Why You Need an Extra Layer of Security in your M365
Microsoft 365 (M365) is one of the leading collaboration and communications platforms among organizations today. Companies have been migrating in droves to M365, including Microsoft Teams. But organizations must keep security in mind as they navigate the expanding world of SaaS services – despite having built-in security features, Microsoft 365 still requires an extra layer of security to secure your critical SaaS data. Let’s explore why.
Shared responsibility model
The shared responsibility model details the responsibilities of cloud service providers (CSPs) and their customers in ensuring data security and compliance. While the CSP is responsible for maintaining the infrastructure’s security, including the physical hardware, data centers, and network, customers are responsible for managing their data, access controls, device management, and user behavior.
Note the following infographic from Microsoft, detailing the shared responsibility of customers across on-premises, IaaS, PaaS, and SaaS. As shown, even with the completely hosted nature of SaaS, customers are responsible for their information and data, devices, accounts, and identities.
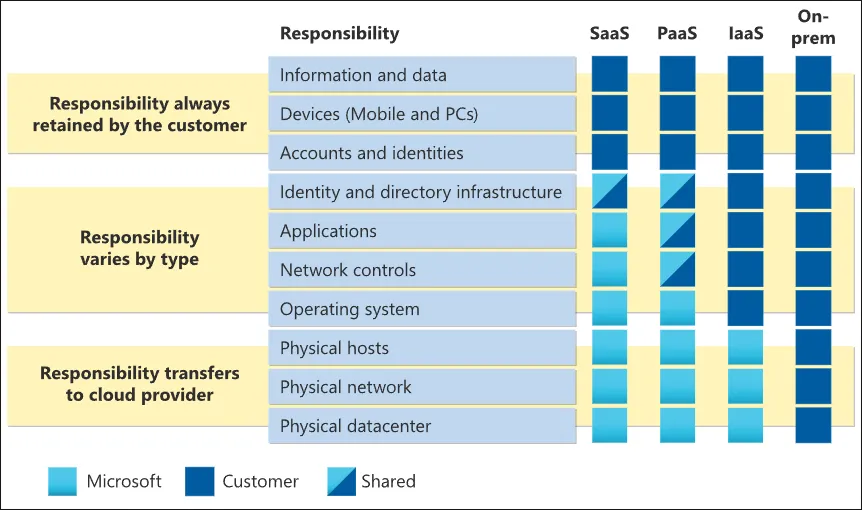
Importance in SaaS Environments
In SaaS platforms, understanding the shared responsibility model is crucial. Note the following ways:
- Data Protection: While the SaaS provider ensures their infrastructure is secure, data protection—like classifying sensitive information, encryption and managing encryption keys, or data loss prevention measures—falls under the user’s purview.
- Access Control: The provider will ensure their service is accessible, but users must manage who has access to what extent and monitor for any misuse.
- User Behavior: It’s up to the organization to train its employees, ensuring they are aware of best practices, phishing threats, and maintaining strong authentication measures.
- Device Management: Mobile devices and PC’s are considered an end-user tool – the administration and management of these devices falls on the organization.
Why It Matters
Without a clear understanding of the shared responsibility model, businesses can overlook their part, assuming that the SaaS provider handles all security aspects and data protection. This misunderstanding can lead to vulnerabilities, data breaches, and compliance violations.
With a better understanding of the shared responsibility model and how organizations are responsible for their data, let’s also consider common security risks in Microsoft 365 and why these can put company data in danger due to advanced threats.
Microsoft 365 security risks
Today’s cyber threats are not static. With machine learning and AI advancements, threats have grown more sophisticated. We’ve moved beyond simple viruses to complex phishing attacks and malware that can embed itself within email attachments. Sophisticated phishing campaigns, for instance, aim to gain access to user identity data or even network access controls.
As organizations move their critical data to the cloud, what risks exist in SaaS environments like Microsoft 365? Consider the following.
- Phishing Attacks and Email Security – Phishing attacks have seen an alarming increase in sophistication. Given that email systems, particularly Exchange Online, are primary communication tools for many businesses, they are prime targets for attackers. Phishing scams often disguise themselves as legitimate messages, tricking users into revealing sensitive information or downloading malicious content.
- Data Breaches and Unauthorized Access – With M365 storing vast amounts of sensitive data, it’s a treasure trove for hackers. Data breaches can occur when malicious actors gain access through weak passwords, unsecured networks, or vulnerabilities in the system itself. An intruder can exfiltrate intellectual property, financial data, or employee information, leading to significant business and reputational losses.
- Malware and Ransomware Threats – Malware and ransomware pose significant threats to businesses using M365. Malicious files can infiltrate the system through email attachments or compromised apps, corrupting data or locking out users until a ransom is paid.
- Insider Threats and Human Error – Often overlooked, insider threats and human error are substantial risks. An unintentional configuration mistake, intentional data loss, or even a disgruntled employee with harmful intentions can destroy an organization’s security posture.
- Compliance Violations – Businesses operating in regulated industries might face compliance challenges. It is relatively easy to violate industry standards and compliance requirements without proper data protection and access management, resulting in hefty fines and legal complications.
Microsoft 365 built-in security offerings and limitations
Microsoft is renowned for its efforts in cyber security and has many security features built into the solution. Some native security features include Exchange Online Protection, which can identify potentially dangerous content, including potentially malicious files, advanced threat protection with security score metrics, and multi-factor authentication.
While M365 boasts many security features, implementing tools that offer deeper data protection, better access management, and real-time threat intelligence can make all the difference. Organizations may find the native Microsoft offerings limited in their feature set. Note the following considerations:
Data protection – Microsoft 365, like most SaaS solutions, does not include a native backup feature for protecting your data. As we see in the shared responsibility model, data protection ultimately falls on the customer as a responsibility.
Ransomware recovery – Ransomware is becoming a larger threat in SaaS environments as businesses migrate file storage and email offerings to the cloud. While Microsoft has its own antimalware protection, organizations may face issues recovering large amounts of data after a ransomware attack.
Data loss prevention (DLP) – Microsoft has DLP features built into the Microsoft 365 solution – but while these DLP features are a great start in protecting your data, the built-in DLP features aren’t as powerful as commercial offerings when preventing data leakage and can create a lot of false positivess
App and browser risk assessment – App risk assessment is a huge area where companies must have protections in place to prevent security vulnerabilities. Security risks like Shadow IT, malicious browser plugins and apps, apps that leak data, and other integrations can lead to data leaks and compliance violations. Microsoft does have App Risk assessment, but note the following:
- It only assesses companies, not apps
- It isn’t real-time
- It can’t assess an internally developed app
- It only protects Microsoft 365 and not other SaaS platforms that may be used
- It doesn’t assess security and compliance
- It doesn’t assess based on exact app configuration”
- It doesn’t assess browser extensions integrated into the environment
SpinOne provides an extra layer of protection
While Microsoft offers basic and even some advanced security protections, an extra layer of security can detect and defend against threats that slip through the cracks. It can provide a more comprehensive security posture, encompassing vulnerability management and improved identity and access management.
SpinOne is an AI-powered cybersecurity solution that helps add an additional layer of protection to Microsoft 365 and helps customers fully satisfy the requirements of the shared responsibility model. Note the following SpinOne features.
Backups
As mentioned earlier, Microsoft 365 lacks a native backup solution. SpinOne not only backs up critical data, it ensures that recovery is fast and easy – restoring access to M365 SaaS data quickly in case of a ransomware attack.
Ransomware
Ransomware is a growing problem affecting both on-premises and SaaS environments. While Microsoft’s ransomware protection provides basic capabilities, SpinOne uses behavioral analysis to pinpoint a ransomware attack quickly and provides a Service Level Agreement (SLA) recovery time of less than 2 hours.
It provides industry-leading cybersecurity automation that proactively stops the attack and recovers data:
- Machine learning behavioral analysis detects a ransomware attack
- SpinOne stops the source of the attack by blocking it’s API
- It scans files to determine if any have been affected by ransomware encryption
- It proactively recovers any affected files automatically (configurable)
- Administrators are alerted of the attack and the measures taken to recover the data
Data loss prevention (DLP)
SpinOne goes beyond simple keyword searches to find and stop sensitive data from leaking outside the organization. It considers context and provides a more intelligent handling of sensitive data to reduce false positives.
App risk assessment
In addition to the protections given by Microsoft’s native app risk assessment, SpinOne:
- Focuses on assessing individual apps, providing more detailed insights
- Offers real-time app risk assessments
- Has capabilities for evaluating internally developed apps
- Protects a range of platforms, not just Microsoft 365
- Conducts thorough security and compliance assessments
- Provides more granular health checks, assessing apps based on their exact configuration
- Exclusively assesses browser extensions, safeguarding from potential vulnerabilities they might introduce
Microsoft 365 + SpinOne
Rather than being a competing replacement for the security tools and solutions in the Microsoft 365 environment, SpinOne adds a highly effective additional security layer on top of the native cybersecurity features in M365.
Organizations will find the Microsoft security solutions a great place to start. However, by investing in advanced security features and practices with SpinOne and Microsoft together, organizations have cutting-edge security defenses that can help stop the sophisticated, modern attacks carried out against SaaS environments like Microsoft 365. If you would like to learn more about how SpinOne can help you secure your Microsoft 365 environment and bolster the native cybersecurity features in M365, click here to schedule a demo: Request a Demo of SpinOne.
FAQs
Does Microsoft 365 have built-in security?
Yes, Microsoft 365 has built-in security. However, they have a shared responsibility model that makes certain security incidents user responsibility.
What are the security options in Office 365?
Microsoft 365 (formerly Office 365) has many security options including multifactor authentication, data retention, data encryption, advanced threat protection, compliance, DLP, and access management.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...
Data Loss Prevention Techniques for 2025 and Beyond
It’s painstakingly clear that data loss is a major challenge facing businesses today. Our experts...
What is SaaS Security? Challenges & Best Practices
Businesses increasingly rely on Software as a Service (SaaS) for increased efficiency, collaborativeness, and scalability....


