Password Spraying Attack: How to Protect Your Business
Password spraying attacks are becoming increasingly popular among cybercriminals wishing to gain unauthorized access to corporate networks. Learn what these attacks are, how cybercriminals carry them out, and how to prevent them.
What is password spraying?
Password spraying is an attack technique used by cybercriminals to get the credentials of a user and access their corporate networks or SaaS environments. It is based on the fact that many people usually do not like complex secure passwords like S3%7ghI80O and instead use something simple like 123456. All a criminal needs to do is to find a company’s employee with a simple password. For this purpose, they use special password-spraying tools and lists of employee emails they get from online databases or generate on their own.
The success rate of password spraying is said to be 1% for accounts without password protection.
Password spraying vs other types of attacks
Password spraying vs brute force attack
A brute force attack focuses on one email address at a time and tries to ‘guess’ a password to it. Many SaaS solutions have created protection against this technique. They lock out the criminal after several attempts. Spray attack uses several popular passwords against multiple accounts.
Keylogging
Keylogging requires special malware installed on a device. This program tracks the passwords that a user enters in different programs. It then provides the exact password to a cybercriminal.
Phishing
Phishing is sending the link to a malicious application, tricking the victim into believing that they enter their credentials into a secure program. Meanwhile, they grant access to their environment to malware.
How the password spray attack works
In this section, we’ll talk about how cybercriminals carry out their password spraying attacks.
Preparation stage
At this stage, cybercriminals will generate lists of their potential victims (list of organizations and working emails of their employees) and pick the passwords for the attack.
Obtaining the users’ email addresses of a certain organization is easier than one can imagine. In fact, all you need is one email address of a worker, a list of employees, and an email checker.
A list of employees can be easily obtained from a company’s website and LinkedIn. Generating the email addresses is a no-brainer either. As a matter of fact, many companies use a certain scheme, a unifying principle to create email addresses for their staff.
For example, an organization can use the first letter of the first name + last name. So John Brown will have sbrown@domain.com. Other examples would be the first letter of a given name + dot + family name; or forename + dot + surname. Many people use similar logic when creating their emails for personal use, e.g. sam.brown@gmail.com.
That’s why, once you know one email address of an organization’s employee, you can easily generate the rest of them. Furthermore, there are tons of tools that can verify the correctness of an email address. They are completely legal as they are used by marketers and salespeople to generate the send-out lists.
An example of a free online email checker
Once a cybercriminal has generated and checked the list of email addresses, they can proceed with a password spraying attack.
Usually, they take the most popular passwords used by people. You can easily find them by googling. It is absolutely amazing but the most popular passwords haven’t changed much from the first days of the Internet. We did research and found the most used passwords of 2022 and previous years and compiled them in a comprehensive infographic:
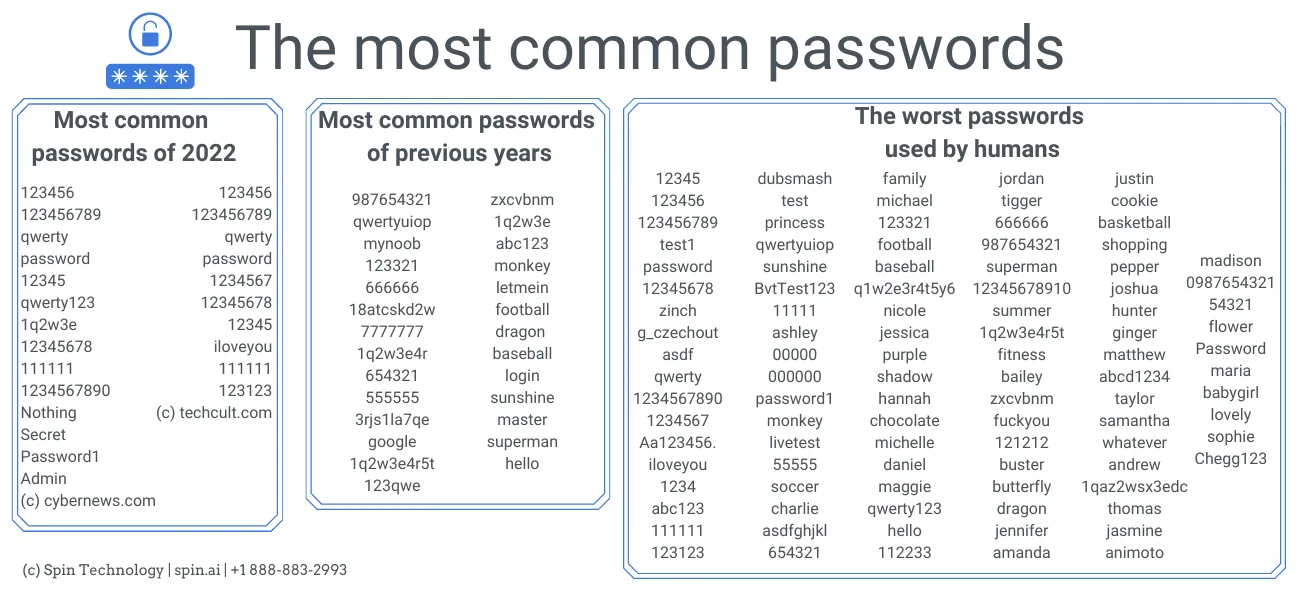
Cybernews recently posted a very good article analyzing the use of different words as passwords. They divided them into categories. Here are several examples of the most popular words by category:
- Year: 2010
- Name: eva
- Sports team: suns (meaning NBA’s Phoenix Suns)
- City: abu (meaning Abu Dhabi)
- Season: summer
- Month: may
- Day: friday
- Food: ice
Execution stage
Once a cybercriminal has formed a list of emails and picked the popular passwords they can initiate the attack. There are plenty of tools that enable automate password spraying. There’s no need to go to the dark net, you can find many of them via regular search engines.
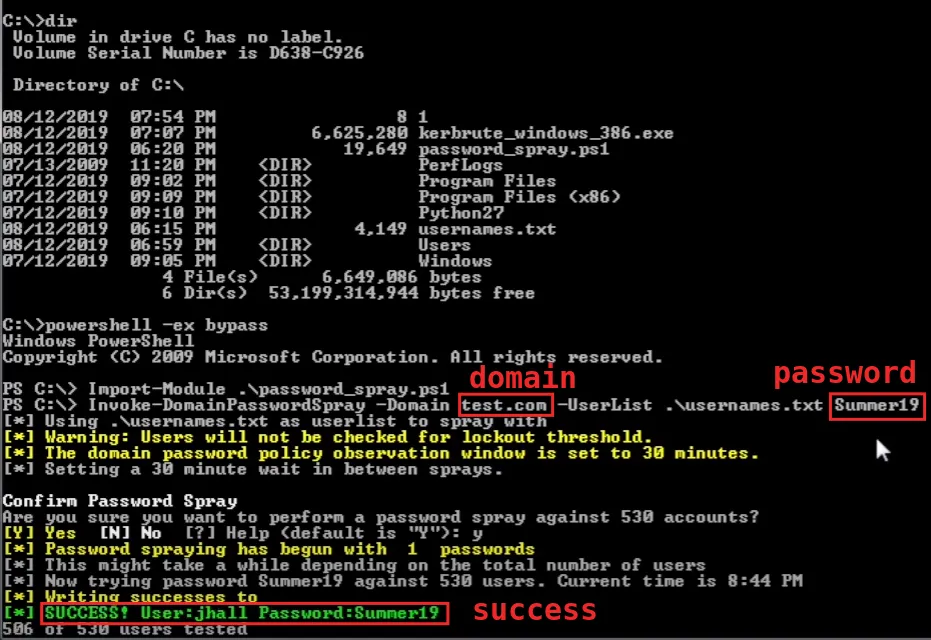
The picture below is the screenshot from a YouTube video that explains in great detail how to carry out the spraying attack. It took the tool approximately 4 seconds to check 530 usernames in a test environment to find one account that had the password Summer19.
How to prevent password spraying attack
There are several ways to protect the corporate environment from password spray attacks.
Regular cybersecurity training for your employees
Even people working in cybersecurity and understanding all the risks of cybercrime can become sloppy and carefree as time goes on. Cybersecurity precautions create additional discomfort for your employees which they naturally want to avoid. Regular training can remind them of the consequences of uncautious behavior. Explaining that millions of people around the world use 123456 and that cybercriminals are aware of it can be really helpful.
Enforcing multi-factor authentication
This is probably the best way to secure your users from password spraying. However, it’s not available in all programs. Furthermore, certain companies don’t want to enforce such a policy on their employees.
Both Google Workspace and Microsoft Office 365 allow their Admins to enforce multifactor authentication. In the case of GW, it is called 2-step verification. Here are short guides on how to enable it in both SaaS programs:
Google Workspace:
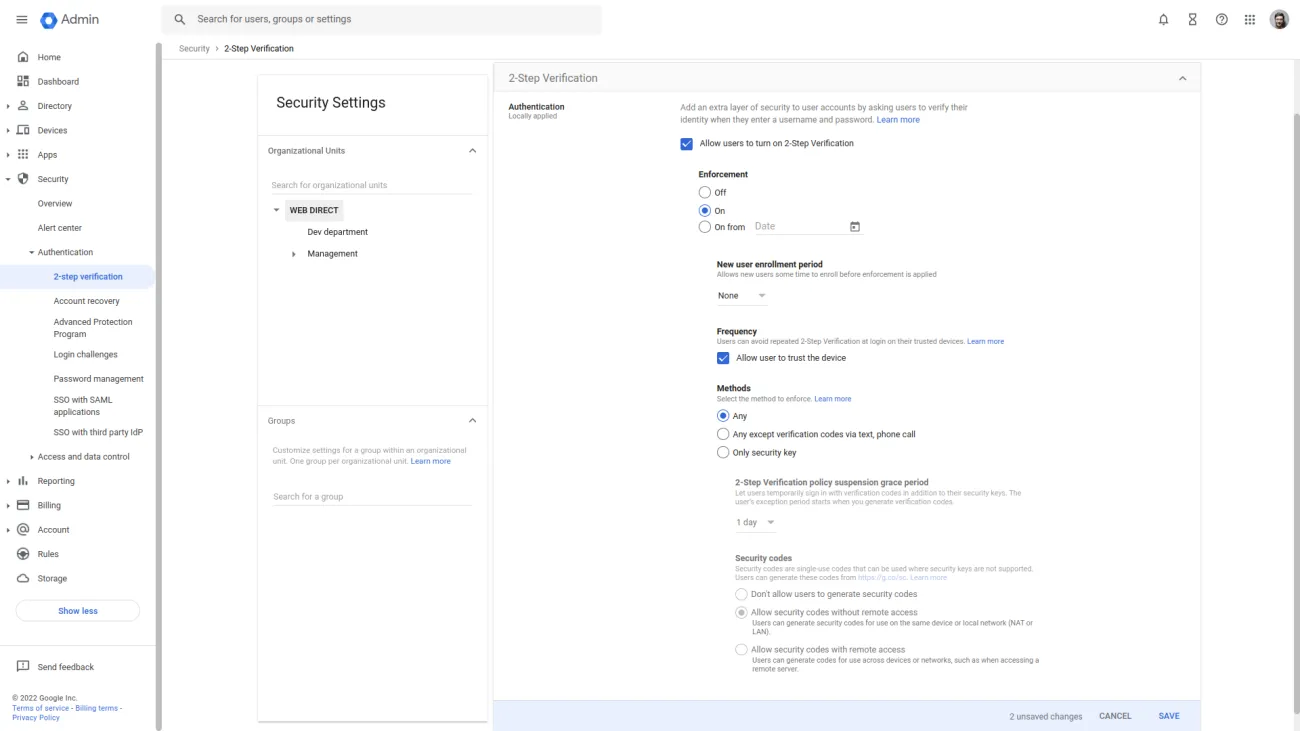
1. Log in as an Admin to Admin Console.
2. Click on Security in the left menu, then Authentication -> 2-step verification.
3. Look for Enforcement and click On. Save changes.
Microsoft Office 365
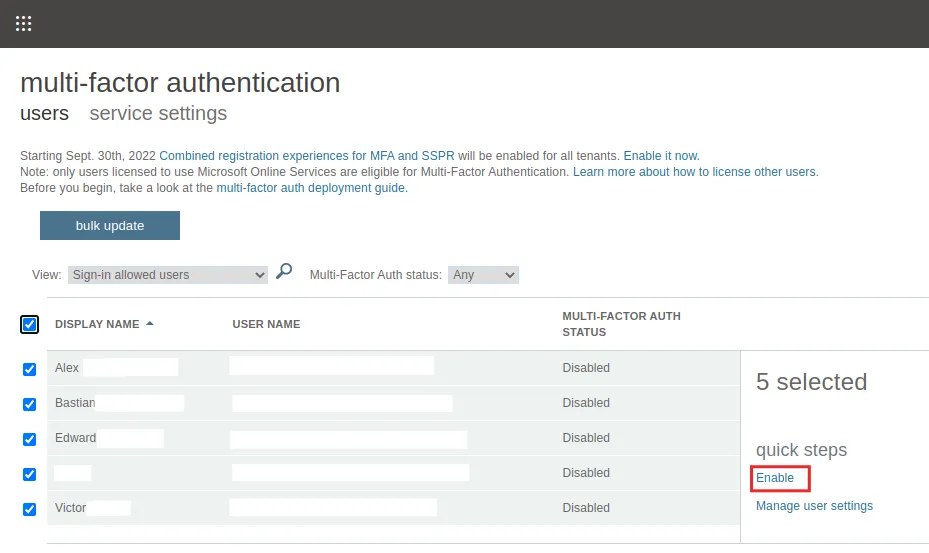
1. Log in as an Admin to Admin Center.
2. In the left menu, click on Settings.
3. Scroll to and click on Multi-factor authentication. In the pop-up, click on Configure multi-factor authentication.
4. You will be redirected to the respective page. Tick all your users and then click Enable as shown in the screenshot below:
Protect your business-critical data from loss with Microsoft Office 365 backup solutions.
Regular password resets
Some programs enable Admins to reset user passwords on a regular basis forcing employees to come up with new passwords. Regular log-outs can also be helpful as users who forget their passwords have to create new ones when they re-login.
Using monitoring tools
Tools like SpinOne enable Admins to monitor user activities via APIs. As a rule of thumb, such tools have filters to sort cyber events by category and monitor them more easily. In a screenshot of SpinOne platform below, you can see the list of log-in events in Google Workspace:
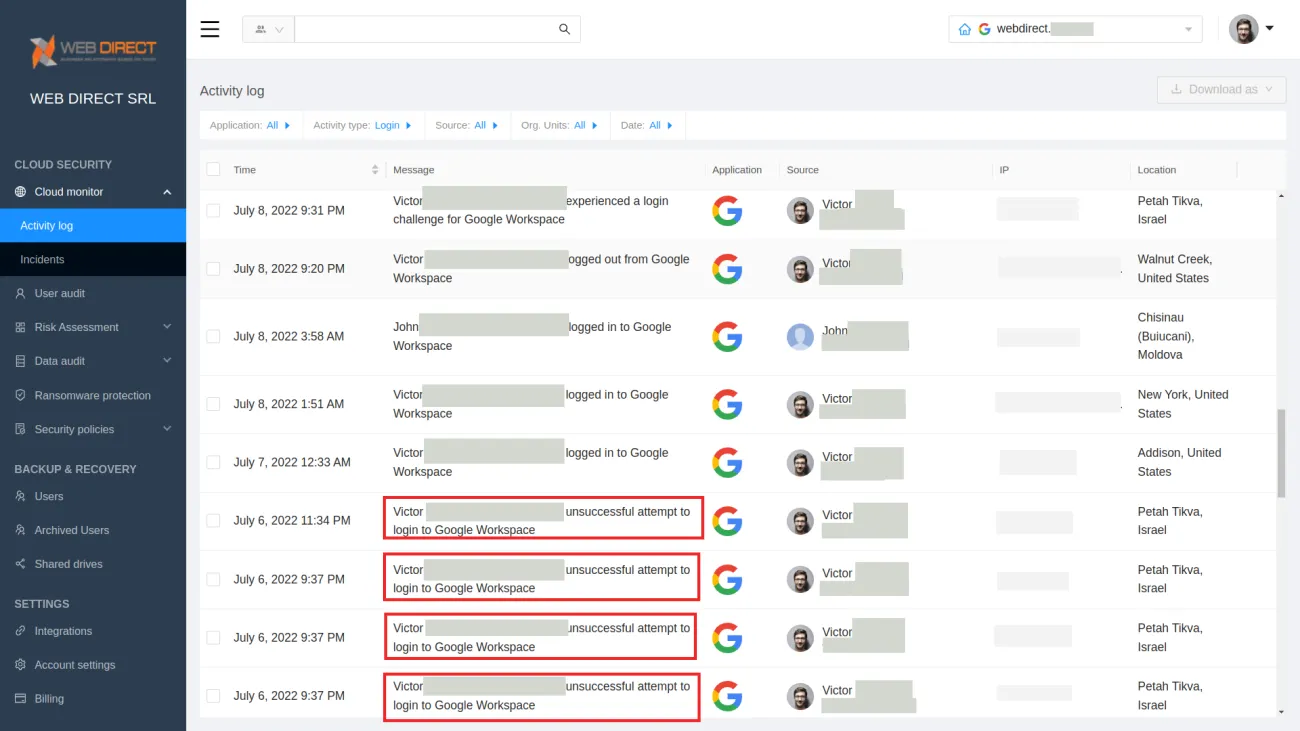
As you can see there were several unsuccessful attempts to log in to one account on July 6, 2022, from a specific location from one IP. It looks more like a brute force attack. If you see several unsuccessful login attempts to multiple logins (or most, or all) that means your environment has been attacked with password spraying.
Frequently Asked Questions
What is the difference between brute forcing and password spraying?
Both brute forcing and password spraying are used in hacking to gain unauthorized access to accounts, yet they differ in their approach.
In brute force attacks, an attacker systematically tries every possible combination of characters, often starting from the simplest and most common ones. Thus, the brute force attacks are very time- and resource-intensive and can be effective if the password is weak, short, or lacks complexity.
Password spraying, in contrast, relies on trying a few common passwords against a large number of user accounts. So, it is a more targeted and efficient approach, and it is less likely to get detected.
What are the 3 main types of password attacks?
The three most common types of password attack methods include brute forcing, dictionary attacks, and password spraying.
- Brute forcing is the attempt to guess a password by trying all possible combinations of characters.
- Dictionary attacks try to guess passwords by trying commonly used passwords, such as words found in the dictionary.
- Password spraying tries a small number of common passwords against many accounts trying to access at least one of them.
What are the six 6 types of attacks on network security?
The six common types of attacks on network security include:
- Malware: Malicious software like viruses, ransomware, and spyware can infect systems, disrupt operations, or steal sensitive information.
- Phishing: Phishing involves sending deceptive emails or messages to trick users into revealing sensitive information, such as login credentials or financial details.
- Distributed Denial of Service (DDoS): These attacks overload a network or system with excessive traffic, causing disruptions or making services unavailable.
- Brute Force: Attackers attempt to gain unauthorized access to systems or accounts by trying all possible password combinations until they succeed.
- Zero-Day Exploits: Attackers target vulnerabilities in software or hardware that are not yet known to the vendor or lack available patches.
- Insider Threats: These attacks involve individuals within an organization with access to sensitive data who intentionally or unintentionally compromise security.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...