Types of AI Ransomware Detection in SaaS Collaboration Tools
Ransomware is one of the biggest cyber threats to companies of any size. It has been evolving with computer technologies and even developed capabilities to infect SaaS collaboration tools like Google Workspace and Microsoft 365. Luckily, cybersecurity professionals came up with various methods of detecting and stopping ransomware in the cloud. In this article, we’ll talk about different types of AI ransomware detection and suggest the best one.
Ransomware and SaaS Collaboration Tools
Ransomware can hit SaaS collaboration tools like Microsoft 365 and Google Workspace just as it hits any computer. Once in the system, the malware acts similarly, encrypting documents, spreadsheets, emails, and some other types of data. Cloud ransomware also targets the file versions to disable businesses from restoring data from previous versions.
The difference between SaaS and on-prem ransomware is the attack vectors. Cybercriminals do not try to make victims download a file, use compromised hardware, or strike using the botnet. They use:
- The vulnerabilities of SaaS applications that have OAuth access to Google Workspace or Microsoft 365
- Credential theft
- Social engineering techniques.
Cloud ransomware acts as a regular application that accesses SaaS collab tools with OAuth and has editing permissions. To stop it, IT teams need to identify the ransomware application and revoke its access to the system. Then many teams choose to recover data from the backup.
However, companies that keep large amounts of data in Google Workspace or Office 365 might experience downtime due to a long time of recovery. It’s a signature feature of all such tools.
That’s why many businesses choose ransomware detection tools to stop the attack early on.
Types of AI Ransomware Detection: Which is Best for SaaS?
There are three main types of ransomware detection principles. Two of them require AI technology to operate. The AI-based ransomware detection analyses large data sets to understand whether the attack is taking place.
Signature-based
Signature-based ransomware detection is often used for on-prem tools. It scans the environment in search of familiar patterns of ransomware (“signatures”). Upon detecting it, the tool stops the attack and initiates decryption using the available decryption keys.
This method has a significant weakness as it relies exclusively on the available database of ransomware strains. Unfortunately, ransomware technology is quite simple, and new strains appear almost every day. Some of them are based on old strains. However, there are plenty of new ransomware tools that are completely unknown to signature-based detection.
Traffic-based
This type of detection analyses how traffic behaves in the cloud. It collects the data from multiple sources. That’s why it requires machine learning technology. This method is used for un-prem and cloud solutions alike.
The key benefit of this method is that it doesn’t depend on the signatures and thus can detect completely new strains of ransomware. There’s a downside too.
Signature-based ransomware detection produces way too many false positives perceiving the irregular increase in traffic as ransomware. As a result, it might intrude on important business work processes and damage the data.
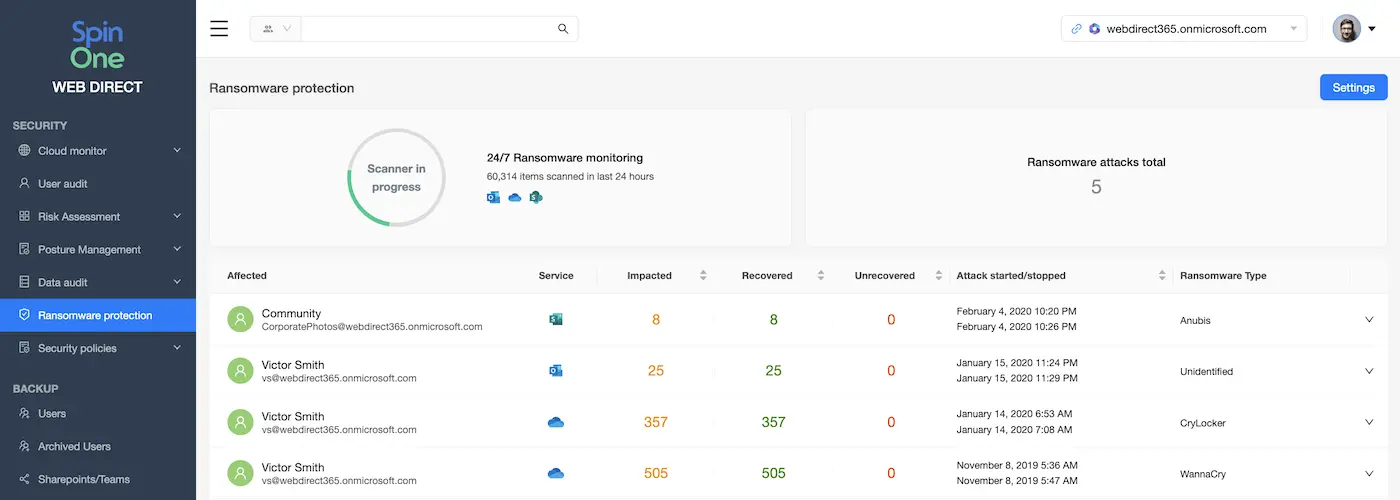
AI Ransomware Detection Based on File Behavior
The tools that have this type of ransomware detection analyze the behavior of data in the system’s files. They use machine learning to study regular data behavior in a company’s Google Workspace of Microsoft 365. These tools establish API connections with SaaS and feed their AI with the behavior data (file edits, downloads, deletions, creations, etc.).
After some time, the AI can predict how data will behave in the cloud during different periods of the day. At this point, it can also detect abnormalities in data. In the case of ransomware, it is the mass editing of file data at the same time.
Similar to traffic-based detection, this method doesn’t depend on a signature. However, it generates very few false positives. It is considered the most reliable ransomware detection.
Learn more about SpinRDR AI ransomware detection based on file behavior.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...

