Unpacking the Browser Extension Threat Model
Mastering the Balance Between User Empowerment and Organizational Security
Web browsers are not just passive recipients of the internet but active intermediaries between users, clients, and servers. Originating from the concept of a “user agent,” browsers flexibly interpret server data, allowing the client to decide how to present, transform, or discard information.
Browser extensions are a pure and powerful extension of this idea, empowering users to customize and automate their browsing experience by granting software privileged access to their browser. This privileged access can be deployed with dramatic effect: web pages can be styled and transformed to the user’s liking, keyboard and mouse actions can be automated, and network payloads can be dispatched on behalf of the user. Extensions allow the user to shape and define their own online environment, turning passive browsing into a deeply personalized and dynamic experience.
Users and businesses alike have taken notice of this power: extension marketplaces like the Chrome Web Store are replete with thousands of extensions that help users boost productivity, generate income, and streamline workflows. Entire businesses are built atop the browser extension platform, and the most popular extensions attract tens of millions of active users. However, the widespread adoption and deep level of access that browser extensions enjoy make them an attractive attack vector, so users and organizations must understand the ways in which browser extensions can be turned against them.
Security Risks and Challenges with Browser Extensions
Extension permissions are poorly understood or ignored
The reach of an extension is governed by the permissions granted to it, but the grant process is fraught with hazards. When a user is presented with the permission warning message, “This extension can read and change all your data on the websites you visit”, they likely do not understand that the extension will be given access to every network request in and out of the browser, everything you type, everything you see, every website you visit, and every authenticated account.
Extensions are implicitly trusted by users
The vast majority of extensions are installed from Google’s Chrome Web Store, and used inside the Google Chrome browser. This Google “branding” invites trust in extensions that is not earned. Although extensions are subjected to a review process before they become publicly available through Google’s extension marketplace, malicious extensions can and do sneak through. Furthermore, extension reviews can be cheaply purchased, and are not subject to any verification.
Extensions have limited paths to monetization
Unlike mobile app marketplaces featuring first-class support for purchases and payment rails, extensions lack any formal infrastructure for developers to charge money for extensions. Traditional web payment processors are still at their disposal, but developers who wish to charge money for their extensions must resort to ad-hoc signup flows and feature-gating. Extensions are also denied traditional paths to monetization used by the rest of the web, such as digital advertisements. Marketplaces such as the Chrome Web Store forbid injecting advertisements into web pages, but also disallow the use of advertising networks like AdSense to render ads inside the extension itself. As a result, extension developers presented with an opportunity to sell their extension might not be picky about who the buyer is.
Extension permissions are dynamic
Extension developers are able to push updates that request permissions beyond what was initially granted upon install. Consequently, the purpose and reach of an extension can profoundly inflate over time. Users will still need to explicitly approve access to additional sensitive permissions, but in many cases the added permissions will not require approval and will be silently added. These latent permissions can pose a potential data leak or non-compliance incident in the future.
Extension ownership changes can occur abruptly and silently
Extensions with large userbases are high-value targets for acquisition. Handoffs for these extensions often occur on escrow websites, and sometimes the acquiring entity requires a handoff of the developer’s email as part of the transaction, making the change of ownership entirely undetectable.
The Threat of Malicious Extensions with Broad Permissions
Once installed, a malicious extension with broad permissions can do almost unlimited damage.
Extensions can behave as an agent of the user. Even with highly secure authentication patterns such as OAuth or 2-factor TOTP, an authenticated session is compromised if a malicious extension has permissions on that hostname.
Detection of malicious extensions is extremely difficult. Detecting malicious code in an extension’s bundle is slow and extremely expensive, and therefore infeasible at the scale of an extension marketplace. Modern web bundlers are highly adept at compiling codebases into an inscrutable mess, and the flexibility of the JavaScript language enables highly sophisticated manual obfuscation of dangerous code paths. When analyzing network traffic, a malicious extension communicating with a C2 server is nearly indistinguishable from a benevolent extension collecting telemetry or analytics.
Notable Incidents Involving Malicious Extensions
Malicious actors have taken notice of this.
- The PDF Toolbox Chrome extension secretly allowed a third-party site to inject malicious JavaScript into users’ browsers.
- A new trojan malware campaign infected over 300,000 users by installing OS-level malware via fake download sites, which then modified the system registry to forcibly install malicious extensions and prevent their removal.
- An analysis of the Chrome Web Store by Kaspersky revealed malicious Chrome extensions that were downloaded more than 87 million times
- The malicious Aggr Chrome extension was used to drain $1 million from a Binance account
- An extension masquerading as a benign ChatGPT extension stole cookies of all authorized active sessions and installed a backdoor that gave the malware author super-admin permissions to the user’s Facebook account.
- Browser extensions were caught collecting sensitive user data, including browsing histories, which were then exposed through a service called Nacho Analytics, impacting millions of users and numerous companies.
- Security conferences routinely feature programs on how extensions are used to target developers
The purpose of aggregating these exploits is not to elicit fear, but rather to demonstrate the serious and measured consideration this software platform deserves. The extension platform captures the best aspects of the internet: users should be afforded a high degree of control and autonomy with respect to how their web browsers behave. What’s more, extensions are essential for safe web browsing. Ad blockers and password managers are two of the most effective tools for protecting privacy and security; to wit, the FBI officially recommends the use of an ad blocking extension.
Beyond the realm of protecting users, businesses and organizations stand to benefit from multiplicative productivity gains, driven directly by the effective use of extensions; yet by the same token, a single compromised account within an organization almost guarantees a systemic security breach. Fortunately, every organization is capable of mitigating risks from malicious extensions with a deliberate and considered approach.
Strategies for Mitigating Extension Risks and Strengthening Security
Set an aggressive corporate extension install policy
Administrators can enforce organization-wide policies that govern precisely how employee browsers are allowed to handle extensions. Google’s Chrome Enterprise extension policy allows five degrees of control over installation policy:
- ExtensionInstallSources controls where extensions can be installed from. This is useful for restricting side-loading of extensions.
- ExtensionInstallAllowlist controls extensions that the user is allowed to install, but are not required.
- ExtensionInstallForcelist controls which extensions are automatically installed and updated by the browser. Ad blockers, password managers, and third-party vendor extensions deemed necessary for employees can be listed here.
- ExtensionInstallBlocklist controls extensions that are not allowed to be installed. Commonly, this is set to disable all extensions that are not explicitly enumerated by the ExtensionInstallAllowlist or ExtensionInstallForcelist.
- ExtensionAllowedTypes controls the allowed extension variants. Overwhelmingly, all extensions you will ever install are of type “extension”, so this setting has negligible utility.
Chrome Enterprise also allows you control over allowed/restricted permissions via the Extension Settings policy. These can be set browser-wide, or only for specific extensions. Specifying these values can significantly mitigate security vulnerabilities, but when applied too broadly they can cripple benevolent extensions:
- blocked_permissions controls permissions that are disallowed. Extensions that request these permissions will be totally denied access to the underlying interface or JavaScript API corresponding to the permission.
- runtime_allowed_hosts controls which hosts an extension should have access to. This is useful if you know ahead of time which hostnames an extension will need to access.
- runtime_blocked_hosts controls which hosts an extension must not access. This is useful if you wish to explicitly protect domains from extension access – your sensitive email account domains, corporate intranet, sensitive financial domains, etc.
Learn to evaluate extension risk
Evaluating an extension for risk should be a combination of factors:
- What permissions does this extension require, and why? Though you may not always be able to discern why an extension needs a permission, an extension that requests additional permissions after updating should always be closely scrutinized.
- Who owns and operates this extension? An extension written by Adobe should be trusted more than a faceless GMail address.
- How does this extension make money? If it’s not clear how an extension makes money, be wary. These extensions might be selling data, or might entertain acquisition offers from bad actors.
- Is the extension communicating with other domains, and in what capacity? An extension sending traffic to an untrusted domain should ring alarm bells.
- Does the extension supply privacy policies or compliance reports? Reputable extensions should provide clear documentation on data handling and compliance. A lack of these reports may signal low transparency or weak adherence to best practices, suggesting potential risk.
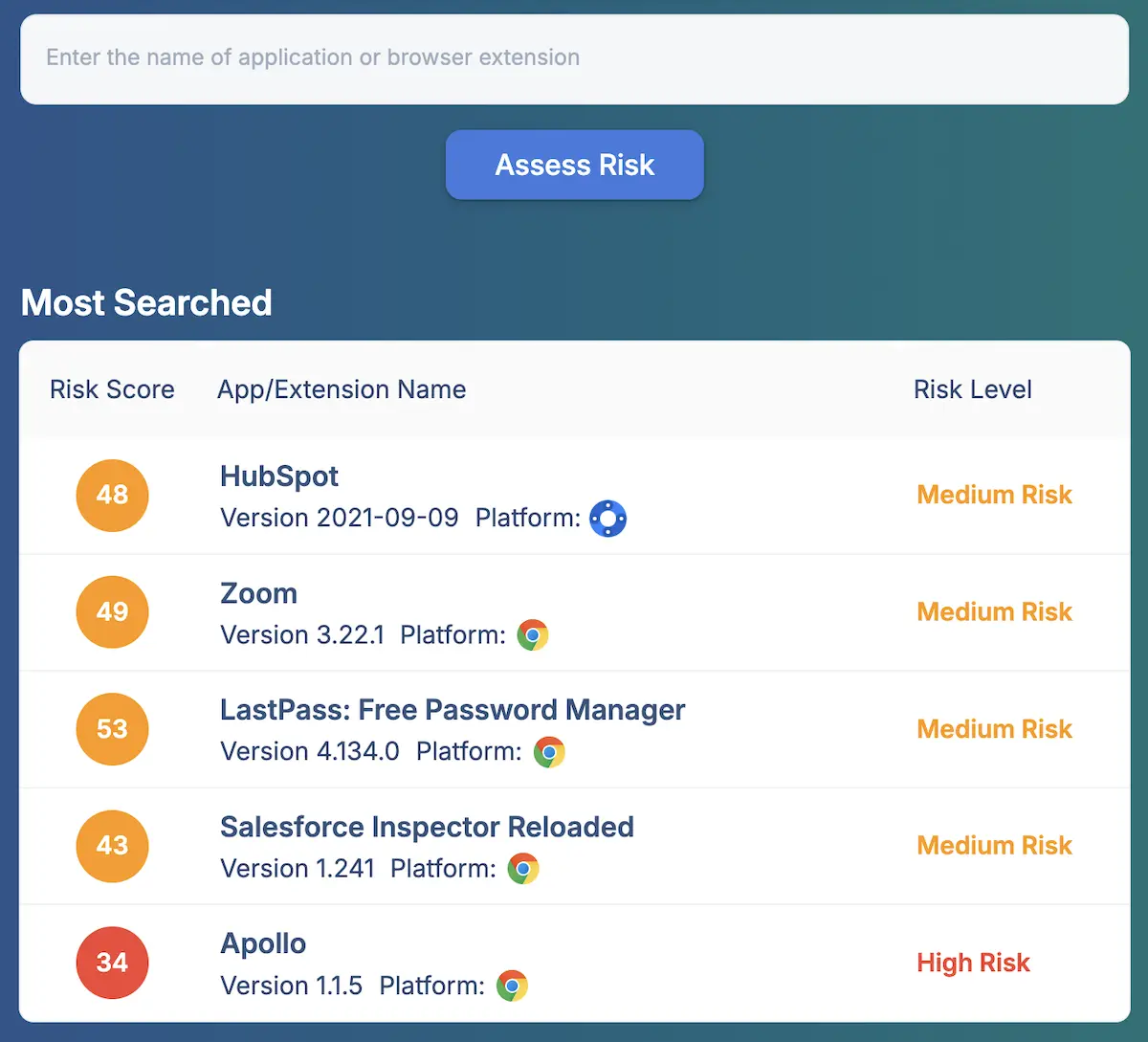
Perform regular security audits
Stagnant security is bad security. Extensions change over time, software policies need revision, and organisational needs evolve. Audit your company’s extension policies and risk management strategies regularly, ensuring each of the above extension risk factors is addressed. Spin.AI’s Browser Extension Risk Assessment tool streamlines this process, offering real-time insights into extension behaviours, permissions, and potential vulnerabilities. Integrated directly into the Google Workspace Admin Console, Spin.AI’s tool empowers security teams to continuously monitor and manage extension risks, providing audit-ready reporting and ensuring your enterprise stays ahead of potential threats.
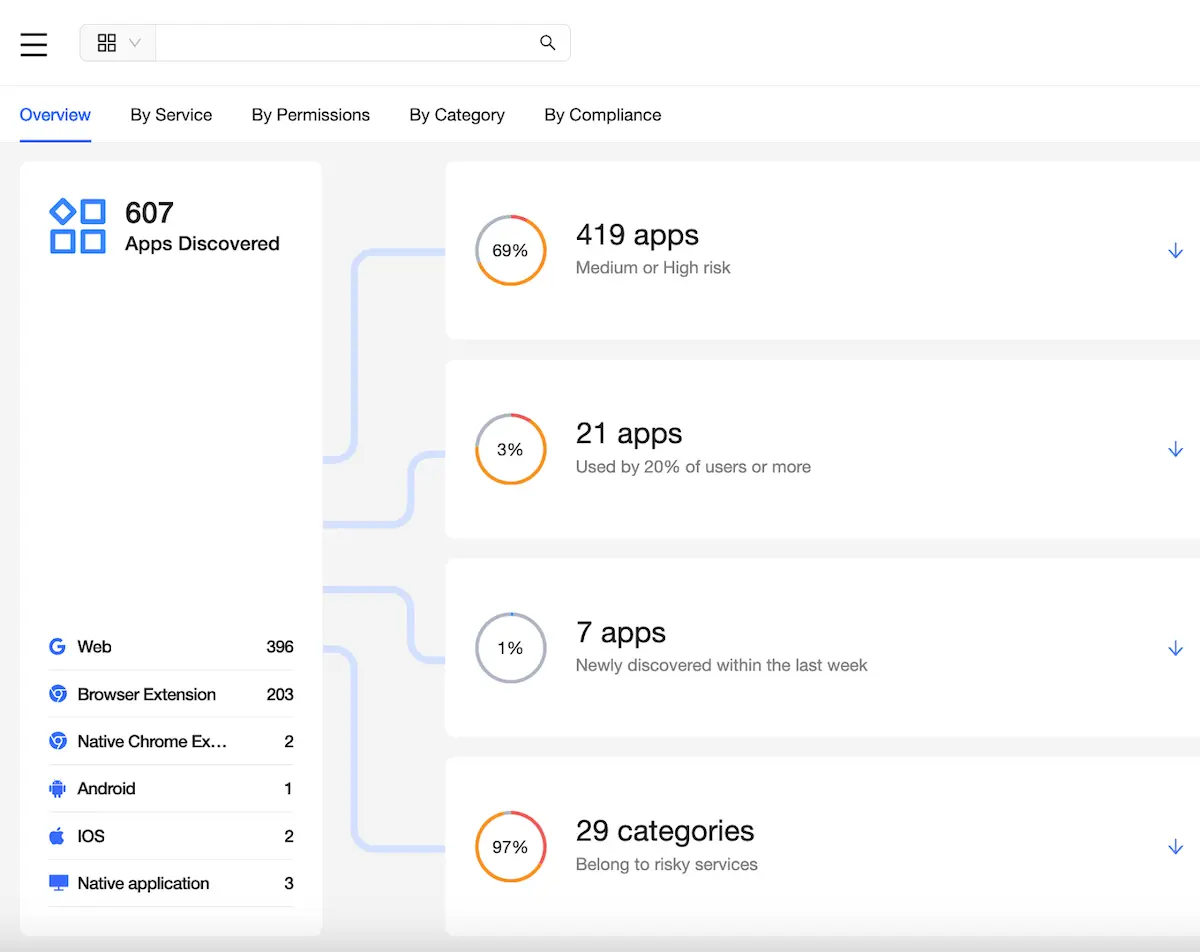
Enlist the expertise of security companies
Enterprise security is not the place for ad-hoc solutions or half-measures. Cybercriminals are more skilled than ever, attacks are increasingly sophisticated, and the attack surface of an organization grows exponentially with its headcount. Platforms like Spin.AI provide you with a broad and deep toolkit to protect your organization from all types of threats, especially malicious extensions. Take advantage of Spin.AI’s free risk assessment tool now , and ensure your organization is equipped to face today’s ever-evolving security challenges.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...

