How to Remove Ransomware If Your Files Got Corrupted
- How to Detect a Ransomware Attack
- How to Remove the Ransomware
- How to Remove Ransomware Depending On the Type
- Screen Locker Ransomware (Blockers)
- Crypto Ransomware (Encryptors)
- Responding to Ransom Demands: A Practical Advice
- How to Protect Your Data From Ransomware Using SaaS Ransomware & Response Tools
- How to Protect Your Data From Ransomware Using SaaS Ransomware & Response Tools
- Bulletproof SaaS Data Protection With SpinOne
Facing ransomware can be a nightmare scenario for anyone. Whether you’ve experienced encrypted files or a locked screen, the prospect of paying to retrieve access may seem daunting. However, despite the frustration, there are actionable steps you can take to tackle the situation head-on.
As a SaaS data protection company, we help companies restore their data corrupted by ransomware every day. However, simply restoring your data without eliminating the source leaves you vulnerable to future attacks.
That’s why we’ve put together this comprehensive guide to help you not only regain access to your files but also eliminate the malware responsible for the encryption. Within this article, you’ll discover various ransomware removal tools, along with valuable tips and tricks. By reading through to the end, you’ll not only learn how to remove the ransomware virus but also gain insights into essential preventive measures to safeguard against future attacks.
How to Detect a Ransomware Attack
Our data is as valuable as gold, but given that 68% of cyberattacks worldwide were ransomware, the stakes have never been higher.
A ransomware attack can strike in the blink of an eye, lock away your important information, and demand a ransom for its release.
Fortunately, however, early detection mitigates the risk. Here’s how you can spot one before it spirals out of control.
Signature
Every piece of malware has its unique signature containing indicators like domain names and IP addresses. Signature detection compares these markers against a library of known threats.
While this method is straightforward, it’s not foolproof. That’s primarily because the world of malware is constantly changing, and attackers can create new variants for every strike.
So, in case a signature doesn’t get recognized, the system remains vulnerable.
Behavior
Unlike signature detection, this method takes a more proactive approach. Put simply, it focuses on what the malware does rather than what it looks like.
For instance, ransomware typically exhibits telltale behaviors like opening a slew of files and rapidly encrypting them. Behavior-based detection can monitor these unusual activities and alert you to potential threats.
Abnormal Traffic
Ransomware attacks are often two-pronged. First, they encrypt your data. Next, they exfiltrate it before locking you out.
This way, they create a double whammy and lead to unexpected spikes in data transfer because malicious software sends your information to remote servers.
Although these attacks are sneaky, abnormal traffic detection keeps an eye on network activity. It looks for any unusual patterns that might indicate a breach. As soon as it spots a suspicious data transfer, it traces the traffic back to its source.
As such, you can quickly identify – and eliminate – the threat before it wreaks havoc.
Options Upon Detection
So, you’ve detected a ransomware attack; now what?
The clock is ticking, and your data is hanging in the balance. Knowing your options can help you make an informed decision when faced with this pressing situation.
- Pay the Ransom: Let’s start with the most controversial option. Paying the ransom may seem tempting, especially when your data is time-sensitive. However, it’s no less than a gamble. Sure, some attackers release your files, but there’s no guarantee they’ll keep their word. What’s worse, paying them could make you a future target. As the CEO and Co-Founder of Halcyon, Jon Miller, mentions, “In more than half of the scenarios where you pay, you get ransomware again within the next year.” Plus, it fuels the ransomware economy, which means more attacks.
- Use Specialized Tools to Remove Malware: Another option to fight back is using specialized ransomware removal tools. They can help decrypt your files without feeding into attackers’ demands. But again, this strategy might not be as effective since some ransomware strains are pretty advanced (even the best tools may struggle to keep up). However, if you catch the attack early, there’s a chance to regain control without shelling out any cash.
- Reset to Factory Settings: When all else fails, you might need to consider the nuclear option: resetting your device to its factory settings. While this might help with ransomware removal, it also means losing data that wasn’t backed up.
How to Remove the Ransomware
Once you’ve been hit by ransomware, every second counts. Quick action can mean the difference between a manageable recovery and a crisis. So, here’s how to take control and remove the menace before it spreads further chaos.
Isolate the Infected Device
The moment you realize you’ve got ransomware on your hands, treat it like a fire alarm goes off (evacuate and contain the threat as soon as possible).
Disconnect the infected device from everything. That means pulling the plug on network cables, switching off Wi-Fi and Bluetooth, and logging out of any external storage or cloud accounts.
Otherwise, ransomware will quickly leap onto your entire network. So, the faster you isolate it, the better your chances of keeping the infection contained.
Identify the Ransomware Type
You need to identify the type to figure out your options for ransomware removal. Consider using a tool like ID Ransomware to match the symptoms with a known ransomware variant.
Some ransomware can be cracked with decryption tools – others, not so much. So, knowing what you’re facing will give you a clearer path forward.
Remove the Malware
Now, pick the best ransomware removal tool to run a full scan on your system. However, remember the security software might be able to quarantine or even completely remove the ransomware from your device.
Also, be sure not to rush this step, though. Let the software do its thing. If the scan successfully wipes out the malware, congratulations! But don’t celebrate too soon; you’re not in the clear yet.
Restore from a Clean Backup
This is where your backup strategy matters. Hopefully, you’ve been regularly backing up your data because when ransomware locks your files, backup is your only safe zone.
But before you go ahead and restore anything, double-check that the ransomware is fully removed and that your backup files are safe.
The last thing you want is to reintroduce the malware onto a clean system!
How to Remove Ransomware Depending On the Type
Ransomware comes in different forms, and how you handle it depends on the type you’re dealing with. So, the first step is knowing whether you’re up against Screen Locker Ransomware (blockers) or the more dangerous Crypto Ransomware (encryptors).
Screen Locker Ransomware (Blockers)
Screen Locker ransomware hijacks your screen and makes it impossible to access your computer or certain applications. This type of malware often pretends to be a message from law enforcement. It claims that your device has been locked due to illegal activities.
Thankfully, however, it doesn’t mess with your files or system; it only locks your screen.
So, while it does give you a frustrating experience, it’s not a catastrophic one.
How to Remove Screen Locker Ransomware
Screen lockers can be stubborn but are relatively easier to defeat. Here’s how ransomware removal for this attack works.
- Restart in Safe Mode: This will boost your system with only essential functions and block the malware from launching. Once in Safe Mode, the ransomware should be temporarily disabled.
Use Ransomware Removal Tools: A reliable ransomware removal tool can locate and delete screen locker malware. Make sure your antivirus is up to date, though, and consider running a full system scan. A tool like Kaspersky can be your go-to here.
Crypto Ransomware (Encryptors)
This is where things get serious.
Crypto ransomware locks your device and, beyond that, encrypts your files and restricts access until you pay a ransom. This payment is often requested in untraceable cryptocurrencies and promises to provide the decryption key.
The bad news is that if you don’t have a backup, crypto-ransomware can cause irreversible damage to your data.
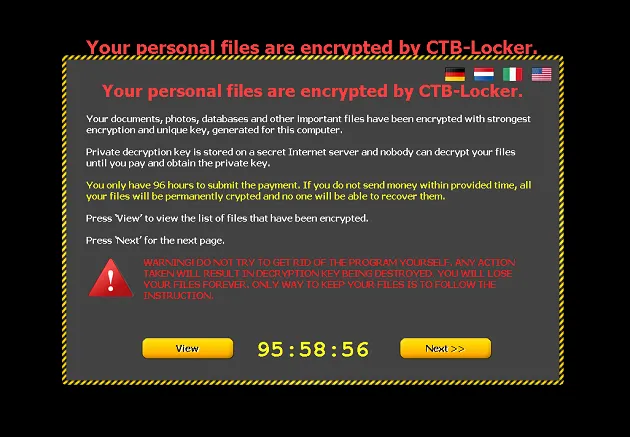
How to Remove Crypto Ransomware
The process for removing crypto ransomware depends on whether you have a backup or not. Here’s a quick breakdown.
Ransomware Removal With Backup
If you have a backup of your files, you’re in much better shape. Here’s what you need to do.
- Neutralize the Malware: Before you start restoring anything, you need to eradicate the ransomware from your system. Consider tools like AVG, Kaspersky, and McAfree to conduct a thorough scan. The key here is to clean out every last trace of the malware.
- Restore Your Backup: Once you’re certain everything is clear, it’s time to bring your files back. This might take time, depending on the speed of your internet and the size of your backup. But your device will soon be back to its pre-ransomware glory.
Ransomware Removal Without Backup
If you find yourself in the unfortunate situation of having no backup, don’t throw in the towel just yet. Here are some steps to consider.
- Identify the Ransomware Strain: Knowledge is power, and this is where you need to use it. Figure out what type of ransomware has attacked your system. Tools like ID Ransomware or Crypto Sheriff can help you in this regard. Knowing the specific ransomware variant can help you devise a successful counter-strategy.
- Remove the Malware: Use the best ransomware removal tool to sweep your system clean. This is your chance to take back control and oust the malware. Remember, a clean slate is important before recovering any files. Otherwise, you might just invite the malware for a second round.
- Find a Decryptor: Here’s where the situation can get a little more dicey. If luck is on your side, a decryptor might already exist for the ransomware that has infiltrated your system. Websites like NoMoreRansomware have some free decryption tools for specific ransomware strains. If you manage to find a match, you could potentially recover your files without paying a cent to those dastardly criminals.
- Decrypt Your Files: Once you’ve secured a decryptor, the actual decryption process begins. In case you can’t find a decryptor that works for your situation, your options start to dwindle. You might have to consider waiting for a cybersecurity expert, or, as a last resort, pay the ransom. Just be warned that paying doesn’t guarantee you’ll receive the decryption key.
While many advise against paying the ransom, sometimes circumstances push you to the edge: pay up or risk losing your data forever.
Responding to Ransom Demands: A Practical Advice
Unfortunately, many businesses – especially small to medium-sized ones – aren’t equipped to survive a ransomware attack. There’s a reason why a staggering 60% of these companies go under within six months of an attack.
If you find yourself without a backup and downtime is not an option, the grim reality is that paying the ransom may seem like the only lifeline.
In case you decide to take that risky plunge, keep these points in mind.
Verify Their Claims
Before you hand over any money, confirm that the hackers genuinely have the means to decrypt your files.
As a rule of thumb, ask them to decrypt a small sample of your data. If they refuse, consider it a red flag.
Their inability to comply suggests they might not be able to help you after all.
Negotiate
Believe it or not, you often have room to haggle over the ransom price. So, reach out through the contact information they provided and don’t hesitate to negotiate. Here’s why:
- Oftentimes, hackers prefer to receive something rather than nothing. So, a little back-and-forth might lead to a reduced price.
- If you’re going to take the plunge, negotiating the lower amount at least minimizes your financial hit (especially if they ultimately don’t deliver a decryption key).
- Showing that you’re not going to comply with their initial demands right off the bat signals they won’t get a blank check from you.
This tip, however, might not work for larger enterprises since cybercriminals are less likely to budge on their ransom demands.
How to Protect Your Data From Ransomware Using SaaS Ransomware & Response Tools
Having a backup isn’t quite enough to keep your data safe. Sure, it makes up for a solid protection strategy, but if those backups aren’t connected to your primary data, they can become targets, too.
So, besides frequent backups, keep these tips in mind.
Automated Ransomware Protection: Ransomware protection tools can monitor your system for suspicious activity and intercept it before it gets a chance to cause disruption. So, consider installing a reliable tool on your device.
Knowledge Is Your Shield: A popular adage goes like this, “What you don’t know can hurt you.” When it comes to ransomware, ignorance can be a disaster. So, take the time to educate yourself (and your team) about the latest ransomware tactics. Share articles, hold workshops, and bring in experts to talk about the risks. The more informed everyone is, the better you’ll be to fend off attacks.
Two-Step Authentication: Adding a two-step authentication alerts you if someone tries to enter your system without permission. Therefore, implementing a second form of verification means you’re making it exponentially harder for attackers to gain access, even if they’ve got your password.
Stay Updated: Those pesky update notifications can be annoying, but trust us when we say it: ignoring them can cost you in the long run. So, regularly update your operating system to keep hackers at bay; your future self will thank you.
Antivirus and antimalware are must-haves. These systems are your frontline defenders against cyber threats. They quickly scan your system for signs of trouble and give you much-needed protection. Make sure your organization has a policy that prioritizes using reliable security software. After all, it’s better to be safe than sorry!
How to Protect Your Data From Ransomware Using SaaS Ransomware & Response Tools
Having a backup isn’t quite enough to keep your data safe. Sure, it makes up for a solid protection strategy, but if those backups aren’t connected to your primary data, they can become targets, too.
So, besides frequent backups, keep these tips in mind.
- Backup Regularly: Backing up your data is important, but make sure your backups are separate from your main data to avoid them becoming targets.
- Use Automated Protection: Install ransomware protection tools that can spot suspicious activity and stop it before it causes problems.
- Enable Two-Step Authentication: This adds an extra layer of security. It alerts you if someone tries to access your system without permission, making it harder for attackers.
- Keep Software Updated: Don’t ignore update notifications. Regularly updating your operating system helps protect against hackers.
- Install Antivirus and Antimalware Software: These are essential for defending against cyber threats. They scan for issues and keep your data safe, so ensure your organization uses reliable security software.
Bulletproof SaaS Data Protection With SpinOne
If juggling multiple security measures feels like a hassle, it’s time to simplify. SpinOne offers an all-in-one solution that keeps an eye on, secures, and backs up your Google Workspace and Microsoft 265 data.
Besides keeping you compliant, it also cuts down on IT costs, and given that business expenditures are always sky-high, who wouldn’t want to save money while keeping their data safe?
Solid Backups
Rest assured that your essential SaaS data is locked down with daily, secure cloud-to-cloud backups. Whether once or thrice a day, SpinOne’s got your back by securing your critical files safely.
Compliance? Check.
Peace of Mind? Check.
Smart, Automated Policies
Keeping control of your data doesn’t have to be an uphill battle. With SpinOne, you can automate policy-based rules over third-party apps and data sharing. For instance, it lets you set alerts for any strange logins or large file downloads, allowing you to act fast before any real damage is done. This means you’ll always stay ahead of the curve.
Protect Your Sensitive Data
Sensitive information falling into the wrong hands? Not on our watch! SpinOne’s proactive tools are designed to prevent data leaks, so you never have to worry about breaking compliance. Keep it secure, always.
Misconfiguration Management
One slip-up in your app settings can open the floodgates for unauthorized access. However, our misconfiguration management keeps your system watertight against security risks, whether you use Google Workspace, Slack, or Microsoft 365.
SpinOne: Your All-In-One Defense
SpinOne lets you reduce downtime, prevent data leaks, and streamline compliance efforts across Salesforce, Google Workspace, Microsoft 365, and Slack. Besides keeping you compliant, it also cuts down on IT costs.
Given that business expenditures are always sky-high, who wouldn’t want to save money while keeping their data safe?
Click here to request a free demo of SpinOne!
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...

