continuous monitoring of connected apps. If an employee grants access permissions to a risky add-on, administrators can be alerted of this and choose to revoke the permissions and block the add-on.
Another essential step is to ensure that an adequate backup system is in place. If an add-on deletes vital company data either through a software error or because it has been hijacked by a hacker for malicious purposes, having a full Google Workspace backup in place will limit the impact as you will be able to restore all company files to a point in time before they were deleted.
To find out more about Spinbackup Google Workspace Backup and Cybersecurity with risky third-party apps control, and increase the security of your organization’s data, request a demo of the service today.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
6 Common Mistakes in Google Workspace Backup
Google Workspace is a set of productivity apps, including Gmail, Drive, Docs, Meet, and Calendar...
Google Workspace vs. Microsoft 365 comparison
With so many productivity suites available, it can be overwhelming to decide which one is...
Top 10 Low-Risk Applications and Extensions for Google Workspace
Google Workspace is an extremely popular SaaS productivity suite used by millions of organizations today....


