SaaS Application Security for Achieving Compliance
When it comes to shadow IT, “what you can’t see can certainly hurt you.” It is especially true when it comes to the security and compliance of your business-critical data. Shadow IT is a term coined to represent activities outside of the “view” or “knowledge” of IT and security operations. For an organization today, shadow IT is dangerous as it opens a business up to all kinds of security and compliance issues.
Cloud SaaS applications have exploded in popularity among organizations today, increasingly supporting remote workers since the onset of the global pandemic. However, shadow IT is a risk that also affects cloud SaaS environments. Let’s look at SaaS application security and see how organizations can achieve compliance in cloud SaaS environments.
Why is shadow IT a threat to compliance?
Compliance regulations require businesses to have the guardrails to protect, secure, and provide the availability of business-critical and sensitive data. To do that, organizations need to know the applications that interface and access the data under compliance.
Shadow IT encompasses anything from a technology perspective not sanctioned, tested, secured, and fully vetted by IT and security operations. These technologies may include hardware, software, and applications. Quite often, especially in cloud SaaS environments, shadow IT involves end-users using unsanctioned cloud applications.
Typical risk assessments and security testing are not performed when shadow IT cloud SaaS applications are used. As a result, it leads to end-users violating existing compliance and governance guidelines. More importantly, shadow IT puts organizations at risk for the possibility of violating regulations, including PCI-DSS, GDPR, HIPAA, SOX, and others, exposing them to severe penalties and fines.
As an example of just how severe the penalties and fines can be, the General Data Protection Regulation (GDPR) fine for non-compliance can be up to 4% of an organization’s global revenue or €20 million, whichever is greater.
It can also lead to the severe consequences of a data breach. When IT and security operations lose control over the software and applications used in an environment, business-critical data is at a much higher risk of being exposed by Shadow IT applications.
According to the IBM Cost of a Data Breach Report 2021:
Data breach costs rose from $3.86 million to $4.24 million, the highest average total cost in the 17-year history of the report
“Since shadow IT applications have not had the proper risk assessments performed, it is unknown how data is accessed, secured, or even transmitted. Unfortunately, not all software providers treat security in the same regard. As a result, applications may be “leaky,” exposing data unnecessarily. In addition, they may not use the proper encryption protocols for transmitting or storing data securely. They may also request higher levels of permissions than are needed.”
Shadow IT operations in cloud SaaS environments shed light on a bigger problem for organizations. A lack of control and governance. If employees can install and integrate third-party applications the business does not know of, this is an even bigger problem, showing a lack of proper visibility, audits, and controls.
Cloud SaaS application risk assessment
As mentioned, one of the dangers of shadow IT is the lack of risk assessments performed on applications that may be unknowingly used in an unsanctioned way by end-users or departments. On the other hand, one of the tremendous benefits of using cloud SaaS environments is access to thousands of third-party applications.
Most organizations have issues with shadow IT, security, and compliance due to the lack of visibility and control to third-party cloud SaaS applications. For example, with Google Workspace Marketplace apps, the default setting allows users to install any app available in the Google Workspace Marketplace as noted in the manage Google Workspace Marketplace apps KB here.
For organizations that are serious about Google Apps Security and compliance, this default setting is risky. Letting any end-user install any application available on the Google Workspace Marketplace or the Microsoft 365 AppSource is asking for shadow IT activities that bring about all the compliance risks already mentioned.
Instead of carte blanche access to marketplace apps, a smarter approach from a security and compliance perspective allows only specific applications to be installed. Only after an application passes a proper risk assessment can it be installed by an end-user.
However, performing a proper risk assessment on thousands of cloud SaaS apps would be tedious, time-consuming, and infeasible. In addition, while both Google Workspace and Office 365 Data Security and Risk Assessment have provided tools to allow or ban apps, these are not automated. Therefore, organizations must take advantage of automated risk assessment tools to properly scrutinize cloud SaaS applications.
Cloud SaaS application access management
Closely tying into automated risk assessments, businesses must scrutinize the access to the applications given to end-users in the cloud SaaS environment and the data access given to an application. Cloud service providers such as Google and Microsoft recommend this approach.
In the Google Admin Console, IT admins can select from the following three options:
- Allow users to install any application from Google Workspace Marketplace—Allows users to install these apps.
Block users from installing any app from Google Workspace Marketplace—Blocks users from installing these apps. In the Marketplace, the Approved for you section highlights to users that their organization approved no apps. - Allow users to install only allowed applications from Google Workspace Marketplace—Users can only install apps from your allowlist. In the Marketplace, the Approved for you section highlights to users the apps that are allowed.
- By using an allowlist of sanctioned applications, organizations can provide the guardrails needed for ensuring only third-party cloud SaaS applications are approved for installation in your organization. Microsoft provides a tool to manage OAuth permissions for apps so organizations can have visibility to the OAuth permissions granted by end-users.
While a step in the right direction, the tools provided by Google and Microsoft lack the security automation and orchestration needed to help businesses make automated security and compliance decisions and have these orchestrated automatically. Organizations need third-party tools to properly implement cloud SaaS application access management in their cloud SaaS environments.
Security policy orchestration
The sheer size and depth of cloud SaaS environments require automated solutions related to security and compliance. Manual processes are no longer feasible and practical to maintain proper visibility and enforce policy-based controls. Security policy orchestration is a term that is often associated with network firewalls and firewall policy changes.
In the realm of network firewalls, security policy orchestration provides:
- Centralized management
- Unified visibility
- Automation-assisted orchestration
- Streamlined audits, change tracking, and policy violation visibility and reporting
Security policy orchestration in the context of cloud SaaS provides similar capabilities, including automated management and visibility to user activities, data sharing, and application auditing and controls. However, many organizations find using the native cloud SaaS security and compliance tools are not enough. These often lack the security automation and orchestration needed to manage security and compliance in cloud SaaS environments effectively.
Third-party solutions that leverage artificial intelligence (AI) and machine learning (ML) capabilities can help businesses have automated security intelligence. For example, AI and ML processes can quickly and efficiently spot dangerous behaviors from users and applications. Also, this provides the opportunity for policy orchestration when needed in an automated fashion, depending on behaviors and other activities.
Cloud SaaS application monitoring
Another point to consider is the risk assessment, and application monitoring process should happen continuously, not just one time. Applications may be safe at a point in time. Then later, the application may become “leaky” or lax in its security implementation.
Monitoring has been described as the “lifeblood” of effective cybersecurity. Therefore, effective cloud SaaS security and compliance must include monitoring on all fronts, including cloud SaaS applications. It should include continuous risk assessments, data access, permissions granted, users who have installed the apps, and other aspects.
Businesses need continuous visibility and application monitoring to know that applications remain safe from a security and compliance perspective. Unfortunately, the application monitoring provided by Google and Microsoft by default is basic. As mentioned earlier, with built-in tools, many of the audit processes and visibility to potential threats must be performed manually by a human looking at a dashboard.
SaaS application security with SpinOne
The points discussed above shed light on crucial requirements to effectively prevent shadow IT operations in their cloud SaaS environments. These include:
- Application risk assessments
- Controlled access to cloud SaaS applications
- Application monitoring
SpinOne is a SaaS Security Posture Management (SSPM) solution that provides organizations with the tools needed to effectively empower end-users with powerful third-party applications for productivity while at the same time ensuring security and compliance.
Note the following capabilities provided by SpinOne’s SpinAudit module for controlling cloud applications:
- Automated application risk assessments
- Review user activities across your domain
- Review how your data is being accessed and shared
- Blacklist/Whitelist applications
- Implement security policies
- Identify connected devices
SpinOne takes the heavy lifting out of application risk assessments and control by providing an automated security score for every single app that has access to your sensitive data. It uses an AI-based security assessment to provide organizations with a current view of the application’s security posture based on behavior, intent, access, reputation, and other metrics.
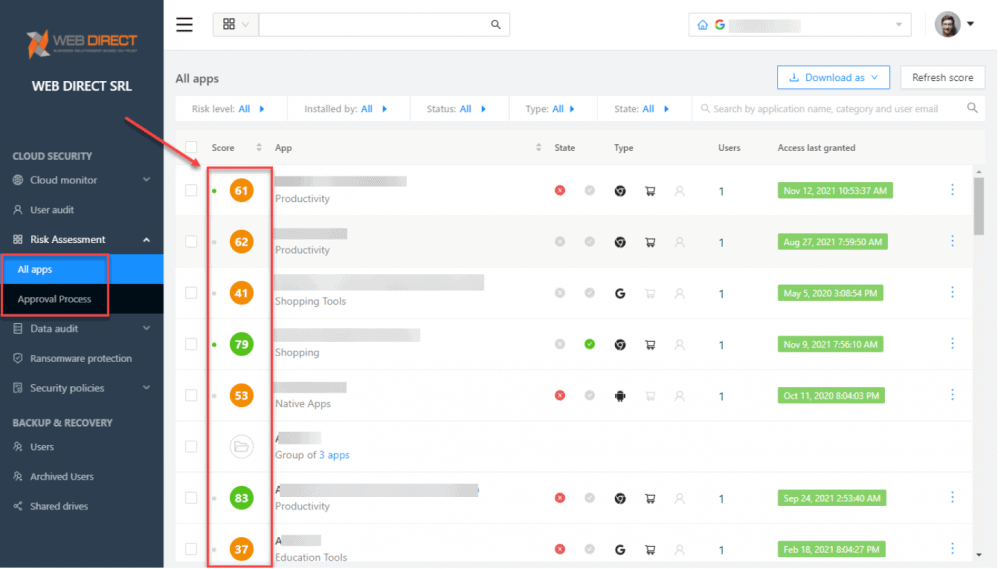
Using the SpinOne application score, admins can build security policies that automatically blocklist applications that have a security score below a configurable threshold. With this capability, SpinOne easily provides organizations with the tools needed for effective security policy orchestration that can control SaaS applications.
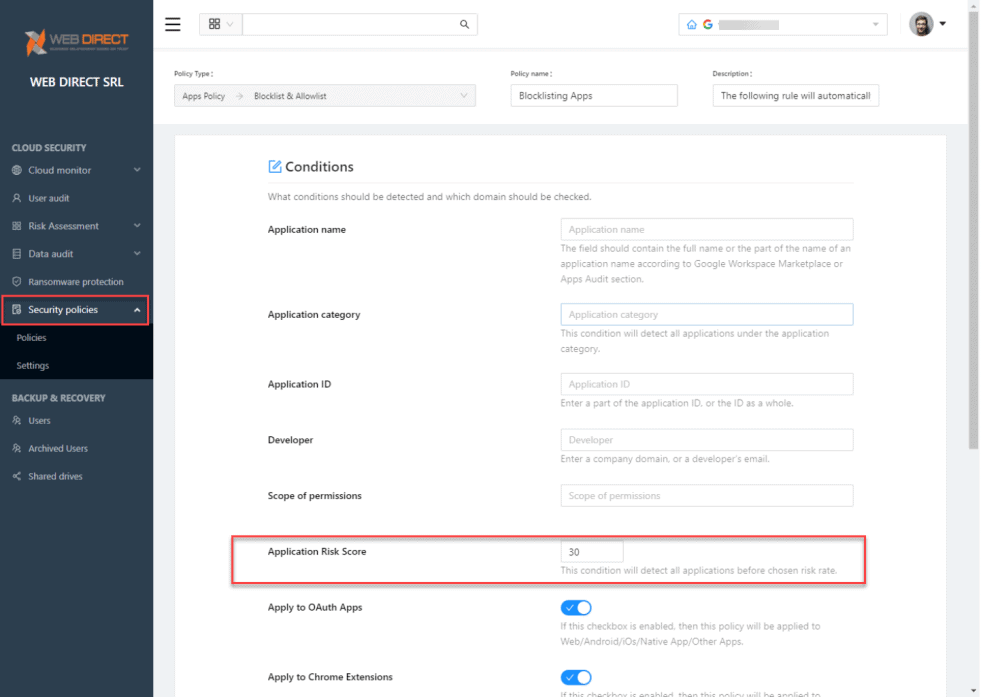
In addition to the automated risk assessment, SpinOne provides 24/7 monitoring and complete audit logging and activity history. It allows going back in time to investigate any suspicious activity from any fake app or malicious browser extension.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...

