Holiday Extension Risks: Navigating the Web Safely During the Festive Season
As the holiday season unfolds, there is a surge in digital engagement. This time of year is marked by a flurry of online shopping, travel planning, and communicating with family and friends. While apps and browser extensions add a layer of convenience to these activities, they also pose a risk, potentially endangering the security of both personal and work accounts.
To ensure a joyous and secure holiday, it’s important to understand the potential dangers associated with browser extensions so you can safeguard your SaaS data during these festive times.
The Browser Extension Landscape
Marketplaces such as Google Marketplace and Microsoft Edge Add-ons feature an extensive array of browser extensions, numbering hundreds of thousands. Additionally, there are numerous extensions available beyond these official channels. However, it’s important to note that not all of these extensions maintain adequate security standards. In the previous quarter, we identified 2,297 extensions that were installed externally, bypassing the official Google Marketplace. This highlights the need for vigilance when selecting and installing extensions.
Extensions can pose significant risks to browsers and SaaS data, especially in corporate environments, where in one case, a company with over 2,000 employees had 1,642 different extensions installed.
Risky Categories
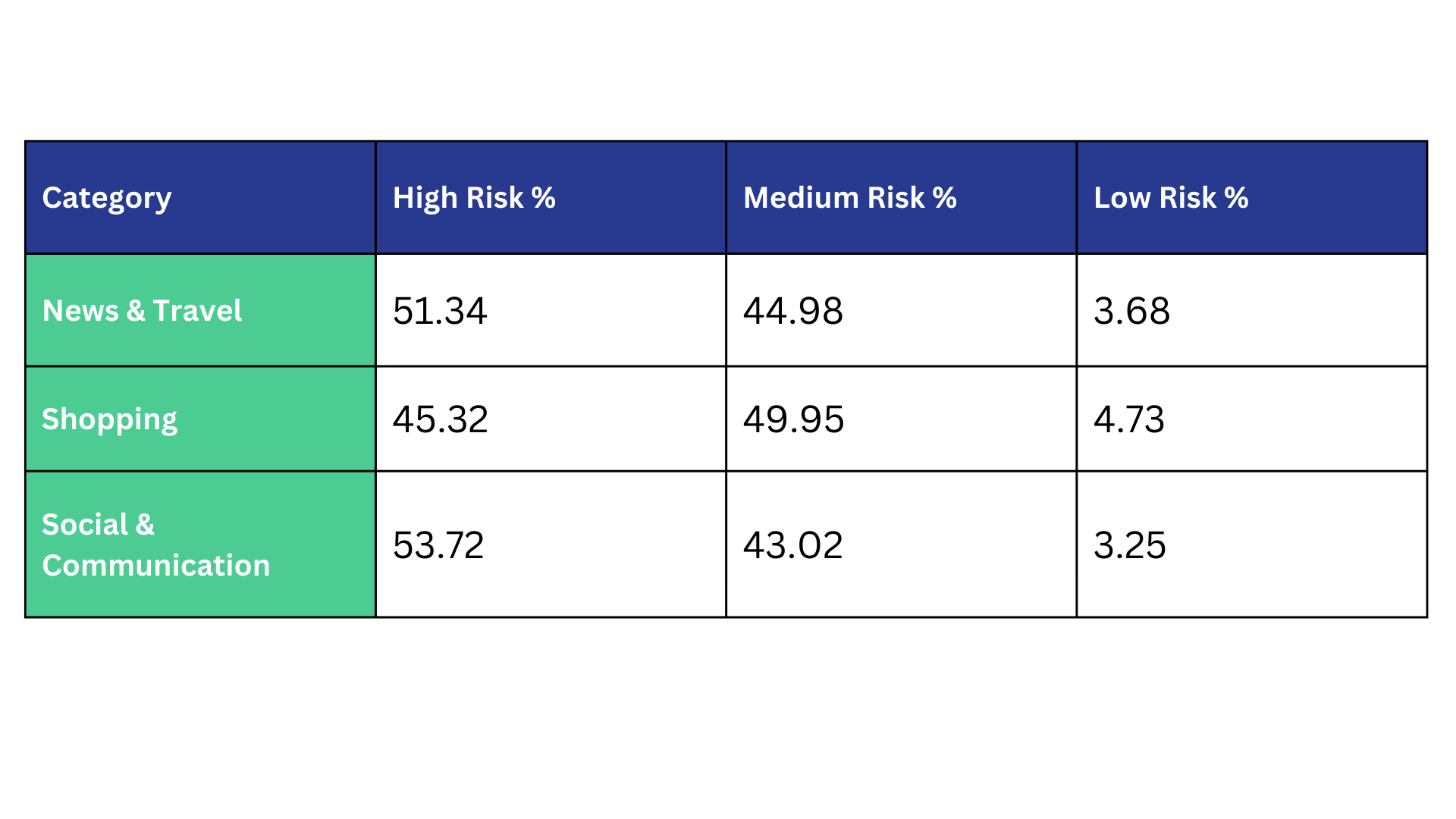
Evaluating Extension Risks
What qualifies an extension as risky, and are all types of risks created equal? At Spin.AI, we assess extension risks across operational, security, privacy, and compliance dimensions, categorizing them into High, Medium, or Low Risk. For example, a risky extension or application may have one or more of the following characteristics:
- It requests high levels or excess permissions (even if it doesn’t need them)
- It has code vulnerabilities or security bugs
- It isn’t regularly updated
- The developer may not disclose whether the extension has undergone a third-party security or compliance audit
- It may have recently been subject to a data breach
- It sends requests (especially user information) to a lot of suspicious websites
These are a few examples, but there are many others. One startling finding from our research is the existence of 43,221 extensions with unknown authors, highlighting the need for rigorous evaluation. And, unlike OAuth apps, browser extensions can access all data in the browser like website content, local or session storage cookies, browsing history, profile information and more, making their risk assessment more critical.
For reference, here are the top five riskiest extensions we identified in each of the categories listed earlier. While some of these should be obvious to even the most inexperienced cybersecurity practitioners, others may not be as obvious.

Protect Yourself
Safeguarding your digital space this holiday season starts with awareness and cautious navigation. Do not use corporate resources (computers, browsers, accounts) to organize entertainment or personal travel. Choose well-known, verified extensions, remove unnecessary or erroneous extensions, and keep your security settings updated to avoid potential risks.
For broader protection, especially for businesses, implement strategies from the Spin.AI Browser Extension Risk Report: maintain a real-time inventory of extensions and SaaS applications, conduct ongoing risk assessments, establish and enforce risk management policies, and utilize automated controls.
Spin.AI is dedicated to empowering users with knowledge and tools to safeguard their digital presence, particularly during high-risk periods like the holidays. Discover more about SaaS security and how to protect your digital environment by visiting https://spin.ai/application-risk-assessment/.
Stay safe and secure this season with Spin.AI.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...

