Ransomware Detection Using Machine Learning
“Ransomware Detection Using Machine Learning” now serves as a watchful guard in the extensive world of data. This is similar to how a solitary administrator faces the complex screens of his security console, much like looking into “The Matrix”.
His attention is firmly locked onto the multitude of screens before him. His main task is to spot the menacing presence of ransomware, a serious threat to your data.
The sheer scale of today’s data and network traffic is immense. This makes it impossible for a single administrator to identify ransomware threats using conventional methods. Mere manual efforts are inadequate. The era of scrutinizing network traffic, sifting through logs by hand, and using other manual approaches to effectively detect security threats is now behind us.
Modern ransomware combat necessitates the employment of innovative tools, techniques, and technologies. Among these, Machine Learning (ML) emerges as a crucial component in effective ransomware defense strategies.
Leveraging Ransomware Detection Using Machine Learning
Is there a better way to detect today’s ransomware threats? With all the new ransomware variants that are in the wild along with the monumental amount of attack vectors that can exist both on-premises and in the cloud. There is – ransomware detection using Machine Learning (ML).
What is Machine Learning?
When you consider Machine Learning, you might imagine scenes from the movie “Terminator”. In this movie, machines become conscious and dangerous. However, contrary to this fictional image of machines “learning”, ML is a good thing when it comes to detecting threats such as ransomware.
According to SAS Analytics Software & Solutions, Machine Learning is “…a method of data analysis that automates analytical model building. It is a branch of artificial intelligence based on the idea that systems can learn from data, identify patterns and make decisions with minimal human intervention.”
Computers are able to use a massive amount of data they collect to make determinations using a series of special ML algorithms. These ML algorithms adjust themselves as more data is gathered.
There are many different machine learning mechanisms that are used today for both detecting and protecting your data from a ransomware infection. However, many of the current means used are considered to be a legacy at this point.
(Source)
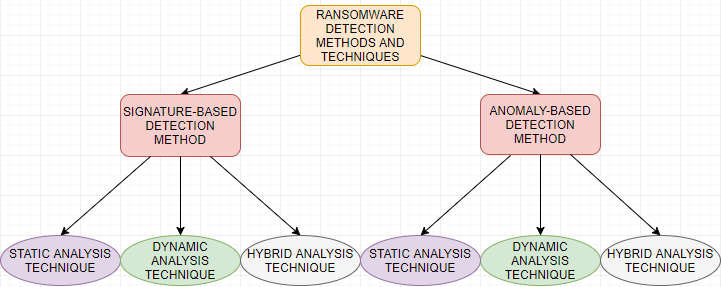
Let’s take a look at the first two ransomware detection methods and see the advantages and disadvantages of using these types of detection methods.
Signature Detection
Since the early days of virus protection, signature-based detection was the de facto standard for detecting malware threats. The signature-based protection works off the premise of having a signature that covers the specific malware to know how to detect the threat.
You can think of a signature like a “fingerprint”. The signature of the malware is the specific fingerprint that allows the software to correctly identify the malware in question. The problem with signatures is they work relatively well for known malware but do not cover threats they do not know about. This includes zero-day threats (threats that exploit an unknown bug or security vulnerability).
Signatures are extremely easy to get around since the known signature of a piece of malware can be changed by copying it or otherwise altering the code in some way. This allows attackers to easily get around this particular way of identifying and stopping ransomware variants of known threats.
The dark web offers “Ransomware-as-a-Service” options. This enables malicious actors to customize known malware, such as ransomware, to target specific organizations.
Abnormal Traffic Detection
Abnormal traffic detection is considered a step up from signature-based detection. Anomalous traffic is detected based on many different metrics including network intrusion detection, and other traffic detections that may be identified as malicious.
The main downside of using the abnormal traffic detection mechanism is the high false-positive rate. What this means is there is a good chance that legitimate network traffic may get classified incorrectly as ransomware or other malicious traffic. The downsides of this include breaking legitimate applications and potentially even corrupting data if data exchanges are stopped mid-stream.
As you can see, both ransomware detection techniques – abnormal traffic detection and signature-based detection – are not reliable solutions for detecting ransomware.
New detection mechanisms must be used to more effectively catch ransomware infections that may target your organization.
File behavior detection
When Machine Learning is implemented in the realm of file behavior detection, this can create an extremely powerful solution for detecting ransomware.
One of the powerful tools that machine learning brings to the fight against ransomware is the ability to predict. Machine Learning is much like human learning in a sense. When you get to know a good friend, you learn their tendencies and behaviors over time. After a time, you can even predict how that friend will react in various situations.
This is similar to Machine Learning. Legitimate normal code execution and applications present a certain type of behavior. Over time, ML “learns” how normal programs act. It does this by taking in large amounts of data. This analysis can involve interactive debugging or post-mortem code execution.
In this detailed and very thorough examination of legitimate code execution, ML becomes very good at identifying programs that are impostors and have malicious intent.
In the context of using Machine Learning to detect security threats, software solutions running on top of computers can essentially “learn” what is normal and what is abnormal and then make intelligent decisions prompting specific actions.
“Normal” baselines may represent what normal day-to-day activity looks like, both from a user perspective as well as from a resource perspective. This can include logins, file access, user and file behaviors, resource usage, and other pertinent key indicators of normal activity.
This “learning” process may take a number of days or weeks depending on how much data needs to be ingested to determine what normal activity looks like, statistically speaking, based on the data that is gathered. Once this normal baseline is gathered, anomalies that are outside of the normal baseline can be effectively identified and scrutinized.
Behavioral Analytics Systems – the Best Method for Detecting Ransomware
Machine Learning is used to build behavioral analytics systems that are trained to detect anomalous file behavior. These systems provide a great way to recognize and stop ransomware infections from progressing through the file system. Solutions that make use of ML are able to recognize anomalies in file behavior that may include changes being made by ransomware.
As you most likely know already, ransomware uses file encryption to hold your data hostage so that you are forced to pay a ransom to retrieve your data. Not only is ransomware holding your data hostage, but certain new variants are also using the threat of leaking your data along with holding it hostage.
The Maze ransomware uses threats of leaking data as leverage to get the victims to pay the ransom. This takes ransomware to a whole new level of malicious behavior. As ransomware threats and capabilities continue to evolve, using Machine Learning ransomware detection is going to be required to be completely effective.
Why Backup Solutions Need Built-in Ransomware Detection
As shown by the Maze ransomware that not only holds your data hostage but also threatens to leak your data, backups only protect you from part of the ransomware threat. Even if you have effective backups and are able to restore your data quickly, you now risk having your sensitive data leaked to the public or dark web.
This emphasizes that you need a two-fold approach of both protecting against ransomware infecting your files and having effective backups. If ransomware does infiltrate even those initial defenses, you want to be able to stop it as quickly as possible. This helps to ensure, if criminals threaten to release data, the scope will be very limited if not minimal.
Backups come into play after the initial ransomware threat has been neutralized and the hopefully small amount of damage caused by the ransomware can be remediated. This helps to illustrate why backup solutions need built-in ransomware detection to be effective in the landscape of today’s ransomware threats and capabilities.
SpinOne – Unique Ransomware Protection Using Machine Learning
With the momentum of cloud migrations across the board, attackers are certainly aware that cloud environments are a prime target for holding your files hostage. There have already been proven means to infect cloud environments either via file synchronization of ransomware-encrypted on-premises files or encrypting email inboxes as in the case with RansomCloud.
Software-as-a-Service offerings like Google G Suite and Microsoft Office 365 are prime targets of ransomware infection since these are the two most popular SaaS offerings that your business may use to host cloud storage and email. Protecting your environments hosted in these SaaS offerings is absolutely crucial.
There is a solution that stands out among the others in the cloud backup and protection space – SpinOne. SpinOne provides a unique solution that leverages both enterprise-grade backups of your cloud SaaS data and also Machine Learning-enabled ransomware protection to detect abnormal file behavior.
SpinOne analyzes file-level behavior for any anomalies. If ransomware encryption patterns are recognized, SpinOne blocks the source of the attack and revokes access to the user account to stop any further encryption processes.
SpinOne’s ML-based logic does not block the victimized user account so the user can proceed to work. This is a tremendous benefit as this could be your CEO’s account that has been hijacked. It will still allow the user to be productive while at the same time protecting resources for any further attacks associated with the account.
After protecting and blocking the ransomware attack, SpinOne’s data protection capabilities kick in as its unique Ransomware Protection module starts automatically restoring any files that may have been affected by the ransomware attack. The granularity of the restore operation performed by SpinOne is limited to only the specific files affected. This is without any administrator intervention or any other manual actions.
How machine learning works in SpinOne
On top of the automated actions carried out by the SpinOne solution, administrators are automatically notified of the ransomware attack and the Ransomware Protection restore operation.
SpinOne Ransomware Protection Workflow:
- Identify new ransomware attack
- Automatically block access in real time
- Identify any encrypted files
- Recover the files automatically from last successful backup
- Send Security alert to notify administrators of a ransomware attack
SpinOne uniquely provides a truly end-to-end solution to fight ransomware in your SaaS cloud environments. This results in 100% accurate ransomware protection for your files in the cloud.
SpinOne Backup and Protection
Aside from the Ransomware Protection module included with SpinOne, it provides a number of cybersecurity defenses that can stop ransomware dead in its tracks before it can even infect any files in your SaaS environments. Additional SpinOne security features include:
- Risky apps control – block risky third-party applications from integrating into your SaaS environment
- Behavioral analysis – Detect anomalous behavior from end-users
- Insider threat prevention – Effectively identify a malicious end-user or one that has compromised credentials
- Brute-force login detection – Provides visibility to brute-force login attempts to your SaaS environment
- Abnormal data download protection – Is a user performing an unsanctioned data download? Identify and prevent data leakage
- Reporting and alerting – Realtime alerts and reporting based on ML intelligence
- Policy-based control – Configure different policies based on different business units or other organizational boundaries
How Widespread is Machine Learning in Cybersecurity?
Leading cybersecurity experts are recognizing and publicizing the need for Machine Learning use in the cybersecurity fight. The volume and sophistication of today’s attacks require using the computing power available to help stop threats like ransomware.
The scale and sophistication of attacks have grown considerably:
- Advanced attackers and techniques
- Cybercrime for sale has become popular
- Growing collateral damage
Why is ML more relevant now than ever before?
- Compute power has become more powerful than ever
- The volume of data has massively increased
- Numerous data sources are present
- Data can be collected and analyzed quickly and efficiently
- Computing costs are lower than ever
- Free open-source tools
- Codesharing in the community
Companies Already Using Machine Learning Currently
You don’t have to look very far to see very large companies already leveraging Machine Learning as part of their security solutions. Note the following examples:
Microsoft:
- Currently using ML in the Windows Defender Advanced Threat Protection solution that is part of Windows 10. It automatically updates and employs cloud AI and machine learning algorithms to spot threats.
Splunk:
- Splunk’s Enterprise Security and Splunk User Behavior Analytics use machine learning to detect threats so they can be identified and eliminated quickly
Blackberry:
- Blackberry currently specializes in cybersecurity solutions that utilize machine learning. Recently they purchased Cylance which employs AI/ML logic for cybersecurity
The above three examples are only a few of the many large companies leveraging Machine Learning capabilities in their cybersecurity solutions and products effectively. We can expect that Machine Learning will only become even more widespread in the realm of cybersecurity across the board as companies recognize its effectiveness in eliminating security threats.
Concluding Thoughts
Today’s ransomware variants require new technologies and tools to fight them effectively. Traditional detection and protection tools that use signature-based detection or abnormal traffic detection are not totally effective against new ransomware attacks.
Using solutions that leverage to detect abnormal file behavior is an effective means to quickly detect ransomware activity and stop it as soon as possible. SpinOne is a unique solution that leverages this approach. Not only does SpinOne use Machine Learning to power its abnormal file behavior engine, it also provides effective backups of your cloud environment.
Using these tools together effectively, SpinOne can stop ransomware and revert any damage it may have caused automatically.
Be sure to check out a Try SpinOne for free for either G Suite or Office 365.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...

