Salesforce Shield: a Comprehensive Overview for SMBs
Salesforce Shield is a powerful security tool by Salesforce. In this article, we review the tool from the standpoint of small and medium businesses. Here is a summary of the tool’s features, pricing, customer rankings, and pros and cons of the solution.
What is Salesforce Shield?
Salesforce Shield is a security tool for Salesforce CRM encompassing three solutions: Event Monitoring, Field Audit Trail, and Platform Encryption. A business can purchase any of these solutions separately or the three of them together.
The solution enables companies to achieve several goals:
- Data security
- Compliance
- Governance
- Transparency
Salesforce Shield provides an advanced data encryption solution and enables data and app monitoring. With it, you can automate your security policies and audit compliance. Its features include:
- Multi-Factor Authentication
- Access Management
- Mobile Device Management
- Device Control
- Database Management
- Data Encryption
- Data tracking
- Engagement tracking
- Data history
- Encryption keys
- Multi-tenant
- Remote data access
- Transaction security
- Field audit trail
- Data triggers
- Data archive & storage
- Data permission
- Event monitoring
- Platform encryption
For more information on the key features of Salesforce Shield, please go to the article’s next section.
Pricing
Salesforce Shield pricing depends on 2 main factors: the number of components you purchase and your business’ “net spend.” Salesforce defines the latter as the amount of money you spend on “other applicable, technically compatible Salesforce products.”
Thus the cost will be calculated as a percentage of your net spend as follows:
- Event Monitoring – 10%
- Field Audit Trail – 10%
- Platform Encryption – 20%
- Salesforce Shield – 30%
The solution’s cost will change based on buying or stopping SF products and increasing/decreasing the number of users. It will also depend on any changes in the price of the abovementioned products.
Thus, there’s a high probability that the Salesforce event monitoring cost will grow as business ‘engagement’ in the Salesforce environment tends to increase over time. And so are the product prices.
Three tips on how to reduce the price of Salesforce Shield:
- Negotiate lower prices for Salesforce products.
- Negotiate a lower percentage for your business from the start.
- Make sure that you fix the percentage in your agreement with Salesforce.
Shield Platform Ratings
On G2 the tool received mostly positive feedback from small and medium-sized companies. Most find it a valuable security solution. The mentioned drawbacks were the use complexity and somewhat slow performance.
Overall G2 reviews are positive:
- ease of use 7.8
- quality of support 8.1
- ease of setup 8.5.
According to Grid Report for Mobile Data Security Summer 2022, the users estimate Salesforce Shield features for Mobile Data Security as follows:
- Access Management 77%
- At-Risk Analysis 83%
- Multi-Factor Authentication 87%
This list is not complete. Please, find the whole report here.
The website comparecamp.com gives it an 8.8 score based on the following criteria: features, ease of use, customer support, and value for money. Another website, financesonline.com, gives a similar estimation scoring the Shield 8.8.
The functionality of the solution
In this section, we’ll take a closer look at the Shield Platform features.
Shield Platform Encryption
This feature encrypts your Salesforce data across all the applications. The encryption doesn’t impact the performance of essential functionality like search. The Admins have full control over the encryption keys.
The key goal is to secure your data and achieve compliance with existing rules and regulations.
Salesforce Shield vs. Classic Encryption
Classic encryption is the feature of a base Salesforce license. Why does your business need additional encryption?
In the screenshot below, you can see the comparison table between Salesforce Shield Encryption vs. Classic Encryption.
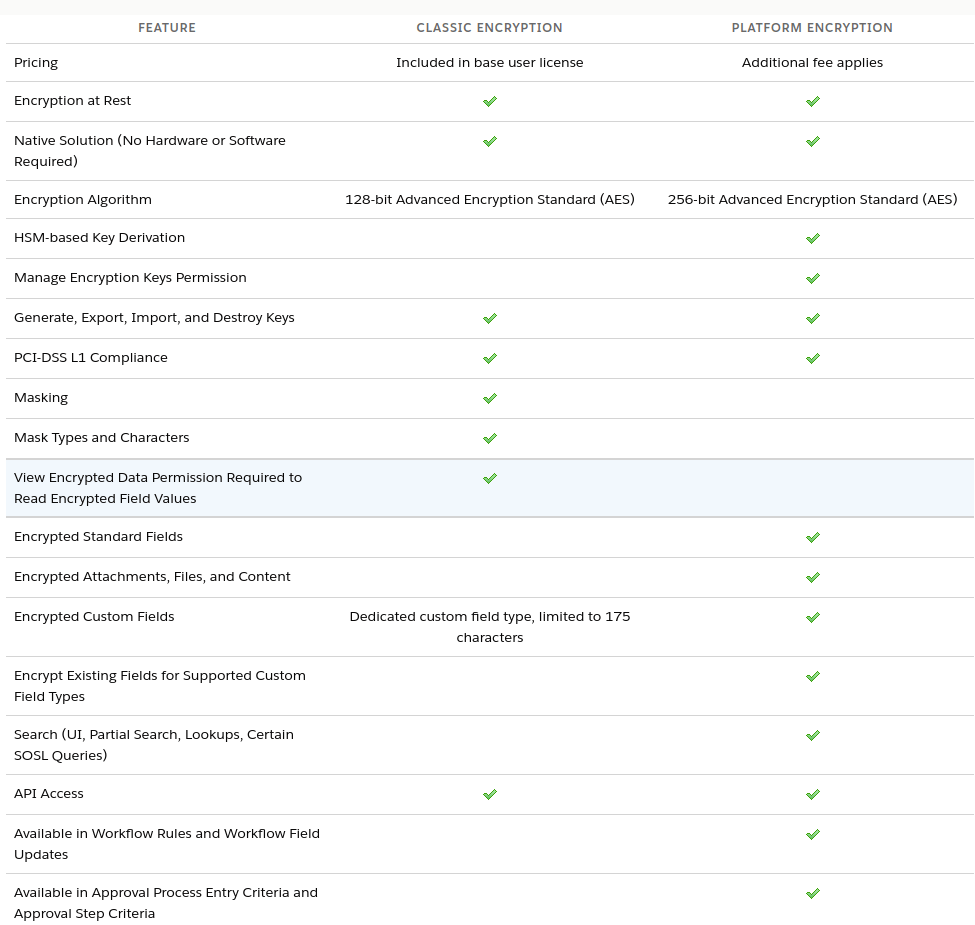
We’d like to point out the features that Classical encryption doesn’t have:
- HSM-based Key Derivation
- Manage Encryption Keys Permission
- Encrypted Standard Fields
- Encrypt Existing Fields for Supported Custom Field Types
- Search (UI, Partial Search, Lookups, Certain SOSL Queries)
- Available in Workflow Rules and Workflow Field Updates
- Available in Approval Process Entry Criteria and Approval Step Criteria
Also keep in mind that the basic version has encryption limitations to the dedicated custom field type, limited to 175 characters.
At the same time Shield doesn’t have the following features:
- Masking (so that your users can’t see certain types of data like CCN)
- Checkmark Mask Types and Characters
- Checkmark View Encrypted Data Permission Required to Read Encrypted Field Values
At first glance, this functionality seems unnecessary for SMBs. The common perception is that usually, it is the enterprises that become the targets of cybercriminals. However, we need to point out one important thing to consider.
Recently we’ve seen a shift in cybercrime victims. Cybercriminals understand that usually enterprises have resources to protect their IT systems. Meanwhile small and medium businesses catering to these companies are not as protected. SMBs become a popular target because of the data they might possess. It is important to protect that data.
That’s why we believe that SMBs need data encryption functionality.
Real-Time Event Monitoring
This functionality uses API to enable you to track the number of significant events that might signify a cybersecurity incident. It can also help understand how your apps are adopted or how performance can be improved. You’ll need data visualization tools to use this data more efficiently.
The monitoring tracks up to 50 types of events, including:
- Access to business-critical data (which user, when, from where)
- Data usage in Salesforce applications
- Logins in Salesforce
- Search within the apps
- Reports
See the full list of events here.
You can use this functionality to enhance security, improve transparency, and boost performance.
This functionality can be tricky in terms of use for SMBs, who often do not have large IT teams, let alone Salesforce administrators. On the other hand, it might provide valuable insights on performance as well as enhance security. So we’d recommend purchasing it.
Field Audit Trail
This functionality enables you to analyze a large data set, set retention policies, and retain your data for 10 years.
Set data retention policies on the following objects: Custom Objects, Accounts, Cases, Contacts, Leads, and Opportunities.
Field Audit Trail vs. Field History Retention
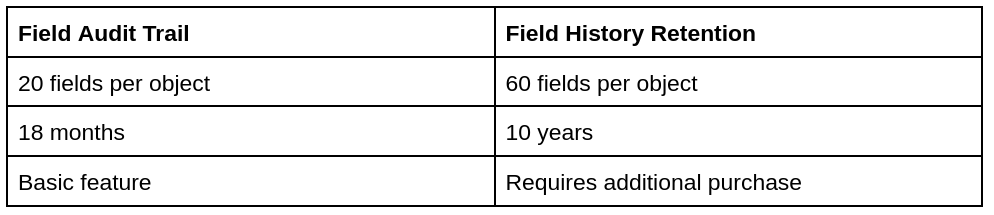
This feature might not be that necessary for SMBs, because they usually do not have large data sets or mandatory periods of data retention. However, it heavily depend on the field you work in.
Pros & Cons of Salesforce Shield
Overall, most customers, as well as independent analysts, give positive feedback to Salesforce Shield emphasizing its multiple advantages. However, no tool is perfect. Thus there are obvious limitations and drawbacks.
Advantages:
1. Achieving compliance
2. Improving data governance and transparency
3. Additional security due to encryption and data monitoring.
4. Improving your retention capabilities.
Disadvantages:
1. Price that is mostly beyond your control.
2. Because of data encryption, certain functionality may be unavailable for certain users or to all users. Similarly, it will disable certain applications.
3. The encryption doesn’t provide masking for data and you have to implement Field level security.
Is the Shield enough for Salesforce Security?
Salesforce Shield is a great security tool, however, it doesn’t protect your data from all the cybersecurity incidents. One of the most frequent incidents in Salesforce is metadata loss due to a developer’s mistake.
The loss of this data can significantly damage the whole architecture of your pipeline in Salesforce and thus paralyze the operations of your revenue-generating team. Salesforce has several native backup tools. However, they do not match the needs of modern businesses.
These tools do not back up all types of data Learn more from our comprehensive guides on Salesforce Backup and Salesforce Recovery Solutions. We recommend purchasing a third-party Salesforce backup tool like SpinOne.
With SpinOne you can:
- back up all types of data, including objects, files and metadata
- back up your sandbox and save hours of developer work
- set automated daily backups
- recover data quickly and directly to Salesforce (no CSV files)
- discover data losses or mistakes with Compare function
Frequently Asked Questions
What are the 4 components of Salesforce Shield?
The 4 components of Salesforce Shield include:
- Shield Platform Encryption that allows encrypting sensitive data at rest across all organization’s Salesforce apps.
- Real-Time Event Monitoring provides organizations with access to detailed performance, security, and usage data on all their Salesforce apps.
- Field Audit Trail monitors the state and value of the organization’s sensitive data for any date and time.
- Einstein Data Detect performs scanning orgs for sensitive data and then takes steps to protect it.
What type of encryption is Salesforce Shield?
Salesforce Shield utilizes a robust 256-bit Advanced Encryption Standard (AES) encryption algorithm. This encryption approach offers significant advantages over traditional native encryption. It incorporates features like HSM-based Key Derivation, permissions to manage encryption keys, encryption of standard fields, support for searching (including UI, partial searches, lookups, and specific SOSL queries), and compatibility with various functionalities like Workflow Rules, Workflow Field Updates, Approval Process Entry Criteria, and Approval Step Criteria.
Why do I need Salesforce Shield?
Use Salesforce Shield if you need an advanced native event monitoring and platform encryption solution, field audit trail tool, and regular scans of your Salesforce orgs. Together or separateдy, these solutions companies allow organizations to achieve advanced data security, compliance, governance, and transparency.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...

