How to Choose a Ransomware Prevention and Protection Solution
Ransomware is a type of malware that restricts access to data or a computer system, usually by encrypting it, and demands a ransom payment from the victim to restore access. The demand often includes a time limit, with the risk of data being lost forever or the ransom amount escalating if the payment is delayed.
The history and evolution of ransomware demonstrate the severity of the issue. The earliest ransomware attacks simply demanded a ransom in exchange for the encryption key needed to regain access to the affected data or use of the infected device. The first ransomware attack was carried out with AIDS Trojan Horse by evolutionary biologist Dr. Joseph Popp in 1989. He demanded as little as $189 in exchange for the decryption key.
Modern ransomware attacks have increased both in severity and ransom payment amounts. In 2024, the mean ransom payment was estimated at $3,960,917. One of the severest ransomware attacks of the last decade was the attack on Colonial Pipeline. In response, the company paid the $5 million ransom and halted pipeline operations for almost a week, resulting in fuel shortages and prompting a state of emergency in 17 states.
Figure 1 below demonstrates the evolution of the ransomware threat over the past two years.
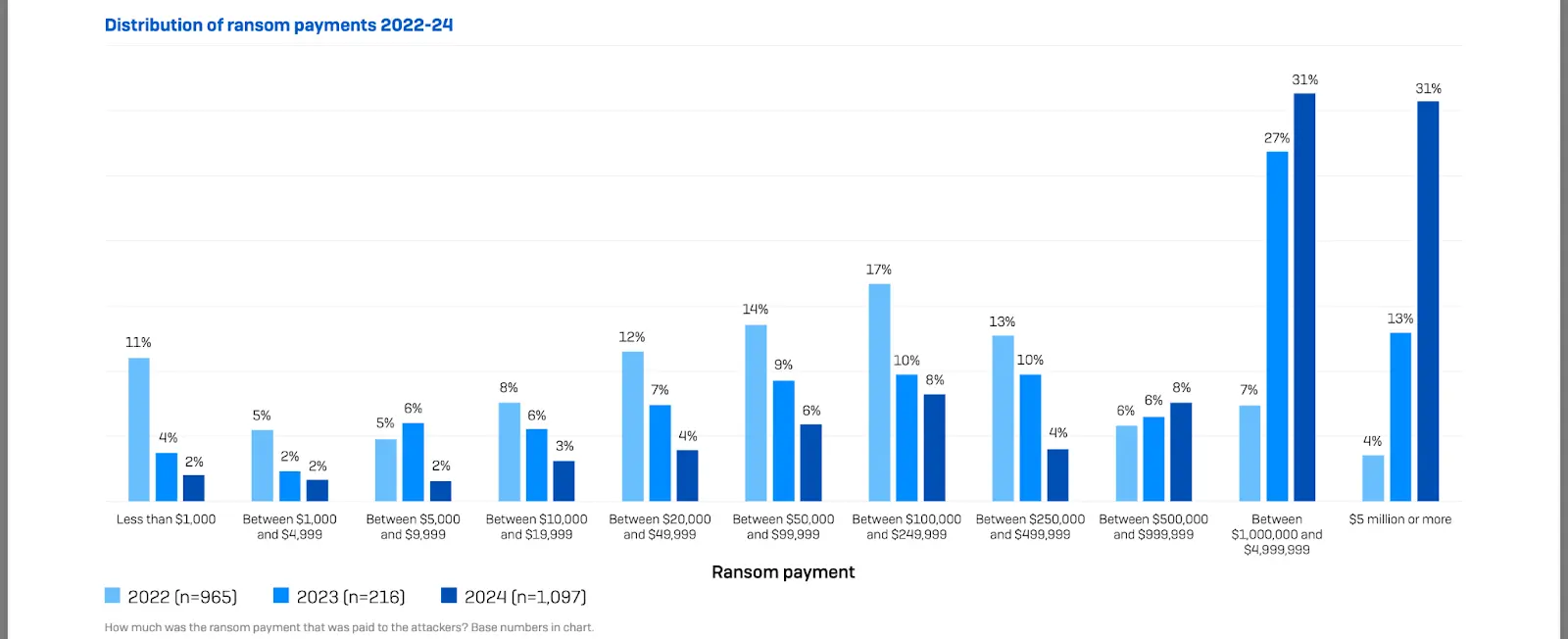
Figure 1 Distribution of ransom payments 2022-24 by Sophos State of Ransomware 2024
In recent years, ransomware trends have evolved to include double-extortion and triple-extortion tactics that raise the stakes considerably. The former involves the threat of stealing the victim’s data and leaking it online. At the same time, the latter threatens to use the stolen data to attack the victim’s customers or business partners. In addition, attackers often exploit the ransomware-as-a-service model, or RaaS, which involves hackers providing the ransomware tools and infrastructure to other cybercriminals on a subscription basis. These “clients” pay to use the ransomware to carry out attacks, often sharing a percentage of the ransoms with the service providers.
Hopefully, organizations can limit the possibility of a ransomware attack along with damages that could arise if one occurs by making regular or continuous data backups, protecting common ransomware entry points, and performing continuous detection and monitoring. Alternatively, they can choose an all-in-one ransomware prevention solution that integrates all these capabilities, offering an enhanced level of security. Let’s see how to choose the best one.
Importance of Ransomware Prevention and Protection
The best ransomware attack is the one that didn’t happen. The growing sophistication and frequency of ransomware attacks make proactive measures essential for protecting organizational assets. Ransomware attacks can have devastating financial and reputational consequences for businesses:
Financial and reputational damages
The immediate financial impact of a ransomware attack can be immense, including the cost of paying the ransom, potential fines for non-compliance, and the expense of recovering from the attack. Excluding any ransoms paid, in 2024, organizations reported a mean cost to recover from a ransomware attack of $2.73M. In addition to these direct costs, businesses may face significant revenue losses due to downtime, as operations are often halted until systems are restored. One-third (34%) of organizations now take over a month to recover.
In addition to financial losses, organizations face substantial reputational damages. Customers, partners, and stakeholders may lose trust in an organization that has suffered a breach, leading to a loss of business and a tarnished brand image.
Legal and compliance issues
Many businesses are subject to strict regulatory frameworks (e.g. HIPAA, GDPR, PCI DSS, CCPA, etc.) that mandate the protection of sensitive data. A ransomware attack can result in non-compliance with these regulations, leading to hefty fines and sanctions. Hence, businesses affected by ransomware may face legal action from clients, partners, or other affected parties. Nearly one in five (18%) ransomware incidents in the US led to a lawsuit, with data breaches being the primary reason for the ransomware lawsuits. For example, a technology company Accellion has paid an $8.1m settlement to resolve a legal claim relating to a data breach in December 2020. Additionally, organizations may be held liable for failing to adequately protect data, which also leads to costly settlements. For example, three lawsuits were issued against Colonial Pipeline. These included negligence, improper safeguards, breach of public duty, and violations of consumer protection statutes. However, all three of these lawsuits were dismissed.
Data integrity issues
Ransomware can compromise the integrity of data by encrypting it, making it inaccessible, or even corrupting it. Seven in ten (70%) ransomware attacks resulted in data encryption in the last few years (see Figure 2). In some cases, attackers may threaten to delete or release sensitive information, further compromising the integrity of the data. Even if the ransom is paid, there’s no guarantee that the data will be restored to its original state.
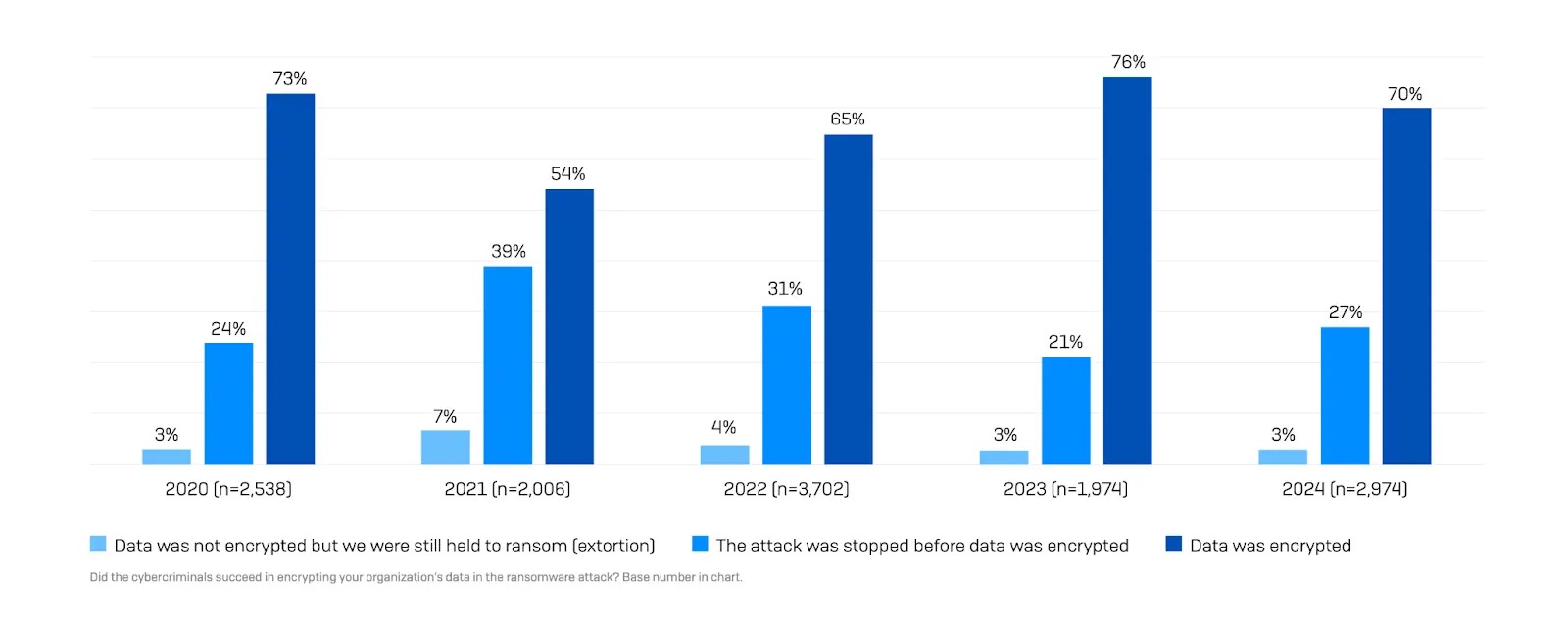
Figure 1 Data encryption rate by Sophos State of Ransomware 2024
Data integrity and availability are critical for business operations. Ransomware attacks can render essential data and systems inaccessible for extended periods, crippling business functions. The inability to access data disrupts daily operations and impairs decision-making, customer service, and overall productivity.
Therefore, ransomware prevention is a technical challenge and a comprehensive business imperative. By taking proactive steps to secure systems, educate users, and comply with legal requirements, organizations can significantly reduce the risk of falling victim to a ransomware attack.
Key Features of an Effective Ransomware Prevention and Protection Solution
An effective ransomware prevention solution integrates multiple layers of defense to protect an organization from the ever-evolving threat landscape. Below are the key features that contribute to a robust ransomware prevention and protection strategy:
Real-time threat detection and monitoring
Ransomware monitoring of core services proactively detects ransomware patterns and stops an in-progress ransomware attack, acting as your last line of defense. Use solutions with AI-powered capabilities to proactively detect any early signs of cloud ransomware attacks using behavior-based detection methodology. And remember organizations with security AI and automation identified and contained a data breach 108 days faster.
Backup and recovery
Effective ransomware prevention solutions always have regular backups to restore sensitive data to its pre-attack state. Having your backups compromised increases the complexity of recovering encrypted data while adding the overhead of creating and securing new, untainted backups. The median recovery costs were eight times higher for organizations with compromised backups, totaling $3 million compared to $375,000 for those without backup issues. So, a robust backup and recovery feature is a must for ransomware prevention solutions.
At the same time, not all backup solutions are created equal. Ideally, it must follow the 3-2-1 backup rule (3 copies of your backups stored on 2 different mediums, with at least 1 stored offsite), offer separate storage for SaaS data backups, and make long-term archived backups. Finally, backup and recovery solutions should include automated processes for regular backups, ensuring that data is frequently updated and available for restoration.
Endpoint protection
Strong foundational security includes endpoint, email, and firewall technologies. Endpoints (including servers) are the primary destination for ransomware actors, so an effective ransomware prevention solution must ensure that all organization’s endpoints are well defended. Security tools need to be correctly configured and deployed to provide optimal protection, so look for solutions that deploy out-of-the-box with straightforward posture controls. And remember, protection that is complicated and hard to deploy can quickly increase risk rather than reduce it.
Network segmentation
Limiting the spread of ransomware within an organization’s network is vital to minimizing damage. Network segmentation isolates different parts of the network, preventing ransomware from easily moving laterally and compromising multiple systems. By dividing the network into smaller segments, organizations can control access and restrict data movement between these segments—the same works with damaged asset isolation offered by ransomware prevention solutions. Damaged files are isolated once a ransomware attack is detected, preventing further encryption of your SaaS data. This containment strategy makes it more difficult for ransomware to increase, thus reducing the overall impact of an attack.
How to Choose a Ransomware Prevention
Let’s say a few words about choosing a good ransomware prevention solution for your business. Generally speaking, it is standing on five whales that include reputation, updates, scalability, integration, and cost-effectiveness. Let’s dive deeper into all of them.
Reputation and experience-Strong reputation, extensive expertise, and customer trust are the core attributes of a good ransomware prevention solution provider. Reputable vendors have a proven track record and deep industry knowledge, allowing them to stay ahead of evolving threats and provide cutting-edge protection.
Regular updates—Regular updates are essential to defend against the constantly evolving tactics of cybercriminals. These updates ensure that the latest security patches, threat intelligence, and detection mechanisms are in place to identify and block new ransomware strains. Without regular updates, your system may become vulnerable to attacks, increasing the risk of data breaches and financial loss.
Scalability and flexibility—Ransomware prevention solutions must be scalable and flexible to effectively support a growing business and adapt to an evolving threat landscape. As organizations expand, their security needs increase, requiring solutions that can seamlessly scale without compromising performance.
Integration with existing systems—Smooth integration with existing IT infrastructure is crucial A solution that integrates smoothly with current systems ensures minimal disruption and maximizes efficiency, allowing for streamlined deployment and management.
Cost vs Value – When choosing a ransomware protection solution, consider the cost, value, and specific business needs. Small businesses might benefit from more affordable solutions that still offer essential protection, while larger organizations may require higher-cost options with advanced features and regular updates. Balancing cost with effective protection tailored to your business ensures optimal value and risk management.
Comparing top Ransomware Prevention Solutions
If your company has embraced cloud data storage, breaches will become an inevitable reality. Investing in a ransomware protection solution that best fits your needs is one of the imperative steps to better securing your data and having a reliable backup at your disposal in a crisis.
With various solutions, features, and pricing packages available, it is essential to evaluate each option thoroughly, but don’t wait for a breach to occur to realize you need a plan.
| SpinAI | Rubrik | SysCloud | Veeam | |
| Automated regular backups | ✅ | ✅ | ✅ | ✅ |
| Continuous monitoring and alerting | ✅ | ✅ | ✅ | ✅ |
| AI-powered threat detection | ✅ | ✅ | ||
| Immutable, unlimited storage | ✅ | |||
| Automated ransomware recovery | ✅ | ✅ | ||
| Microsoft 365 | ✅ | ✅ | ✅ | ✅ |
| Google Workspace | ✅ | ✅ | ✅ | ✅ |
| Salesforce | ✅ |
SpinRDR – a fully automated AI-powered ransomware detection solution (recommended)
Spin Ransomware Detection and Response (SpinRDR) is a fully automated ransomware detection solution that offers complete visibility over SaaS data and immediate incident response. Live environment scanning and instant remediation it offers can cut business downtime from one month to under two hours and lower recovery costs by more than 90%. In addition, SpinRDR offers:
- automated regular backups for mission-critical SaaS applications;
- continuous monitoring and alerting;
- advanced AI-driven threat detection and mitigation;
- granular backup management and regional backup options.
Take advantage of flexible, subscription-based pricing to select the ideal solution for your cloud environment. Request a demo to explore the full potential of SpinRDR.
The only limitation it has is that it is limited to Google Workspace, and Microsoft 365.
Check out customer reviews on G2
Rubrik – a solution with an in-house storage vault
Rubric is one of the leaders of enterprise backup and recovery software solutions with a unified platform for data management, backup, and disaster recovery. It offers continuous monitoring of risks to your data, including ransomware, data destruction, and indicators of compromise. It is an easy-to-manage tool with solid performance and scalability. Along with these features, Rubric offers:
- simplified data protection with policy-driven automation;
- instant data recovery and cloud mobility;
- comprehensive security and compliance features;
- data storage through an in-house storage vault, outside of AWS, GCP, or Azure.
Rubrik does have a few limitations, such as a complex setup process, a challenging licensing model, and higher costs compared to other vendors. Additionally, its third-party application protection is primarily limited to Microsoft 365.
Nevertheless, Rubrik offers customizable subscription pricing based on an organization’s specific requirements, enabling companies to choose the most appropriate option.
SysCloud with unique solutions for K-12 schools and non-profits
SysCloud supports a wide range of backup applications, including QuickBooks and HubSpot. It can detect files encrypted by ransomware and restore safe versions using SysCloud-recommended files or selecting from all deleted files in the last safe snapshot. Additionally, it offers unique solutions for K-12 schools and non-profits. Among the other SysCloud’s key ransomware protection and backup features are:
- powerful search function to easily find content inside any email, file, or conversation;
- real-time data loss prevention, automated policy enforcement, and active compliance management;
- detailed audit logs and reporting.
However, SysCloud does have some drawbacks, such as a steep learning curve for new users and higher costs for additional features.
Its pricing is subscription-based, depending on the number of environments and users.
Veeam offers coverage for cloud, virtual, and physical environments
Veeam is a comprehensive backup and disaster recovery solution. It provides proactive management with real-time visibility for cloud, virtual, and physical environments. The high-speed recovery and data loss avoidance it provides make it a good and reliable ransomware prevention solution. The other Veeam’s features include:
- ability to choose storage options and types based on location and quality;
- advanced monitoring, analytics, and automation tools;
- secure zero-trust data protection with encryption and ransomware protection;
- high-performance backup and recovery;
- strong community and customer support network.
Among the main limitations are complex pricing, which is high for smaller businesses. Furthermore, it has a complicated integration process, so fully leveraging all features requires technical expertise.
The pricing is subscription-based with perpetual licensing options.
Conclusion
The best ransomware attack is the one that didn’t happen. Data leakage, financial and reputational damages, legal and compliance issues are a few things that may happen when an organization falls victim to a ransomware attack. While modern ransomware attacks have increased both in severity and ransom payment amounts, organizations are urged to take proactive measures to protect their SaaS data against ransomware. To protect sensitive data from ransomware, organizations need to make regular or continuous data backups, protect common ransomware entry points, and perform continuous detection and monitoring. Alternatively, they can choose an all-in-one ransomware prevention solution that integrates all these capabilities, offering an enhanced level of security.
Frequently Asked Questions (FAQs)
What is ransomware?
Ransomware is a form of malware that blocks access to data or a computer system, typically by encrypting it, and requires the victim to pay a ransom to regain access. The demand usually comes with a deadline, with the threat that the data may be permanently lost or the ransom may increase if payment is delayed.
How can I tell if my system is infected with ransomware?
The early signs and symptoms of a ransomware infection include the sudden inability to access files or systems, the appearance of ransom notes demanding payment, and unusual file extensions or encryption messages on your files. You may also notice a significant slowdown in system performance or the disabling of security software.
Is paying the ransom a good idea?
Deciding whether to pay a ransom is a complex matter. Most experts advise that one should only think about paying if all other solutions have failed and the data loss would cause greater harm than the payment.
There’s no certainty that paying the ransom will lead the attackers to follow their promise once they receive the money. Even if they do, obtaining decryption keys from them can be complex and time-consuming. Furthermore, it’s possible that the attackers could still keep a copy of the data after payment.
No generally applicable law prohibits individuals or organizations from paying the ransom (except when the ransom is demanded by entities on the U.S. Sanctions Lists). However, businesses should think twice before paying a ransom to adversaries, even if backups are compromised. For example, the U.S. Department of the Treasury says in their ransomware advisories that companies could face future legal trouble being involved in ransomware payments. FBI does not support paying a ransom in response to a ransomware attack because it just escalates the problem.
What should I do if I fall victim to a ransomware attack?
If you fall victim to a ransomware attack, immediately disconnect the infected device from the network to prevent the spread of malware. Contact your IT or cybersecurity team for support. Report the incident to relevant authorities and restore your system from the most recent backup. Finally, a thorough security assessment must be conducted to identify vulnerabilities and prevent future attacks.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...

