5 Predictions for Ransomware Trends in 2023
As we look forward to 2023, the threat landscape is ominous. In the past, most cyber attacks used to come from individuals or small groups of organized crime rings. The latest ransomware trends reveal that organizations are targeted by well-funded, highly-skilled and well-organized cyber criminals.
Organizations today face a wide range of threats across both on-premises and cloud environments, including cloud Software-as-a-Service (SaaS) environments. In addition, cloud ransomware is a threat that continues to gain momentum and evolve, two factors we hoped we would not see moving into a new year. Several ransomware trends are developing as we look at 2023. Taking note of the developing ransomware trends helps improve cybersecurity the overall posture to defend against these new threats.
Ransomware trends for 2023
What ransomware trends are developing for the upcoming year? Take note of the following areas that ransomware attacks are evolving and how these aspects may become even more prevalent in 2023.
- Initial Access Brokers (IABs)
- Ransomware-as-a-Service
- Double extortion
- Malicious cloud SaaS applications
- Increasing ransomware attacks on critical services
1. Initial Access Brokers (IABs)
Gaining access to a corporate network is often the most labor-intensive process for an attacker or group of attackers as they look to compromise a target organization with ransomware. An alarming trend that is developing in ransomware attacks is the Initial Access Broker (IAB). What is an Initial Access Broker?
Initial Access Brokers are criminal individuals or groups that have obtained access to corporate resources, including on-premises networks, cloud environments, or cloud SaaS. They may have used various means to get the credentials, including phishing, brute-force attacks, or exploiting vulnerabilities. The IAB then sells access to corporate networks on dark-web forums.
Numerous studies of dark web activities have seen sharp increases in the number of offers to sell access to compromised corporate networks. So, what types of access do IABs sell to ransomware gangs and others?
- VPN and RDP
- Citrix Gateways
- Web shells
- Reverse shells
- Web site credentials
- Cobalt Strike sessions
- VMware vSphere ESXi access
- Many others
The newly escalating criminal industry of the Initial Access Broker is helping threat actors to attack a targeted organization with ransomware and other attacks much more quickly. Gaining initial access to the victim’s corporate network allows easy penetration of the network with a legitimate user account, including administrator accounts.
With the success of the Initial Access Broker, two things will happen that are not good news for businesses today. First, the number of access brokers will increase, and second, the price for credentials on dark-web forums will decrease. Unfortunately, these trends will only increase the ease with which cybercriminals can obtain credentials to victim organizations’ corporate networks and use these to launch an attack.
The pricing requested by Initial Access Brokers may vary. It generally depends on the company size, revenue, and the privilege level of the credentials and access sold. A recent report by KELA, a cybersecurity intelligence organization, noted the following statistics on the pricing of credentials and privileged access:
- The average price for network access was $5,400
- The median price was $1,000
- 25% of the published listing was allegedly sold
High-level domain admin credentials are the most expensive, as you would imagine. The same report by KELA observed the following credentials for sale:
- Access to an Australian company with 500 million USD in revenue with domain admin access was offered for 12 BTC
- Access through ConnectWise to a US IT company was listed for sale for 5 BTC
- Access to a Mexican government body offered for 100,000 USD
One thing is for sure. The Initial Access Broker is an alarming trend on the scene of evolving ransomware attacks that allows attackers quicker time to compromise and will undoubtedly speed up the adoption of the next trend on our list, Ransomware-as-a-Service (RaaS).
2. Ransomware-as-a-Service (RaaS)
Undoubtedly, one of the most alarming developments in ransomware attacks has been Ransomware-as-a-Service (RaaS). Traditionally, ransomware was a tool operated by a malicious attacker or group of attackers with very advanced coding and development skills. They had to take the time to develop the ransomware, find a way into the corporate network, and then launch the attack.
However, Ransomware-as-a-Service (RaaS) has commoditized the use of ransomware among those in the criminal community. Since it is an adaptation of the Software-as-a-Service (SaaS), it becomes a subscription-based model that allows affiliates to use readily available ransomware tools to launch an attack. Think of it as “pay-for-use.” If the attack is successful, the ransomware group that offers the RaaS service gets a percentage of the ransomware payment.
Ransomware-as-a-Service has all but removed coding skills and other technical prerequisites as a requirement. Like all Software-as-a-Service (SaaS) offerings, operators do not need to know the inner workings of the RaaS solution, how to code it, encrypt data, issue decryption keys, etc. Instead, all of the technical components and underlying code are abstracted from the affiliate hacker to simply concentrate on the task at hand – extorting a victim organization.
Ransomware-as-a-Service offerings are popping up all over the dark web as malware developers provide affiliate hackers an easy way to compromise victim organizations with readily available ransomware. What’s more, RaaS offerings are often provided at little or even no cost to affiliate hackers. With malware vendors only charging a percentage of a ransom payment if the attack is successful, there is little barrier or cost of entry for even novice hackers.
This new model has served to rapidly increase the use of ransomware as an easy way to attack and extort victim organizations with ease. With the Initial Access Broker (IAB) market providing hackers with easy access to privileged accounts, and the availability of Ransomware-as-a-Service, criminals have everything they need in an ala carte fashion to put together a successful attack in very little time.
In addition, the Ransomware-as-a-Service model extends the accessibility and reach of a ransomware variant. For example, a malicious developer may not be able to attack many victim organizations. However, if the ransomware variant is offered “as-a-Service,” its accessibility and reach become exponentially greater.
Many examples of ransomware groups offer Ransomware-as-a-Service (RaaS) to affiliate groups. These include:
Avaddon
Appearing on the scene in 2019, the ransomware operations have compromised around 88 victims, 47 in 2021. Additionally, the group offers Ransomware-as-a-Service to dark web customers and leaks documents to threaten organizations into ransom payments.
Darkside
A well-known group for its ransomware attack on the Colonial Pipeline that took down some 5,500 miles of pipeline, causing fuel shortages in the Northeaster United States for weeks. They operate Ransomware-as-a-Service on the dark web. It has even been speculated the attack against Colonial was carried out, not by Darkside itself, but an affiliate group, using the RaaS offering.
DoppelPaymer
Based on the BitPaymer ransomware, DoppelPaymer is known for targeting critical infrastructure organizations, including healthcare. They have compromised 186 victims in total, with 59 in 2021.
Maze
It appeared in 2019 and is a ransomware group that threatens to expose sensitive data publicly to force ransom payments. They operate a Ransomware-as-a-Service offering that has been used in several high-profile attacks.
REvil
A newer RaaS ransomware group on the scene that has victimized over 161 organizations, with 52 attacks in 2021.
Ryuk
Ryuk is an extremely successful ransomware group that has targeted technology companies, healthcare providers, education, financial services, and government organizations. Their RaaS offering is popular with affiliates carrying out attacks.
3. Double extortion
An extremely worrisome trend that has developed with ransomware groups proliferating the use of RaaS is “double extortion.” What is double extortion? According to the Microsoft Digital Defense Report 2021, double extortion involves the following workflow:
“A ransomware and extortion attack involves a threat actor deploying malware that encrypts and exfiltrates data and then holds that data for a ransom, often demanding payment in cryptocurrency. Rather than just encrypting a victim’s files and requesting a ransom in exchange for the decryption key, the attackers also exfiltrate sensitive data before deploying the ransomware. This practice prevents victims from disengaging from negotiations and raises the victim’s reputational costs of not paying the ransom as the attackers likely will not only leave the victim’s data encrypted but also leak sensitive information.”
The practice of double extortion helps the attackers to have much more leverage against victim organizations as they not only have their data encrypted, they have good copies of the data they can threaten to leak to the dark web. Arguably, this threat may be the more sinister and damaging of the two.
In a post from Infosecurity Magazine, researchers have recorded a 935% year-on-year increase in double extortion attacks with data from over 2300 companies posted onto ransomware extortion sites. As we are on the cusp of 2023, there is no question the trend with double extortion will continue to plague businesses. Ransomware groups will continue to look for new ways to “bleed” companies using the data stolen from their corporate networks.
4. Malicious cloud SaaS applications
As businesses move their critical data to cloud SaaS environments, attackers are placing increasing focus on cloud SaaS. Unfortunately, one of the ways that cybercriminals can compromise cloud SaaS environments is by using malicious cloud SaaS applications.
End-users are accustomed to accepting permissions requests to cloud SaaS applications to a point where most do not give it any thought. However, a cloud SaaS app might request very high-level permissions to be authorized by a user. If the permissions request is not scrutinized appropriately, a malicious app can be granted privileged permissions to carry out high-level tasks.
Attackers also use sophisticated and very convincing phishing emails that masquerade as legitimate solutions and services requesting permissions. They may even send emails that appear to be from the cloud service provider themselves, requesting the user install an “update” or a “security patch.” Instead of a legitimate or safe application, the phishing email clandestinely installs a malicious ransomware application that begins encrypting cloud emails, storage, and group drives.
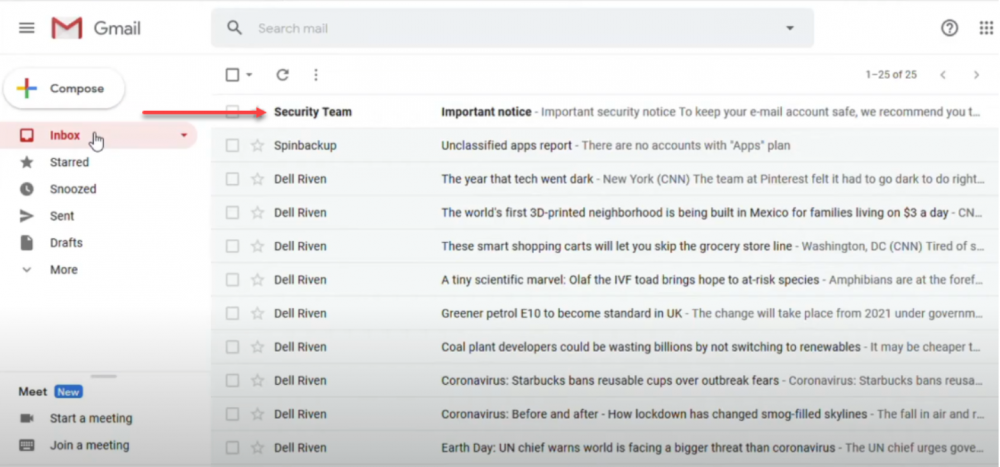
Below, a malicious phishing email arrives that appears to be from the “security team.”
A malicious phishing email containing ransomware
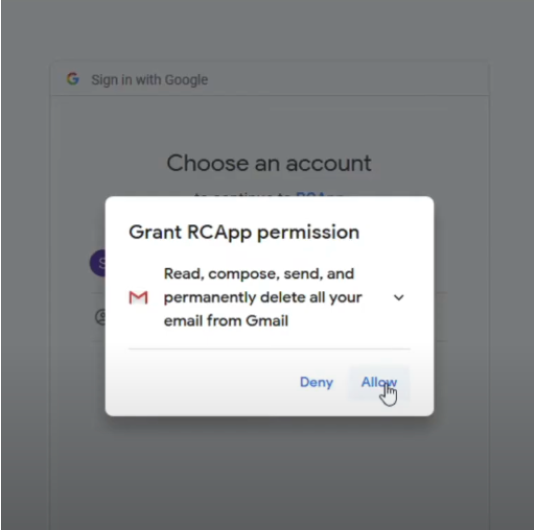
The email directs the user to grant permissions to the cloud SaaS application.
Granting permissions to a malicious cloud SaaS application
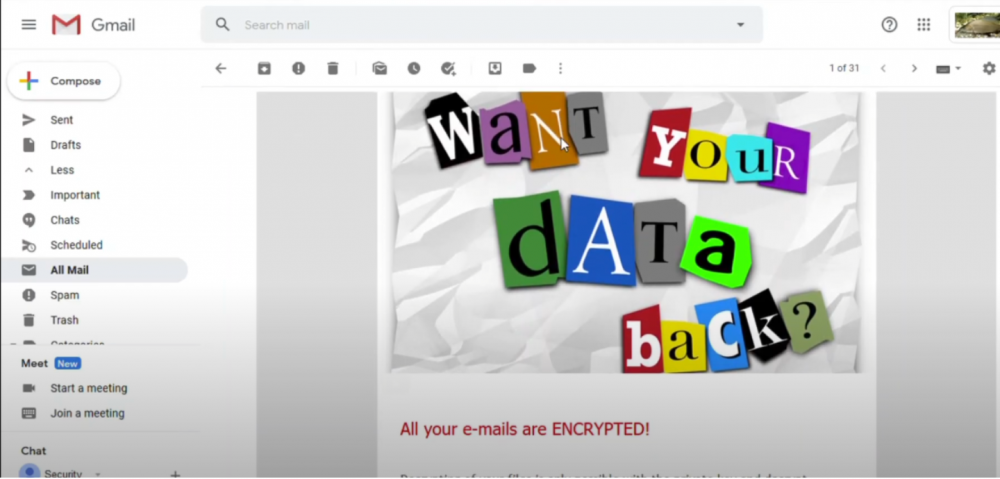
After the user grants the OAuth permissions request, the user’s email is encrypted, and they receive the ransom note via an email to the encrypted inbox.
Ransom request via email after a user’s inbox is encrypted
As we look ahead to 2023, malicious cloud SaaS applications will become more common. Attackers will use phishing campaigns in conjunction with OAuth permissions requests to attack mission-critical cloud SaaS data. As a result, organizations must control which cloud SaaS applications can integrate into the environment and provide an allowed list of applications users can install in the sanctioned cloud SaaS environment to protect sensitive data.
5. Increasing ransomware attacks on critical services
Look for increasing attacks on critical infrastructure services this coming year and beyond. As the attack on Colonial Pipeline shows, outages of critical infrastructure escalate quickly when people’s livelihoods are involved. Likewise, the danger posed by ransomware to essential services is escalating as more services rely on technology underneath the hood to power these systems. Ransomware groups know this fact. With ultra-critical infrastructure services, ransom demands can be much higher, and they are more likely to be paid.
Even with proper backups of business-critical systems and data, this is often not enough to bring services back up quickly. It is a gamble as some find the decryption process equally slow compared to restoring backups. In addition, using double extortion techniques, simply bringing services and data back online is not the only concern. Sensitive leaked data can be just as damaging as taking services offline.
Note the following ransomware attacks on critical infrastructure in 2021:
- May 2021 – Ransomware attack on Colonial Pipeline
- June 2021 – Ransomware attack on JBS meat-producing plans
- June 2021 – Martha’s Vineyard and Nantucket Steamship authority was a victim of ransomware
SpinOne Ransomware Protection for 2023 and beyond
SpinOne is a solution providing businesses with a proactive, artificial intelligence (AI) powered solution. It proactively stops and remediates ransomware attacks in your cloud SaaS environment. Key SpinOne capabilities allow companies to have visibility, control, and protection in cloud SaaS environments to stop ransomware before the damage critically impacts their business.
SpinOne’s Ransomware Protection uses cybersecurity automation to protect against ransomware as it:
- Performs real-time scans to detect ransomware
- Blocks the network source of the ransomware attack
- Scans to determine which files were affected by ransomware
- Automatically restores files that were encrypted
- Automatically notifies administrators of the ransomware attack and remediation
SpinOne provides continuous real-time Google Workspace Ransomware Protection of your cloud SaaS environment
Protecting SaaS data in cloud services like Google Workspace, Microsoft 365, and Salesforce is your responsibility. Stay safe and schedule a demo here.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...