How to Ensure that Your Google Chrome Extensions are Safe
Google Chrome is the world’s most popular internet browser, enjoying a global market share of over 65%. Chrome is fast, stable, and user-friendly. Plus, its functionality can be easily enhanced with browser extensions.
Unfortunately, many of these browser extensions are not safe to use. They can have dangerous levels of unauthorized access to your organization’s sensitive, mission-critical SaaS data, putting it at risk of data leaks, data loss, or ransomware attacks. Using these dodgy extensions can also expose you to malware attacks, phishing scams, and privacy violations.
So how can you ensure that your Chrome extensions are safe?
Here are 6 ways!
#1 Research the developer
The Chrome Web Store (CWS) is the official marketplace for Chrome extensions. Many are completely safe and provided by legitimate vendors. However, extensions that are not from legitimate or trustworthy sources also make it to the CWS.
These extensions can put your system and data at risk. They can make you vulnerable to malware and adware, steal your information, violate your privacy, hijack your email, or slow down your browser. To avoid these problems, research the developer whose extension you plan to download.
Check their full name and run a Google search to learn more about the company.
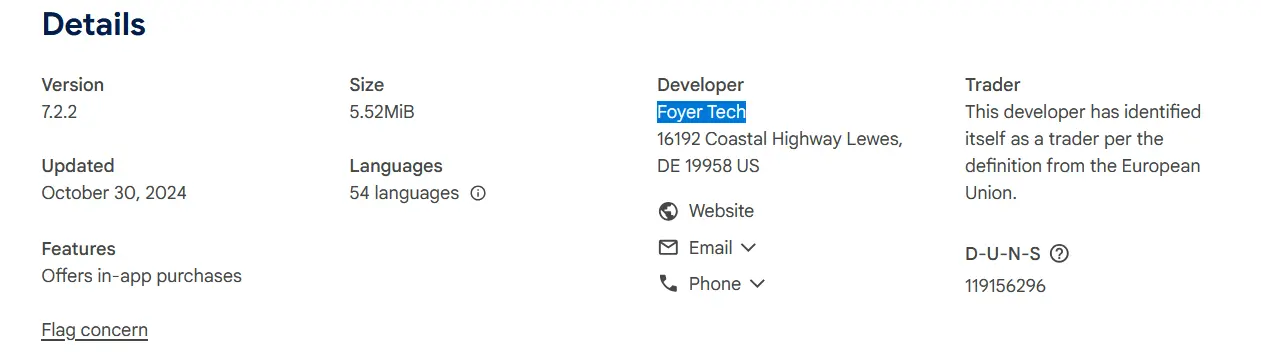
Then check how they describe the product on the CWS.
Also see if they have a full website describing the extension’s features and benefits.
A developer that cannot properly describe their product is unlikely to be reliable or trustworthy.
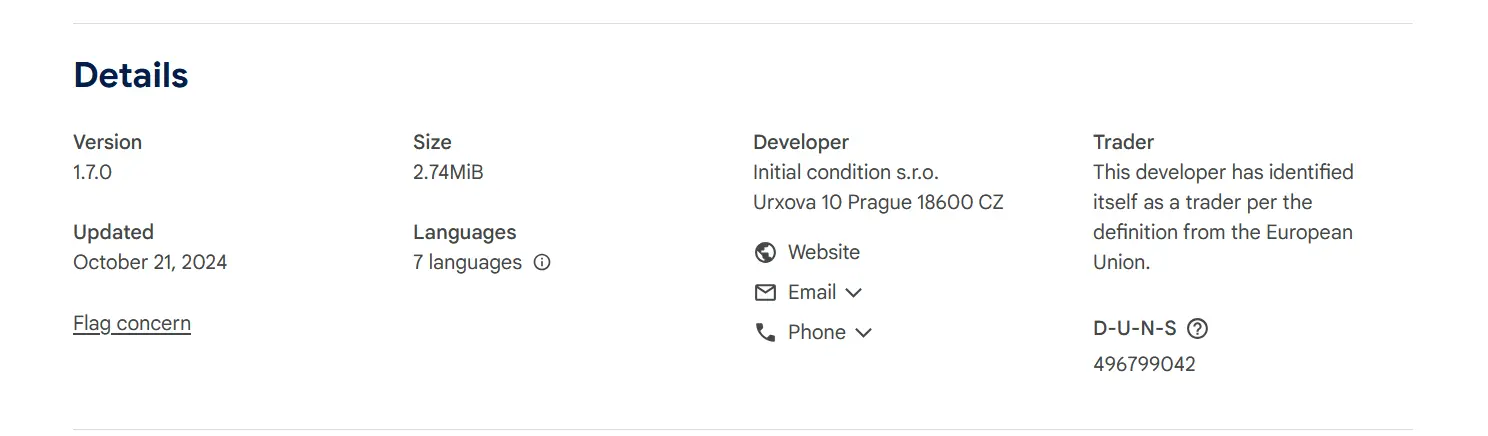
Next, check if the developer provides contact details and a business registration number. These details can indicate that they are a legitimate business, not a shady, fly-by-night operator. For example, if you see that the developer has provided a gmail address instead of a business email address, that can be a red flag.
You can further verify the extension’s safety by checking its privacy notice.
Does the vendor clearly explain how they collect and use your data?
Do they confirm that they won’t sell your data to third parties?
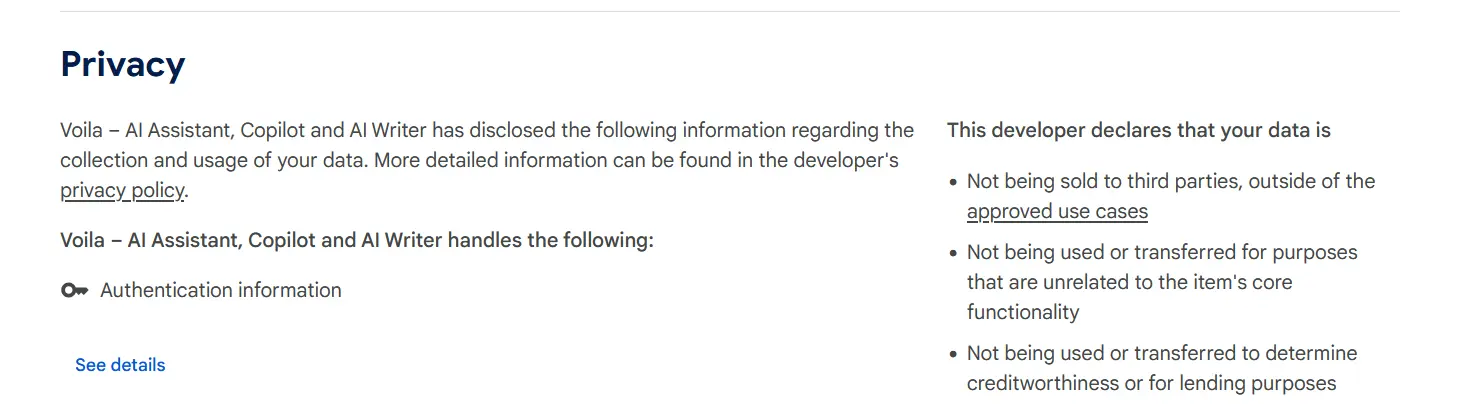
If yes, they are likely to be more trustworthy so you are less likely to face security issues by using them. If not, exercise caution before downloading it.
#2 Check third-party reviews
User reviews are also a good way to verify if an extension is trustworthy. The CWS uses a 5-star rating system. A higher average review can indicate that more people trust the extension, which means so can you.
In addition to star ratings, also look at user reviews. Too many negative reviews may indicate problems with an extension’s usability, features, or security so it’s better to look for a similar extension with a higher average star rating and more positive reviews.
#3 Check Chrome Editors’ Picks
Chrome editors frequently feature certain handpicked extensions in the Editors’ Picks section of the CWS.
Developers cannot pay to be featured here. To make it to this section, an extension must have a:
- high average user rating
- user-friendly design
- clear purpose
This means that you can download and use an Editors’ Pick extension knowing that it is vetted by Google and therefore less risky and comparatively safer to use.
Some extensions also earn badges from Google. These badges offer added signals for quality and trustworthiness, making the products lower risk and offering greater peace of mind to users.
#4. Check when and how often the extension is updated
The cyberthreat landscape is constantly expanding with new security vulnerabilities emerging almost every day. This is why it’s important to check that an extension is regularly and recently updated from a security standpoint before installing it. An extension that has not been updated for a few years may contain vulnerabilities that can put your browser and data at risk.
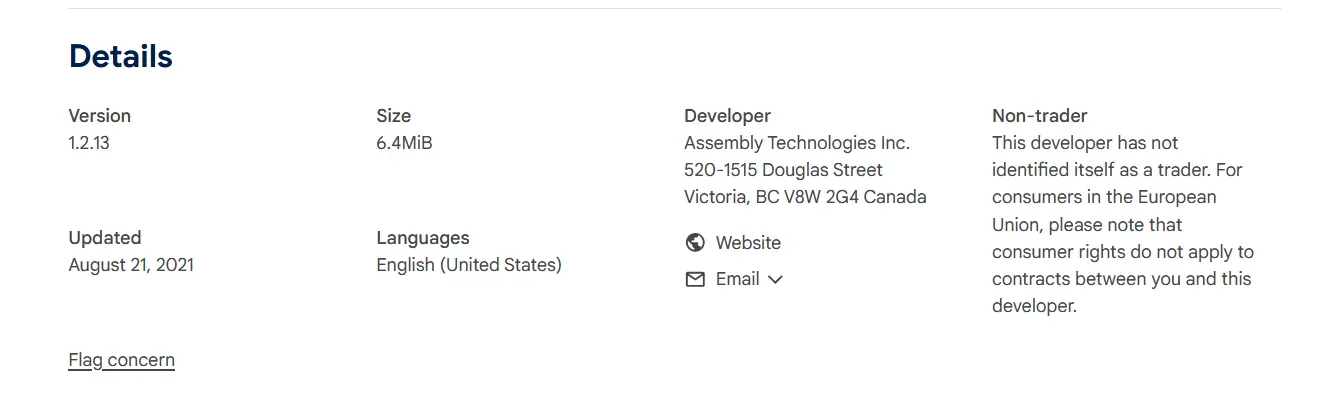
On the other hand, frequent and recent updates indicate that the developer takes security seriously and makes an effort to fix newly discovered vulnerabilities on priority. This then translates to a safer extension.
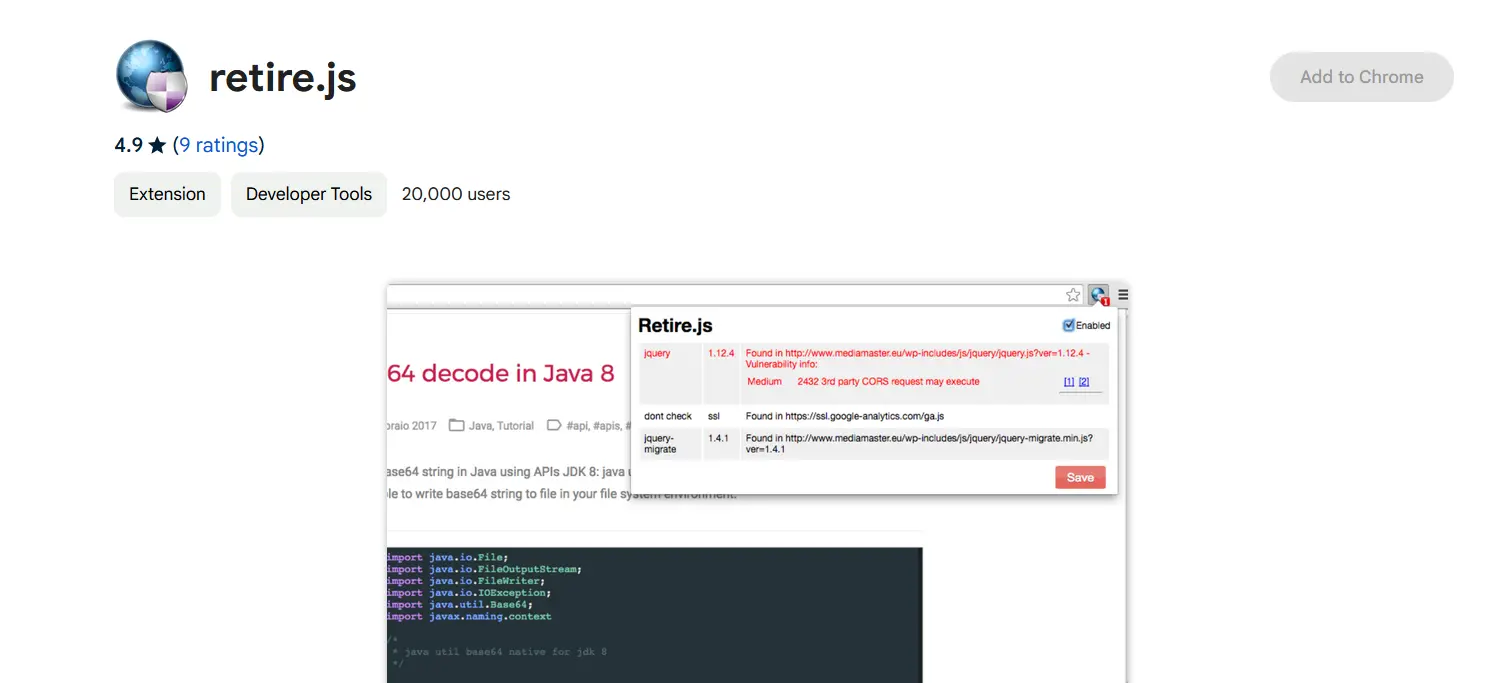
#5 Scan for vulnerable JavaScript libraries
A JavaScript library is a collection of pre-written JavaScript code that extension developers use to enhance its features or simplify common tasks. However, insecure libraries can pose serious security risks. For example, attackers can exploit known vulnerabilities to steal your sensitive data or hijack your browsing session.
To identify vulnerable libraries in a Chrome extension, run a scanner tool like RetireJS. RetireJS uses a frequently updated database of vulnerable libraries to identify vulnerabilities in extensions. It also provides details about discovered vulnerabilities that will help guide your next actions (e.g., remove the extension).
Some other things you can do to stay safe from risky extensions:
- Regularly run an antivirus scan
- Only install the extensions you really need
- Check extension permissions and risk scores with Spin.AI’s FREE Risk Assessment for SaaS Apps and Browser Extensions tool and remove extensions asking for excessive permissions
- Analyze extensions’ source code with Chrome Extension Source Viewer (note: technical knowledge required)
- Identify malicious extensions by analyzing network trace files (accessible from Chrome Developer Tools)
#6 Run a risk assessment tool
Another easy way to discover unsafe Chrome extensions: run a risk assessment tool. One such tool, CRXcavator from Duo Labs, would allow users to evaluate an extension from multiple angles:
- Whether it could potentially upload user data to external sites
- How many permissions it requests and their security implications
- Whether its JavaScript libraries included known vulnerabilities
- Which risky domains it could communicate with
It would then calculate a risk score to help users determine if an extension is risky.
CRXcavator also included enterprise features to help companies manage their Chrome extension allowlist and improve the security hygiene of their Chrome extensions.
Unfortunately, CRXcavator is no longer in service.

Fortunately, an alternative is available: FREE App and Browser Extension Risk Assessment Tool from Spin.AI.Spin.AI’s risk assessment offers similar functionalities and more advanced capabilities than CRXcavator, such as AI-driven assessments, a comprehensive extension inventory, risk history, security policies, access management, vulnerability scanning, and compliance audits. The Spin.AI tool automatically detects and assesses risky Chrome extensions. It then generates a risk score to help you to make more informed decisions about which extensions to install and run. Furthermore, unlike CRXcavator, Spin.AI also assesses risks for third-party applications, providing a more comprehensive security solution for your organization.
Discover a Better Way to Secure Your Browser Extensions with Spin.AI
Most Google Chrome extensions are very useful, helping you to block ads, manage passwords, to check grammar, take notes, automate tasks, convert text-to-speech, and much more. However, some extensions can be very risky to use, making your browser, system, and data vulnerable to compromise or damage.
One great way to minimize the risk of dodgy extensions is to conduct a risk assessment. SpinAI’s Risk Assessment tool provides full visibility into the risk profile of all your Chrome extensions based on a database of 400,000 apps and extensions assessed by AI. Leverage its insights to protect your organization from threat actors looking to exploit unsafe extensions for nefarious purposes.
Click here to request a demo of this powerful tool.
Do Google Chrome extensions collect data?
Yes, Chrome and Chrome extensions collect data about users, such as their location, device type, and browsing history.
Can Chrome extensions access browsing history?
Yes.
Can Chrome extensions have viruses?
Some extensions may contain viruses that can potentially hijack browser sessions, compromise user systems, or steal user data.
Are Chrome extensions stored locally?
Yes, Chrome extensions and associated files and data are stored locally on a user’s computer.
Are Chrome extensions safe to use?
Many Chrome extensions on the Chrome Web Store are safe to use. However, some contain vulnerabilities that can put a user’s system or data at risk. Our research team found that 51% of extensions are high risk so it’s important to assess and re-assess risk using automated tools.
What if I’ve installed an unsafe Chrome extension?
It’s best to uninstall unsafe extensions as soon as possible.
How to see extensions that have already been installed?
To view installed Chrome extensions, open your Chrome browser and navigate to More tools> Extensions. To see the risk score of installed extensions, you can also download the new SpinMonitor – Free Extension Security Checker from Spin.AI.