Why Ransomware Attacks are on the Rise and What to do to Protect Against Them
If there is a single cyberattack that puts fear into the hearts of business stakeholders and IT admins alike, it is ransomware. Ransomware has evolved from an inconvenience for a few end users to a major concern for large enterprise organizations and SMBs alike. In 2023, we’ve seen a major increase in monthly ransomware attacks, and the growth trend will likely prevail. What are the reasons for this growth? How can businesses protect against ransomware attacks in what we can safely call cybercrime pandemic. The present guide will answer these critical questions.
Are ransomware attacks on the rise?
Ransomware attacks are on the rise, according to the statistical cybersecurity data collected over the past few years. According to one report, ransomware incidents are up 600% from 2018. In another report, Cybersecurity Ventures predicted that by the end of 2021, we would see a ransomware attack every 11 seconds.
Cybercriminals are increasingly using ransomware to target critical data
According to the new IBM Cost of a Data Breach Report 2022, note the following statistics relating to ransomware attacks:
- In 2022, ransomware attacks cost, on average, USD 4.54 million
- The frequency of ransomware attacks has increased from 7.8% of breaches in the 2021 report to 11% in the 2022 report
- The average time to identify and contain ransomware or destructive attacks was significantly higher than average
- A ransomware attack took 237 days to identify and 89 days to contain, for a total lifecycle of 326 days
- Alarmingly, the average cost of a ransomware breach was higher for those that didn’t pay the ransom
- For organizations that didn’t pay the ransom, the average cost of the breach was USD 5.12 million, 13.1% higher than the cost for those that did pay up
- Ransomware and destructive attacks were responsible for more than a quarter of breaches in critical infrastructure industries, at 12%
All of these statistics and trends point to one conclusion. Ransomware is here to stay, and attackers increasingly use it to compromise business-critical data and extort unsuspecting organizations.
Why are ransomware attacks on the rise?
Looking at the numbers mentioned above, why do we see the increase in ransomware attacks? There are many reasons for this trend. However, there are three reasons we will consider to have insight into why hackers increasingly prefer this destructive attack.
These include:
- Ransomware attacks are highly successful
- Ransomware-as-a-Service (RaaS)
- Initial Access Brokers (IABs)
- Larger payouts
Ransomware attacks are highly successful
A primary reason for the increase in ransomware attacks is the success ratio. As shown by the numbers, ransomware attacks are wildly successful at extorting money and doing this efficiently and effectively. Many organizations at this point have implemented modern backup solutions allowing them to “undo” the damage caused by a ransomware attack. However, new ransomware tactics include “double extortion.” What is double extortion?
Double extortion is a new tactic that ransomware gangs are using to ensure their victims pay the ransom, one way or another. Traditional ransomware forced victims to pay a ransom to decrypt their data or make it readable and usable once again. With double extortion, criminals charge another ransom to prevent the data from being leaked to the dark web. Unfortunately, having good backups only can’t protect you from this secondary extortion. Arguably, this is the worst of the two since data leak events can lead to all kinds of compliance violations, lost customer confidence, and other fallout.
Another contributing factor to the success of ransomware attacks is it is usually less costly to pay the ransom than not. This fact is born out by the numbers found in the IBM Cost of a Data Breach Report 2022, cited above. As businesses pay the ransoms demanded by hackers following a major ransomware attack, it emboldens attackers to continue. It is a vicious cycle of attacks, payments, and newer, faster, better, and more fully-featured ransomware.
2. Ransomware-as-a-Service (RaaS)
When ransomware first came onto the scene, it required a sophisticated effort to break into a network, carry out the attack, and develop all the application code needed to collect ransom payments, etc. However, ransomware groups, to bring in even more revenue, have commoditized ransomware services in what is known as Ransomware-as-a-Service (RaaS). So what is Ransomware-as-a-Service (RaaS)?
Ransomware-as-a-Service (RaaS) provides similar benefits to criminals who want to carry out a ransomware attack as legitimate services like Google Workspace and Microsoft 365 bring organizations to consume legitimate software-as-a-service applications.
With Ransomware-as-a-Service, the attackers taking advantage of the service do not have to be skilled ransomware developers or own the infrastructure needed to distribute and control the attack and collect ransom payments. Instead, these services are provided “as-a-service” to attackers who want to use the existing ransomware service developed by well-known ransomware gangs.
Ransomware-as-a-Service has helped to proliferate attacks as criminals no longer need to build out their own ransomware, infrastructure, and other components to carry out an attack successfully. The ransomware group running the as-a-service offering collects a percentage of the ransom collected from the victim organization.
3. Initial Access Brokers (IABs)
One of the hurdles to carrying out a ransomware attack is infiltrating the victim’s network. Instead of having to gain access to the victim’s network AND carry out the attack, Initial Access Brokers (IABs) make this process much easier. IABs are nothing more than hackers or hacker groups that have infiltrated a victim’s network and sell the access credentials on the dark web.
An attacker looking to carry out a ransomware attack can simply purchase credentials from the IAB, taking the heavy lifting out of the process to gain access to the network to carry out the attack. Think about it. With tools like Ransomware-as-a-Service (RaaS) and Initial Access Brokers (IABs), even relatively novice attackers can purchase everything they need to pull off a sophisticated ransomware attack.
Think how this is increasing ransomware attacks and allowing hackers to quickly and efficiently victimize organizations worldwide.
4. Larger payouts
Ransomware payouts have gotten larger. It is not unheard of for ransomware groups to demand ransom payments in the USD millions of dollars. Note the following:
- Colonial Pipeline ransomware attack – Hackers charged nearly $5 million
- JBS meat packing ransomware attack – The company paid $11 million to attackers
- CWT Global ransomware attack – $4.5 million
In fact, the average ransom demand made following a ransomware attack has risen to $2.2 million as attackers are becoming bolder and carry out highly effective attacks on victim organizations.
How can organizations protect against ransomware?
Protecting against a ransomware attack requires a multi-faceted cybersecurity strategy. Relying on any single layer of security to protect against ransomware is generally not going to be effective against all types of attacks. Let’s look at the following best practices to protect against ransomware.
- Use multi-factor authentication
- Secure remote access solutions
- Regular patching
- Have a strong anti-phishing email solution
- Protect cloud Software-as-a-Service (SaaS) environments
1. Use multi-factor authentication
Ransomware attacks often begin with compromised credentials. We often read about a breached password leading to a ransomware attack. For example, hackers carried out the Colonial Pipeline attack with hacked credentials linked to a stale VPN account that still had privileged access.
It helps to emphasize the need to ensure user accounts are secured with multi-factor authentication, especially those that have remote access. Compromised credentials and the activity associated with them are difficult to detect.
According to the IBM Cost of a Data Breach Report 2022, compromised credentials were the initial attack vector with the longest mean time to identify and contain the breach, at 327 days. Using multi-factor authentication means that even when an attacker has compromised the password, they still do not have all the “factors” required to authenticate successfully.
2. Secure remote access solutions
Secure remote access is a requirement for businesses looking to protect themselves from a ransomware attack successfully, tying in closely with the point above. Many businesses may place improperly secured Remote Desktop Protocol (RDP) servers on the Internet as a quick way to provide remote access to end-users.
However, this leads to unnecessary risk. Hackers often look for insecure remote access solutions to brute force them for credentials or find vulnerabilities that exist in unpatched systems placed on the Internet.
3. Regular patching
New security vulnerabilities are frequently discovered. Keeping up with the latest security patches from various vendors helps to address these vulnerabilities as they are discovered and patched. Hackers often look for old vulnerabilities that have not been patched or patched fully.
Have a regular schedule for patching business-critical systems and ensure all systems are patched across the board, including servers, workstations, and remote clients.
4. Have a strong anti-phishing solution
Ransomware gangs commonly target organizations through phishing emails. Attackers masquerade malicious emails under the guise of legitimate or even official emails. As a result, employees may think they are opening legitimate emails when, in fact, they are installing a malicious application.
Organizations need to have strong third-party phishing protection to help filter out malicious emails or emails with dangerous attachments or URLs. It helps to ensure that most, if not all, malicious emails are filtered out before they make it to the end-user.
5. Protect cloud Software-as-a-Service environments
When thinking about ransomware, many businesses only focus on on-premises environments. While ransomware has been a primarily on-premises problem over the past decade, attackers realize that organizations are putting more of their business-critical data in the cloud, specifically cloud SaaS environments. These include Google Workspace and Microsoft 365.
Businesses need not forget their cloud SaaS environments regarding proper backups and ransomware protection. However, cloud SaaS providers only provide basic protection from ransomware, which is more a glorified notification of an attack than anything. For example, Microsoft’s ransomware detection notifies you when your OneDrive files have been attacked, but the response is more reactive than proactive.
Organizations need to use third-party solutions to provide proactive ransomware protection and enterprise-grade backups for their business-critical cloud data.
Cloud SaaS ransomware protection with SpinOne
SpinOne helps businesses meet the challenges of protecting their cloud SaaS environment from modern ransomware threats. The solution features artificial intelligence (AI) and machine learning (ML) capabilities, is agentless, and provides enterprise backups of your critical cloud data. SpinOne stands out from competitors due to its real-time threat automation response that allows businesses to cut their downtime due to cloud ransomware to 2 hours and save costs up to 90%.
SpinOne uniquely helps protect businesses from the threat of double extortion since it provides a way to stop malicious processes AND recover data. It helps to minimize data leaked by malicious processes, protecting your sensitive data. Note the following features of SpinOne Ransomware Protection:
- It monitors cloud SaaS environments for signs of ransomware 24/7/365
- When ransomware is detected, SpinOne blocks the ransomware source
- It automatically isolates assets affected by the ransomware attack
- It restores files automatically to the latest backed-up version (configurable)
- Admins are notified of incidents in real-time
- It provides granular SaaS security policy orchestration
Google Workspace Backup Solution Comparison Table
View our competitive pricing chart
*Contact Us for current pricing.
SpinOne also:
- Cuts downtime from 21 days to 2 hours
- Reduces SaaS security management effort and costs by as much as 80%
- Provides ransomware detection, cloud backup, and recovery in a single solution
SpinOne Ransomware Protection module is easy to configure and starts protecting your environment immediately after being enabled. Admins can also create domain-level policies to control ransomware protection in their Microsoft 365 organization, further automating administrative and security tasks.
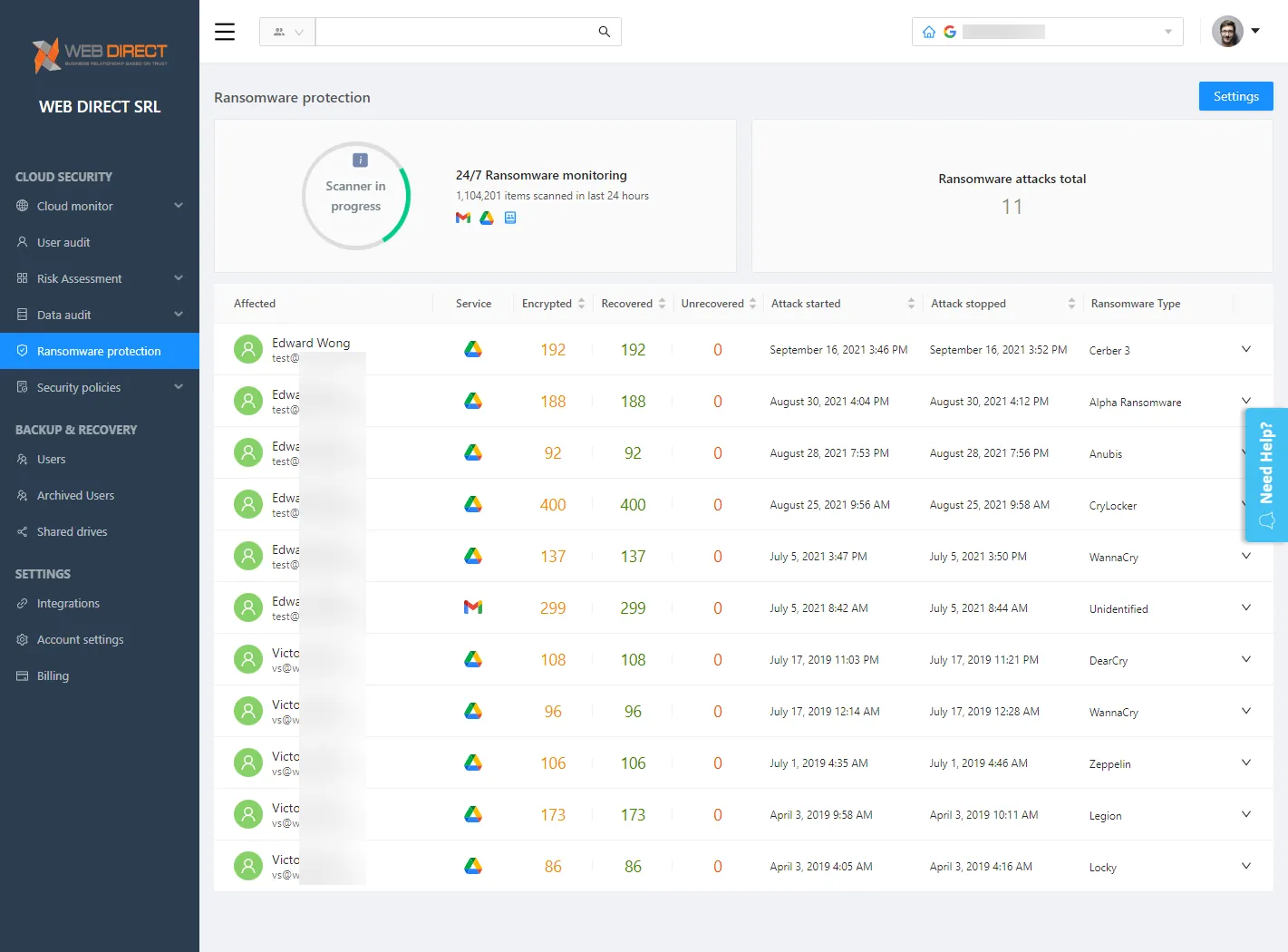
SpinOne Ransomware Protection provides automated protection from cloud SaaS ransomware Using SpinOne, businesses can leverage modern AI and ML technologies to help level the playing field with attackers using advanced ransomware targeting their business-critical cloud SaaS environments. Learn how SpinOne can help your organization meet the cybersecurity threats in your cloud SaaS environment: Enterprise ransomware protection and apps security solutions (spin.ai)
Can I recover my files without paying the ransom?
You can recover files if you have a backup or are lucky enough to be infected by a ransomware strain that has a decryptor made available online by white hackers.
How can employee training help prevent ransomware attacks?
Most ransomware attacks are caused by successful social engineering attacks (e.g. phishing emails). Employees who know how to detect these types of attacks are less likely to become victims of social engineering.
Are there any tools that can help detect and prevent ransomware attacks?
SpinOne platform has ransomware protection that can detect and prevent ransomware attacks.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...



