Hidden Dangers You’re Overlooking in Your Chrome Extensions
Modern browsers provide tremendous capabilities to browse the web, manage passwords, download files, and interact with rich media content. In addition, like cloud SaaS environments, today’s browsers offer a large catalog of third-party software extensions and applications, easily integrated with the browser. Unfortunately, while these offer compelling capabilities to enhance browser capabilities and experience, they can lead to security vulnerabilities. Chrome, in particular, has seen a wide range of vulnerabilities. Let’s look at the hidden danger of Chrome extensions and how these can increase the risk for businesses.
The popularity of Google Chrome
Many browsers are available for desktop clients, laptops, tablets, and other mobile devices. These include Google Chrome, Mozilla Firefox, Safari, Microsoft Edge, and others. Arguably, Google Chrome remains the most popular browser used by clients today. It quickly gained popularity as a lightweight, quick, intuitive browser that appeals to the masses.
Despite other browser selections available to the community, many of today’s popular web browsers use the free and open-source web project known as Chromium, developed and maintained by Google. The codebase found in the Chromium project is the source of most Google Chrome code.
So, despite adding a few proprietary features between many of the predominant web browsers in the market, many browsers share the “Chrome DNA.” Popular browsers in this category include Microsoft Edge, Opera, and mobile browser solutions, including Samsung Internet.
Unfortunately, the success and popularity of the Chromium code base and engine have made it a significant target for attackers since the damage path is large.
Significant vulnerabilities
A new report released by Atlas VPN noted Chrome as the most unsafe browser in 2022, measured by the sheer number of vulnerabilities. According to the report:
- Chrome has the most reported vulnerabilities among other major browsers on the market, with 303 vulnerabilities discovered so far in 2022
- It is the all-time leader in vulnerabilities, with 3159 cumulative vulnerabilities
- Compared to Chrome, Mozilla Firefox had 117, and Microsoft Edge had 103, only a third of the vulnerabilities
- Opera was noted as the safest browser with “0” vulnerabilities so far in 2022, and only 344 all-time vulnerabilities
- Recent Chrome vulnerabilities include: CVE-2022-3318, CVE-2022-3314, CVE-2022-3311, CVE-2022-3309, and CVE-2022-3307
Don’t underestimate the risk of third-party extensions
With the popularity of Google Chrome and the vulnerabilities noted, organizations need to pay attention to the risks associated with using Chrome in the enterprise. This risk includes third-party Chrome extensions. With the underlying vulnerabilities found in Chrome, the risk of third-party extensions is amplified. Attackers can easily use malicious extensions to capitalize on new security vulnerabilities found in the browser.
In addition, unrelated to the vulnerabilities themselves, hackers can use malicious extensions to compromise credentials and carry out OAuth abuse for Chrome extensions that integrate with cloud Software-as-a-Service (SaaS) solutions like Google Workspace or Microsoft 365.
As a result, these factors result in an elevated risk profile for organizations due to the wide range of modern browser features and extensions found in browsers like Chrome. It underscores the need for the following:
- Make sure all clients are running the latest version of Chrome – New Chrome releases contain patches for newly discovered security vulnerabilities. Ensure your business has a strategy for keeping end-user applications and productivity tools updated, even for remote employees.
- Control third-party Chrome Extensions – Attackers can leverage malicious extensions to compromise passwords, leak data, and compromise cloud SaaS environments. The hidden danger of Chrome extensions can introduce tremendous risks for organizations. It is also a springboard for Shadow IT operations.
- Control data sharing – Ensure your organization has visibility and control over which data is shared and who it is shared with, especially for cloud SaaS environments.
- Visibility of user activities – Organizations need to maintain visibility of end-user activities and actions, including data sharing, which cloud SaaS apps they are installing, etc.
Protect your organization against dangerous Chrome Extensions
One of the challenges to ensuring your data is safe in cloud SaaS environments like Google Workspace and Microsoft 365 is controlling third-party applications. Unfortunately, modern cloud SaaS environments make it extremely easy for users to install and use third-party applications without the visibility and consent of IT. As a result, users can easily become involved in Shadow IT operations and potentially expose the business to security and compliance risks.
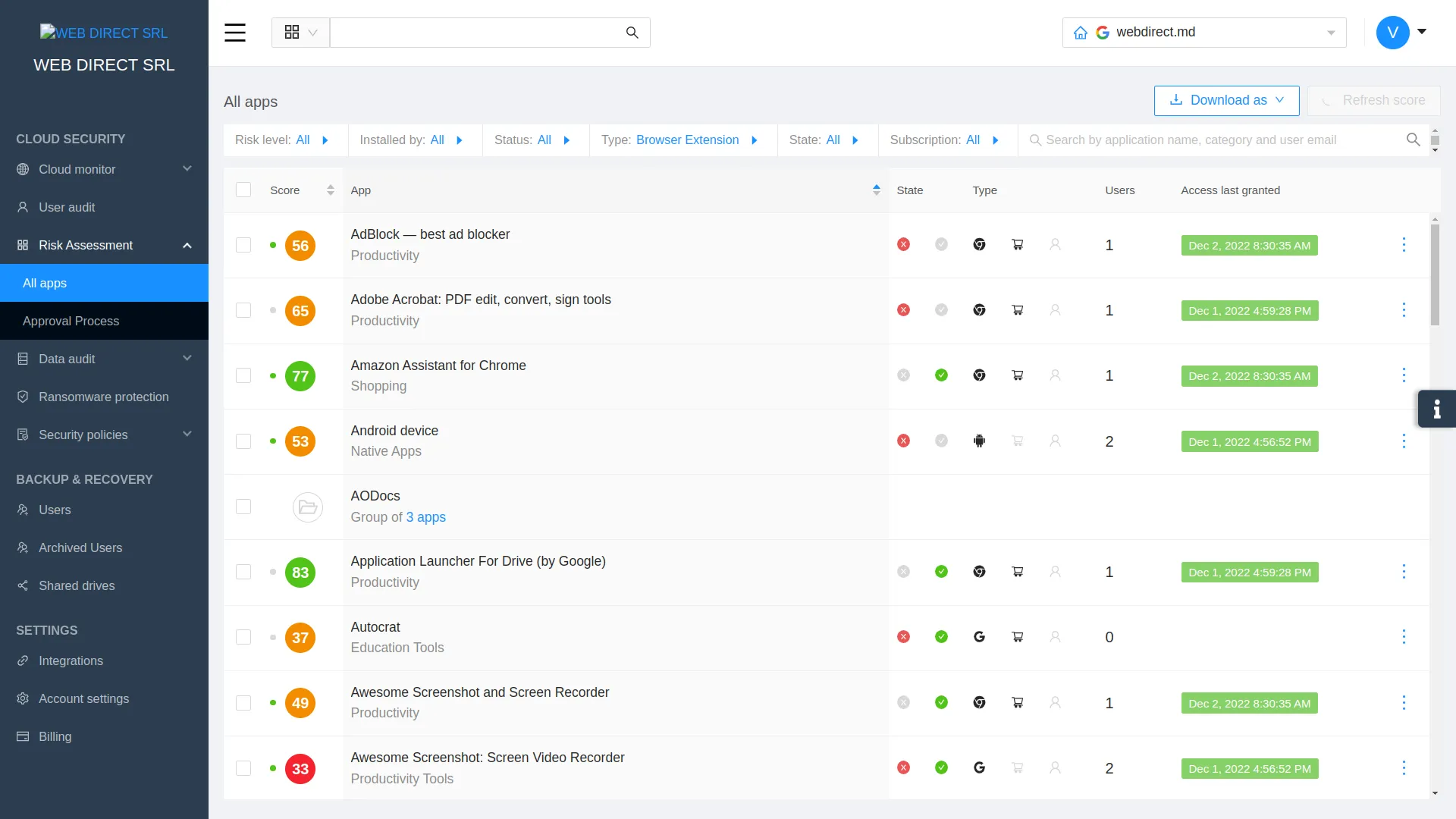
Spin.ai provides a robust cybersecurity and cloud security posture management (CSPM) solution that provides admins visibility and control over the dangers of third-party Chrome Extensions and cloud SaaS applications. It allows organizations to have automated risk assessment capabilities to reduce the impact of zero-day attacks and meet compliance challenges.
Using artificial intelligence (AI) and machine learning (ML), Spin gathers data from different sources to outline the possible business, security, and compliance risks posed by various applications.
With Spin.ai, you can:
- Block risky third-party applications and browser extensions
- Perform automated risk assessments of cloud SaaS applications and browser extensions
- Automate allowed applications based on automated scoring from SpinOne
- Only allow access to compliant applications
Click here to learn more.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...

