How to Fix SaaS Security Issues with Working Remotely
Since the beginning of 2020, organizations have seen a tremendous shift to a remote workforce, enabling employees to have the flexibility to work from home. Unfortunately, the change to a majority remote workforce has also introduced an increased risk of cybersecurity threats. Employees may work from home on insecure networks, personal devices, and other aspects that may not be desirable from a security perspective. Remote employees are also generally laxer in their security hygiene, working in the comforts of home. How can businesses fix main SaaS security issues and maintain good security posture and hygiene with the remote workforce, including securing cloud SaaS environments?
Shift to remote work
There is no question that businesses worldwide have shifted to a remote and hybrid workforce across the board in response to the onset of the global pandemic in early 2020. It has led to a digital transformation for most businesses and how they empower remote workers with the communication and collaboration tools needed to carry out business-critical tasks remotely.
This shift to a majority remote workforce has accelerated the migration of organizations to cloud Software-as-a-Service (SaaS) environments such as Google Workspace and Microsoft 365. These hyperscale cloud service providers have the infrastructure and software solutions to easily consume remote work productivity, communication, and collaboration tools as a simple subscription service for each user.
These modern cloud SaaS solutions provide the technology platform that makes it easy for employees to consume productivity and collaboration tools over a simple browser connection from any device or any network. With these easy access capabilities, businesses can be aligned to solve modern remote and hybrid workforce challenges.
As with any technology solution, attackers are quick to look for ways to compromise business-critical data. While cloud SaaS allows easy access to data for remote workers, it can also introduce security concerns for a business’s remote workforce management.
Cloud SaaS security issues and vulnerabilities related to remote work
Today’s digital world is full of cybersecurity threats and risks to business-critical data. What vulnerabilities are a direct result of the remote workforce? These include but are not limited to the following:
- Insecure remote networks and devices
- Third-party cloud SaaS applications
- Phishing, ransomware, and data breaches
1. Insecure remote networks and devices
The security boundary has now extended to the remote workforce environment with the largely remote workforce, including home networks and devices. Thus, traditional workplace security boundaries are no longer effective. As a result, remote employee networks may be highly insecure.
Suppose employees can use BYO (bring your own) devices for accessing the sanctioned cloud SaaS environment. In that case, these are more likely to have malware or other security risks outside traditional corporate endpoint management control.
2. Third-party cloud SaaS applications
One of the appealing components of cloud SaaS environments is access to third-party cloud SaaS applications. Google Workspace and Microsoft 365 offer access to a rich catalog of thousands of third-party applications. These can augment cloud SaaS services with additional capabilities and functionality beyond the native features included.
However, with third-party cloud SaaS applications, there is also the risk of SaaS security threats. For example, attackers targeting cloud Saas may masquerade a malicious application as a legitimate or helpful cloud SaaS utility or some native cloud SaaS “update.” In addition, unsuspecting end-users may grant high-level permissions to cloud SaaS applications without much scrutiny.
When employees grant permissions to cloud SaaS applications, they are handing over an OAuth token to the application. This OAuth token allows the cloud SaaS application to perform actions with the same level of permissions as the user. These permissions may include reading, writing, modifying, or even deleting data.
A malicious application granted a legitimate OAuth token by a user can read business-critical or sensitive data, delete it, or ransomware-encrypt the data. OAuth tokens, by design, even bypass other security measures such as two-factor authentication and must be manually revoked as they do not expire.
Businesses must have a solid solution for visibility and control over third-party cloud SaaS applications and specify which applications can be integrated with the environment.
3. Phishing, ransomware, and data breaches
Remote employees are often more distracted and susceptible to phishing and ransomware attacks than employees working on-premises. Data breach risks are also enhanced with the remote workforce. According to the IBM Cost of a Data Breach 2021 report, note how remote work changes the dynamics of cybersecurity and the cost of a data breach.
The average cost was $1.07 million higher in breaches where remote work was a factor in causing the breach, compared to those where remote work was not a factor. The percentage of companies where remote work was a factor in the breach was 17.5%. Additionally, organizations that had more than 50% of their workforce working remotely took 58 days longer to identify and contain breaches than those with 50% or less working remotely. IT changes such as cloud migration and remote work increased costs, yet organizations that did not implement any digital transformation changes as a result of COVID-19 experienced $750,000 higher costs compared to the global average, a difference of 16.6%.
With cloud SaaS environments, the impact of remote work follows this same trend. As a result, workers may be more apt to be responsible for cybersecurity breaches due to increased distractions, insecure networks, and BYO devices. As a result, businesses today must have highly robust cybersecurity defenses that protect cloud SaaS environments from ransomware and data leak threats.
Bolster security for the remote workforce cloud SaaS environment
When accessing business-critical SaaS resources, businesses must maintain good security posture and hygiene with the remote workforce by using reasonable security practices and enforcing policies that help keep the cloud SaaS environment secure. Also, organizations must ensure they have good backups of their data to protect against data mishaps of remote employees.
SpinOne is a robust data protection and cybersecurity solution for modern cloud SaaS environments, including Google Workspace and Microsoft 365. SpinOne allows businesses to have visibility and control over data sharing, user activity, and third-party cloud SaaS applications in a seamless single-pane-of-glass dashboard.
Using SpinOne, organizations can bolster remote work environments using cloud SaaS in the following ways:
- Create automated backups of cloud SaaS data
- Have visibility to cloud SaaS and SpinOne events
- View and control cloud SaaS data sharing
- Automatically audit and control third-party cloud SaaS applications
- Proactively protect the cloud SaaS environment from ransomware
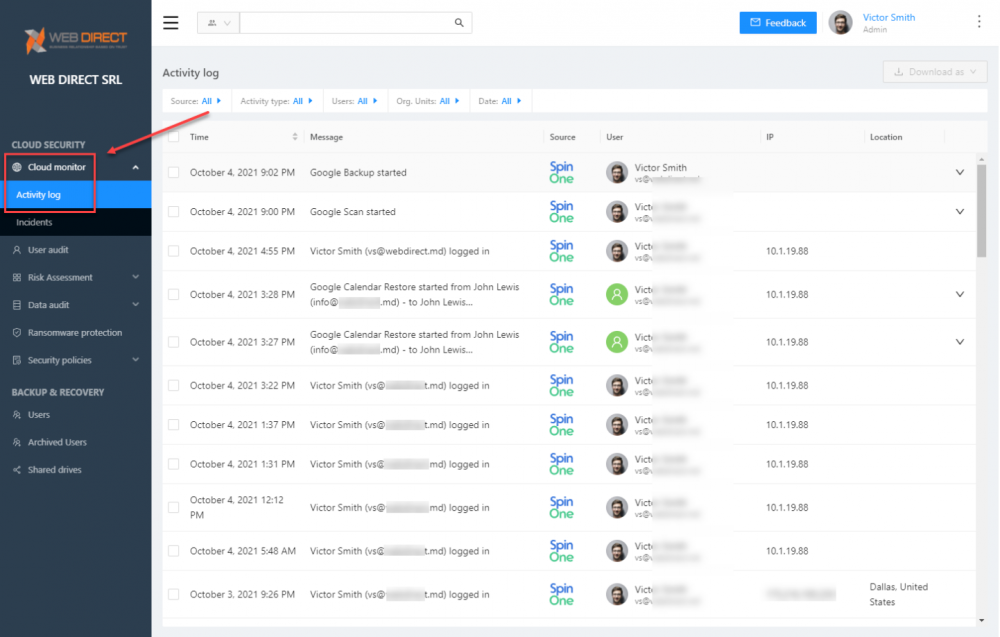
Cloud monitor and the Activity log dashboard provide detailed visibility into user activities and other cloud SaaS events.
Cloud monitor Activity log
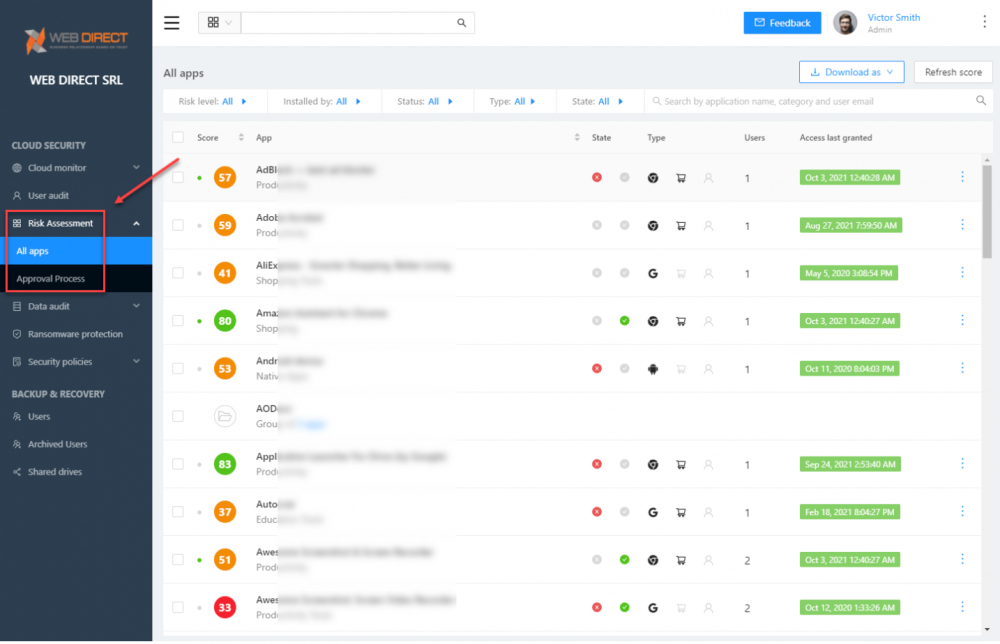
The SaaS Application Risk Assessment dashboard allows organizations to see any third-party cloud SaaS application integrated into the environment. SpinOne immediately performs a risk assessment of all installed third-party applications. Next, it rates the applications with a security score based on cybersecurity and reputation metrics. SpinOne continues to audit applications even after the initial scoring has been completed. It ensures that if the application behavior changes in the future, this will be visible and can even be blocked from SpinOne policies.
In addition, the Risk Assessment provides an intuitive and seamless workflow and approval process for cloud SaaS applications requests from end-users.
SpinOne SaaS Application Risk Assessment dashboard
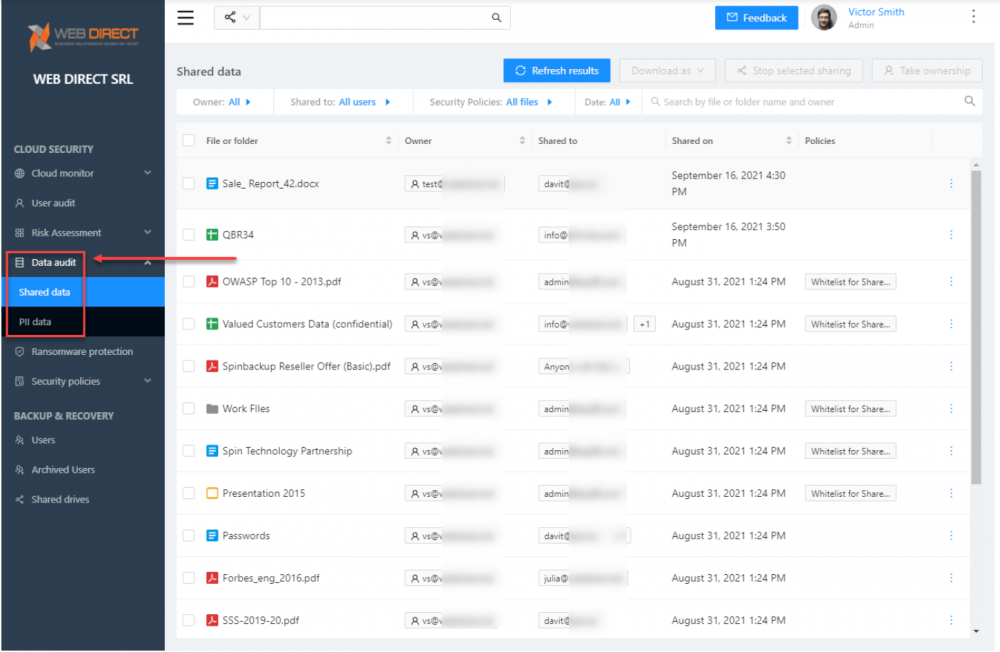
Gain visibility to data shared outside the cloud SaaS environment. SpinOne allows quickly seeing all data shared inside and outside the organization. It includes details such as which file or folder, owner of the data, who it is shared with, when it was shared, and applicable SpinOne policies.
SpinOne Data audit dashboard with visibility to cloud SaaS shared data
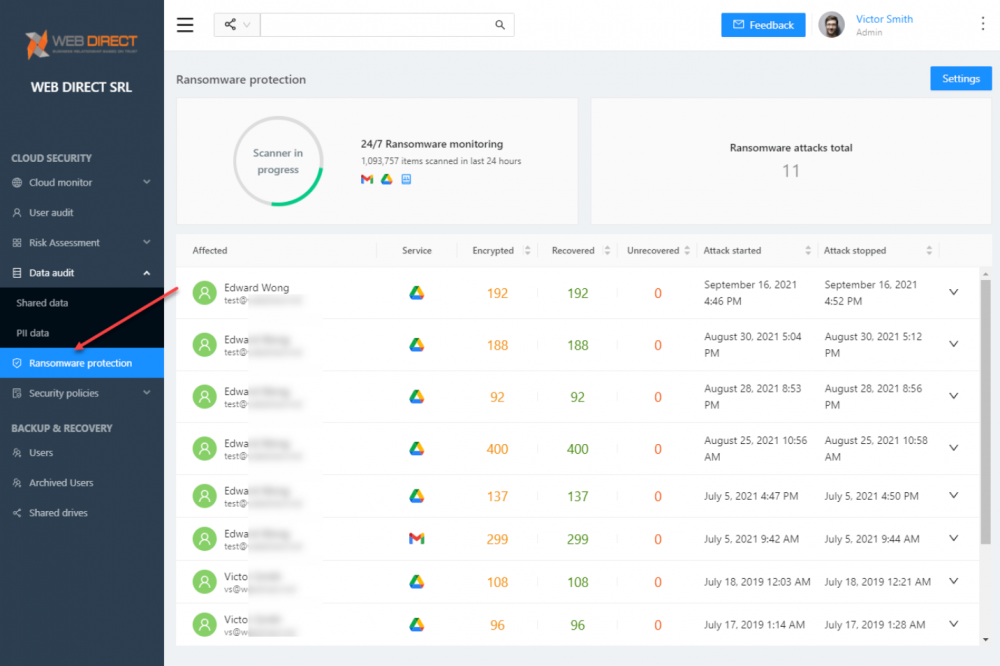
SpinOne provides industry-leading ransomware protection. The SpinOne Ransomware Protection module is proactive and uses artificial intelligence (AI) and machine learning (ML) to combat ransomware attacks in your environment. Note the following security automation used by SpinOne to protect your environment from ransomware.
- SpinOne continuously scans for the signs of ransomware attacking the environment
- If ransomware is detected, SpinOne forcibly removes the network connection from the ransomware process
- It performs scans of the environment to find affected files
- Any affected files found are automatically recovered from the last good SpinOne backup (configurable)
- It automatically notifies administrators of the attack and remediation.
SpinOne ransomware protection
Backing up cloud SaaS data is extremely important with the remote workforce. Data can accidentally or maliciously get deleted by an end-user, malicious application, or attacker. SpinOne provides enterprise-grade data protection with automated backups of cloud SaaS services multiple times per day. It allows recovering data granularly or in bulk as needed. This capability is used intelligently with other SpinOne solutions such as Ransomware Protection.
SpinOne provides backups of cloud SaaS environments
All of these data protection and security tools are essential with businesses leveraging cloud SaaS environments that empower their remote workforce. With new threats and cybersecurity risks threatening cloud SaaS environments, SpinOne allows businesses to leverage the cloud effectively to overcome modern communication, collaboration, and productivity challenges.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...