Cyberthreats – What to expect in 2023
Businesses face a multitude of challenges, including those resulting from cybersecurity threats. The years 2021 -2022 proved to be a landmark regarding cybersecurity threats, ransomware attacks, and vulnerabilities. Unfortunately, the landscape of cyber threats, vulnerabilities, and compliance challenges is not improving. So, looking ahead to 2023 and beyond, what can we expect regarding the threat landscape? What cyberthreats do businesses need to defend against, and how can they successfully protect their business-critical assets, both on-premises and in the cloud?
Cyberthreats – What to expect in 2023
The consensus among cybersecurity experts is that ransomware is now the number one threat to an organization’s business-critical data. Security experts at Cybersecurity Ventures predict the frequency of ransomware attacks over the next five years to increase and reach a frequency of an attack every two seconds by 2031.
In 2021, major ransomware attacks increased in frequency and scope, including critical infrastructure services. For example, in late April 2021, Colonial Pipeline, a major fuel supplier to the Eastern Seaboard of the United States, was attacked with ransomware using stolen VPN credentials, shutting down the fuel supply for days and leading to fuel shortages to the general public.
JBS Meat Packing, responsible for a large percentage of the meat supply worldwide, was attacked with ransomware, shutting down production and affecting supplies. JBS reportedly paid an $11 million ransom to restore access to critical files. These attacks on critical infrastructure services placed organizations worldwide on high alert and demonstrated just how quickly and easily a significant ransomware attack can wreak havoc on the general public.
There are two developments in ransomware leading to the proliferation of attacks worldwide. These include:
- Ransomware-as-a-Service (RaaS)
- Initial Access Brokers (IABs)
Another phenomenon adding to the increase in ransomware attacks is the growing Shadow IT.
Ransomware-as-a-Service (RaaS)
In the early years of ransomware, attackers had to be very skilled developers who could develop the malicious code, compromise a victim’s network, manage the ransom payment, and all the other details involved in a successful attack. These tasks could require high skill levels to carry out an attack from start to finish. By default, these requirements eliminated the majority of novice to intermediate hackers.
However, things have changed. One of the new and very ominous developments on the dark web is the appearance of Ransomware-as-a-Service (RaaS) offerings. Ransomware groups are now offering RaaS to make easy money and commoditize the use of malicious code by attackers of all skill levels. If a RaaS attack is successful and the ransom is paid, the ransomware group takes a percentage of the ransom payment.
When you think about how legitimate Software-as-a-Service (SaaS) platforms work, customers do not have to understand the inner workings of the underlying infrastructure and code. Instead, they simply consume the application as-a-Service. Unfortunately, the same is now true with RaaS offerings from ransomware groups. Conceivably, even attackers with little to no coding experience can now carry out a successful ransomware attack by using the tools provided by the RaaS service. Another key to the growing number of ransomware attacks is Initial Access Brokers (IABs).
Initial Access Brokers (IABs)
Another development leading to the significant increase in ransomware attacks is the appearance of the Initial Access Broker (IAB) market on the dark web. IABs commoditize attackers obtaining legitimate, high-level credentials quickly. IABs phish or obtain legitimate credentials using various means at their disposal and then post these for sale on the dark web.
Depending on the gross yearly revenue of the business and the system permissions of the compromised user, the amount IABs charge is based on this amount. When coupled with the capabilities provided by Ransomware-as-a-Service, attackers who gain credentials from an IAB have everything they need to quickly launch a sophisticated and very damaging attack on a victim organization. The IAB market has been growing and is making the initial compromise of a victim organization a simple business transaction on the dark web.
Ransomware-as-a-Service and Initial Access Brokers have a very symbiotic relationship with one another. IABs make it extremely easy for RaaS customers to gain entry into victim’s networks, and RaaS offerings provide the market for the credentials sold by IABs. Together they combine to form a potent malicious cocktail leading to lost or exfiltrated data, lost revenue, and even disrupted infrastructure services with successful attacks on critical services.
How can businesses protect against cyber threats in 2023?
Many attack vectors that allow cybercriminals to compromise an organization’s business-critical data are not new. These include risks that come from:
- Improperly secured or vulnerable remote access technologies
- Compromised or stolen credentials
- Critical vulnerabilities
- Cloud infrastructure and cloud SaaS environments
Improperly secured or vulnerable remote access technologies
Many organizations are continuing to use a hybrid workforce. The hybrid workforce requires remote access tools that allow communication, collaboration, and productivity tools to carry out critical tasks. Attackers know this and often target improperly secured or vulnerable remote access technologies such as Remote Desktop servers that may be insecurely exposed to the Internet.
VPNs are also commonly used for remote employees. However, as demonstrated in the ransomware attack on Colonial Pipeline, compromised VPN credentials can allow an attacker to enter the internal network. As a result, organizations need to ensure remote access technologies are adequately secured and use multi-factor authentication.
RDP servers are commonly attacked and compromised due to vulnerabilities. Using Remote Desktop Gateways to tunnel RDP traffic is a much more secure way to use RDP for remote access or use other technologies besides RDP altogether. Again, multi-factor authentication is crucial to prevent compromised credentials allowing easy access to internal resources.
Compromised or stolen credentials
Suppose an attacker is able to gain knowledge of a user password without multi-factor authentication. In that case, they essentially become that user and assume all the expressed permissions and privileges the user account possesses. It is dangerous, especially if the user account is a privileged administrator account. Therefore, organizations must use strong password policies combined with multi-factor authentication to help secure user credentials in the environment.
Monitoring failed login attempts and gaining visibility to evidence of brute force attacks and other malicious attempts in the environment is essential to defending business-critical resources from today’s cyberattacks.
Critical vulnerabilities
Another essential area of securing business-critical data is securing against critical vulnerabilities. Therefore, organizations must maintain a healthy schedule of security patching. This practice helps to ensure systems are patched as soon as possible against critical flaws or vulnerabilities that can allow an attacker to gain unauthorized access and carry out an attack. Zero-day vulnerabilities may be disclosed with little warning. So, businesses need to have a process to perform emergency security patches regardless of change control processes for regular patching and other software changes.
Cloud infrastructure and cloud SaaS environments
Most organizations are now using some form of cloud infrastructure or cloud Software-as-a-Service (SaaS). Unfortunately, attackers are now combining attacks on traditional on-premises infrastructure with attacks and compromise of enterprise cloud infrastructure and cloud SaaS environments.
For example, at the beginning of 2023, ransomware group Lapsus$ attacked Impresa, a Portuguese media company. During the process, Lapsus$ gained control over the company’s Amazon Web Services account. Undoubtedly, future ransomware threats and cyberattacks will also attempt to expose and compromise cloud services.
Today, businesses leveraging cloud resources for business-critical processes and productivity must protect cloud infrastructure and cloud SaaS environments such as Google Workspace and Microsoft 365 from ransomware and other security issues.
The challenge for most organizations is the lack of tooling to secure and protect data in cloud SaaS environments adequately. In addition, many businesses may even assume there is no need to protect data and services housed in cloud SaaS environments since these are operated by hyperscale cloud providers like Amazon, Google, and Microsoft.
However, hyperscale cloud SaaS providers like Amazon, Google, and Microsoft operate on what they refer to as a shared responsibility model placing the final burden of protecting and securing their data on the customer. As detailed by Microsoft for their cloud SaaS offering, customers are responsible for the following:
- Information and data
- Devices (mobile and PCs)
- Accounts and identities
AI-assisted cloud security and protection with SpinOne
Organizations today must use next-generation technologies to even the playing field with cybercriminals using RaaS, IABs, compromised credentials, vulnerabilities, and many other attack vectors. SpinOne provides next-generation protection for cloud SaaS environments and uses artificial intelligence (AI) and machine learning (ML) to protect your cloud SaaS environment from cyber threats.
SpinOne provides immediate, real-time visibility into your cloud-based applications and cloud-native companies and solutions, such as Google Workspace, Microsoft Office 365, Salesforce, and other SaaS services. SaaS data disasters can be costly, and as businesses become increasingly reliant on cloud technologies, SaaS technologies must be protected and secured.
Using the protections provided by SpinOne, organizations can protect their critical cloud SaaS assets from many risks, including:
- Ransomware and cyberattacks – Ransomware can and does attack and affect cloud SaaS environments, in addition to on-premises. It is NOT an on-premises-only problem. Increasingly, ransomware groups are using the “double encryption” and “double extortion” scheme to not only encrypt your data on-premises but also to steal the data and extort companies with the threat of data leakage. It helps to underscore the potential damage of ransomware threats cannot be solved entirely by good backups. SpinOne not only backs up your data but also stops the ransomware attack quickly and decisively.
- API throttling limitations – Google and Microsoft limit the number of API calls customers can make to the backend APIs used to interact with cloud SaaS environments programmatically. However, these limitations can also lead to slow recovery times when large amounts of data are compromised, such as in a widespread ransomware attack. It helps to underscore the criticality of stopping an attack as quickly as possible. Only then can companies limit the “blast radius” of damaged data.
- Cloud Outages – Cloud outages do happen, leading to data loss for customers, at least in a few instances. Amazon, Google, and Microsoft have all had significant outages recently, leading to disrupted services and customers potentially being locked out from their data.
- Human error – Most data breaches are caused or related to human error. One study mentions human error is to blame for as many as 95% of all breaches. Whether the mistake is intentional or accidental, organizations must be prepared to recover and protect their data at all costs.
Google Workspace Backup Solution Comparison Table
View our competitive pricing chart
*Contact Us for current pricing.
SpinOne acts quickly when cyber attacks such as ransomware are detected:
- SpinOne ransomware protection monitors your cloud SaaS environment 24/7/365
- SpinOne blocks the ransomware network source if an attack is detected
- Resources are discovered that have been affected by the ransomware attack
- It automatically restores affected files to the latest backed up version
- IT admins are immediately notified of ransomware events in real-time
With SpinOne ransomware protection and cloud-to-cloud backups, downtime is significantly reduced for cyberattacks affecting your organization. It helps businesses meet the needs of cybersecurity posture management in cloud SaaS environments and protect critical cloud assets from attack. Learn how SpinOne can help your organization reduce the risk of cloud SaaS downtime here: How Avoid SaaS Downtime with SpinOne – spin.ai
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
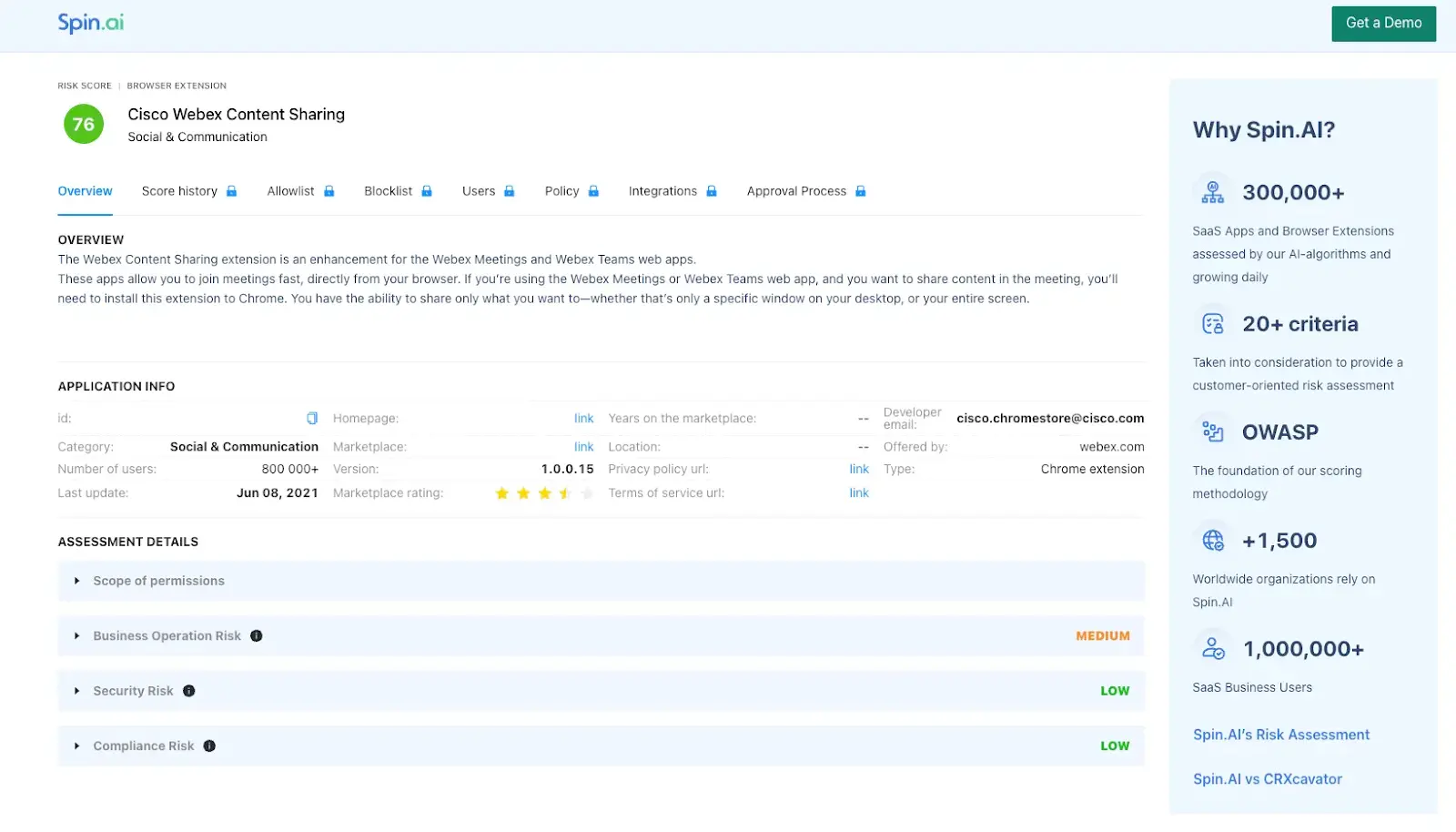
Best CRXCavator Alternative for Browser Extension Risk Assessment
Of the 300,000 browser extensions used in enterprise environments, more than half (51%) could execute...
The Ultimate Guide to SharePoint Cloud Backup: Securing Your Data
For businesses using Microsoft 365, SharePoint has become central to document management, team collaboration, and...
How to Ensure that Your Google Chrome Extensions are Safe
Google Chrome is the world’s most popular internet browser, enjoying a global market share of...