Data Loss Prevention Best Practices for the Cloud: Complete Guide
Losing sensitive corporate information can be devastating to a business. Learn how to reduce the risk of data loss in our latest guide: Data Loss Prevention Best Practices for the Cloud.
Understanding cloud data loss and its common causes
In 2023, about 60% of all corporate data is stored in the cloud. Similar to data stored on-prem, cloud data is subject to loss.
While cloud data centers guarantee data protection against physical damages, the responsibility for data security is largely placed on the data owners.
The main causes of data loss in the cloud are:
- Human error (e.g., accidental deletions)
- Absence of backup
- Ransomware attacks
- Zero-day attacks
- Account hijacks
- Unauthorized access
- Man-in-the-middle attacks
- Cloud misconfiguration
All these causes, including ransomware attacks, lie beyond the scope of responsibilities of cloud providers. Businesses using cloud services have to address these issues on their own.
Cloud Data Loss Prevention
Cloud data loss prevention is a system of practices and tools that prevent data loss in the cloud.
Cloud data loss prevention includes:
- Cloud security configurations (e.g., disabling outside sharing)
- DLP policies (e.g., creating a copy of a deleted file in a secure vault)
- Third-party tools (e.g., backup, SSPM)
In some cloud environments, the term DLP encompasses both data loss and data leak prevention. While the security practices and tools for both leak and loss prevention overlap, they are not the same. Data leak requires some extra practices (e.g., detection of PII transfer, mass down-load detection).
Benefits and significance of implementing DLP
Data loss prevention helps businesses avoid many risks, including:
- Downtime
- Legal fines due to non-compliance
- Lawsuits from the clients and/or employees
- Reputational losses
- Revenue losses
- A surge in client churn
- Termination of important project
- Incident response expenditures
- Loss of employees
- Business termination
Cloud data loss prevention best practices
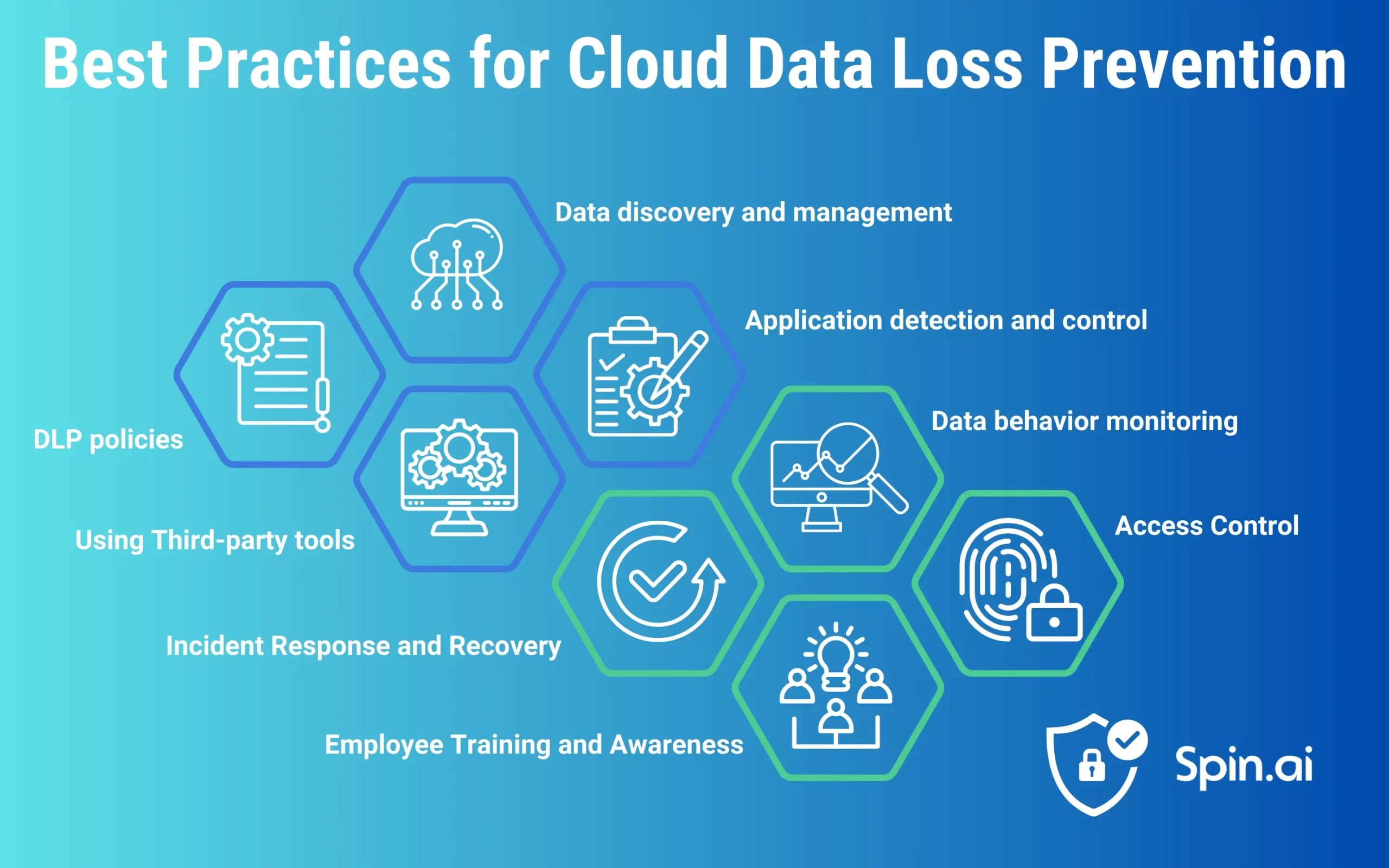
Data discovery and management
Data discovery and management enables your IT team to achieve data visibility within your cloud environment. Without this visibility, efficient control over data integrity is impossible.
This practice requires that you discover and catalog all the data in your cloud. Next, you need to categorize it in accordance with its sensitivity and value for the organization. This helps you create DLP policies and data retention rules. It also enables you to set the rules for the deletion of obsolete data.
Data discovery and categorization should be a regular practice for your team.
Data behavior monitoring
Your IT team needs to monitor data events such as mass editing or mass deletion. It will help you stop the incidents that include the loss of large data sets. Such events can happen due to human factors (errors or malicious actions), software malfunction (an error in an application), ransomware attack, or a zero-day attack.
Such monitoring is impossible to carry out without automation tools. That is unless you use dedicated human resources, which is highly unlikely to take into account the cost of such monitoring and the current cybersecurity talent shortage.
Data behavior patterns will also help you detect covert threats within the organization if you feed the information about data behavior to SIEM.
Access Control
Access control has two aspects. First, you need to secure the user access to your cloud environment by ensuring that:
- Users have secure passwords that they change on a regular basis.
- Multifactor authentication is enforced.
- Regular log-out on all devices is enforced.
- You monitor user behavior to detect abnormalities that might imply the account hijack.
Second, you need to limit access to sensitive data within a cloud environment. For example, there is no need to provide the finance department with access to all sales data and vice versa. The best principle that comes to mind is divide and conquer. Divide your data into clusters and enable access to it only for a limited number of your employees.
Application detection and control
Application control can be achieved only through full visibility and risk assessment of every app with OAuth access to your cloud environment. An app or extension could have an unknown (and exploitable) vulnerability – exposing you to the risk of a zero-day attack.
Control over applications will also enable you to detect similar apps that are used by different departments (or even within one department). You can reduce tech stack expenditures by removing apps with duplicating features from them.
Employee Training and Awareness
Employee training can help your team correct their behavior to avoid data loss incidents. This includes:
- Detecting potential threats like phishing emails with ransomware
- Sharing files in accordance with the company security policies
- Avoiding using unauthorized applications
- Creating complex passwords both for corporate and personal accounts
- Never using permanent deletion for files
DLP policies
DLP policies are often created when employees fail to follow data protection rules. These are algorithms that are triggered whenever an incident with data loss potential occurs. Many cloud environments have DLP policies. There are also third-party tools that enable companies to create additional, automated policies.
IE: When a person incorrectly shares a sensitive data fil, the policy might only notify the user (and, in some cases, the Admin and the user’s manager), disable the action, or even take ownership of the document from the user.
Incident Response and Recovery
Incident response and recovery are critical to minimize the impact of a data loss event and the event that caused it on the company. It includes the following activities:
- Retrieving data from backup,
- Revoking sharing permission, app access, etc.
- User suspension
- Taking over ownership
- Incident investigation.
It’s important not only to restore data but quickly identify the cause of the leak to prevent repeating similar incidents in the future.. For example, more than one-third of businesses that survived a ransomware attack become the victim of a new attack. This often happens because the business failed to detect all the entry points that hackers left when they infiltrated your environment for the first time.
Using third-party tools
It’s impossible for IT teams to carry out all the necessary data loss prevention practices alone – your business needs cloud-native data protection.
Meet the SpinOne platform – specifically designed to address multiple threats to data integrity in the cloud, on one automated platform. At its core is the incremental regular backup that copies your data on a separate unlimited cloud storage.
To protect against data loss, SpinOne has powerful behavior-based ransomware protection and response. It detects and stops ransomware within minutes after the attack and recovers all data automatically.
SpinOne also offers App Risk Assessment. This functionality detects all the OAuth apps and extensions that have access to your cloud environment and gives your Admins the power to block them.
Additionally, the SpinOne platform monitors and detects abnormalities in data and user behavior, helping IT security teams detect and respond to data incidents immediately.
SpinOne is designed to help your security teams automate critical data loss prevention practices and decrease the response time and the number of incidents.
Learn more about protecting your sensitive SaaS data here.
FAQs
What are the key components of an effective DLP policy framework?
The main elements of an effective DLP policy framework are discovery, classification, and monitoring.
How can access controls and user permissions help in preventing data loss?
Access control can prevent unauthorized users from accessing data and carrying out an attack (for example, deleting it or overwriting it with false information).
How do employee training and awareness contribute to DLP best practices?
Trained employees are less likely to take actions that can cause data loss (e.g., fall for a social engineering attack or have their accounts hijacked).
How often should DLP policies be reviewed and updated?
DLP policies should be reviewed and updated at least once every year. However, it’s best to make it at least twice a year.
Can DLP solutions be integrated with existing security infrastructure?
It depends on the solution.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Top 12 Slack Security Best Practices In 2024
Slack might feel like the digital version of your office break room with quick chats,...
Backup Microsoft: Securing Critical Business Data Across Microsoft ...
We all know Microsoft is a behemoth with all types of critical products used by...
Unpacking the Browser Extension Threat Model
Mastering the Balance Between User Empowerment and Organizational Security Web browsers are not just passive...