SaaS Ransomware Protection: Guide to Achieving Compliance
We have seen a literal pandemic for the past 18 months or so. However, another pandemic is sweeping the digital world – ransomware. Ransomware is quite possibly the most dangerous threat to business data that businesses have had to face. It is as dangerous as it is sly in infiltrating environments and silently destroying data. As many organizations migrate their business-critical workloads and data to the cloud, many business leaders may assume that ransomware is only a threat to on-premises data. However, this couldn’t be further from the truth. Cloud SaaS environments are also at risk and targeted by ransomware. Therefore, organizations must implement SaaS ransomware protection for achieving compliance and securing their data.
The rising threat of ransomware
It seems like every few days at most, we hear about the next major ransomware attack. The news is riddled with stories of small to large organizations who have had their data encrypted by ransomware. Earlier this year, in May 2021, a major ransomware attack crippled Colonial Pipeline, a major fuel supplier to the eastern United States. In the attack, mission-critical systems were affected, taking over 5500 miles of pipeline out of commission for days.
This ransomware attack on critical services shows how devastating an attack can be for digital assets and essential day-to-day services. Unfortunately, this type of story is becoming more and more common as attackers target lucrative large enterprise organizations with plenty of cash and business-critical data vital to their livelihood.
Moreover, ransomware gangs are no longer simply encrypting data and holding the data hostage until payment. They are using a new tactic to coerce organizations into paying the ransoms demanded. Ransomware gangs are threatening to intentionally leak sensitive data obtained in the ransomware attack to the dark web.
In the case of the Colonial Pipeline attack, months later, in August 2021, Colonial acknowledged that attackers stole the personal information of some 6000 individuals due to the ransomware attack. So on top of being a security disaster, ransomware attacks are a compliance nightmare.
Organizations must double down on SaaS ransomware protection across the board. Ransomware variants are also now cloud SaaS aware, meaning they can attack your critical data housed in cloud SaaS environments, including Google Workspace and Microsoft 365.
Ransomware can attack cloud SaaS environments
As mentioned at the outset, there is a misconception about ransomware that it is an “on-premises” problem. However, attackers have evolved ransomware variants to include capabilities to encrypt data in cloud SaaS environments. There are a couple of primary ways cloud ransomware can infect cloud SaaS environments. These include:
- File synchronization
- OAuth token abuse
Let’s see how each of these cloud SaaS technologies can lead to a ransomware infection of cloud SaaS data.
File synchronization
Most are familiar with the popular Google Drive Sync and Microsoft OneDrive tools to synchronize local data to cloud SaaS storage. File synchronization allows synchronizing files placed in the respective Drive or OneDrive folders, which will initiate a synchronization operation to the cloud. Users who upload new files will trigger synchronizations for users whose sync utility is connected to the shared cloud SaaS storage location.
Herein lies the danger to business-critical data. If a single user connected to shared cloud storage becomes infected, the ransomware encryption process will be seen as file changes and synchronized to cloud storage. Ransomware-encrypted files will replace the good copies of the files so that everyone will only have access to the encrypted copies of the files.
OAuth token abuse
Cloud SaaS environments use the OAuth authorization protocol to grant access to cloud resources on behalf of a specific user. The OAuth tokens granted allow applications to act on behalf of the user without knowing the user’s password. It helps to bolster the security of user account passwords. However, attackers have increasingly targeted OAuth authorization tokens by means of social engineering and phishing attacks.
The way OAuth token abuse works is an attacker will send an end-user a phishing email that looks legitimate. The email may have the correct branding, pictures, logos, and other visual cues that it is from a legitimate and trusted source. The email may direct the user to install “an update” or other legitimate “security update” to the cloud SaaS environment from a trusted source.
However, instead of an update or other legitimate installation, the cloud application is a malicious cloud application containing ransomware. Once the user grants the OAuth token to the malicious cloud application, the ransomware has all it needs to start encrypting data.
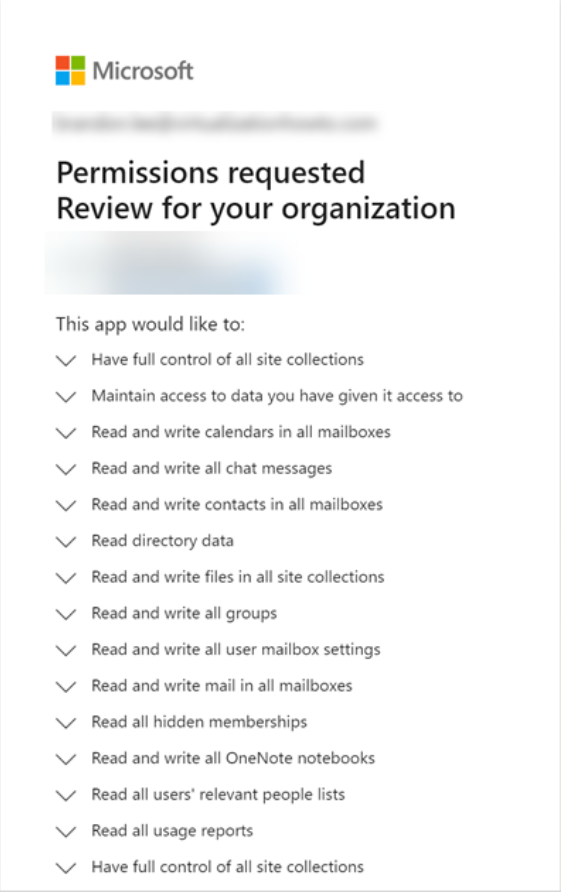
Users become preconditioned to simply granting permissions requests in cloud SaaS environments that often, requested permissions are not scrutinized closely. The common cloud SaaS permissions dialog shows an OAuth request for high-level permissions in Microsoft 365. End-user training and strong third-party application control are needed to prevent users from installing malicious cloud SaaS applications.
High-level cloud SaaS permissions requested in Office 365 Data Protection
The importance of ransomware monitoring and remediation
It is essential for organizations using cloud SaaS environments to have proactive ransomware monitoring and remediation processes to help curtail the damage caused by a ransomware attack. There are many reasons for quick action. These include:
- Less damage to data and business reputation
- Quicker Restore Time Objectives (RTOs)
- Reduced likelihood of throttling
Less damage to data and business reputation
First, ransomware is extremely destructive to your data and your business reputation.
The quicker a ransomware attack is discovered, the less damage there is to your data and business. Unfortunately, while cloud service providers like Google and Microsoft have improved their cybersecurity defenses against ransomware, they still leave much to be desired from a monitoring and proactive remediation standpoint.
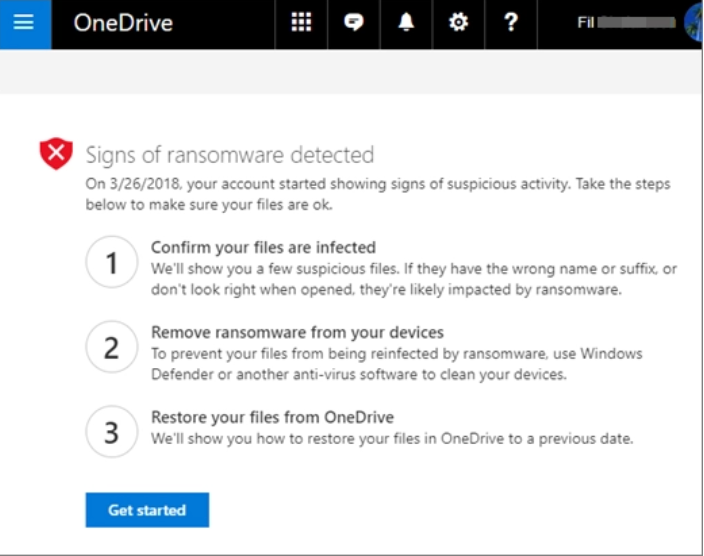
Currently, native ransomware protection is very reactive and passive. In their ransomware detection and recovering your files KB, Microsoft mentions:
When Office 365 Ransomware Protection detects a ransomware attack, you’ll get a notification on your device and receive an email from Microsoft 365. If Microsoft 365 detected a ransomware attack, you see the Signs of ransomware detected screen when you go to the OneDrive website (you might need to sign in first). Select the Get started button to begin.
Signs of a ransomware attack have been detected in Microsoft Office 365
Tenant customers simply receive an email that Microsoft suspects a ransomware attack has encrypted a large amount of data. Again, this is a very reactive approach. Also, Microsoft recommends you find the source of the ransomware to prevent the encryption process from happening again, even after you restore your data.
Google details very similar customer responsibilities of proper cybersecurity hygiene and other best practices to prevent and recover from a ransomware attack. You can read Google’s best practices to protect your organization against ransomware threats here:
Quicker restore time objectives
The faster a business can respond to and remediate a ransomware attack, the less data is affected. The time it takes to recover from a ransomware attack directly relates to the amount of data affected. Therefore, businesses want to have their Restore Time Objectives (RTOs) as low as possible. Proactively responding to a ransomware attack produces drastically better outcomes related to RTOs and the amount of data affected.
Reduced likelihood of throttling
Due to the multi-tenant nature of cloud SaaS environments, cloud service providers like Google and Microsoft impose limits on the number of API (specialized web endpoints) calls tenants can make. Once a customer exceeds the number of API calls, throttling limits are imposed. It leads to greatly reduced API performance.
For example, even if customers can restore data from a third-party backup solution, if large amounts of data are affected, the restore process will likely hit the throttling limitations imposed by Google and Microsoft. Additionally, if customers do not proactively monitor and stop a ransomware infection as soon as possible, recovery will likely require large numbers of API calls, resulting in the likelihood of throttling.
Proactive cloud SaaS ransomware protection
When hours, minutes, and even seconds count with ransomware attacks, proactively detecting and stopping an attack is essential for protecting your data. Unfortunately, native cloud SaaS ransomware protection provides passive, reactive ransomware protection at best. Organizations need a proactive and robust ransomware response.
SpinOne provides industry-leading ransomware monitoring and remediation. In addition, it offers 24/7 monitoring, and artificial intelligence (AI) based detection. The ransomware protection provided by SpinOne not only quickly detects an attack unfolding on your business-critical data, it automatically blocks the source of the attack at a network level.
The SpinOne ransomware protection workflow includes the following:
SpinOne artificial intelligence (AI) and machine learning (ML) algorithms detect a ransomware attack
- It automatically blocks the attack source in real-time
- SpinOne algorithms identify the number of damaged files
- It automatically recovers damaged files from backups (configurable)
- SpinOne proactively notifies cloud administrators of the attack
With this approach, SpinOne limits the damage ransomware can inflict on your environment. In addition, it significantly reduces downtime by providing a 2-hour Incident Response SLA and zero hidden costs by over 90%, saving millions of dollars per ransomware attack.
SpinOne SaaS ransomware protection
Ransomware is a threat to business-critical data worldwide. As a result, organizations must proactively protect their data and limit the damage path of a ransomware attack. Protecting SaaS data in cloud services like Google Workspace, Microsoft 365, and Salesforce is your responsibility. Stay safe and schedule a demo
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...