How Malicious Browser Extensions Steal Your Data and Security Risks
Many organizations are now focused on using cloud SaaS environments for many different things, including collaboration, communication, and productivity. With that being the case, most of these solutions are accessed using a web browser. Browser extensions are commonly used to help enhance productivity and add capabilities and integrations right into the web browser. Many of these browser extensions bring along security risks that can lead to security concerns and even data leaks. Let’s see how they can steal your data and how organizations can protect themselves and their users from these risks.
The dangers of browser extensions
When browser extensions are used for legitimate purposes and are from trusted developers and solutions, they can help with extra capabilities and productivity. However, they can also be a back door for malware or a conduit for an attacker to exfiltrate data.
When extensions are connected to your cloud SaaS environment, these often need high-level permissions in the environment to work properly. At the very least, browser extensions may be able to access your browsing history. However, others can access personal information and may even require extensive permissions over your cloud SaaS data.
How Browser Extensions can steal your data
When it comes down to it, browser extensions can access any data that passes through your web browser. This is a bit unnerving when you think about the information that may flow through your browser. It includes sensitive information like login credentials, tokens, personal identifiers, and even financial information if you are browsing banking websites, etc.
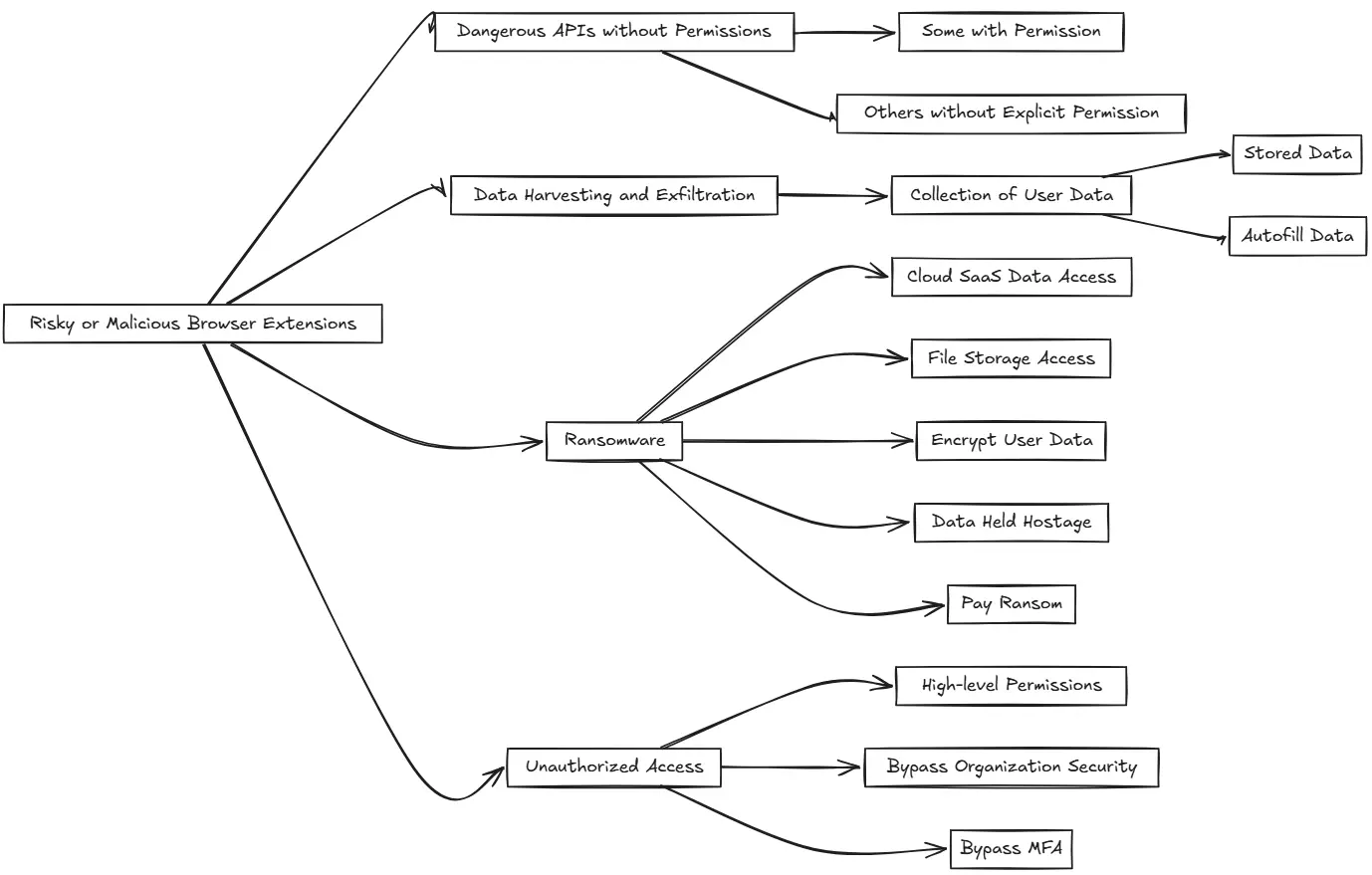
How can risky or malicious browser extensions be used to compromise sensitive data? Note the following points to consider:
- Use of dangerous APIs without permissions – There are tons of APIs and permissions that web extensions can access, some with your permission and others without explicit permissions needed. It is concerning to note that extensions with just a simple permissions popup are allowed to do things like take screen captures, log keystrokes, act as a “man in the middle” to web inputs, and many other dangerous things.
- Data harvesting and exfiltration: Malicious extensions can collect a large amount of user data. This data may include browser habits and history, saved passwords you may have stored, and autofill data, which can also contain lots of sensitive personal information. Attackers can sell this on the dark web or use it in other types of attacks, including phishing.
- Ransomware: Some extensions can carry out ransomware attacks. Since cloud SaaS data like file storage can be accessed through your browser, a malicious extension could encrypt all the data the user has access to and then hold the data hostage until the ransom is paid.
- Unauthorized Access: Extensions with high-level permissions can often bypass security measures an organization may have in place, like multi-factor authentication (MFA). Browser extensions may cache a token that gives it long-term access to the environment and does not initiate the MFA prompt.
The Spin.AI browser risk report
Spin.AI has created a great resource for the community, the Browser Risk Report. It provides a look at the dangers of using certain browser extensions. It provides detailed insights into how Spin.AI evaluates extension risks, focusing on factors such as data access permissions, developer reputation, and compliance with security standards.
It uses Spin.AI’s database of apps, which, at this point, currently numbers over 400,000 apps and browser extensions. With the insights provided, organizations can use it to have visibility to risks in their environments and why certain apps may be deemed as risky.
New App and Extension Risk Assessment
Along with the browser extension risk report, Spin.AI has released a new tool for assessing and managing risks, the new App and Extension Risk Assessment. This tool is designed to give you quick and complete insights into the security and compliance risks of any SaaS app or browser extension.
Note the following features of the App and Extension Risk Assessment:
- AI Driven Assessment: The Spin.AI app risk assessment tool uses machine learning algorithms for risk assessment. These modern algorithms help to make sure the tool is accurate and discovers risks before manual risk assessments. By using the tool, you have access to over 400,000 apps and extensions that have already been assessed and cataloged by Spin.
- Access Risk Scores: When you enter the name of an app or extension, you will get an instant score of the app which is based on Spin.AI’s extensive database. The risk score includes the threats that the app or extension may bring to your SaaS data.
- Risk Assessments: It assesses many factors related to risk assessments. These include permissions requested, the reputation of the developer, the history of vulnerabilities, and compliance with leading security standards.
- Compliance: If you are concerned with compliance regulations like GDPR, HIPAA, or CCPA, the risk assessment tool also provides a separate compliance risk score. The compliance score helps you understand how well an app or extension aligns with key data protection regulations and certifications, including ones like ISO 27001 and SOC 2.
- Free to use: The tool is free to use, and you don’t even have to register to use it. All you have to do is simply enter the name of the app or extension and get your risk report in seconds. This helps you conduct quick and frequent assessments, which helps to bolster your security stance in protecting your SaaS environment from modern threats.
The App and Extension Risk Assessment tool, helps to make sure you are less vulnerable to things like ransomware attacks, data exfiltration, and unauthorized access when using SaaS apps in your cloud environments like Google Workspace, Microsoft 365, Salesforce or Slack. Identifying risky apps and browser extensions as early as possible enables you to take proactive measures to protect your data.
Risk assessments are vital
Hybrid work and cloud SaaS environments are here to stay. This means that the risks to businesses are higher than ever. These risks include unauthorized access to data, ransomware attacks, data leaks, and data breaches for businesses that are not prepared. The consequences are also more severe than ever before, with companies that fall victim to one of these attacks suffering devastating financial consequences and damaged customer confidence.
Consider the following scenarios that can lead to disaster:
- Ransomware: Ransomware is becoming all too common. If you can imagine a scenario where an employee downloads and installs a malicious SaaS app or browser extension. The app or extension starts encrypting the organization’s SaaS data, leading to data being held hostage by attackers. The financial and reputational damage could be catastrophic.
- Data leaks: Do you have visibility into any apps or browser extensions in your environment that could be stealing your data? By default, employees in most cloud SaaS environments can download and integrate any app or browser extension into the environment. These can include apps or extensions that are risky and that leak data to unauthorized users. This could be disastrous.
- Compliance: You need to make sure apps and extensions in your environment are in compliance with regulations such as HIPAA, GDPR, or CCPA. What if employees download apps that are out of compliance with regulatory demands? This can lead to fines, legal action, and other consequences.
Spin.AI’s Risk Assessment provides an app risk score and compliance risk score, which helps you decide which apps and extensions meet the standards needed by your organization.
Wrapping up
There are many advantages to using cloud SaaS apps and browser extensions that can enhance your productivity workflows and even add features and capabilities to the environment. However, the risks of using third-party apps are real and cannot be ignored.
Spin has released many great resources for use, including the new App and Extension Risk Assessment. All you have to do is enter the name of the app or extension, and in just a couple of seconds, Spin.AI will let you know the risks associated with the app. This allows organizations to be proactive and secure their environments to protect from potential threats.If you are interested in seeing how SpinOne can help prevent data leaks and breaches in your organization, sign up for a free demo here: https://spin.ai/demo.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...

