Chrome Extensions Security Risks Every Business Should Be Aware Of
Chrome extensions offer users enhanced capabilities in productivity, customization, and overall user experience. They’re becoming increasingly popular. However, they can pose a great threat to individuals and businesses alike. This article dives deep into Chrome Extensions Security Risks and elaborates on the ways to mitigate them.
Understanding Chrome Extensions
Chrome extension is a type of software that is installed on the Chrome browser. They provide additional functionality to Google Chrome or other applications (e.g., Google Meet, Google Docs, Hubspot) when they’re opened in Google Chrome.
In the screenshot below, you can see several examples of Google Chrome extensions:
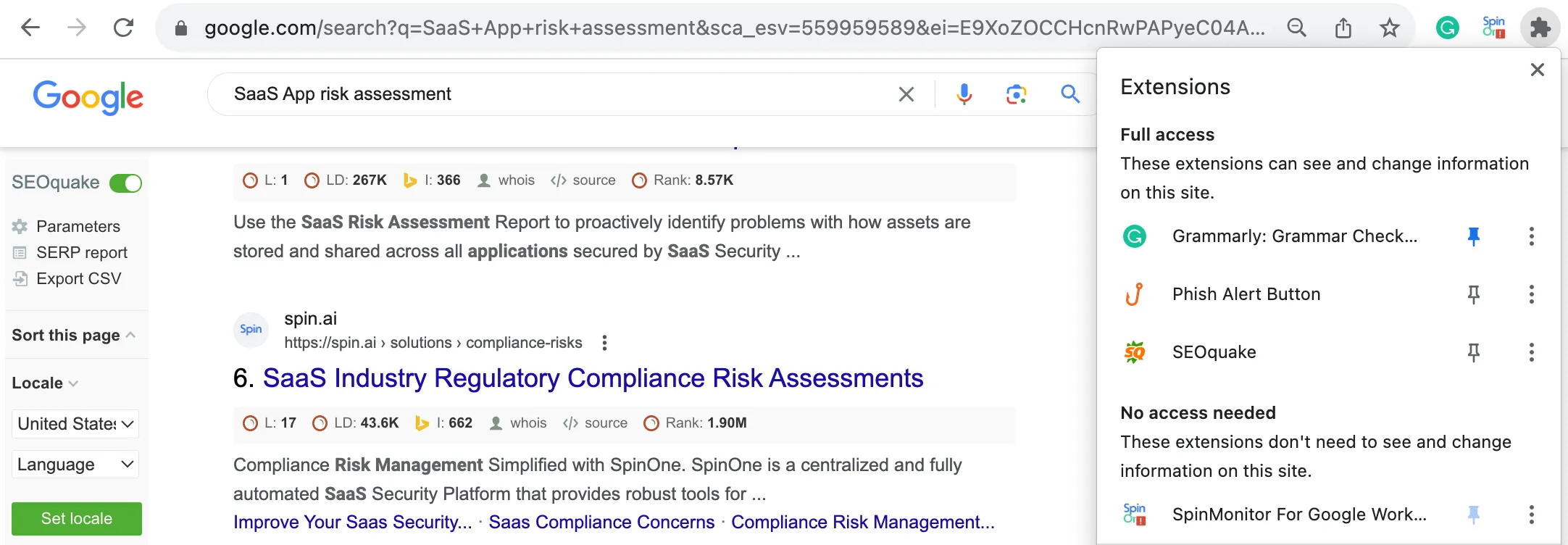
First, on the left side of the screen, there’s a panel of an SEOquake extension. This extension is used by marketers to study the Google SERP page. The extension shows how the SERP appears in different regions of the world and in different languages. It also demonstrates the SEO data of each page.
On the right side of the screen, you can see the panel with the extensions that are installed on this browser:
- Grammarly – extension for spell-checking in Google Docs and other websites.
- Phish Alert Button – extension for marking phishing emails in Gmail and email servers
- SpinMonitor for Google Workspace – extension for risk assessment and control over other Chrome extensions.
As you can see, Chrome extensions can change the way a certain website appears, just like SEOqueake does. They can access Google services that contain your private data, like the Phish Alert Button. They can read and edit your data like Grammarly. And they can ultimately control your Chrome extensions like SpinMonitor.
The benefits of Chrome Extensions:
1. Improved user experience
Chrome extensions can improve your experience as an Internet user. One of the best examples is an ad blocker. Although the time when websites reserved most space on the page for advertisements is gone, there are still media with distracting, flashy banners. It’s nice to have them removed.
2. Accessibility
Making the Internet accessible for everyone is one of the greatest benefits society-wide. We have many examples of accessibility design that was initially created for a certain group of people but is now used by everyone (e.g., text-to-speech, ramps). Accessibility also increases the quality of life of individuals with disabilities and makes them less dependent on their family, friends, and society overall.
3. Increased productivity
Many Chrome extensions help boost the productivity of employees. They offer a wide range of features that streamline your work processes. For example, Grammarly can not only check your grammar and spelling but also improve your writing style.
Despite all these benefits, Chrome extensions have many hidden risks and need diligent control by a company’s IT security team.
Chrome Extensions Security Risks
To understand the risks associated with Chrome extensions, we need to understand how they work. Basically, they aren’t very different from your regular SaaS Applications. Moreover, many SaaS apps have Chrome extensions.
When a person adds the extension to their Google Chrome, the extension gets access to the data and permissions to alter it. For example, the Loom screen recorder can capture your tab, page, or entire screen. It can also use a computer’s microphone and camera to record your voice and body. But that’s not all. It can also transcribe your speech into text.
Now, that’s where the risk for your company begins. Many employees use their work accounts to log in to Google Chrome. It’s much easier to have several “persons” in the browser, one designated for work, the other for personal use, and the third one for a family member, for example.
So, when your employee installs an extension on their Chrome designated for work, the extension gains access to the corporate data contained in their Google Workspace. In many cases, it also gets the editing permissions.
There are three potential problems with Google Chrome extensions:
1. Malfunction
The browser extension market is booming. Thousands of companies and individual developers are willing to profit from the popularity of extensions. Not all of them work diligently. In an attempt to make the extension ASAP, developers can cut corners and leave some unresolved bugs.
As a result, a malfunction can seriously undermine productivity and even result in unwanted data alterations.
2. Vulnerability exploits
Similarly, some developers do not make sure to detect and remove security vulnerabilities. As a result, cybercriminals can take advantage of this mistake. They can take over the extension and gain unauthorized access to the data of its users.
3. The extension was created by cyber criminals
Last but not least, a portion of extensions can be developed and uploaded by cybercriminals. They take advantage of the users who do not analyze the potential risks of the extension.
The above-mentioned issues pose multiple risks for your company:
1. Data leak
A data leak can occur as a result of extension malfunction or cyber-criminal activity. The latter is especially risky, as hackers seek access to data intentionally. Their goal is to:
- use it for other crimes, e.g., credit card fraud, blackmailing, etc.
- sell it to your competitors or on the Dark Web.
2. Data loss
It can occur as a result of Chrome extension’s malfunction. However, a hacker attack can also wipe data, for example, if they hold a personal grudge against your company or they want to show their capabilities.
3. Ransomware attack
Ransomware can infect Google Workspace. Your company will either have to pay ransom for the decryption key or face downtime. This type of incident can disrupt business operations for weeks or even months. Furthermore, the chances of fully recovering your data are around 40% even with a decryption key, while the chances of being attacked with ransomware for the second time are around 50%.
4. Downtime
The disruption caused by a major incident related to browser extensions, can result in a downtime and related financial losses.
5. Compliance risks
There are two main aspects to compliance. First, in case of data loss or leak, your company can face serious
Read more about it in our Browser Extensions Risk Report.
How to Secure Chrome from Malicious Extensions
One of the biggest challenges of Chrome Extensions security is their control. Google Workspace doesn’t have the necessary native tools to do it. So many extensions will operate under the radar and fall under the category of Shadow IT. This means that your IT security team will not be able to detect them and revoke their access.
Another problem is the scope of browser extensions that your company can have. A single employee can use several dozens of browser extensions. If the attack occurs, the investigation and search for the attack source will take an enormous amount of time for an environment that has hundreds of apps and extensions connected to it via OAuth.
The lack of “app hygiene” furthers this issue. There aren’t many individuals, who actually make sure to revoke access of the unused apps and browsers to their account.
The solution to the Chrome Extensions security risks is a security tool that controls them. An example of such a tool is SpinMonitor for Google Workspace.
SpinMonitor capabilities include:
- the detection of all the Chrome extensions installed on the browsers of your employees
- the creation of allow and block lists
- the risk assessment of the extensions
- the security policies to automatically block the extensions
- the automated process of requesting and allowing/denying the use of the extension.
For example, our own SpinMonitor blocks automatically all the browser extensions that our employees install. Then, if we need it for work or accessibility we can easily apply it right in Chrome. See an example of request:
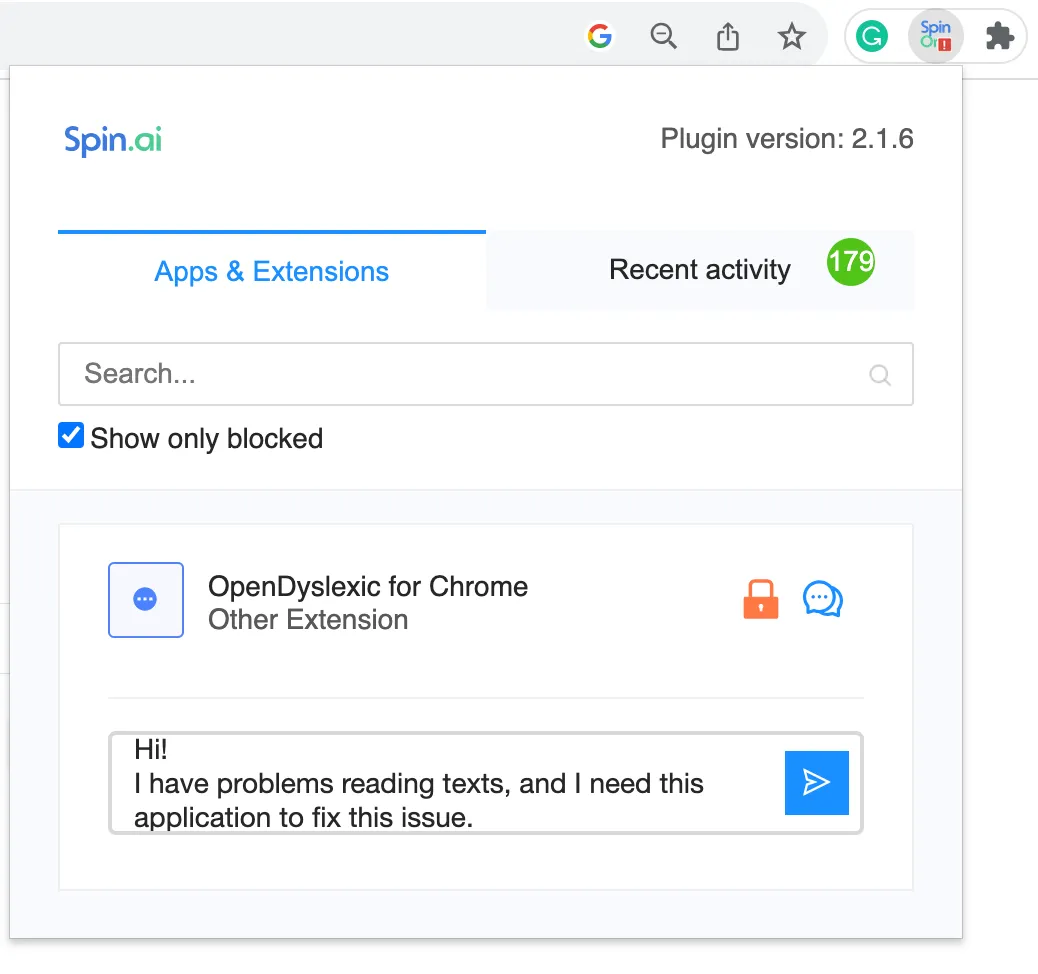
We use our tool to secure our corporate data and prevent multiple risks related to Google Chrome browser extensions.
Try SpinMonitor to enhance your data security.
FAQs
What risks are associated with browser extensions?
The risks associated with browser extensions are data loss, data leaks, ransomware attacks, downtime, and non-compliance.
How to determine if a browser extension is safe to use?
The criteria for browser extension safety include scope permissions, country of developer registration, and privacy policies.
What steps can businesses take to minimize extension-related risks?
What steps can businesses take to minimize extension-related risks?
To minimize extension-related risks, businesses should use tools that enable them to control browser extensions, for example, SpinMonitor.
Where should I download browser extensions from to ensure safety?
The place of download doesn’t ensure safety. However, using Chrome Web Store reduces your chances of getting a risky extension.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Top 12 Slack Security Best Practices In 2024
Slack might feel like the digital version of your office break room with quick chats,...
Backup Microsoft: Securing Critical Business Data Across Microsoft ...
We all know Microsoft is a behemoth with all types of critical products used by...
Unpacking the Browser Extension Threat Model
Mastering the Balance Between User Empowerment and Organizational Security Web browsers are not just passive...