Google Backup and Sync: Service Discontinued, What’s Next?
Google Backup and Sync app was a popular application. Unfortunately, in October 2021, it stopped functioning, leaving users to wonder what’s next. Today we talk about Google Backup and Sync and which tools can replace it. This text is specifically aimed at small and medium businesses and their unique needs.
Looking for a replacement for the service? Try Google Workspace Backup.
What Is Backup and Sync from Google?
Google Backup and Sync was an application that allowed users to create unique folders on their computer that automatically sync files with Google Drive for a potential Google Drive Backup solution. Some people and even businesses used it also to back up their data. The application merged last year with another files sync app: Google Drive File Stream. It was later renamed to Drive for Desktop or some called it the Google Drive App.
What were the benefits of Google Backup and Sync?
Google Backup and sync had multiple benefits:
Some people preferred working on a stationary computer or laptop rather than in cloud solutions. The Google Drive sync functionality provided a better experience.
Internet independence
It enabled employees to be less dependent on the Internet and avoid file downloads when they get access to the web. The files sync was carried out automatically.
Data protection
It provided a limited backup functionality for files and folders. We explain in the next chapters why this tool wasn’t reliable enough as a backup.
Collaboration
Many users praised the tool for collaboration capacities. Similar to working with Google Drive files or the google cloud option, users could cooperate on files stored on their computer.
In the next few sections, we cover the drawbacks of this application for a shared drive. We also suggest tools that can replace it and perform the respective functions better.
Why was the Google Backup and Sync App terminated?
There are several reasons why Google decided to get rid of this application. And while they never explicitly explain themselves, we deem several suggestions plausible.
1. Google had another application with similar functionality.
It was called Google Drive File Stream. Unlike Google Backup and Sync, it was available only for the holders of business accounts. Another notable difference between the two was the backup storage location.
Backup and Sync stored files on a computer, while Google Drive File Stream created the folder in the cloud and sent all the files there for cloud storage.
The app was later renamed Drive for Desktop and merged with Google Backup and Sync app.
We consider that the company was willing to reduce user bafflement over many similar applications. Instead, it tailored a single offer.
It might have been a part of a bigger process of transformation from GSuite to Google Workspace. During this period, the company analyzed its applications and services as well as branding. This resulted in multiple remakes of apps, their functionality, and even names.
2. The confusion around the name.
The name of Google Backup and Sync App was somewhat misleading. Think about it. When businesses hear ‘backup,’ they think about protected storage where they can safely keep up-to-date copies of their files and folders.
Check out the review of this application. The drawbacks include the request to make backup versions:
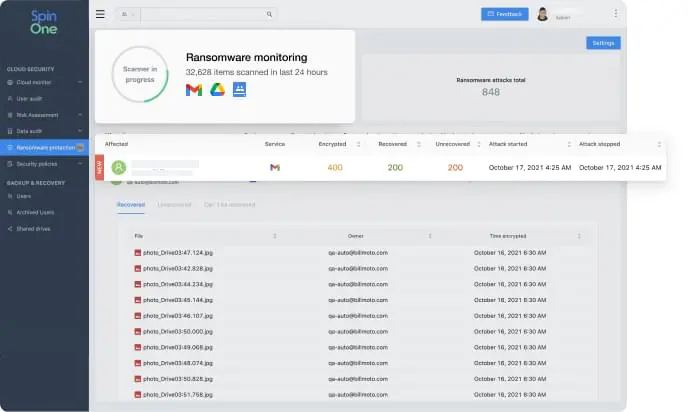
A folder on a computer that synchronizes files with the cloud is subject to multiple cyber threats. It cannot be considered a backup.
To make sure their Google Drive data is safe, companies should use Google backup tools like SpinBackup. We’ll talk about it below.
3. It had several drawbacks
Despite overall good reviews, users admitted that they weren’t completely satisfied with several things:
- speed of performance
- quality of performance
- UI/UX
- poor resolution of files sync conflicts
Are there alternatives for Google Backup and Sync?
Sure! However, the choice of a specific tool depends on the goals the users pursued when they used Google Backup and Sync backup software. That’s what we’re going to discuss in this section. And below, you’ll find a detailed guide on how to install two alternatives for the backup and sync. Keep reading!
Judging by functionality and user feedback, we can safely say that Google Backup and Sync was used for two different purposes:
- Sync app
- Data Backup
Sync functionality of Google Backup and Sync app
Most of the positive reviews that users left were focused on how well the application performed its files sync feature. Many were devastated to learn that Google had decided to discontinue the app.
Instead, the provider offered Google Drive for Desktop. We’ll talk about this solution later on in the post.
Backup functionality of Google Backup and Sync app
Was Google Backup and Sync Really Backup? The answer is no.
Interestingly, the backup and sync functionalities conflict with each other. And some users understood it pretty well. Here’s an example of feedback from a platinum product expert:
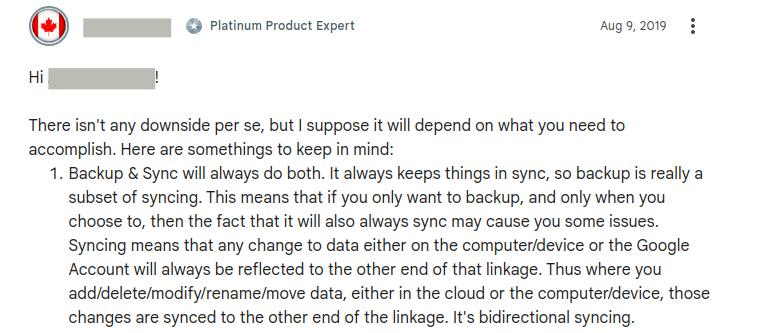
His summary is pretty accurate. Google Backup and Sync didn’t store several copies of the same document from different points in time (as backup tools usually do). Instead, it created a final and only version of a document eliminating other versions in the files sync process.
Imagine somebody opened a file with critical information and deleted its contents by mistake or malicious intent. The sync functionality did the same in a synchronized folder. And that’s the loss of your data unless you have a backup.
Another reason Google Backup and Sync wasn’t very good as a backup option is the limits of storage Google provided to its users. If you have ever reached those limits, you should know that you won’t be able to receive emails on your Gmail account until you free some space.
Finally, Google Drive data and files are vulnerable to cloud ransomware. If it hits your account and starts decrypting your files, the files sync functionality will copy all the changes from Google Drive to your Sync Folders.
We strongly advise companies against using sync tools for data backup. Use cloud-to-cloud backups instead. Solutions like SpinBackup are specially tailored to meet business needs in cloud environments.
They will keep multiple versions of your full backup files in a remote data center totally secure from any ransomware impact.
Google Drive for Desktop
Previously known as Google Drive File Stream, this app is the only sync offering for computer files that Google has for its users. It works with two systems: Windows and macOS.
Functionality
Similar to Drive File Stream and Backup and Sync solutions, the application will create one or several sync folders on your computer. It will then connect these folders with your Google Workspace. In addition to a regular Google Drive Folder, the app will automatically capture pictures and send them to Google photos.
Google Drive for Desktop has two configurations for synchronization:
- Mirror copies your files and folders from the cloud to your computer.
- Stream enables you to access your Google Drive files only via the Internet.
Both configs have serious disadvantages. The Mirror will devour your computer storage space. The Stream is unavailable without the Internet.
Advantages of Google Drive for Desktop
The advantages are similar to those of Google Backup and Sync. In addition to that, we’d like to point out several more advantages:
1. Settings customization. If you choose stream functionality, you are still able to set the ‘Mirror’ configuration on certain files and folders, provided you need them at all times.
2. Work from multiple accounts.
Let’s say your employee has a personal Google account. And your company uses Google Workspace. This employee can install Google Drive for Desktop on their computer and have two sync folders (one for work, the other for personal use).
Disadvantages of Google Drive for Desktop
1. Similarly to Backup and Sync and File Stream apps, it doesn’t work with Linux. It is especially critical for small companies that cannot pay for Windows or Apple.
2. Starting January 2023, the application will stop working with Windows 7 and macOS below 10.15.7.
How to Get Started With Google Drive for Desktop?
Google Drive for Desktop is as easy to use as its predecessor, Backup and Sync. But it’s not that easy to find.
Step 1: Download Google Drive for Desktop and install it
You’ll need to go to a special section of the Google Workspace Support website. There you will find two download links:
Step 2. Install the application
Open the downloaded file on your computer and proceed with installation instructions.
The application will create one or several folders on your computer if you have several accounts.
Step 3: Access your Google Drive files or copy files from your computer into the folder.
Can you use Google Drive for Desktop as Backup and Sync?
The answer is ‘Yes and no.’ The app performs perfectly as files sync for your computer and Google Drive. However, it is still not good as a backup solution for similar reasons we laid down in one of the previous sections.
If you need to back up your Google Drive, a private or working computer is not the best solution. We highly recommend using cloud-to-cloud backups to guarantee your data security.
SpinBackup Cloud-to-Cloud Backup for Google Workspace
SpinBackup is a cloud-to-cloud backup for Google Workspace that’s a great alternative backup and sync service . Here are several advantages of this tool:
1. It can help with the following:
- Backup Google Drive including Shared Drives and Google Team Drives
- Backup file types like Google Docs, Google Sheets and other files
- Save Emails in Gmail (Contacts and Google Calendar, too)
2. It copies data on a daily basis and automatically. Additionally, your Admins will be able to perform backup upon demand manually.
3. SpinBackup stores multiple versions of a single file. You will never have problems with correct data restoration, even if the information was deleted a long time ago.
4. You can choose sync Google Drive to different locations for your data storage from the best data centers: AWS, GCP, Azure. This is a preferred method to storing to an external hard drive.
Learn more about SpinBackup capabilities.









