How to Prevent Phishing in Google Workspace and Microsoft Office 365
Today we will teach you how to prevent phishing in Google Workspace and Microsoft Office 365. Security threats are among the most alarming concerns for IT professionals and C-level executives alike. In one major security breach, a company can literally be taken out of business.
There are many different types of security vulnerabilities and concerns that organizations today need to be aware of. However, some of the most successful types of compromising techniques used by threat actors are often the most basic and traditional long-known methods.
One of these is phishing. Phishing is a technique used by threat actors to lure end-users into disclosing valuable or sensitive information under false pretenses. There are various types of phishing attacks that are used today that organizations need to be aware of. Is phishing still a concern when organizations are making use of public cloud resources such as Google Workspace (G Suite) or Microsoft Office 365?
In this post, we will take a look at the various types of phishing attacks and how they have evolved. We will also discuss how to prevent phishing attacks in an organization, with particular attention to Google Workspace and Office 365.
Types of Phishing Attacks Used Today
Before exploring the topic of phishing attacks and how they relate to the public cloud, let’s first take a look at traditional phishing attacks in general terms. This includes differentiating between the various types of phishing attacks that are commonly used. When it comes to phishing, there are different types of techniques attackers use to steal information. These include the following:
- Bulk Phishing
- Spear Phishing
- Whaling
- CEO Fraud
- URL Phishing and Misspelled Domains
- Filter Evasion
While not an extensive list of phishing types, these are some of the most commonly used. Additionally, new and advanced techniques are introduced into the wild on a regular basis. Let’s take a look in a bit more detail at the above type of attacks and why they are dangerous for organizations.
Bulk Phishing
Bulk phishing is an age-old technique employed by threat actors, involving the mass distribution of phishing emails to potentially millions of recipients. Although these emails may lack specificity, their success lies in the sheer volume of messages sent. Bulk phishing emails may entice users to click links with the purpose of harvesting personal information or system information under the guise of a legitimate purpose. However, the unsuspecting end-user is unwittingly handing over login or other sensitive information to an attacker.
Spear Phishing
With Spear Phishing the message that is seen by the end-user is much more personalized. This helps with the façade of legitimacy. The attacker may have already harvested or obtained personal information about the end-user which is then used in the spear-phishing attack. It is possible that threat actors possess the personal information of the end user, including their name, phone number, address, or other details. This data allows them to make additional information requests that seem legitimate or at least create the impression of having a genuine connection with the requestor.
Whaling
Whaling is a specific type of phishing attack that is differentiated from the other types of phishing attempts by the target of the phishing attack. Projected targets of whaling include high-ranking or senior executives such as C-level employees. Information requests contained in the whaling attack are more tailored to an executive. Information presented may include subpoena requests, customer complaints, wire transfer requests, or other financial transaction-related requests.
An unsuspecting senior executive may be lured into disclosing sensitive system information or other data that is valuable due to the position within the company the individual holds. Often, C-level and other executives have system access that lower-level employees do not have. If attackers can phish system-related or other information tied to high-level executives, the level of compromise can often be much greater.
CEO Fraud
Another type of highly effective phishing attack on the rise involves impersonating a CEO or other high-ranking executive. However, its intent and purpose are slightly different. Unlike whaling, the attacker, instead of targeting the C-Level or high-ranking executive, impersonates the identity of a CEO or other C-Level executive. They use this impersonation to communicate with a lower-level end user. This is to persuade the unsuspecting end-user to execute unauthorized wire transfers, financial transactions, or make other purchases.
This type of phishing attack plays on basic human nature to please those in positions of authority quickly and without question. Unsuspecting end users may quickly want to carry out any request made by someone of this level in the organization. This can lead to bypassing the usual scrutiny applied to similar requests from lower-level employees.
CEO fraud is a growing type of phishing attack that is extremely effective. Attackers generally carry out this type of attack by way of an email. They may scrape the relevant information for C-Level employees from various social media channels to make the request seem as legitimate as possible. Thus, the attacker can combine the various techniques found in spear-phishing and social engineering in this highly effective form of a specialized phishing attack.
URL Phishing and Misspelled Domains
URL phishing is very common method attackers utilize to steal personal information or other valuable system information from unsuspecting end users. URL phishing typically makes use of misspelled domain names that are very close to the real, legitimate domain. Attackers may even make the misspelled domain look very similar to the legitimate site, giving further success to this form of phishing.
Many have inadvertently landed on a URL phishing site by accidentally misspelling a character or two when typing in the URL. An unsuspecting end-user may simply attempt to login and click through a URL that has been set up by an attacker that impersonates a familiar website. In this way, individuals can easily become victims. They might end up entering information and inadvertently handing over sensitive items to attackers. These could include accounts, passwords, email addresses, and contact information.
Filter Evasion
“Anti-Phishing” mechanisms are becoming smarter and can identify keywords in phishing emails. In response, attackers have become more cunning, using filter evasion techniques to bypass these filters. These include using images that contain embedded phishing text which helps to avoid simple string parsing by anti-phishing filters. This and other filter evasion techniques can prove to be very effective in especially avoiding traditional anti-phishing techniques.
These examples are only a small subset of the overall phishing tools and techniques utilized by today’s attackers. While phishing is fairly archaic compared to other means of system compromise, it is still surprisingly effective in manipulating unsuspecting end users. The above list of phishing techniques is a basic example that has proven to be very effective in compromising end users.
How do phishing attacks look in the public cloud? Are they different? What do organizations need to know about phishing dangers in public cloud Software-as-a-Service environments such as Google Workspace (G Suite) or Microsoft Office 365? What techniques are attackers using there? How can organizations protect themselves?
How to Prevent Phishing Attacks in Google Workspace and Office 365
As organizations move more business-critical resources out into public cloud environments such as Google Workspace (G Suite) and Microsoft Office 365, attackers are taking notice. In fact, more and more phishing and other attacks have been geared toward public cloud environments. Attackers are aware that Google, Microsoft, and other entities employ advanced methods to mitigate these types of attacks. Consequently, attackers persistently adapt their techniques in an effort to counter these defenses.
With modern types of phishing, attackers are not after the typical target of the traditional phishing days such as financial transfers. Now, the target is system credentials and administrator credentials if possible. These are far more valuable as they can lead to even greater types of compromise and the stealing of data.
As posted by Forbes, in 2017, a very sophisticated phishing attack was carried out on Gmail users. End users received an email that appeared legitimate, leading them to a Google web page. On this page, they were prompted to grant permissions to a seemingly harmless third-party application, which, unbeknownst to them, was actually malicious. After the permissions were granted, the attackers were able to read the contacts, emails, location, and even access files of the compromised users.
Pubic cloud authentication mechanisms for third-party integrations are designed to be user-friendly, easy, and painless to grant access to resources by end-users. However, when end users casually grant permissions to third-party applications without thoroughly examining the requested access, the consequences for organizations hosting resources in public cloud Software-as-a-Service solutions like Google Workspace and Office 365 can be severe. This careless behavior can result in significant security implications that need to be considered.
Most of the time, end-users will typically blindly grant permissions without questioning them appropriately. After all, most of us are guilty of this and do well to ask, when was the last time we read through the permissions requested by a cloud application requesting access to resources? It is a bit sobering to think about the implications that malicious third-party applications pose to organizations in regards to data leaks and sensitive data breaches.
Phishing attacks targeting Office 365 have become increasingly sophisticated. Similar to the Google Workspace, advanced techniques are being employed by attackers. This is done in an attempt to circumvent phishing protection and other anti-malware safeguards that organizations have implemented. Redmond Magazine reported on a sophisticated phishing attack. In this attack, the perpetrators exploited internal systems of Office 365. Their aim was to infect Office 365 end users with malware. How is this type of attack carried out?
The term coined for this type of attack is “PhishPoint” as the attacker makes use of Microsoft’s own Office 365 SharePoint to carry out the attack. As most realize, Microsoft allows free Office 365 trials to be provisioned for POC and other initiatives with Office 365. Attackers carrying out PhishPoint provision a trial version of Office 365 for which they only need to have an email address.
After standing up the trial version of Office 365, the attacker inserts a malicious link into a SharePoint file instead of an email. The attacker then sends an invitation to “collaborate” on the SharePoint file to an unsuspecting end user.
After clicking the link, the browser opens an impersonated copy of a standard access request to a SharePoint file. This request contains a hyperlink to a OneDrive file. However, this hyperlink actually leads to a malicious URL. The malicious URL is yet another impersonation of an Office 365 login screen that has the sole purpose of harvesting credentials. The link will behave as if the login credentials fail, however, it is simply harvesting the user account and password from the user input.
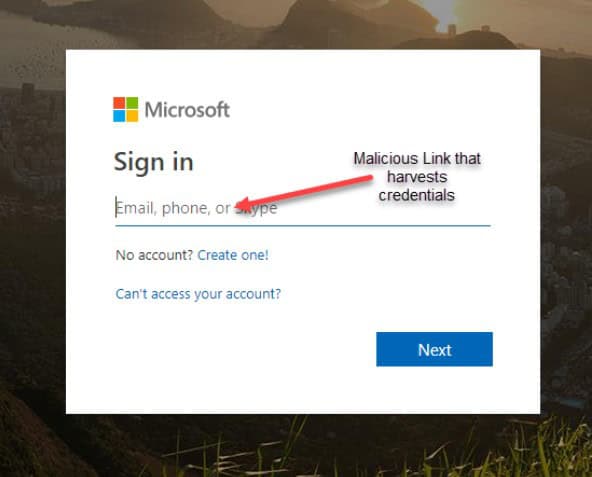
PhishPoint impersonated Office 365 screens and exploited weaknesses in the built-in Office 365 Phishing protection
Attackers are constantly searching for weaknesses in the defenses of public cloud Software-as-a-Service systems. PhishPoint serves as a stark example. It shows just how quickly and effectively these vulnerabilities can be exploited.
A point for emphasis for organizations utilizing SaaS resources is that Microsoft and other public cloud environments are not immune to skilled attack techniques and weaknesses in defense mechanisms. Often vendors and providers may be looking at traditional threat vectors and utilizing more traditional means of protecting tenants from phishing attacks. This includes traditional scanning of links in email bodies to look for blacklisted or suspicious domains.
As demonstrated by the PhishPoint attack, Microsoft is focusing its attention on email threat vectors for phishing and other malware payloads, and SharePoint links and other “Microsoft” resources are not being scrutinized and scanned properly. Since Microsoft’s link scanning method is only going to a certain level and not scrutinizing and scanning the actual files the links are calling, this presents a clear vulnerability that attackers can exploit for compromising credentials.
Public Cloud Phishing Lessons Learned
There are certainly some hard-hitting lessons that organizations need to be aware of when utilizing public cloud Software-as-a-Service environments such as Google Workspace (G Suite) and Microsoft Office 365. First of all, the idea that the public cloud has impenetrable defenses when it comes to phishing and other malware threats is not true. Organizations need to pay due diligence to the threats posed by modern phishing attacks that utilize sophisticated methods outside of the more traditional means of phishing on-premises environments.
Public cloud environments such as Google Workspace utilize OAuth authentication that provides a seamless experience with granting permissions to third-party applications. It allows granting permissions to third-party applications without having to reenter their user credentials.
The tradeoff for this type of convenience is security. End users will all too often blindly grant requested permissions to third-party applications without truly scrutinizing those permissions or questioning the level of permissions being requested. As the Google Workspace (G Suite) phishing exploit demonstrated, this can easily be used by attackers for malicious purposes in harvesting system credentials, gaining access to files, contacts, etc.
The PhishPoint phishing attack on Microsoft’s Office 365 environment demonstrates how public cloud providers have a long way to go when it comes to implementing truly effective phishing and malware defenses. By simply changing the method of delivering a malicious URL via a SharePoint collaboration request, attackers were able to harvest user credentials without being properly stopped by Microsoft’s anti-phishing mechanisms.
A hard lesson learned from only these two examples shows that organizations cannot simply rely on the default native security and protection from phishing and other attacks provided by Google Workspace or Office 365. They need to bolster security with a solution that allows effective filtering and protection of their user environment and data, going beyond just the default Gmail phishing protection measures.
Intelligent Phishing Detection, Security, and Data Leak Protection
Relying on the native security mechanisms of today’s public cloud environments is simply not enough. Organizations must take the extra step to bolster the security of their user environment and proactively protect their data. How can this be done easily and in a cost-effective manner?
Spinbackup provides the ultimate solution for organizations running business-critical applications in either Google Workspace (G Suite) or Microsoft Office 365 environments. Specifically related to phishing and malware protection, Spinbackup provides the following to organizations housing resources in Google Workspace and Office 365 public cloud SaaS environments:
- Proactive Monitoring of user behavior.
- Proactive Monitoring of data shared both inside and outside public cloud environment.
- Third-party Apps Control – Spinbackup can block risky third-party applications such as was used in the Google Workspace phishing attack in 2017 allowing organizations to have much better control over who and what applications access data.
- Ransomware Protection – Spinbackup can proactively monitor ransomware operations and automatically remediate infected files.
- Insider Threat Protection – Monitor risks from within the public cloud.
- Powerful machine learning and AI baselines and constantly monitor behavior, activity, data, backups, etc.
- Enterprise-level Backups – Automatic, versioned backups for Google Workspace and Office 365 services.
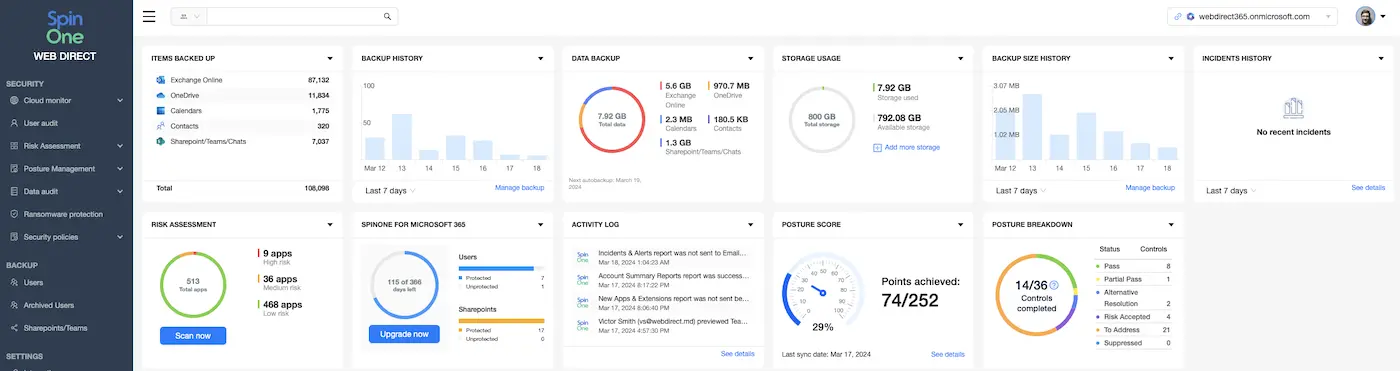
Spinbackup provides an extremely powerful, bolt-on solution that allows organizations to easily provide the backup and security mechanisms needed in Google Workspace and Office 365 (security coming soon). It provides a single pane of glass view of the critical activities and security-related events that allows having the tools needed for monitoring, securing, and maintaining the integrity of organization data.
Counteract phishing effectively with Spinbackup. Download a free trial of Spinbackup for either Google Workspace (G Suite) or Microsoft Office 365 today.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...


