Spin vs Microsoft Apps Risk Assessment
- Benefits of third-party cloud SaaS applications
- Why do cloud SaaS apps add risk to the environment?
- What is Microsoft Defender for Cloud Apps?
- How does Microsoft Defender for Cloud Apps work?
- What are the shortcomings of Microsoft Defender for Cloud Apps Risk Assessments?
- Spin SaaS Application Security
- Spin vs. Microsoft Apps Risk Assessment
- Wrapping Up
More than ever, organizations are using cloud Software-as-a-Service (SaaS) environments and leveraging third-party SaaS apps. Third-party cloud SaaS apps are a tremendous value-add to the existing functionality provided by cloud SaaS vendors. In addition, they allow organizations to extend and augment the native functionality found in the cloud. However, cloud SaaS apps can add cybersecurity risk to the environment. Microsoft Apps risk assessment is part of the functionality of Microsoft Cloud App Security, now rebranded as Microsoft Defender for Cloud Apps. So what is Microsoft Defender for Cloud Apps, and what risk assessment capabilities does it offer?
Benefits of third-party cloud SaaS applications
The Microsoft 365 AppSource marketplace is chocked full of third-party cloud SaaS applications that provide tremendous capabilities to extend the native functionality found in Microsoft 365. If you navigate the Microsoft 365 AppSource site, you will see thousands of searchable third-party cloud SaaS applications in many categories.
It provides an excellent option for businesses who may find functionality or features missing in the native Microsoft 365 offering. Often a third-party vendor provides functionality or capabilities that businesses or certain department groups may need. In addition, organizations may already use third-party vendors with traditional on-premises software for specific tasks or capabilities.
Companies will likely find the same vendor provides a cloud SaaS version of their software to integrate with the Microsoft 365 environment. Using the same vendor solution in the cloud helps to maintain similar processes and familiarity with technologies that may already be used on-premises, among other benefits.
Why do cloud SaaS apps add risk to the environment?
As we have described the benefits of third-party cloud SaaS applications, why do cloud SaaS apps add risk to the environment? There are many reasons that organizations today need to be careful with cloud SaaS apps in the environment. These include:
- Malicious apps
- Data leaks
- Shadow IT
Malicious apps
Malicious apps are one of the primary reasons businesses need to scrutinize the third-party cloud SaaS applications integrated into the environment. Unfortunately, attackers often masquerade malicious apps as legitimate applications to persuade users to install them.
Using a phishing email, an attacker may prompt the user to install a legitimate “security update” or other “upgrade” to the cloud SaaS environment. The malicious app then prompts the user to grant OAuth authorization to the app. Once granted, the malicious app generally has all the access it needs to begin carrying out malicious activities.
By default, users in Microsoft 365 can install any cloud SaaS app, allowing attackers to capitalize on the scenario mentioned. Additionally, malicious browser plugins can also instantiate themselves in the cloud SaaS environment using the same OAuth compromise.
Data leaks
Another cybersecurity concern with cloud SaaS apps is data leaks. Data leaks happen when users or applications share or communicate business-critical or sensitive data with external users in an unsanctioned or unapproved way. For example, an unknown third-party cloud SaaS application may exfiltrate, store, or communicate sensitive data out of the cloud SaaS environment.
Even legitimate, non-malicious cloud apps can communicate or store data in a way that leads to data leaks. Therefore, it emphasizes the need for businesses to perform a risk assessment on any cloud SaaS app granted access to the cloud SaaS environment to ensure the way the app stores, communicates and interacts with sensitive data aligns with the security and compliance requirements of the organization.
Shadow IT
Shadow IT is any cloud application used by an end-user to perform work-related tasks without the knowledge or approval of the in-house IT team. It is a growing problem with the easy availability of cloud SaaS apps.
Note the following statistics:
- One-third of Fortune 1000 employees share and upload corporate data on third-party apps
- One in four employees links to cloud apps, including personal ones, using corporate logins and passwords
- 83 percent of corporate employees engage in informal Shadow IT practices
Each business group or department may find they need a tool to perform a specific operation in their everyday workflow. Cloud SaaS marketplaces make it extremely easy to become involved with Shadow IT, even inadvertently. A user must plug in a credit card number and install the cloud SaaS app without knowledge or interaction with IT.
Wrapping up, organizations need proper Microsoft risk management tools and practices to tackle these threats. That’s when Defender for Cloud Apps is necessary. But is it enough?
What is Microsoft Defender for Cloud Apps?
The Microsoft Defender for Cloud Apps solution is a Cloud Access Security Broker (CASB) supporting many capabilities, including log collection, API connectors, and reverse proxy. It provides customers visibility, control over data travel, and analytics data to identify and defend against cyberthreats across all your Microsoft and third-party cloud services. It integrates with Microsoft solutions and is designed with security professionals in mind. It is relatively easy to deploy and provides centralized management and automation capabilities.
How does Microsoft Defender for Cloud Apps work?
Microsoft Defender for Cloud Apps is a solution from Microsoft to help analyze your traffic logs against Microsoft Defender for Cloud Apps cloud app catalog. It examines some 25,000 cloud apps. These are ranked and scored based on several criteria, including 80 risk factors. These risk factors help to provide visibility into cloud use, Shadow IT, and the risks that Shadow IT operations pose to your organization.
It is kept up-to-date using the following processes as part of the solution:
- Data extraction from the cloud app – The extraction is for attributes such as SOC 2 compliance, terms of service, sign-in URL, privacy policy, and HQ location
- Advanced data extraction for data by the Defender for Cloud Apps algorithms – For attributes such as HTTP security headers
- Defender for Cloud Apps cloud analyst team provides continuous analysis – For attributes such as encryption at rest
- Revisions requested by customers – These are based on customer submission requests for changes to the Cloud app catalog. The Microsoft cloud analyst team reviews all requests and updates based on their findings.
What are the shortcomings of Microsoft Defender for Cloud Apps Risk Assessments?
In looking at the Microsoft Defender for Cloud Apps Risk Assessment capabilities, there are a few downsides to note with the solution. These include:
- The same risk for different app permissions
- Limited app catalog
- A proprietary scoring system
- No app scoring history
1. The same risk for different app permissions
The Microsoft Defender for Cloud Apps Risk Assessments performs a general assessment for every single app in a general way that does not consider the specific needs of each organization. For example, a cloud SaaS application may request different permissions for different clients. It may be due to different levels of functionality requested from one customer to another. Differing levels of permissions requested should logically result in different risk scores. However, despite different permissions requested, Microsoft provides the same score for the same cloud SaaS app.
2. Limited app catalog
The Microsoft Defender for Cloud Apps catalog is limited. The Microsoft Apps risk assessment works on the concept of validated apps. Therefore, it can only determine the risk of previously validated cloud SaaS apps. This limitation is less than ideal. Since new cloud SaaS apps are introduced daily, the cloud SaaS app will likely not be found in the Microsoft Apps Security directory.
3. A proprietary scoring system
Microsoft uses its own built-in app risk scoring system that weighs different coefficients and scoring based on its customer base. While this is not a negative in the true sense, it is worth noting. Companies looking for cloud SaaS app risk assessment solutions need to be aware of the differences in the risk assessment scoring metrics and look for a solution that aligns with their business requirements.
4. No app scoring history
With the Microsoft Defender for Cloud Apps risk assessment scoring system, Microsoft does not show the history of scoring changes in their assessment during the app’s lifecycle. When changes are made, the score may be changed. However, you won’t be able to see the history of changes in the scoring system. For auditing, documentation, and security purposes, seeing how risk assessments and scoring change over time can be beneficial.
Spin SaaS Application Security
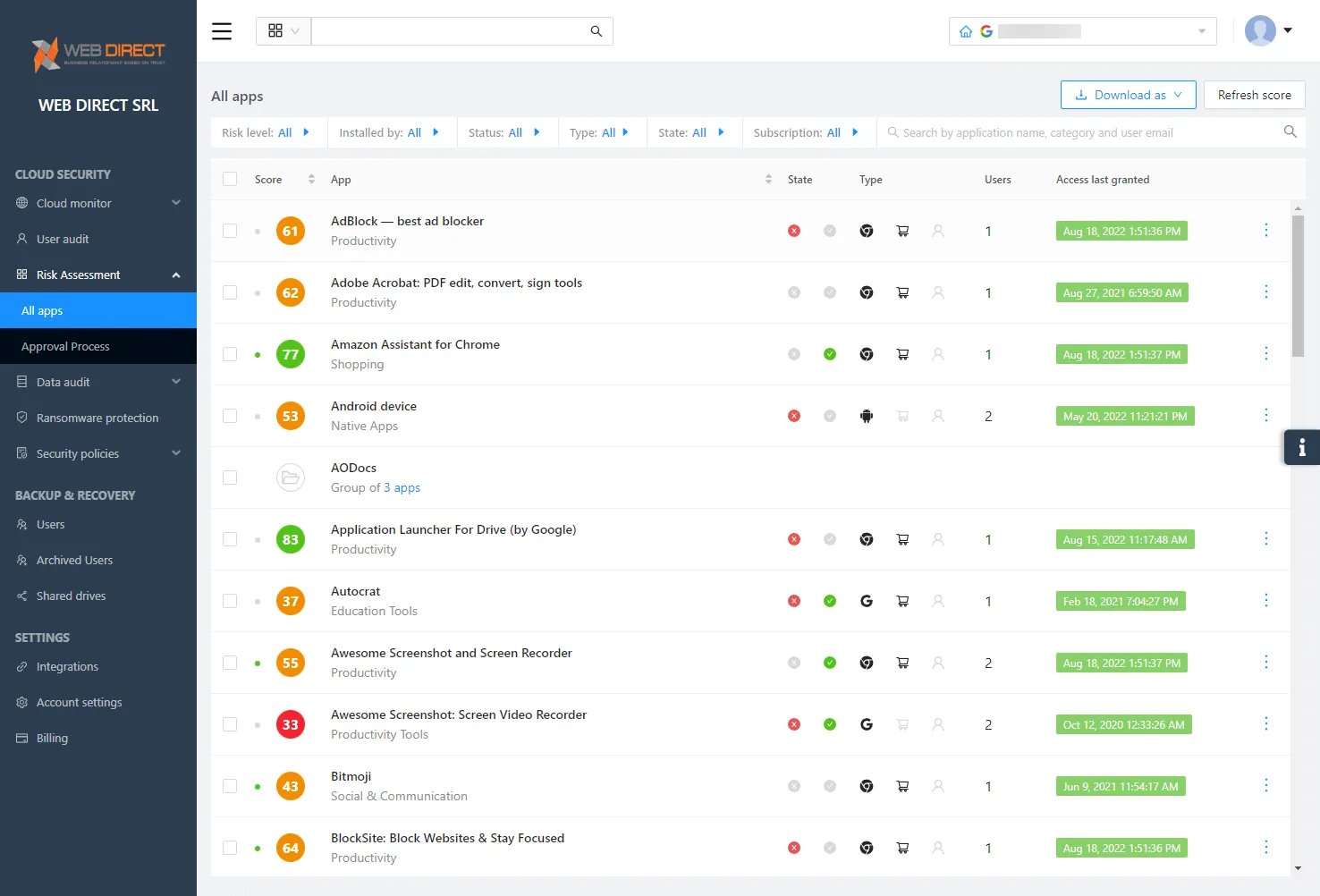
SpinOne is a next-generation cybersecurity and data protection solution allowing organizations to protect their business-critical data located in cloud SaaS environments. It uses artificial intelligence (AI) and machine learning (ML) to protect cloud SaaS environments from modern threats such as ransomware, data leaks, insider threats, and malicious third-party applications. In addition, Spin provides an automated risk assessment for thousands of cloud SaaS applications.
The Spin SaaS Application Security platform provides 24/7 monitoring, assessment, and control of OAuth applications. In addition, it allows admins to revoke functionality and access for specific cloud SaaS applications. Note the following features:
- Application monitoring – With Spin, organizations have instant visibility, monitoring, and risk assessment of cloud SaaS applications with OAuth access
- Access management – Spin gives admins the easy ability to revoke application access in just a few clicks. They can also manage allow lists and block lists for specific applications in the SaaS environment.
- Security policies – Access management for cloud SaaS apps can be automated using security policies in a granular way
- Zero-day mitigation – Spin helps organizations mitigate the risk of zero-day vulnerabilities by allowing complete control over applications installed in the SaaS environment
- Compliance – Spin allows organizations to bolster their compliance posture by only allowing authorized apps that comply with local laws, regulations, and data sovereignty stipulations
- Transparency – Get detailed information about SaaS applications and which employees are using them in the environment
- Integrations – You can integrate Spin with powerful SIEM, monitoring, and notification solutions like Splunk and Slack to receive real-time alerts of unauthorized SaaS app installations and breaches
- Alerts & reports – Receive critical security alerts and summaries. Admins can be notified of app score changes, updates, and additional information
Spin vs. Microsoft Apps Risk Assessment
How does SpinOne’s solution compare with the Microsoft Apps Risk Assessment? Note how Spin compares with Microsoft Defender for Cloud Apps risk assessment solution in the abovementioned limitations.
- Spin considers different app permissions with its risk assessment
- Spin runs a risk assessment on any app or browser extension
- An effective scoring system
- Spin tracks scoring history for cloud SaaS apps
1. Spin considers different app permissions with its risk assessment
As mentioned, the Microsoft risk assessment does not consider that cloud SaaS applications may request different permissions for different clients. As a result, it provides the same risk assessment score regardless of the app permissions requested.
The automated risk assessment provided by Spin.AI considers the app permissions requested as part of the risk assessment score. This approach is more logical and customized for the risk each organization may experience since different risk levels would result in higher or lower level permissions requested by a cloud SaaS application. Spin displays different scores for the same app based on the permissions requested.
Enhance your Risky Apps Assessment with SpinOne
2. Spin runs a risk assessment on any app or browser extension
Unlike Microsoft’s risk assessment solution that scans based on its directory of validated apps, Spin’s risk assessment runs for ANY cloud SaaS app or browser extension that connects to your SaaS data. This approach helps to protect your business-critical data from newly released or integrated applications that may not appear on Microsoft’s catalog of cloud SaaS applications.
3. An effective scoring system
Microsoft and Spin use their own built-in weighting coefficients and scoring system built on their own customer base, which is different. Therefore risk estimates may differ. It doesn’t mean either scoring system is inaccurate. Each company has to test out the risk assessment scoring system of both Microsoft and Spin and identify which one is a better fit. However, as mentioned, Spin’s approach does include advantages from a cybersecurity risk assessment perspective.
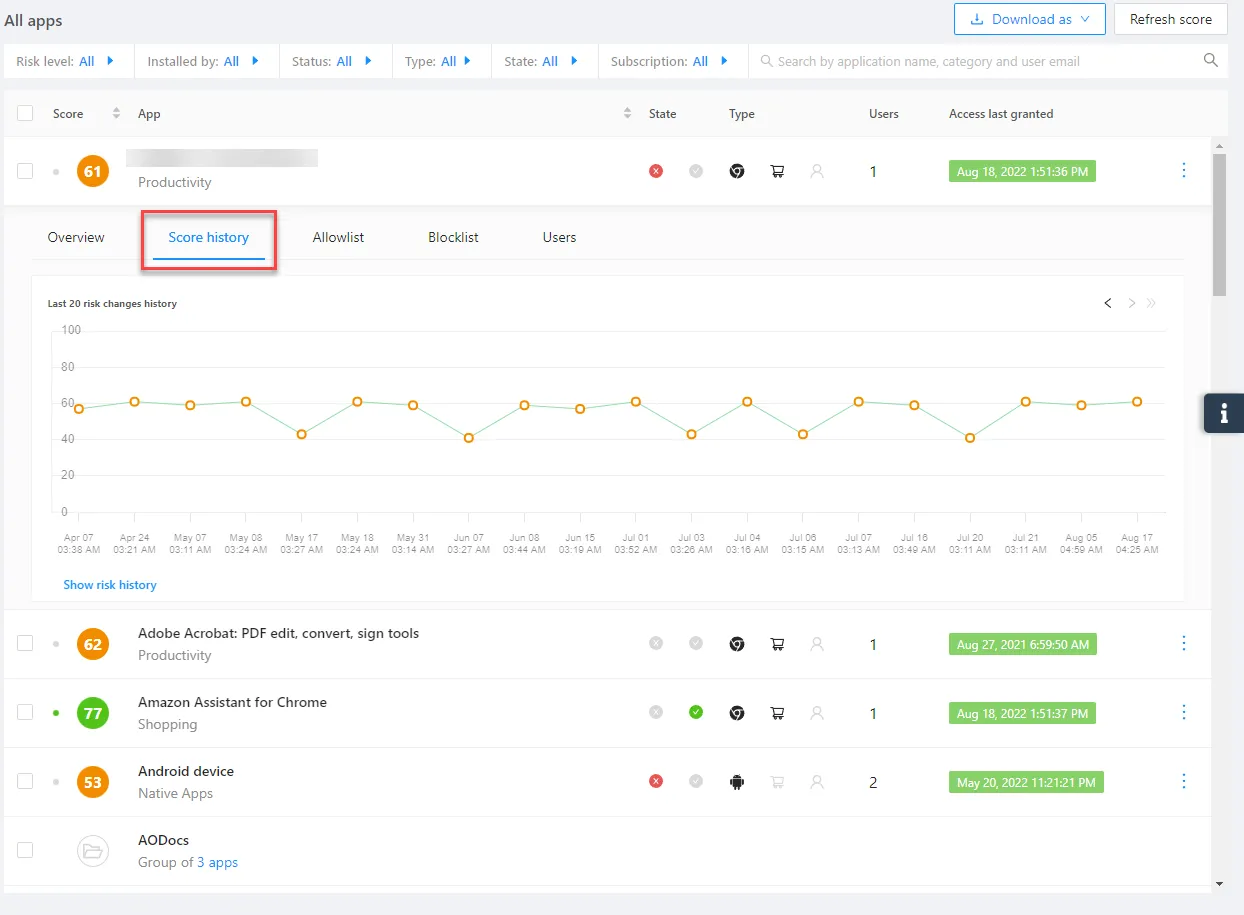
4. Spin tracks scoring history for cloud SaaS apps
Unlike Microsoft, which does not show the history of scoring changes in their assessment during the lifecycle of cloud SaaS apps, Spin’s automated cloud SaaS risk assessment solution tracks scoring history as long as the customer pays for the account. It means customers have a better picture of how risk posture for specific apps has changed over time.
Wrapping Up
Cloud SaaS applications are a great way for organizations to extend the features and capabilities of their cloud SaaS applications. However, third-party cloud SaaS applications can introduce tremendous security risks in the SaaS environment without proper visibility, risk assessments, and control over which apps can be installed and used.
The new Microsoft Defender for Cloud Apps solution enables businesses to have risk assessments in their cloud SaaS environments with a few limitations. The SpinOne Risk Assessment solution provides superior capabilities for assessing risk across the cloud SaaS ecosystem, not just for specific apps but for all applications and browser extensions installed in the environment. The automated risk assessment helps organizations improve their security and compliance posture in their cloud SaaS environment.
Learn more about Spin’s SaaS Risk Assessment capabilities here: Shadow IT – Tackling SaaS Security Risks with SpinOne
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...


