Types of Ransomware Attacks: A Comprehensive Overview
In Q1 2023, ransomware attacks spiked in numbers. It becomes clear that many companies do not have efficient ransomware protection or knowledge about the danger of these attacks. As part of our ransomware awareness initiative, we explain in this post the various types of ransomware attacks.
The difference between ransomware types and strains
Many people confuse strains and types of ransomware, using them interchangeably. These are, however, different terms.
Strains also sometimes referred to as families or variants are individual ransomware programs. Examples of ransomware strains include LockBit, ALPHV, Malas, Cl0p, and Royal Ransomware. These are the most popular strains in 2023.
Ransomware is one of the easiest malware to develop. That’s why dozens of new strains emerge every year.
Sometimes a strain is associated with a certain cybercriminal gang. However, some variants are used by multiple malicious actors. Certain gangs use more than one strain for their criminal activities.
When we talk about types of ransomware, we imply sets of individual ransomware strains grouped by a certain feature. Categorization helps identify the impact the ransomware has made on your system and data.
For example, ALPHV is a classic crypto-ransomware (see the explanation of the type in the next section). Recently the API to enable data extortion has been added to this strain. So now it can also be categorized as double or triple extortion ransomware.
Malas is a double-extortion crypto. What’s interesting about this ransomware is that the group that uses it forces the victims to donate money to various charity organizations.
Types of Ransomware Attacks
In this section, we discuss in detail the ways ransomware attacks can be categorized.
By the target
This way of categorizing ransomware attacks emphasizes the main target of the criminals. There are two main types of attacks:
- On individuals
In most cases, individual users are easier targets for ransomware gangs. The main reasons are the low level of cyber awareness coupled with a lack of ransomware protection tools. The attacks on individuals, however, do not bring as much income as on other entities.
- On organizations
This category includes businesses, non-profit organizations, and governmental institutions.
The organizations are a more desired target as they can pay larger ransom compared to individuals. However, many of them know how to defend against and prevent ransomware attacks, which makes them a harder target. Furthermore, the organizations are usually mandated to report the attack and initiate the investigation. This sometimes can lead to the capture of gang members and pretty large imprisonment terms.
Nevertheless, the number of attacks on organizations is steadily growing year over year.
By the system
This categorization divides ransomware strains into two main categories by the system they target:
- Desktop
Most ransomware strains still target desktop computers, namely Windows. Lately, we’ve seen the rise of ransomware strains that hit MacOs and even the emergence of variants that target Linux. Many developer companies used to work exclusively on Linux OS due to the minimal numbers of malware that target this OS specifically. This trend will probably change with more and more malware developers building solutions for Linux.
- Cloud
Since the rapid cloud adoption by businesses across the globe, new strains of ransomware targeting specifically cloud solutions have emerged. Modern cloud environments contain large data sets that are often used by organizations on a daily basis.
One of the key problems with cloud ransomware is the downtime that it causes even if an organization has cloud backup. Due to API limitations, many cloud environments do not enable rapid data recovery from the backup.
If several hundreds of terabytes of data have been encrypted in one large event, the recovery can take weeks or even months. The financial, reputational, and other negative implications in this case will be devastating for the organization that chooses to pay ransom rather than have data recovery chaos. Hackers count on this when they demand money from their victims.
Unfortunately for many victims, most organizations fail to recover 100% of their data after such an event even if they have a decryption key.
By data recoverability
Most people think of ransomware as an encryptor, however, there are different types of impact on your data.
- Wipers
Wiper ransomware is the worst type an organization or an individual can come across. These strains delete your data completely. And unless you have a backup or the ransomware has extorted your data prior to wiping it, there is no way you can recover it.
Why create a wiper ransomware? First, there has been a mistake in the malware code. Second, the wiper is created deliberately to combat an organization. Oftentimes times wipers are used against governmental institutions as an additional method of combat. This type of malware has been widely used during the ongoing invasion of russia in Ukraine by both the aggressor and the victim.
- Full encryptors
This is the category of classic ransomware encryptors that encrypt files and their previous versions. Usually, data can be restored using a decryption key.
- Non-full encryptors
This type mostly contains the legacy ransomware strains that didn’t encrypt previous versions of files. Hackers do not use these strains anymore.
By data extortion
Data extortion is a relatively new type of malicious activity done by ransomware. It is the process of copying the victim’s data to the hacker’s storage. The data is then held hostage in case the organization refuses to pay a ransom. The gang blackmails the victim threatening to make their data publicly available or sell it to interested actors (e.g., on the Dark Web).
When ransomware attack is the means of political struggle, the data is exposed without notifying a victim. There are three types in this category:
- No extortion
The ransomware doesn’t have the data extortion functionality (older strains) or hackers simply do not use it.
- Double extortion
Hackers copy the victim’s data and blackmail it to expose it unless the victim pays ransom.
- Triple extortion
Many businesses store client data in their databases (e.g., name, contact information, CCN, SSN, etc.). When hackers come across this data, they can use it to blackmail not only the business they extorted this data from but also the data owners. Hackers would blackmail the individuals threatening to sell this data on the Dark Web unless they pay ransom. That is triple extortion.
By impact on your system
This is the most widespread classification of ransomware attacks. It focuses on the way the ransomware impacts the targetted environment.
- Classic crypto
This is the most widespread ransomware type. It encrypts the files on your computer or cloud. However, it doesn’t impact the way your system works. You can still, for example, open your files. However, you won’t be able to decipher the containing data.
- Lockers
This type of ransomware makes your system completely inaccessible. It infects predominantly desktops. The user cannot do anything on their computer until they pay ransom.
- Scareware
Technically, it’s not ransomware as it has a minor impact on your system. Usually, it’s a virus that disguises itself as a ransomware demanding to pay money.
- Leakware
Also known as extrotionware, doxware, or exfiltrationware, is a type of ransomware that threatens to expose sensitive information. It is used in double extortion.
By “business” model
Ransomware is one of the most profitable criminal activities. It is safer for people who commit it as it is very hard to identify them. And the ransom payments rise year over year. Despite the vain attempts of governments to make ransom payments illegal.
- Regular
The classical model implies that the strain developer also delivers the ransomware to potential victims and negotiates the ransom payment. This model is becoming obsolete.
- RaaS
In this model, developers only create the ransomware strain but do not participate in social engineering or other parts of the attack. Instead, they sell access to their ransomware tool to the cybercriminals. Basically, it’s a subscription-based model with monthly/quarterly/annual payments.
By the availability of free decryptors
Last but not least, we categorize ransomware by the availability of decryptors online.
- Decrypted
Ransomware strains of this type have decryption keys available online. For example, this organization of white hackers has over 170 keys. They provide these keys for free and also help with the diagnostics of your ransomware attack to identify the strain correctly.
- Not Decrypted
If you open the above-mentioned database of decrypted ransomware strains and search for the decryption key for the most currently popular strains, you will find nothing. That is because ransomware strains emerge faster than white hat hackers can decrypt them. It’s one of the main reasons, why legacy ransomware protection tools aren’t efficient against ransomware attacks.
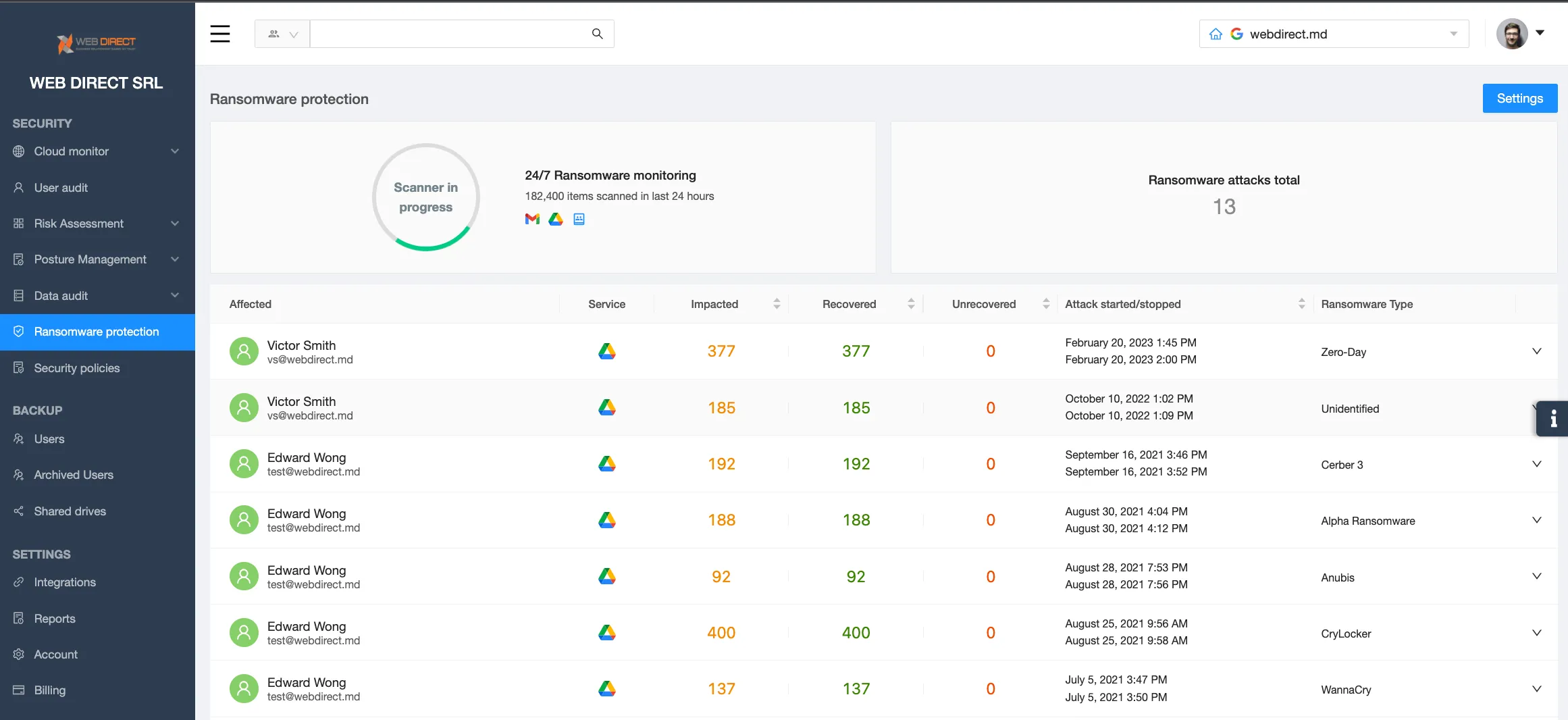
How to protect against ransomware attacks
There are several security practices that will help your business protect against and even prevent ransomware attacks. You need to conduct all of these practices to achieve maximum effect.
- Create and maintain cybersecurity awareness in your organization
- Use backups
- Control risky applications
- Use email servers with strong phishing filters
- Impose strong passwords that should be regularly changed
- Acquire AI-based proactive ransomware protection.
Learn more about ransomware protection.
FAQs
What are types of ransomware attacks?
There are many types of Ransomware. Some of the most popular are desktop and cloud, Crypto, Scareware, Leakware, Lockers, and RaaS.
What are ransomware strains?
Ransomware strain is a particular ransomware program. The examples of strains are Cl0p, LockBit, ALPHV, and Malas.
How to protect against ransomware?
Ransomware protection tools that analyze data behavior are the most efficient against ransomware attacks.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...


