10 Ransomware Examples to Stay Away From
Although at the end of 2019 ransomware seemed to be slowing its pace in the cyber threat arena, 2019 has shown that this slowdown wasn’t anything but “the calm before the storm.” Ransomware statistics for 2020-2021 vividly illustrated the rapid growth of high-profile ransomware attacks and new, more disrupting ransomware examples. Now, these attacks got much more sophisticated and ruinous than they’ve ever been before.
McAffee Lab report for 2019 shows that after a decline in volume in 2018, 2019 year demonstrated the appearance of new and more evasive from the early detection of ransomware families and types of attacks.
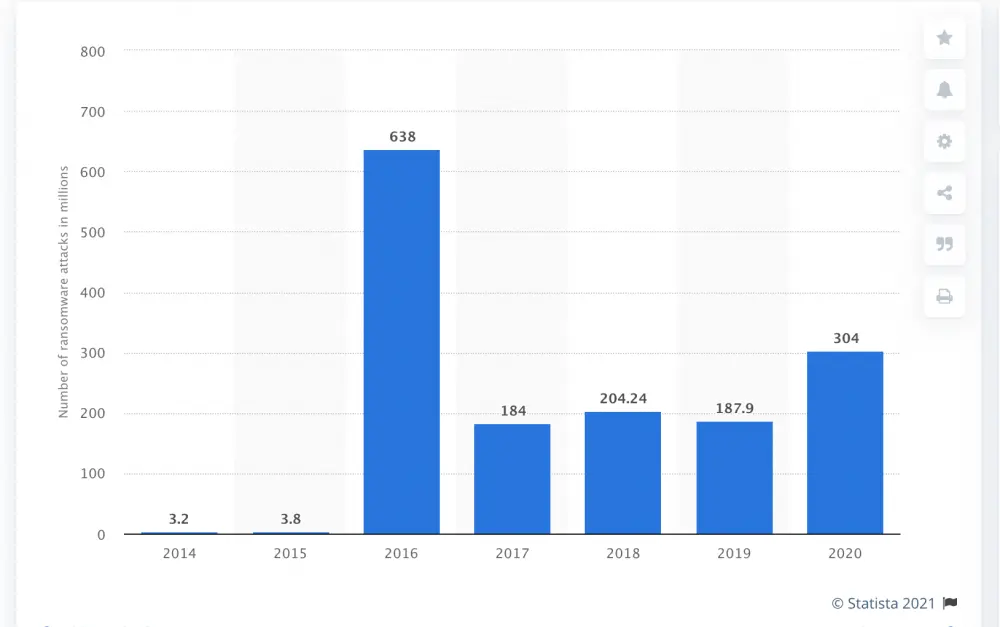
The annual number of ransomware attacks worldwide from 2014 to 2020
Source: Statista reports for 2021
The term “ransomware family” (or “ransomware strain”) can unite many different code modifications that have the same core code. Given that, it’s hard to imagine the number of new ransomware variations that appear every single day.
To defeat the enemy, you need to know its face. And in our case, the enemy has 15 detected faces we will talk about in this article. For some of them, you can find a decryption key; others are “fresh out the oven” and by now can’t be decrypted without paying the ransom.
Here we will list the most widespread ransomware strains that loudly trumpeted across the world in the past few years. Although some of those strains were “retired” or decrypted by security experts, many of them still can infect your computer. That’s why you should be able to identify these ransomware types and protect your systems from them.
Prevalence of ransomware families across the world, 2019
Notice, that we provide links to decryptors for some ransomware versions. Have in mind though that one ransomware family has lots of modifications, and those decryptors may be useless against them. Also, for not tech-savvy users these decryptors may be useless since their deployment require at least some technical knowledge. It boils down to the simple time-tested moral of the story: better prevent than cure.
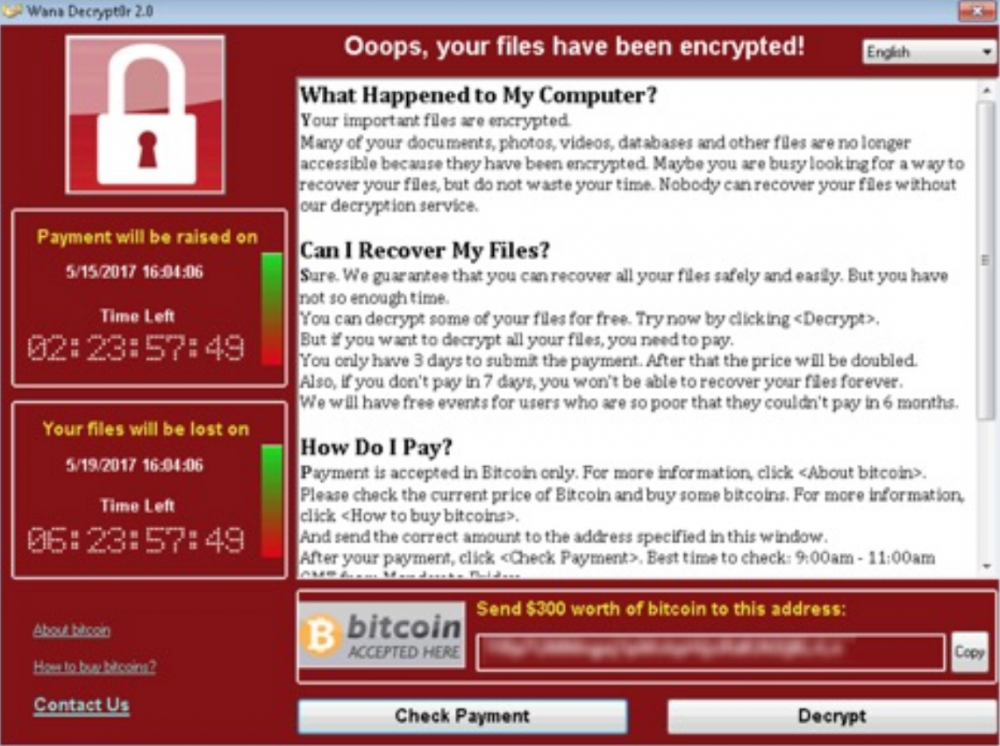
1. WannaCry Ransomware
WannaCry ransomware first appeared in May 2017 and has left a major mark in the history of cyberattacks. WannaCry brought down more than 200 000 systems across 150 countries, causing financial losses of more than $4 billion. This, for sure, makes it one of the most notorious examples of ransomware attacks in history. Some countries like the USA, the United Kingdom, and Australia insisted that North Korea was behind the attack.
How WannaCry spreads
The first step is standard for ransomware infection: a user opens a phishing email and downloads a malicious attachment through which malware infects the computer. But this type of ransomware doesn’t stop there. It can spread across other connected computers by using a vulnerability in the Windows systems called Eternal Blue. More precisely – through the Server Message Block (SMB) protocol.
It doesn’t infect all connected computers though – only those that have the same Eternal Blue vulnerability. The following old versions of Windows still have that vulnerability:
- Windows 7
- Windows XP
- Windows 2003
Security patches for those versions haven’t been released in a long time, which makes them unprotected.
However, if you use a new Windows OS, you can be at risk as well if you don’t update your OS on time. This is what happened with lots of users who fell victim to WannaCry: they didn’t download new patches in time. As a result – they got infected through the network without even clicking on anything.
How WannaCry works
This ransomware tries to access a hard-coded URL, and, in case it can’t, it starts to encrypt files in different formats. Once the files are encrypted, the user sees a ransom notification that demands $300 in Bitcoin.
2. Petya and NotPetya Ransomware
The Petya cyber attack happened in 2017 and was mostly targeted against Ukraine, but later got around as usual ransomware. The overall damage Petya and NotPetya have caused are estimated at more than $10 billion, which makes it, probably, the most destructive attack in history. And while Petya malware is shaped only to make a few Bitcoins, NotPetya evolved as a full-scale political cyberattack.
How Petya spreads
Like WannaCry, at the first stage, Petya propagates via phishing emails when Windows users download infected email attachments. In 2017 however, hackers developed a new version that used the previously mentioned EternalBlue exploit in the Windows systems to spread itself across networks. Specialists refer to this upgraded version of Petya as “NotPetya.”
Also, this ransomware example can gather user credentials when he provides them to fake malicious sites. Using these credentials, Petya can spread across the network shares.
How Petya works
It encrypts and overwrites files in many (more than one hundred) different extensions. Also, Petya encrypts the master boot record to hijack the normal loading process of the infected computer during the next system reboot. After that, the user sees a ransom notification demanding $300 in Bitcoin.
3. Locky Ransomware
This ransomware strain was released in 2016 and, unlike NotPetya, had no major reason behind it except making some money. The ransom payment demand is one of the highest in the industry – 0,5 – 1 Bitcoin.
How Locky spreads
The propagation happens through email. A user gets an email with an attachment in .doc, .xls, or .zip formats, which pretends to be an invoice that needs to be paid. When the user opens this document, they see a gibberish they can’t read. To be able to read it, email prompts them to enable macros, which is launching the virus and encrypts the files.
The problem doesn’t stop there, because the virus can encrypt all network files the user has access to, which potentially broadens the impact area.
How Locky works
When activated, the malware loads in the system and encrypts documents as hash.locky files and encrypts network files if the user has access to them. This virus can encrypt files on fixed drives, removable drives, network, and RAM disk drives.
It’s impossible to decrypt Locky encryption manually – the decryption keys are always generated on the server-side.
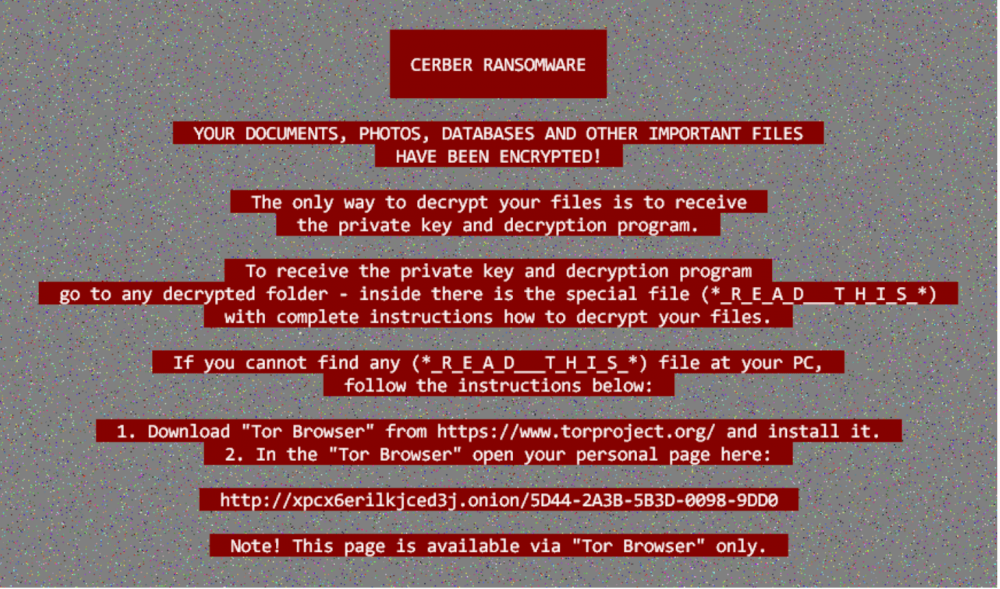
4. Cerber Ransomware
Cerber is the less common type of ransomware called ransomware-as-a-Service. It looks like a vendor platform, where the “reseller” distributes the ransomware as an affiliate for some cut of the ransom.
How Cerber spreads
An interesting thing about this ransomware is that it doesn’t spread in some countries. Ukraine, Russia, Belarus, Turkmenistan, Azerbaijan, Kyrgyzstan, Uzbekistan, Tajikistan, Georgia, Russia, Moldova, Kazakhstan, and Armenia are safe from it. If anyone from these countries gets infected, the virus will terminate itself.
The infection happens commonly – via phishing emails with malicious attachments and links to fake sites where users can download the malware.
How Cerber works
Cerber employs into a system a Trojan virus. The virus scans your system and then encrypts more than 500 file types, converting them into a .cerber or other random extension. The moment all files are encrypted, the screen meets you with a message about ransom demands and instructions. The ransom hackers ask is usually $500 in Bitcoin.
Decryptor: N/A
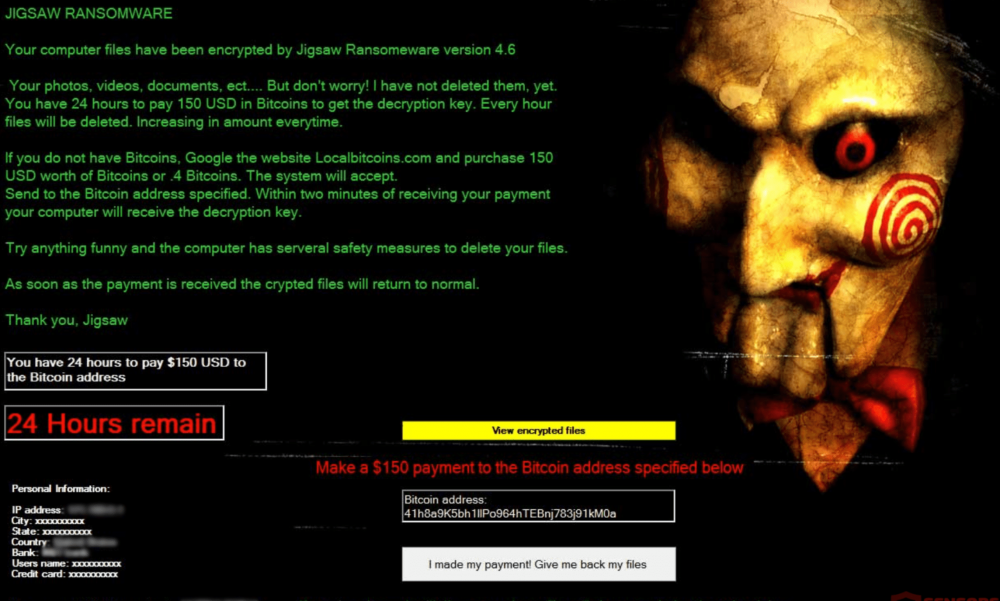
5. Jigsaw Ransomware
Jigsaw ransomware was named after a character from the horror movie “Saw.” Also, it is the first ransomware strain that not only threatens to delete encrypted files in case you don’t pay a ransom but actually does it.
How Jigsaw spreads
Jigsaw spreads across phishing emails with infected attachments. After a user downloads or opens the malicious attachment in the email, ransomware infects the system, and the countdown starts.
How Jigsaw works
Jigsaw encrypts more than 200 file types. After downloading the malware, a user has 24 hours to pay $150 before ransomware starts deleting their files. The files are deleted progressively: the amount of deleted files increases every hour. If the user reboots their computer, the ransomware automatically deletes 1000 files.
To stop the auto-deletion, a user needs to terminate two processes that are causing it – firefox.exe & drpbx.exe in Task Manager. After that, they need to go to the Registry and use MsConfig to purge this autostart entry firefox.exe. This will stop the timer and give some time to find the decryptor and decrypt files.
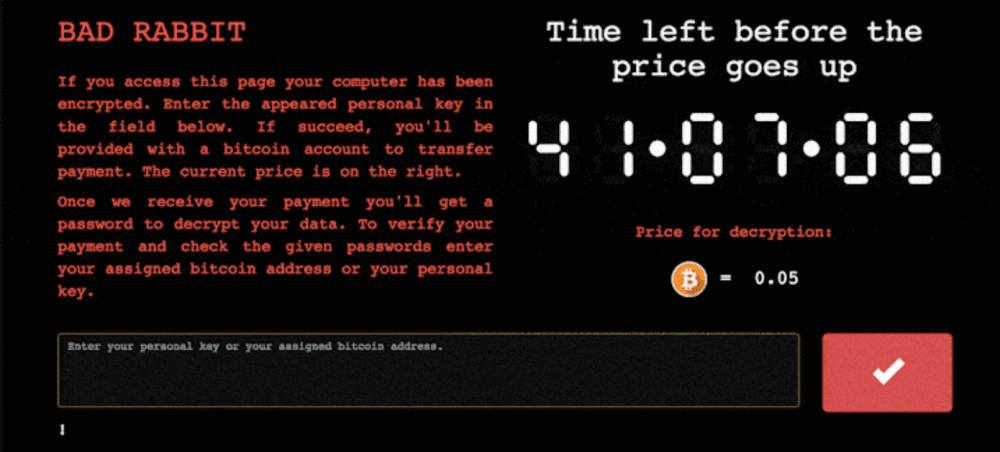
6. Bad Rabbit Ransomware
The code for this strain was “inspired” by WannaCry and NotPetya. Though Bad Rabbit hasn’t created that much damage anywhere outside Ukraine and Russia, it is still considered a big hit.
How Bad Rabbit spreads
The character method of spreading for this strain is by disguising itself as an Adobe Flash installer. The sites you can download it from may seem and even be legitimate, so it is hard to determine the validity of files before you install them. After a person clicks on the Adobe installer on such a site, the malware is installed in the system.
Bad Rabbit can also spread across corporate networks via EternalRomance exploit as an infection vector. To avoid that, you need to deactivate Windows Management Instrumentation through which it spreads.
How Bad Rabbit works
After being downloaded, the ransomware forcefully reboots the computer, then encrypts the files and replaces the Master Boot Record. It makes the affected user buy not one, but two keys: to unlock the bootloader and the data.
When all files are decrypted, the displayed ransom notification demands $280 paid in Bitcoin within 40 hours. After the deadline, the price goes up.
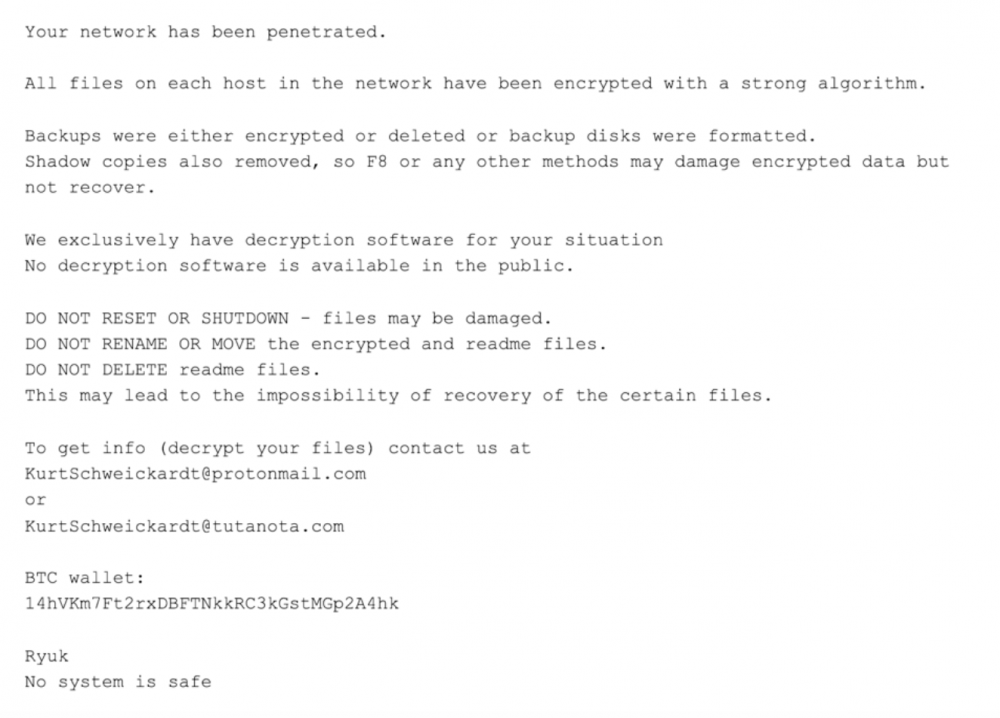
7. Ryuk Ransomware
The family that has produced this virus started its way in 2018 and since then has earned around $3,7 million in 52 payments only. It targets big organizations and other high-value figures, using military encryption algorithms that are extremely hard to decrypt.
How Ryuk spreads
This ransomware is what experts call “targeted ransomware.” It means that hackers choose their victims and attack them. The victims are usually the enterprises that have a lot to lose and will be willing to pay whatever hackers ask to get their data back. Experts say that Ryuk works like a secondary payload through botnets Emotet and TrickBot.
How Ryuk works
When infiltrating the system, Ryuk converts non-executable files in the .ryk file extension. Then it drops a notification with ransom demands and guidelines in the folders that have been processed and names them RyukReadMe (.html or .txt). The ransom demand is insane: from 15 to 50 Bitcoins.
What makes things worse is that Ryuk can stay silent for weeks or months to gather more information and maximize its impact. Also, the virus identifies and enumerates the network shares and deletes the virtual shadow copy. This means hackers can simply ban the Windows System Restore option. Therefore, if you don’t have an external backup, you may not be able to recover your files without paying a ransom.
This is why organizations must have regular external backups and use ransomware detection services that can inform you about malware occurrences. We talk about it in detail as one of the key preventive measures for organizations at the end of the article.
Decryptor: N/A
8. Dharma (aka CrySIS) Ransomware
Dharma ransomware was evolving since 2016 but became a hot topic only in the second quarter of 2019. It is one of the ransomware virus examples that target Windows systems and primarily businesses for the sake of higher payments.
How Dharma spreads
Its recent success can be explained by the use of multiple distribution methods and attack vectors. The first of them is spam emails. As the malware transmitter, Dharma uses infected attachments with double file extensions. Under default Windows settings these attachments may appear as non-executable but in reality, they are.
Also, CrySIS can use disguise to attack, looking like installation files for legitimate software. It looks like harmless installers for licit applications, which in reality are downloadable executables.
But the most popular infection method is targeted attacks by exploiting credential weaknesses in the Remote Desktop Protocol. It involves brute-forcing the victim’s Windows RDP and infecting the machines.
How Dharma works
After Dharma has seeped into the system, it encrypts almost all file types using a strong encryption algorithm (AES-256 combined with RSA-1024 asymmetric encryption).
Before the encryption routine, CrySIS deletes all the Windows Restore Points. The Trojan then gathers the infected computer’s name and the files, sending them to a remote C2 server controlled by the threat actor. On some Windows versions, Also, it can try to run itself using administrator privileges to extend the list of files that can be encrypted.
9. GandCrab Ransomware
GandCrab is a targeted Ransomware-as-a-Service that made a lot of noise across the world and earned $2 billion from 1.5 million affected machines. It had been active from 2018 to 2019 when the group decided to “retire” – most likely because cybersecurity company Bitdefender rolled out a decryption tool for 1, 4, 5.01, and 5.2. GandCrab versions.
How GandCrab spreads
GandCrab targets consumers and businesses with PCs running Microsoft Windows. Threat actors use classic delivery methods – exploit kits and phishing emails.
How GandCrab works
When all files get infected, a user gets a ransom note in English with multiple typos and mistakes, which headline says: “WELCOME! WE ARE REGRET, BUT ALL YOUR FILES WAS INFECTED!”. Then, cybercriminals allow the infected users to download and decrypt one chosen file to prove they possess a decryption key.
Then this note directs you to a Dark Web website to pay a ransom which can vary from $500 to $700,000 (it’s up to the affiliate to establish the price). Payment is conducted in Dash cryptocurrency which is highly focused on privacy. When paid, GandCrab displays a file with a key that users can download and decrypt all files. If something goes wrong with the payment or downloading the decryptor, users are provided with 24/7 online support via chat.
The last versions of the GandCrab virus use Spongebob Square Pants’s character Mr. Krabs on its notes.
10. Sodinokibi Ransomware
Sodinokibi is Ransomware-as-a-Service that appeared in April of 2019 under the parenting of the GrandCrab founders and became the 4th most distributed ransomware in the world since then. A high level of evasiveness and constant upgrades made this ransomware known as highly dangerous for organizations. But countries that were a part of the former USSR can stay calm – the group behind Sodinokibi avoids infecting systems from these regions.
How Sodinokibi spreads
At first, Sodinokibi was only distributed through exploits in servers and other critical assets of SMBs. Later, it started utilizing all possible attack vectors like phishing emails with malicious links, malwaretising, spam campaigns, exploit kits.
How Sodinokibi works
Sodinokibi infects the system quietly, bypassing the first layer of defense – antivirus. It downloads a zip file with JavaScript and executes it, encrypting multiple file-formats and appending a random extension to encrypted files. In case a user has some on-site backup of those files, the virus will wipe it out.
The virus can be quiet for some time to wipe out backup, find more information and networks it can spread itself with. When it’s done, it displays a note demanding $2500 in Bitcoins; if not paid within four days, the ransom is doubled.
Decryptor: N/A
Security Countermeasures
- Use new versions of Windows. Microsoft doesn’t roll out patches for the old OS like Windows 8, Windows XP, and Windows Server 2003, which makes them the main target of many ransomware strains.
- Update your computer regularly. System updates are created as an answer to the newest cyber security threats, so get updated in time.
- Don’t rush to click. Take your time to think when you see an email that seems even a bit weird or unexpected.
- Automize your security for the cloud data using ransomware protection + backup service for SaaS data. In case of an attack, it identifies and blocks the source of the attack, stops the encryption process, and recovers all encrypted files from the last backup.
Colonial Pipeline ransomware attack
On May 7th, 2021, just a few days ago, at the time of this writing, Colonial Pipeline was hit with a ransomware attack from a criminal hacker group known as “Dark Side.” The attack caused the company to shut down critical systems and infrastructure. Ultimately, this resulted in shutting down the 5500-mile long pipeline that feeds half of the fuel to the United States East Coast. The fallout from shutting down the pipeline cause “panic buying” of gasoline and other fuels. The mass shortage of fuel was felt at the pump, with many gas stations running out.
How could hackers infiltrate a large industrial organization and cause this much damage to critical IT systems that affected operations, including the pipeline? Eric Cole, who authored the book Cyber Crisis and has his own cybersecurity company, Secure Anchor, said the situation with the Colonial Pipeline ransomware attack was directly related to the COVID-19 pandemic. The infrastructure changes made to accommodate remote workers for Colonial provided the weakness in the cybersecurity armor that led to the compromise.
Before COVID-19, Colonial carried out critical operations of the pipeline on a secure, closed network with no external access. However, to accommodate remote workers, access to the essential systems controlling the pipeline was made publicly available on the Internet for remote workers. The resulting changes led to the recent ransomware attack.
Many organizations have relaxed security protocols that have been enacted since the COVID-19 pandemic and work-from-home initiatives simply to keep workers productive. This major ransomware attack on Colonial is a wake-up call for all businesses to take a look at their security protocols and configurations to understand any attack vectors that may have crept in.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...