Ultimate Cloud Compliance Guide for Businesses
Data is becoming more centralized to the cloud, instead of on-premises. This is creating exciting opportunities for innovation and agility. However, cloud infrastructure is creating complexities when it comes to the world of security and cloud compliance regulations.
There are many incredibly interesting and fast-moving currents in the public cloud movement for information technology landscapes today. The enterprise’s digital landscape is increasingly cloud-based and intricate. Hybrid networks link on-premises solutions to public clouds, and public clouds to each other. This is creating multi-cloud environments, spanning public cloud vendors and often numerous on-premises sites.
Compliance is becoming an increasingly important aspect of housing data, both on-premises and in the public cloud. Compliance regulations today are driving where data can be housed, who it can be shared with, who owns it, what it can contain, and many other important characteristics. In migrating data to the public cloud, businesses need to be aware of compliance requirements, public cloud considerations, and what tools are available to help meet compliance regulations.
In this post, we will take a look at an ultimate regulatory compliance guide for Google Workspace and Office 365 to see specifically how compliance regulations pertain to two of the most popular Software-as-a-Service offerings in the public cloud today.
What is Compliance?
Compliance is a common word tossed around in the context of infrastructure and technology solutions, and rightly so. Compliance is an extremely important consideration for businesses since it helps to build customer confidence and trust as well as meet legal requirements across various industries. It is set to only increase in its importance in years to come. This is mainly due to the sheer volume of data that is being collected, transmitted, stored, and otherwise consumed across today’s business landscapes.
To understand compliance better, let’s start by defining what it is exactly. The definition of compliance as defined by the dictionary is the action or fact of complying with a wish or command. To put that in context, when thinking about compliance in terms of security and data governance/regulation, compliance can be looked at like a security blueprint that realistically provides a minimum bar of security in relation to the specific type of compliance involved.
Auditing is the way that compliance is enforced. When an audit takes place, it is basically a snapshot of how the organization currently measures up in relation to that compliance blueprint benchmark.
As mentioned, for most, the compliance regulation is only a minimum set of security-related standards and governance. Organizations would be mistaken to feel that meeting with a specific compliance regulation is the “end all be all” of achieving good security. With security and compliance, there is always room to strengthen and fortify the stance as compliance regulations are generally a minimum level of standards that need to be implemented. Regulations set a cloud compliance framework of security and best practices that are necessary and required in many sectors.
What are common compliance regulations in place that organizations today are commonly required to maintain? There are many compliance regulations out there related to various industries. Regulations such as HIPAA, PCI-DSS, NIST, CSA, ISO, and let’s not forget GDPR mean various implications for businesses.
- HIPAA – Health Insurance Portability and Accountability Act – Helps to ensure security and privacy standards to protect all patient records and health information as used by medical organizations and their subsidiaries
- PCI-DSS – Payment Card Industry Data Security Standard.
- NIST – National Institute of Standards and Technology provides security recommendations for Information Technology, allowing organizations to become NIST compliant.
- CSA – Cloud Security Alliance – This provides best practices for security and compliance in the realm of public cloud
- ISO – International Standards Organization provides guidelines to guarantee quality, security, and safety in accordance with best practices set forth.
- GDPR – General Data Protection Regulation – A new set of data privacy and security regulations set forth by the European Union to ensure data privacy, right to ownership of data, and the right to be forgotten to be entrusted to the individual
The above-mentioned compliance regulations are some of the more prevalent compliance regulations that organizations fall under today. However, these represent only a small subset of the compliance regulations that businesses are required to comply with across various regions, countries, and other verticals. There are many other security and compliance regulations that may need to be considered depending on the industry, location, size of business, type of business, and other factors.
Compliance Challenges
There are many challenges when it comes to compliance. Businesses that operate across different locations and infrastructure landscapes may be subject to numerous compliance regulations, all with different requirements and complexities. One location may be subject to one type of compliance and other compliance regulations may be imposed in another location.
New regulations such as General Data Protection Regulation or GDPR are only beginning to be understood with various nuances and considerations that prove to be difficult to understand or are left open to interpretation. There has been a flurry of litigation sparked by the new GDPR regulation taking effect, much of which surrounds interpretation of its various components.
GDPR is only the beginning as it only affects those businesses in the EU or doing business with customers in the EU. New rumblings of data protection regulations across many other regions are rumored to be on the table and will most likely become reality over the next few years.
On top of the difficulty of fully understanding the various aspects of numerous compliance regulations, it can be difficult for many businesses, especially small or medium-sized businesses, to have the resources and skills needed in current staff to manage compliance regulations and complete risk assessments and other duties required properly. Properly implementing, assessing, and auditing for compliance internally can be a full-time job for those with the skills to complete those tasks.
Additional compliance challenges are added with today’s very complex and diverse infrastructure as well as increasingly diverse end-user client devices that may be used to access data. Data no longer resides solely in the confines of “nice and easy” on-premises infrastructure. Today’s businesses are utilizing infrastructure across a wide range of infrastructure configurations, including the use of public cloud, hybrid cloud, and multi-cloud environments. This means that data can be traversing between on-premises, the cloud, and between clouds.
Often businesses may use third-party solutions or entities to perform certain tasks and subsets of the business process. Organizations must consider the effect and impact on compliance with these partnerships and ensure that data is safe across the entire pipeline. This is where businesses must give attention to the compliance certifications of these third-party partners and ensure these comply with the given requirements and can prove they can do this effectively.
Cloud Compliance
Businesses and business leaders today are not simply encouraged, but expected to champion security across all fronts, including IT infrastructure and data security. Over the past few years, we have seen a data revolution that is literally changing the paradigm of how companies view data and the importance of protecting and securing it.
Today, hackers or “bad actors” as they are sometimes called, are going to great lengths to steal data. Data is the new gold of this century as it holds the key to everything. Modern IT infrastructure is there simply as a conduit for data storage, exchange, transmission, and consumption. The importance of the intrinsic value of the data itself, cannot be underscored and emphasized enough.
Businesses today are utilizing cloud computing more than ever before. As they do, data is becoming more and more decentralized and is becoming spread between multiple on-premises locations as well as between on-premises and public cloud and even between different public cloud vendors. In traditional enterprise datacenter environments, typically much of the compliance regulation information gathering is an extremely manual process. This means that many operations teams are tasked with manual auditing of infrastructure, flows, and other operations environment details to determine compliance scope and so forth.
The problem with this is that once public cloud, hybrid cloud, or even multi-cloud environments are introduced into the mix, there is can be additional complexity in understanding the scopes and flows between the various environments. Understanding the scope when public cloud environments are in play can be even more difficult since much of the infrastructure is abstracted away with the public cloud.
On top of the challenge of lessened visibility perhaps into the underlying infrastructure with public cloud, multi-cloud environments often have different processes and tooling between the various public cloud providers. This can present challenges with processes and information gathering on the side of operations to properly see the information needed for compliance and governance.
Google Workspace and Office 365 Public Cloud Compliance Tools
Since compliance is a top priority for businesses today making use of public cloud environments and this will certainly not diminish, public cloud vendors have seen the need to provide compliance tools inside the public cloud environment itself to help tenants ensure meeting compliance regulations effectively.
Google Workspace and Microsoft’s Office 365 Software-as-a-Service environments are two of the most widely used SaaS environments found in the enterprise today. Businesses today are using these public cloud giants and their SaaS offerings to perform many business-critical tasks. What types of technologies and tooling are provided to customers using these SaaS environments to help assist with today’s compliance regulations?
Google Workspace Compliance
Google Workspace is backed by a long list of independent security assessments and certifications. Google Workspace meets the following certification standards and regulatory compliance:
- ISO 27001
- ISO 27017
- ISO 27018
- SOC 2/3
- FedRAMP
- PCI DSS
- FISC Compliance
- Esquema Nacional de Seguridad (ENS) Spain
- HIPAA
- EU Model Contract Clauses
- General Data Protection Regulation (GDPR)
- U.S. FERPA
- COPPA
- South Africa’s POPI Act
Google Workspace provides numerous tools to assist in allowing organizations to more easily achieve their compliance objectives in regards to compliance and regulatory obligations. What are some of the tools that can be helpful for organizations to make use of in order to meet compliance objectives?
Data retention and eDiscovery – Google Vault is a tool that allows businesses to retain, archive, search, and export organizations’ email for eDiscovery purposes and compliance needs. It is easily accessed since it is web-based and no additional software is needed for organizations to make use of this tool.
What can be done with Vault? Organizations can search Gmail, Drive, and Groups data, configure retention policies, place litigation holds on user accounts and point-in-time Drive files. Additionally, it allows exporting specific emails, chats, and files to numerous formats to allow additional review and investigation if need be.

Google provides compliance with today’s toughest standards (image courtesy of Google)
Google provides monitoring tools for organization administrators to be able to use to scan email messages for various patterns they want to match in order to maintain various compliance regulations in regards to enforcing the content of email messages to reject them before they reach recipients or alter them to include modifications.
Google Workspace also provides monitoring and reporting that allows administrators to be able to assess security issues at a domain and user level. API access allows businesses to be able to query these monitoring tools programmatically and also build custom tools from a security standpoint that interact with these APIs.
Much of compliance is about auditing as this is the way organizations can tell if they are measuring up to the compliance regulations and various aspects of the standards enforced. Auditing user actions is essential.
Google Workspace allows administrators to track user actions and set custom alert rules to flag various user actions and notify administrators of that action. An example would be if a user downloaded a file that is marked “confidential” or contained any other sensitive information that is specified by the administrator. This allows administrators to be proactive in the auditing and compliance stance.
What other security features are provided by Google Workspace to administrators?
- User authentication/authorization features
- 2-step verification
- Security key
- Single sign-on (SAML 2.0)
- OAuth 2.0 and OpenID Connect
- Data management features
- Information Rights Management (IRM)
- Drive audit log
- Drive content compliance/alerting
- Trusted domains for drive sharing
- Email security features
- Secure transport (TLS) enforcement
- Phishing prevention
- Data Loss Prevention (DLP) for Gmail
- Email content compliance
- Objectionable content
- Restricted email delivery
- eDiscovery features
- Email retention policy
- Legal holds
- Search/discovery
- Evidence export
- Support for third-party email platforms
- Securing Endpoints
- Mobile device management (MDM)
- Policy-based Chrome browser security
- Chrome device management
- Data recovery
- Restore a recently deleted user
- Restore a user’s Drive or Gmail data
- Security Reporting
As you can see, there is a wide range of tools provided by Google via the Google Workspace platform that allows for securing the environment and give administrators a good range of features and functionality for both security and compliance objectives.
Microsoft Office 365 Compliance
Microsoft touts having over 900 controls in the Office 365 compliance framework that enables them to stay up to date with ever-evolving industry standards. In addition, they have a specialist compliance team that continuously tracks standards and regulations, developing control sets for the product team. Microsoft’s Office 365 SaaS solution contains a list of industry-recognized compliance certifications including the following:
- Argentina PDPA
- CSA-CCM
- CS Mark (Gold)
- DISA
- ENISA IAF
- EU Model Clauses
- FDA 21 CFR Part 11
- FedRAMP
- FERPA
- FIPS 140-2
- FISC
- FISMA
- GxP
- HIPAA / HITECH
- CCSL (IRAP)
- ISO/IEC 27001
- ISO/IEC 27018
- Japan My Number Act
- MTCS
- NZ CC Framework
- Section 508 / VPATs
- SHARED ASSESSMENTS
- SOC-1
- SOC-2
- ENS Spain
- UK G-Cloud
A couple of notes from Microsoft:
- The PCI standard is not applicable to Office 365 or Microsoft Dynamics CRM Online, because credit card processing and data storage is not a function offered by Office 365 or Microsoft Dynamics CRM Online.
- Microsoft offers solutions to help discover and protect personal data in Office 365, however, it is not offered as a GDPR compliance attestation.
Microsoft’s Office 365 solution provides numerous tools to help organizations meet various compliance regulations effectively. What are some of these?
Service Trust Portal contains details about Microsoft’s implementation of controls and processes that protect cloud services and customer data.
The Office 365 Compliance Manager application is a workflow-based risk assessment tool that provides tools to track, implement, and manage the auditing controls to help your organization reach compliance against many different standards. It can help organizations with various compliance and regulatory initiatives such as the General Data Protection Regulation (GDPR).
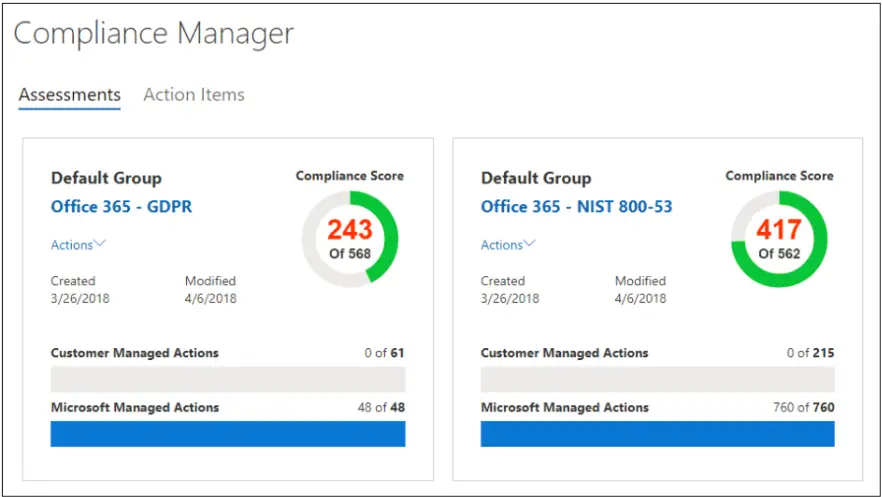
Office 365 Compliance Manager (Image courtesy of Microsoft)
To help manage GDPR Data Subject Requests or DSRs, Microsoft has the DSR case tool that helps to manage investigations in response to these DSRs submitted by a person in your organization. It can find content stored across Office 365 ecosystems, control who has access to DSR cases, export data, and delete cases when complete.
Office 365 Security Incident Response helps organizations to know what an attack on Office 365 looks like and helps to implement Microsoft’s recommended best practices for security Office 365 tenants.
Microsoft provides a wide variety of other security-related tools that go hand in hand with compliance requirements. These include:
- Security & Compliance Center
- Office 365 Cloud App Security
- Threat management
- Advanced threat management
- Mobile device management
- Data loss prevention
- Data governance
- Advanced data governance
- Search and investigation
- eDiscovery search/li>
- eDiscovery export
- eDiscovery holds
- Advanced eDiscovery
- Archiving
Microsoft is continuing to introduce new security and compliance tools to help Office 365 tenants to meet the demands of compliance regulations required.
Are Native Public Cloud Security & Compliance Tools Enough?
You might ask, with all the native tools that are provided by Google Workspace and Microsoft Office 365, why would there be any additional concerns over compliance or security tooling in these leading public cloud SaaS environments? While the tools provided by public cloud vendors are certainly welcomed tools in being able to meet compliance regulations effectively, there are gaps when it comes to covering the various aspects of compliance requirements that organizations will want to think about. What are those?
- Lack of native data protection
- Disjointed and nonuniform tooling
- No single pane of glass view
- Security and Compliance tools determined by subscription levels
The above are a few of the concerns when looking at the security and compliance tools that are built into both Google Workspace and Microsoft Office 365 platforms. Let’s briefly look at these areas one by one.
Lack of Native Cloud Data Protection
This is a huge weakness of current public cloud SaaS environments today. There is no true enterprise-grade native data protection found in either Google Workspace or Office 365. Microsoft recently added file revision rollbacks for OneDrive that allows recovering or rolling files to previous versions in OneDrive for up to 30 days.
However, this does not include any other Office 365 services such as email, etc, and as mentioned, is limited to 30 days’ worth of changes. Google Workspace only has the ability to recover deleted items up to 25 days at this point but doesn’t even have the ability to restore a previous file version.
Why is data protection important? Data protection not only protects data from loss but also plays an extremely important role in an organization’s overall security and compliance strategy. This includes e-discovery, governance, and proof of compliance. The need to protect and be able to restore data is only going to become more and more important, both on-premises and in the public cloud.
The lack of native data protection tools and capabilities in public cloud services offered in Google Workspace and Office 365 are extremely concerning when it comes to both security and compliance objectives.
Disjointed and Nonuniform Tooling
Quite frankly, one of the most challenging aspects of public cloud services and capabilities are the overwhelming number of tools and dashboards that customers need to know about and navigate to in performing various operations. This includes compliance and security operations and tasks. When you look at the list of tools that we have mentioned above for both Google Workspace and Office 365, it can be incredibly challenging to have centralized control and visibility of all the aspects and nuances of security in the public cloud.
No Single Pane of Glass View
This point dovetails into the last point made. Having a centralized single pane of glass view can pay huge dividends in terms of effective security and compliance as well as efficiency. The large number of tools provided that take care of the various aspects of compliance and security in the respective environments can be confusing. This can lead to a lack of visibility and gaps in both security and compliance in general.
Security and Compliance Tools Determined by Subscription Levels
One of the concerning aspects of security and compliance in the public cloud is that certain tools are withheld from customers depending on the subscription level of their public cloud SaaS subscription. A great example of this is with Office 365, various tools such as Office 365 Cloud App Security, Advanced threat management, and Data loss prevention are only available in the upper-level subscriptions such as the Office 365 Enterprise E5 subscription.
This is also the case with Google Workspace tools with such tools and services as the security center for G Suite, Data Loss Prevention for Gmail/Drive, and enterprise-grade access control with security key being held out for only the Enterprise Level subscription.
Ultimate Compliance Tool for Google Workspace and Office 365
Organizations can certainly fill in the gaps of the natively offered security and compliance tools found in Google Workspace and Office 365 with Spinbackup. Spinbackup provides an intelligent, easy approach to security and compliance in the public cloud. It allows organizations to be intelligent about security and compliance by providing a single pane of glass view of the public cloud environment and security and compliance threats found. It does this with powerful machine learning algorithms that constantly watch environments for threats.
Spinbackup stands alone in its class as the only solution to provide both security AND data protection in the same product for Google Workspace and Office 365!
- Automated Daily Backups
- Data Loss Prevention
- Insider Threat Detection
- Data Leak Protection
- Automated Ransomware Protection
- Third-Party Apps Control
- Proactive Security Alerting
- Security Policies
Start a Free 15-day Trial of Spinbackup for Google Workspace or Office 365:
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...


