Log Management in Cloud SaaS: Best Practices
Capturing logs is one of the most basic cybersecurity processes. Logged events from servers, firewalls, network switches, client workstations, and other equipment can provide the information needed to track down a cybersecurity breach or prevent one altogether. That’s why log management has become critical for cybersecurity of an enterprise.
Just about any device on the network keeps log files. Harvesting and managing these log files are essential for visibility and overall security. However, what about cloud SaaS environments? Today, businesses migrate core business-critical data and services to cloud SaaS, such as Google Workspace and Microsoft 365. Disparate logging across cloud SaaS services can be a challenge. Why is this the case? How can businesses solve the challenge of disparate logging in cloud SaaS?
Why log management is important for cybersecurity
Modern appliances, network devices, servers, clients, and other devices generally keep log files detailing all activity taking place. An attacker attempting to compromise your network generally leaves clues behind that are captured in the log files. These clues may include:
- Abnormal login events
- Odd source geolocations
- Logins outside regular business hours
- Access or attempted access to unsanctioned data
Often, these events are captured in log files that exist in the environment. Cybersecurity professionals, who know what to look for, can see events and information in log files that stand out as abnormal. In addition, security professionals can aggregate and put together log files across different devices to see each step an attacker takes as they move throughout a compromised network.
The sheer volume and breadth of logging detailed in even moderately-sized environments can be enormous. As a result, a significant challenge for security teams is disparate log files. Logging across various devices, clients, servers, and network hosts can be overwhelming and infeasible to search and monitor manually. Therefore, security teams often use on-premises tools that aggregate log files from multiple sources, allowing a single collection of log files from various locations.
Logging is equally vital in cloud Software-as-a-Service (SaaS) environments as businesses are now leveraging these more than ever for their core critical services and data storage. For security and compliance, organizations must have visibility and an audit trail of end-user activity, data sharing, and abnormal activities that may constitute malicious attempts to compromise the environment.
Logging important in remote work environments
Since the COVID-19 pandemic began in 2020, many organizations now have at least 60% of their employees working remotely, with many organizations continuing to operate in a majority hybrid workforce layout. Unfortunately, while remote work has provided the flexibility needed, it also increases cybersecurity risks.
In IBM’s Cost of a Data Breach 2021, it was noted that businesses utilizing remote workers had a higher than average cost associated with data breaches. In addition, the study pointed out the need to have deeper visibility into suspicious activity on the company and bring your own (BYO) laptops, desktops, tablets, mobile devices, and IoT, including endpoints the organization doesn’t have physical access to.
Remote work configurations highlight the need for log monitoring for remote employees, data they access, and user activities. Organizations must also closely monitor any cloud SaaS resources the employees are accessing. So, again, good logging across the board is necessary.
Disparate logs across SaaS applications
As mentioned earlier, a significant challenge to SaaS cybersecurity today is disparate logs across SaaS applications. Native cloud SaaS cybersecurity tools, logging, and other solutions leave a lot to be desired. Organizations may find themselves navigating across multiple dashboards, log files, and events information to find pertinent log files. In addition, each cloud SaaS application accessed may have its own logging and audit trail that needs to be examined for forensic purposes.
While cloud service providers have added unified logging solutions, such as in Microsoft 365’s Compliance Center, there are limitations based on the type of subscription and specifically the type of license assigned to specific users. Notice the following details provided by Microsoft regarding logging based on assigned licenses:
- When an audited activity is performed by a user or admin, an audit record is generated and stored in the audit log for your organization. The length of time that an audit record is retained (and searchable in the audit log) depends on your Office 365 or Microsoft 365 Enterprise subscription, and specifically the type of license that is assigned to specific users.
- For users assigned an Office 365 E5 or Microsoft 365 E5 license (or users with a Microsoft 365 E5 Compliance or Microsoft 365 E5 eDiscovery and Audit add-on license), audit records for Azure Active Directory, Exchange, and SharePoint activity are retained for one year by default
- For users assigned any other (non-E5) Office 365 or Microsoft 365 license, audit records are retained for 90 days.
What if your business needs to align logging with a different set of requirements? Looking at the Google Workspace solution, Google provides Google Workspace audit logging information that writes audit logs across various log files, including:
- Google Workspace Enterprise Groups Audit
- Google Workspace Admin Audit
- Google Workspace Login Audit
- Admin Activity audit logs
- Data Access audit logs
It means the Google Workspace administrator or SecOps team has multiple log files containing important security information when these need reviewing, which complicates security efforts.
Truly unified and seamless log management in cloud SaaS environments
Organizations looking for unified security logging in cloud SaaS environments not limited by time constraints, licensing, or multiple disparate log files, can find the native logging in Google Workspace and Microsoft 365 challenging. SpinOne is a robust cybersecurity solution that helps businesses increase their cybersecurity posture for cloud SaaS environments by enabling the visibility, controls, and logging needed for audit and security purposes.
SpinOne aggregates the necessary logs, audit tools, data protection, and data security tools in a single solution that saves time, simplifies operations, and streamlines cybersecurity skills required for cloud SaaS security operations.
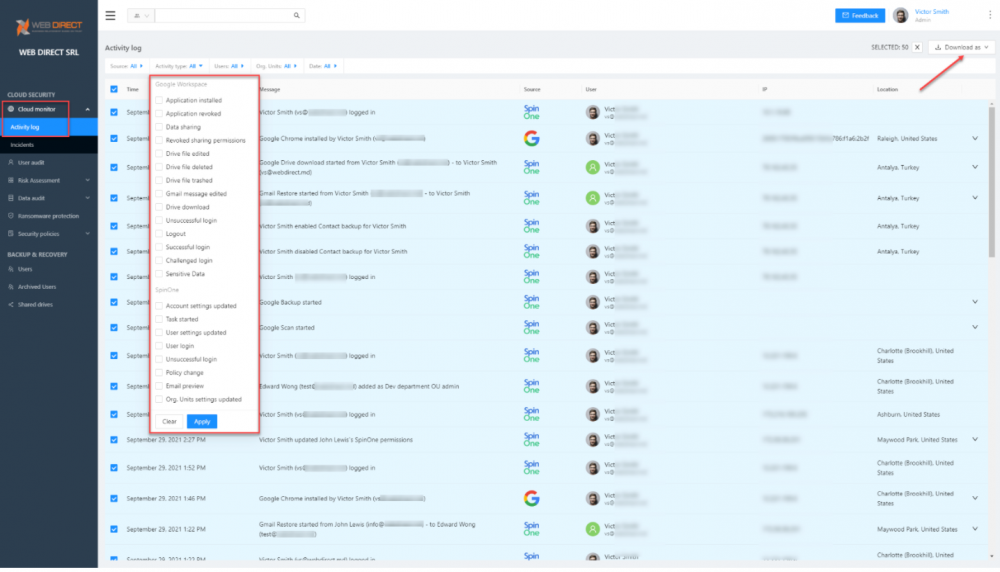
The SpinOne Cloud Monitor Activity log dashboard provides a comprehensive log of both cloud SaaS provider logging and SpinOne events in a single-pane-of-glass view for cloud SaaS administrators, SaaSOps, or SecOps professionals. Note the wide range of events found in the Activity type filter.
SpinOne Cloud Monitor Activity log provides unified logging
In addition to Cloud Monitor, which provides an overall unified view of user activities, SpinOne also provides a powerful data audit dashboard that logs data sharing in the cloud SaaS organization. It offers pertinent details such as the file or folder shared, owner, shared to, shared on, and policies applied. In addition, it also gives quick visibility to PII data such as credit card numbers shared via email.
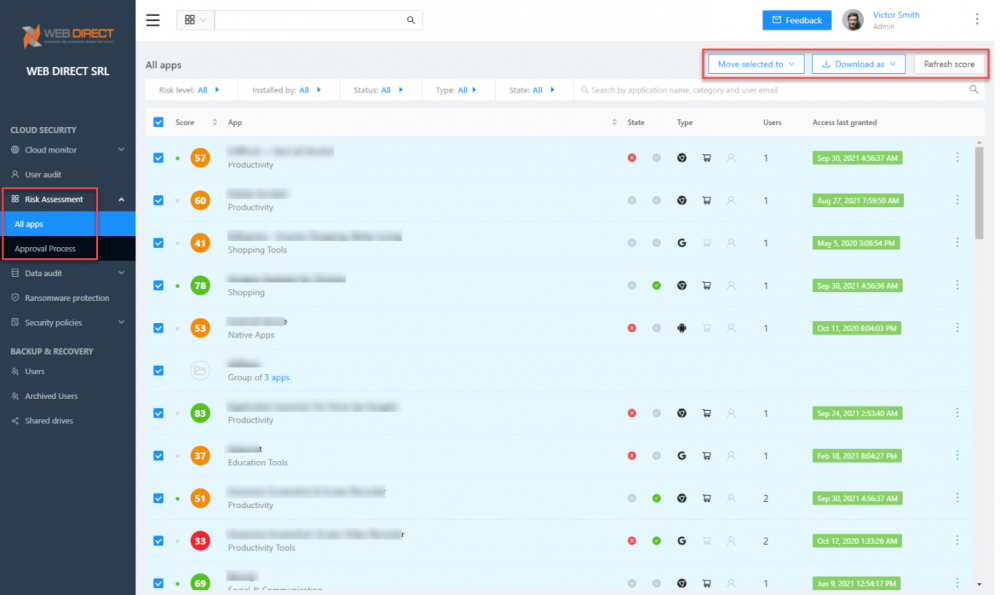
Logging which cloud SaaS applications have access to your cloud data is essential for compliance and security. Therefore, SpinOne logs the app, type, and users installed in the sanctioned cloud SaaS environment.
Risk assessment logging for cloud SaaS apps
All information logged by SpinOne dashboards is exportable for reporting and other security and auditing tasks, such as compliance. Click here to learn more about SpinOne logging capabilities and see how your organization can improve your SaaS security posture management using SpinOne.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...