Microsoft 365 Ransomware Recovery for Businesses
Microsoft 365 is one of the key SaaS solutions in a business’ tech stack. Losing this data can damage operations, and cause downtime and financial losses. In this post, we talk about Microsoft 365 ransomware recovery.
Understanding Ransomware Attacks in Microsoft 365
The number of ransomware attacks has been steadily growing over the past decade. In Q1 2023, we’ve seen a surge in reported attacks on businesses reaching as high as 45 per month. Many companies and governmental organizations were in havoc after these incidents. What is ransomware and why is it so devastating to business?
Ransomware is a type of malware that encrypts the information stored in an IT environment. The hackers then trade this information for the decryption key, and some organizations and individuals decide to pay ransom to get their data back.
Can ransomware infect the Microsoft 365 environment?
In general, Microsoft 365 is believed to be a secure SaaS application. And it indeed has many security features to protect the environment from a ransomware attack on several levels:
- Tenant level.
- Service level.
- The level of developers & service infrastructure.
However, it can be targeted and successfully hit by a ransomware attack. Cloud ransomware usually disguises itself as a legitimate third-party application. Once it gets OAuth access to the victim’s environment along with the editing permissions, it begins encrypting the local files.
Microsoft 365 and Shared Responsibility Model
Not only is Microsoft 365 vulnerable to ransomware, but the developer will hold no responsibility for the incident leaving it entirely on the mistake of your security team and your employees.
Similarly to Google Workspace, Microsoft 365 has a shared responsibility model. This means that the tool’s developer is not responsible for the incidents that happened due to the mistake or malicious action of the client’s users.
Unfortunately, a ransomware attack in most cases is the result of a successful social engineering attack on the victim.
Learn more about Microsoft 365 security from our MSO 365 Security Checklist.
Steps for Microsoft 365 Ransomware Recovery
If you do not have a ransomware protection tools that detects ransomware, stops the attack, and recovers automatically, you will have to take the following steps:
1. Stop the attack
Once you have detected the attack on your environment you need to find the source of the ransomware attack and revoke its access to your Microsft 365. Usually, it’s some risky OAuth application with editing permission. Go to Microsoft 365 Admin Center, find the app, and revoke its access.
2. Take legal action
Inform law enforcement of your country and your legal department. We strongly suggest against paying the ransom. First, it’s illegal in some countries. Second, you reinforce the criminal behavior. Third, criminals understand that you can be easily coerced into paying and will target you again. Up to 50% of victims who paid ransom were targeted for the second time. Fourth, after paying ransom and getting a decryption key, most organizations fail to fully recover their files.
3. Study the ransomware
Chances are low but you might be lucky to get infected by some old strain that doesn’t encrypt the file versions. As a result, your employees can recover the previous versions of their files.
Next, search for the decryption key online. Once again chances are slow that you are infected by an old strain. However, it’s always worth trying your luck. There are white hat hacker organizations that provide decryption keys online. They’ll need a file and a part of a decrypted text to identify the strain.
4. Initiate the investigation
You need to understand how ransomware infected your Microsoft 365 environment. Most likely it was a mistake made by an employee who fell for a social engineering attack. However, it can be the result of a lack of control over Shadow IT, a zero-day attack on the authorized app, or a man-in-the-middle attack.
5. Check your environment
Many hackers prefer to spend some time in your environment to leave the “back doors” they could use to repeat their attack. Remember, that social engineering steals the credentials from your employees, so your attacker might be controlling the user account. You need to make sure that all the entry points are closed.
6. Start data recovery
Restore your data from your backup. It will take a while, as Microsoft 365 has API call limitations. Depending on the amount of data you store there, it can take days, weeks, or even months. Usually 2-3 weeks.
7. Acquire ransomware protection
Ransomware protection is the best way to defend your Microsoft 365 against ransomware.
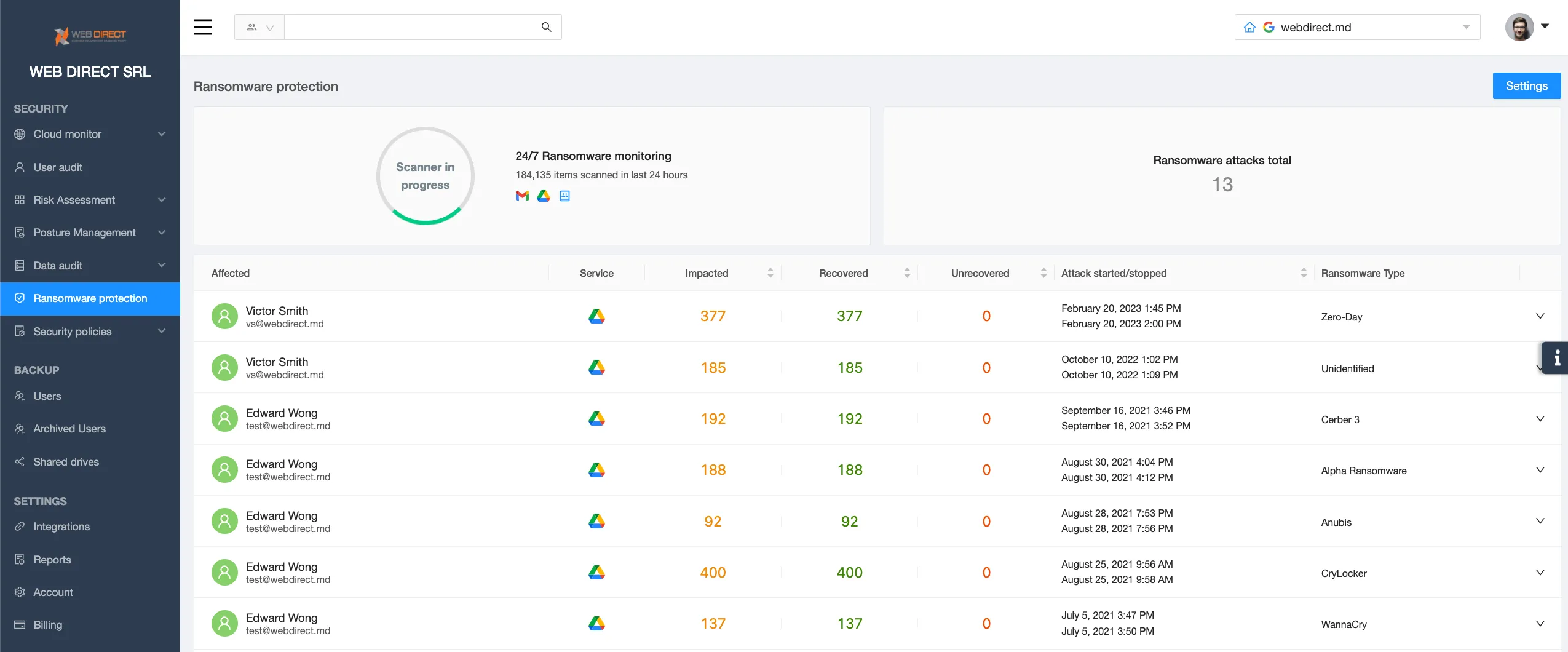
Ransomware Protection for Microsoft 365
Ransomware protection is the best way to address the issue of rampaging ransomware incidents. This is a category of tools that automate attack detection, termination, and recovery.
There are two main types of ransomware protection:
1. The legacy solutions that use historical data about previous attacks for detection and recovery. Unfortunately, ransomware is a type of malware that can easily be designed. As a result, new strains emerge every several months and most legacy solutions cannot keep up with this pace.
2. AI-based tools that analyze traffic or data behavior to detect the attack. The best method is to detect data behavior, as traffic analysis has too many false positives, especially at the peak of a business day.
SpinOne is a ransomware protection tool that uses the data analysis method. The in-built AI can detect and stop a ransomware attack within minutes after it has begun. As a result, the majority of cloud data in the environment remains intact.
After the attack termination, SpinOne initiates the recovery of the files that have been decrypted from its own remote backup. The downtime with this ransomware protection lasts only a couple of hours. This is 99% faster than a several weeks-long recovery after the attack on the unprotected Microsoft 365 environment.
FAQ
What should I do if I suspect a ransomware attack on my Microsoft 365 data?
Disable all the applications that have access to your Microsoft environment, inform law enforcement and begin recovery from backup or with the help of a decryption key.
What steps are involved in containing the spread of a ransomware attack within my Microsoft 365 environment?
The steps involved in containing the spread of a ransomware attack within my Microsoft 365 environment are:
- Stop the attack
- Take legal action
- Study the ransomware
- Initiate the investigation
- Check your environment
- Start data recovery
- Acquire ransomware protection
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...


