Securing Remote Workforce. Ultimate Guide for IT Admins
Beginning in early 2020, the global COVID-19 pandemic has totally changed the way organizations and their employees are doing work. With social distancing and other mandates, most businesses have shifted to a remote work layout for employees, allowing employees to carry out business-critical tasks remotely. To efficiently accomplish this and provide end-users with the resources they need to communicate, collaborate effectively, and access data, many businesses have migrated to cloud Software-as-a-Service (SaaS) environments such as Google Workspace and Microsoft 365 (formerly Office 365).
Since the onset of the global pandemic, cyberattacks have skyrocketed and have placed laser focus on securing the remote workforce, including cloud SaaS environments. Let’s look at securing the remote workforce in an ultimate guide for IT admins and see how businesses can effectively empower remote users and embrace security.
How important is security today?
The onset of the global pandemic and the quick shift to a remote workforce was a perfect storm for hackers to capitalize on businesses unprepared to deal with the changed workflows, infrastructure, and remote access technologies now required for business productivity. It includes businesses that quickly migrated resources to cloud SaaS environments.
There is no question that security must be a critical objective of today’s organizations as the threat landscape continues to expand. Attackers are continuing to use malicious tools such as ransomware to compromise business-critical environments.
Alarming statistics in regards to ransomware in 2020
Have ransomware attacks increased in 2020? Note the following alarming statistics in regards to ransomware in 2020:
In a study carried out by security firm Sophos:
- 51% of businesses suffered a ransomware attack in 2020
- 25% of companies made payments to hackers in response to the ransomware attack
- By mid-year 2020, ransomware attacks thrived during the COVID-19 pandemic, increasing 72%
- The FBI saw a 400% increase in reports of cyberattacks since the start of the pandemic
High-profile ransomware attacks, such as the one carried out on Blackbaud in May 2020, have led to tremendous fallout not only for subsidiary organizations affiliated with Blackbaud but also the individuals whose data they maintain. Later in the year, the FBI, DHS, and HHS warned of the possibility of imminent ransomware attacks against US hospitals. Many hospitals were indeed targeted and hit with a ransomware attack, crippling operations.
As businesses continue in 2021 with the status quo of the distributed workforce, undoubtedly continuing into the foreseeable future, ransomware is still plaguing companies across many different industries. Just a couple of days ago, at the time of this writing, a massive ransomware attack shut down a major US pipeline, crippling a supply line of 45% of all fuel consumed on the East Coast of the US. It helps to underscore the importance for businesses to give needed attention to their cybersecurity objectives and put in place adequate ransomware protection security layers.
Ransomware protection needs to be proactive in nature as the traditional reactive approach to ransomware is simply not desirable for businesses in today’s highly digital world in which businesses live and die by data.
The security challenge for IT admins in 2021
IT and Security admins need the right security tools to protect environments existing on-premises and in cloud SaaS. Due to the COVID-19 pandemic, IT and security operations are already stretched thin due to changes in workflows, systems, devices, and access to data to accommodate the needs of the distributed workforce. Often businesses have migrated data and services into cloud SaaS environments, yet their security tooling and solutions consist of the same legacy tools built for on-premises environments.
Amid the massive changes due to the pandemic, the sheer volume and variety of evolving cyberthreats can overwhelm IT and security teams simply trying to maintain business continuity. With hybrid environments that stretch between on-premises and cloud SaaS resources, having the visibility, control, and security tools to protect against modern threats and maintain compliance can be challenging.
This situation can lead to catastrophic cloud SaaS misconfigurations that can lead to data breaches and an all-out cyberattack. According to the IBM Cost of a Data Breach Report 2020:
“Alongside stolen or compromised credentials, misconfigured cloud servers tied for the most frequent initial threat vector in breaches caused by malicious attacks, at 19%. Breaches due to cloud misconfigurations resulted in the average cost of a breach increasing by more than half a million dollars to $4.41 million.”
Businesses that ignore cloud SaaS security face a wide range of threats, including cloud misconfigurations, data leakage, compliance violations, and ransomware. What tips can help enterprise organizations’ IT admins secure work-from-home arrangements using cloud SaaS post-pandemic?
Actionable tips for securing the remote workforce post-pandemic
There is no question the threat landscape is more ominous than ever, and the risks to your business are certainly not trivial. What tips can help to secure the remote workforce in the post-pandemic era? Let’s consider the following:
- Secure authentication
- Protect against phishing attacks
- Visibility of user behaviors, applications, and data sharing
- Ransomware protection
- Threat automation
1. Secure authentication
In this day and age of so many threats and vulnerabilities perpetrated by attackers using stolen credentials, implementing two-factor authentication should be standard across the board. Two-factor authentication exponentially increases the security of your cloud SaaS environments. Even if users fall victim to a phishing attack and expose their user credentials, two-factor authentication prevents attackers from easily using the compromised credentials to access business-critical data.
2. Protect against phishing attacks
Using robust phishing protection technologies and solutions for both cloud and on-premises email helps ensure the threat of phishing attacks is greatly minimized. The number of phishing email attacks has exploded with the COVID-19 pandemic as attackers seek to capitalize on the fear and anxiety of end-users with COVID-19-themed emails that have malicious intent.
3. Visibility of user behaviors, SaaS applications, and data sharing
A particular challenge facing businesses who move data and services to the cloud is maintaining visibility. Many organizations have security tools and solutions that may help with visibility in on-premises environments, but they lack these tools for cloud SaaS environments. Businesses must have the right tools for visibility to user behaviors, third-party applications, and data sharing.
Next-generation security tools built for cloud SaaS environments use artificial intelligence (AI) and machine learning (ML) to effectively recognize anomalies in the environment that may signal a malicious application, a rogue employee, or a threat-actor who has compromised the environment. Due to the ease with which users can share data inside and outside the organization by default, having visibility to data sharing is critical. Data shared inadvertently or intentionally can lead to an all-out data leak or breach event and compliance implications that can be disastrous for the business.
4. Ransomware protection
Ransomware is arguably one if not the top security concern of businesses today. It is an ominous threat that can wreak havoc on business-critical data and lead to millions of dollars in losses, damaged business reputation, data leakage, and other disastrous consequences. It is no longer good enough to use traditional ransomware protection.
These are reactive and only kick in long after the ransomware encryption process inflicts damage. Also, backups alone may no longer be adequate since ransomware gangs now use the threat of publishing data to the dark web when ransoms are not paid. These threats coupled with cloud SaaS API throttling that cloud service providers are enforcing means that you want to prevent large restores of data if at all possible.
Businesses must use proactive ransomware protection due to increasingly cloud-aware and more sinister ransomware threats. These solutions use effective security automation to protect business-critical cloud-SaaS environments from the need to restore large amounts of data by stopping ransomware in its tracks.
5. Threat automation
Manual, human efforts are no longer enough in themselves to protect and prevent malicious threats. Threat automation solutions apply automated processes when threats are detected to remediate these as they are detected automatically. Threat automation technology can apply a “run-book” of tasks when certain events and anomalies are detected in the environment. Using AI and ML, threat automation can apply split-second decisions and intelligently protect against malicious attacks, including ransomware.
SpinOne – Centralized and Automated Cloud SaaS Security Platform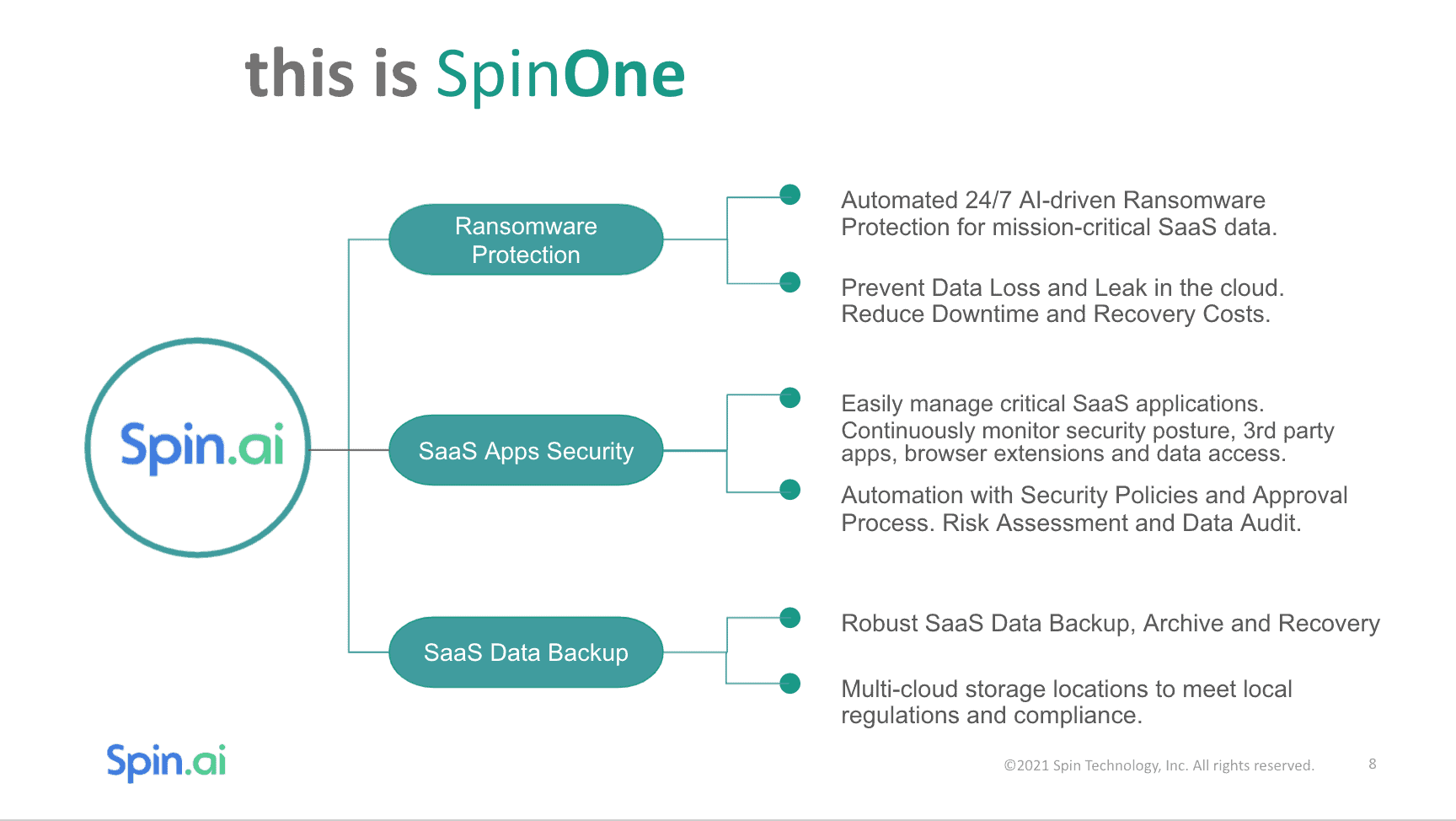
Having the right tools is key to winning the security battle against the myriad of threats coming at businesses in the cloud. SpinOne is an automated SaaS Security Posture Management (SSPM) solution that provides automated evaluations of applications and user behaviors, unified visibility, and control across multi-cloud environments, including Google Workspace and Microsoft 365.
SpinOne helps businesses achieve security objectives effectively in cloud SaaS by providing the technology tools needed to implement the four central SaaS security management pillars in Google Workspace and Microsoft 365 cloud environments. These include:
Discover
- Applications Insights
- Usage Analytics
Manage
- Access Management
- User Lifecycle Management (ULM)
- Visibility & Manageability
- Application Configuration
- Governance by policies setting/threat management automation
- Guardrails to help admins avoid costly mistakes leading to data loss/data leak
- Ransomware protection
Secure
- Least Privileged Access
- File Security
- Insider Threat Protection/prevention
- Incident Response
- Intentional/unintentional user mistakes handling
Compliance Management & Archiving
- Compliance
- Governance
- Archiving (account data archiving and migration, license management, cost efficiency)
SpinOne’s powerful API-driven technology leverages the power of AI/ML behavior monitoring to perform data analysis for multi-cloud SaaS applications. Using effective data analysis, SpinOne can provide robust cloud SaaS analytics, application insights, and automated threat responses, and compliance management.
Intelligent AI/ML behavior monitoring includes monitoring users, data, and applications for anomalies that may indicate compromise, risky behaviors, and malicious activities. It provides robust policy management for your organization so automated decisions can be made, including allowing, blocking, manual actions, or customized responses.
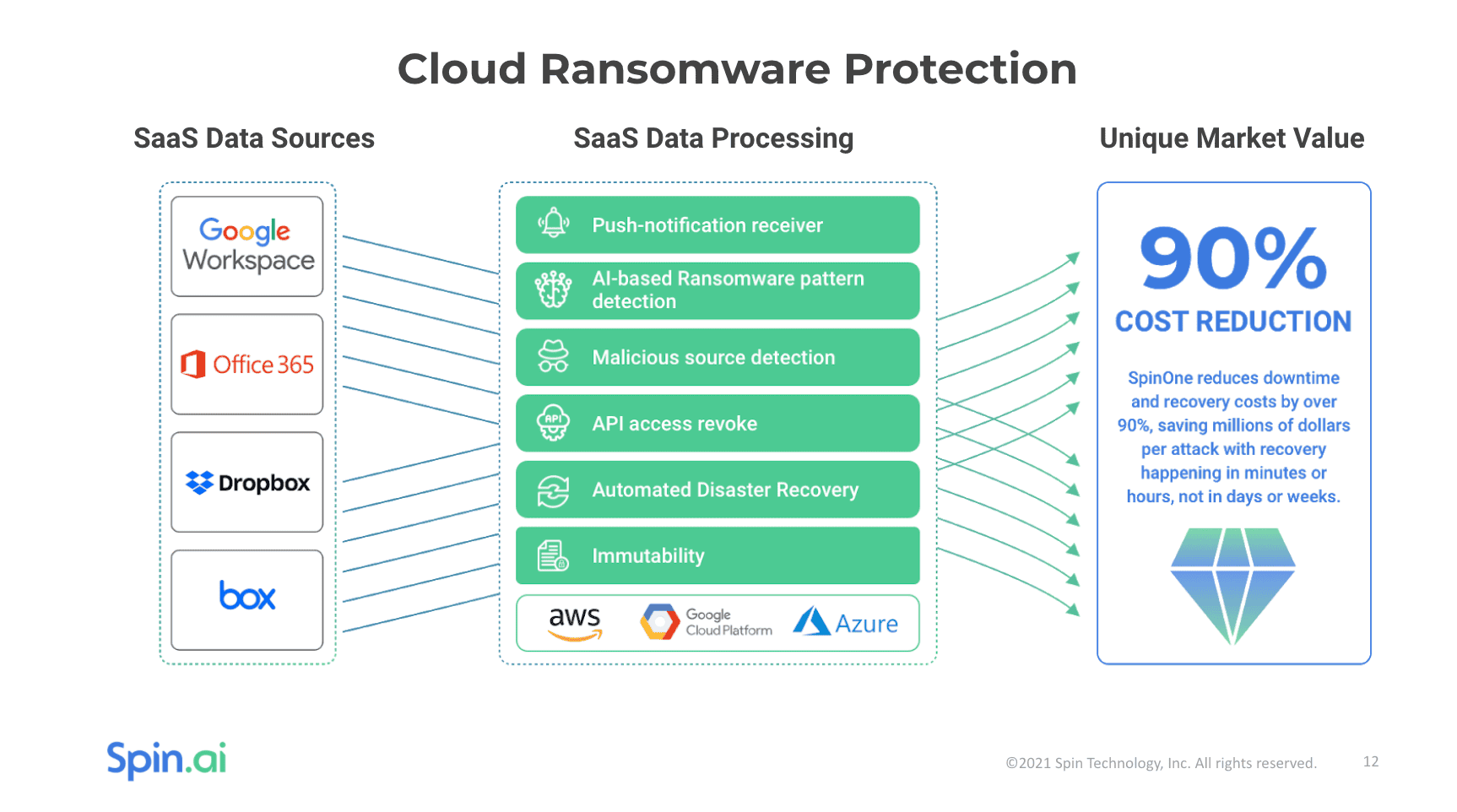
Industry-leading ransomware protection provided by SpinOne allows organizations to have proactive protection against the most ruthless ransomware variants in the wild. It uses an automated defense against ransomware, including the following:
- Monitor – 24/7 SaaS data monitoring
- Detect – Proactive AI-based crypto-behavior
- Stop – Identify the malicious source of a ransomware attack, revoke its API access, stop the attack and prevent encryption of other files or messages in the cloud
- Recover – Identify the number of encrypted files and perform a granular restore from the last successfully backed up version
The proactive, automated defense mechanisms that SpinOne provides businesses allow quickly limiting any damage that ransomware can cause. As the scope of ransomware damage is contained, this helps to ensure business-critical data is not leaked to the dark web. It also helps to ensure your business is not limited due to cloud API throttling to restore vast amounts of data, which can push Restore Time Objectives far beyond acceptable SLAs for your business.
This holistic and proactive security posture helps businesses confidently house data in cloud SaaS environments with automated intelligence that protects against the new and hazardous threats attacking organizations today.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...

