What is CEO fraud and How to Protect against It?
What is CEO fraud? How are incidents of CEO fraud perpetrated against unsuspecting individuals? What can businesses do to protect themselves from this type of fraud of high-level executives? Let’s take a look at these topics and see how organizations can more effectively protect themselves against the CEO fraud attack.
Today’s businesses are more technology-centric than ever before. Most companies utilize technology-driven processes and services for day-to-day operations and business-critical systems. Especially when it comes to business communication, everyone is using technology to communicate. Email has been the preferred means of communication in the business environment for decades. It continues to be heavily utilized for communication both within and outside of the organization.
However, organizations are leveraging the power of social media and other means of communication to provide highly effective real-time communication between employees. With the prevalence of these and other types of communication, there has been an alarming increase in a particular type of fraud, known as CEO fraud among businesses today.
What is CEO fraud?
With the ever-growing numbers of CEO fraud, let’s take a look at what CEO fraud is exactly. Another name for CEO fraud is Business Email Compromise (BEC) fraud.
CEO fraud/BEC fraud is carried out when attackers impersonate the identity of a CEO or another high-level executive in order to coerce unsuspecting employees into sending money on behalf of the executive outside the company. Typically, the target of the CEO fraud may be someone who works in the Finance department or another department that has direct access to budgetary funds and the ability to perform banking transactions on behalf of the organization.
The CEO fraud attack is a special form of social engineering that plays upon employees’ general respect and regard for C-level executives. Most employees are eager to promptly fulfill any request they receive from their purported C-level executive. They tend to avoid questioning or obstructing such requests, as they perceive them as potential obstacles to progress or direct instructions from the CEO or other C-level executives.
With this in mind, employees thought process generally fast-forwards past scrutinizing the request itself and its legitimacy and straight to performing the task at hand. This can result in costly transactions assumed to be made on behalf of the CEO that are simply being transferred into the hands of the attacker via an electronic bank wire transfer.
How are CEO Fraud Attacks Carried Out?
As previously mentioned, the CEO fraud attack targets individuals who possess the capability to electronically transfer funds and engage with banking institutions. Alternatively, it could be an employee that has access to sensitive or otherwise valuable information instead of monetary funds. Typically, these types of individuals may work in finance or HR, but can certainly be any employee with certain types of high-level access.
It should also be noted that victims of the CEO fraud type attack are not limited to employees who work at relatively large corporations. Attacks can see success by targeting businesses in the SMB market as well as even smaller organizations, resulting in successful payouts.
Smaller organizations are particularly vulnerable to this type of attack due to the relatively fewer checks and balances in place for large transactions compared to larger corporations. Additionally, employees may be more accustomed to working directly with a C-level executive on certain business transactions or other types of requests. These types of requests may appear more unusual in larger corporations than is the case with small to mid-sized businesses.
The social engineering involved allows the attacker to play on the emotions and willingness to quickly please individuals who are in a C-level position by lower-level employees. Just the fact the supposed communication is coming from a C-level executive can catch the employee off guard. One may not think to question or feel in a position to question the request from the supposed C-level executive.
Is this type of social engineering and attack carried out randomly without prior planning, etc? No, typically, these types of activities are carefully planned. Attackers may troll the social media channels of various organizations to learn the identities of high-ranking officials in an organization. Additionally, they may gather information about the business structure of the organization through these channels. LinkedIn accounts of executives can also prove fruitful in gathering information about executives.
Even some websites of businesses can potentially reveal the organizational structure and which departments report to certain C-level or other executives. By performing this type of reconnaissance work, attackers can gain familiarity with the organization which allows them to more successfully perpetrate a fraud by carrying out a request for funds transfer or some other scheme in a way that is in line with potentially normal channels of communication and can make the fraudulent request appear believable.
Another potentially dangerous mechanism from a security standpoint is email autoresponders. If a C-level executive turns on an autoresponder in email, attackers can gain visibility into whether or not that individual is in or out of the office which can play into making a successful CEO fraud attack. Attackers may send a frantic request for funds transfer by an “out of the office and otherwise disposed of CEO” which may convince a gullible employee and make it seem all the more reasonable.
Otherwise, if this type of request is made while these individuals are in the office, it can more easily be seen as a fraudulent attempt. Also, if the impersonated official is in the office, it makes for easy access to verify with these individuals, even in person, as to whether or not the request is legitimate.
Having a CEO or other executive out of the office can also play into the mindset of the lower-level employee not wanting to disturb or question a C-level executive that is perhaps on vacation or a business trip. Most employees might rationalize, “well, this request is most likely legitimate, so I won’t question it”.
All the attacker must accomplish is the “appearance” of legitimacy. If they can accomplish this, most often they will come off successful in coaxing a fraudulent wire transfer or some other fraudulent bank transaction.
What are some other tools that attackers utilize for carrying out the CEO fraud attack? There are several other tricks up the sleeves of attackers when it comes to CEO fraud. Malware can certainly be used to compromise environments and allow attackers to scrape information from client devices. This can include information related to the internal business structure or scraping information that allows further compromising of identity.
Phishing is still a powerful tool in the attacker’s arsenal as well. Attackers can phish for information from CEOs or other employees that discloses identities of individuals in the organization’s structure – who employees report to, names of team members, phone numbers, email addresses, etc. Obtaining these types of information, again, is key to being able to pull off a successful attack executing a fraudulent transmission with the appearance of legitimacy.
Obtaining monetary funds may not always be the objective of attackers when carrying out CEO fraud. By masquerading as a CEO, an attacker can also request “information” as the targeted prize in a fraudulent request.
When you think about today’s businesses, data is one of the most valuable assets possessed by any business. Information can be used or sold on the black market for a much higher value than a simple request for wired funds. Additionally, information can be used to extort funds in certain cases as well.
Whether it is monetary funds or information/data, the CEO fraud attack is dangerous as it can often play upon the weakest link in security – the human employee. No amount of security can completely prevent an employee from making a detrimental decision. Such decisions have the potential to cost an organization a significant amount of money or, worse yet, compromise highly sensitive data.
How Can Organizations Protect Themselves Against CEO fraud?
Organizations looking to protect themselves against CEO fraud do well to consider a multi-faceted approach to securing their data and internal processes as well as cyber risk management. This approach should include a good deal of technical security mechanisms as well as cyber security employee training that can help employees be on guard against CEO fraud and recognize the signs of this type of fraud before making bad decisions. The latter aspect of protecting against CEO fraud can arguably be the most powerful means to securing the workplace from this type of fraud.
What are some of the technology tools that organizations need to consider when thinking about protecting against CEO fraud? Well, most of the technical considerations that organizations need to make when protecting against CEO fraud are found in a good overall security strategy, to begin with. Such things as SPAM filtering for email, endpoint virus/malware protection, and next-generation firewalls all play a part in helping organizations filter out potentially malicious or fraudulent traffic looking to steal or phish information from employees.
All of these technology mechanisms have a place in helping to filter out as much illegitimate and potentially malicious traffic as possible. Most organizations today have publicly accessible websites that hold the potential for disclosing too much information. Organizations should be very judicious in how they post organizational information and just how much of this is disclosed to the public. This can help speed along with the reconnaissance work that a potential attacker may need to do to pull off an effective CEO fraud attack.
Cybersecurity Awareness for Employees
What about the human aspect of protecting organizations against CEO fraud? This is as mentioned, arguably, the most effective means of protecting your organization. After all, the target for an attacker is “human employees” who have to decide on whether or not a particular request is legitimate or not. What can organizations do to help with this?
Enhancing cybersecurity awareness and training employees to recognize the signs of illegitimate CEO fraud attacks is critical. There are many solutions out there that actually provide services for hire that can provide self-paced learning modules to train employees on various social engineering type scenarios and help them to become aware of the potential attack vectors. However, a few “common sense” checks can often avoid playing into fraudulent transfers of money or information. These include:
- Identifying the originating email address.
- Scrutinizing the request itself.
- Confirming the request with supervisors.
- Putting processes in place to verify transaction approval.
- Scoping down who has access to transfer funds.
There are several key points that employees need to be trained in considering before responding to or entertaining a communication that can potentially be a CEO fraud attack. Many employees may not be “technically inclined” and these types of employees can potentially fall prey to these attacks more easily. Regardless of technical prowess, employees from any technical skill level can be trained to recognize the signs of fraudulent communication.
Since email is one of the primary means of communication in considering these attacks, let’s look at how employees can recognize the signs of fraudulent C-level communication. Often, attackers will make the “Display name” of an email address appear to be the person in question, however, the actual email address itself, is not from the business-owned domain name.
An easy way that employees can be trained to scrutinize the email received is by looking at the email header. The email header contains the technical information showing how the email arrived in your email inbox. In Microsoft Outlook 2016 as an example, you can view the header by opening the email, clicking the File tab, and then Properties. At the bottom of the box that opens, you will see the Internet headers box which displays the relevant header information.
When scrutinizing email, looking at the display name or friendly name that appears in an email, will often show up correctly as the CEO in question. However, the email address may resemble the CEO’s email address but may also include a fraudulent base domain the business does not own.
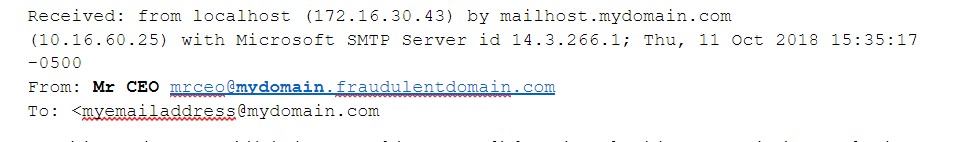
By training employees to quickly look at some of these types of information, fraudulent communication can often be identified. Additionally, the IT team can certainly be enlisted to help identify these types of fraudulent characteristics of emails that may come through. By properly training employees to look at these identifying marks as well as getting the help of the local IT team, can save employees from making costly mistakes.
By scrutinizing the request, employees can often screen out the most fraudulent requests. Employees need to ask themselves questions such as:
- Has the CEO ever asked me to do something like this before?
- Does this seem like an odd request?
- Is there a different person such as the CFO who would generally handle this type of request?
- Why am I being asked to do this?
When in doubt, confirm the request with your supervisor. It never hurts to get additional employees looking into a request, especially if it involves a large sum of money or sensitive information. Attackers generally single individuals out for just this reason – the more employees scrutinizing an email, the more likely it is to be deemed as fraudulent if it truly is.
Organizations often benefit from putting into practice business procedures to verify transactions or send information. Again, the more employees you have involved in various checks and balances, the better. Someone is likely to spot the fraud. Some organizations may put into place a code or passphrase between individuals so that if the code or passphrase is not communicated, the transaction will not be made.
Scoping down who has access to transfer funds is certainly a great idea. If everyone in finance has this ability, the potential fraud target is expanded. If only one individual can transfer the funds, the target becomes much smaller and potentially more difficult to ascertain.
Organizations need to evaluate their own processes and procedures as it relates to transferring money and approving the communication of sensitive information. By continually evaluating these processes and procedures, organizations can help to protect against fraud such as is carried out by the CEO fraud attack.
Data Protection in the Cloud
It is more and more common for businesses today to be leveraging the public cloud for storing data and leveraging cloud-based email systems. Organizations want to make sure they have adequate data protection as well as cybersecurity mechanisms in the public cloud and be able to enforce the same policies in the public cloud as they do on-premises.
Spinbackup allows organizations to effectively employ data protection and cybersecurity technology in both Google’s Google Workspace and Microsoft’s Office 365 environments. Such functionality as automated backups allows data to be protected in an automated fashion. Spinbackup’s Insider Threats detection module also allows machine-learning CASB intelligence to detect odd behavior from employees whose accounts may be compromised or who are exhibiting unscrupulous behavior.
Attacks such as the CEO fraud attack helps to verify the need for strong data protection and cybersecurity measures to be in place, both on-premises and in the public cloud. Spinbackup has organizations covered in protecting their public cloud resources.
Concluding Thoughts
CEO fraud is a very real threat to organizations’ monetary funds and sensitive information. Many businesses from small to large have been duped into sending large sums of money or sensitive information based on requests from attackers posing as C-level executives.
By playing on basic human nature and using social engineering, attackers convince unsuspecting end users into thinking they should follow instructions without asking any questions or scrutinizing the request. The protection against CEO fraud should involve a combination of both technical and human factors that help to provide effective defenses to organization resources.
The human protective defenses are arguably the most important. By training employees to effectively scrutinize communications such as can come through email by evaluating the email address and even asking basic questions can prevent these types of attacks. CEO fraud attacks are on the rise.
Attackers are preying on all types of organizations and are having relative success at gaining access to large sums of money or valuable, sensitive information. Organizations must be on guard for these and other types of attacks that can compromise data integrity.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...
Data Loss Prevention Techniques for 2025 and Beyond
It’s painstakingly clear that data loss is a major challenge facing businesses today. Our experts...
What is SaaS Security? Challenges & Best Practices
Businesses increasingly rely on Software as a Service (SaaS) for increased efficiency, collaborativeness, and scalability....


