Third-Party Applications Audit: Complete Guide
SaaS applications offer users contemporary productivity, communication, and collaboration tools, irrespective of their location. This adaptability has enhanced efficiency, expediting organizations’ transition to the cloud globally. The proliferation of SaaS applications in businesses underscores this shift. Yet, a rapid and often uncontrolled installation of third-party apps may put SaaS data at risk. Attackers can abuse applications with high permissions by deleting, encrypting, leaking, or changing SaaS data.
The top security concerns when adopting SaaS applications are identity and access governance (43%), SaaS misconfiguration (40%), and 3rd party app access and their level of permissions (14%). Understanding which one threatens your company the most is a difficult task. One of the best ways to understand and address top concerns associated with your third-party apps is by conducting a third-party security audit.
Spin.ai offers one of the best third-party application audit tools. It ensures a thorough Google apps auditing and provides Google Workspace (formerly G Suite) admins with a visual report to monitor the enterprise security of third-party apps accessing company data in Google Workspace. Such visibility into the company’s data and systems allows a Google Workspace administrator to easily identify security risks, gain insights into potential vulnerabilities, while at the app level, they can take specific actions to remove the risks and prevent them from becoming significant problems.
Let’s dive deeper into the third-party apps security landscape and learn how regular third-party security audits may help enhance your overall security posture.
Security Risks Associates with Third-Party AppsUsing third-party apps with Google Workspace can be very useful. Apps offer some advanced features, significantly extending cloud functionality and cloud productivity, but they can also introduce a new kind of security risk into your organization. Particularly, third-party apps have the potential to reduce the security level of your Google Workspace cloud storage and apps because:
- Third-party apps may obtain excessive permissions to Google Workspace services;
- They can access data stored within Google Workspace;
- Once given access, they retain this level of authority until it is manually revoked.
It may be helpful to consider every third-party app in the same way as a new employee within your organization. Just as an employee can cause a breach in the corporate data, so can insecure apps that have access to this data.As with any employee, it is important to think about the level of access that they have to corporate data and software. You would definitely not give all your employees full-level access to corporate information and the same should be true of any apps that are installed.
Shadow SaaS
A recent report by the Ponemon Institute reveals that a staggering 88% of organizations use more than 2,500 cloud applications. Having full control over such an amount of applications is hardly possible. Specifically, CSA’s State of SaaS Security: 2023 Survey Report revealed that over half (58%) of organizations estimate their current SaaS security solutions only cover 50% or less of their SaaS applications.
Overreliance on SaaS applications leads to the proliferation of “Shadow SaaS” with employees having the freedom to leverage any tool to get their work done, irrespective of the organization’s IT policies and authorization. The proliferation of Shadow SaaS leads to the lack of visibility or control by the organization creating significant organizational challenges.
Risky Permissions and Vulnerabilities
One of the main problems with third-party apps is that while any employee can easily install t hem onto his or her own devices, their level of access to sensitive data and systems can be hardly controlled. Every third-party app requests specific permissions when connecting to SaaS. Most users do not pay much attention to these permission requests and will click the button to grant permissions without a second thought.
Spin.ai 2023 SaaS Application Risk Report categorizes these permissions as low, medium, and high risk, based on the types of permissions being requested by the application. Specifically, the report shows that risky applications are far more common than they may appear to be. On average, a surprising 35% of apps with OAuth permissions to Google Workspace or Microsoft 365 are classified as high risk, 44% pose medium, and 24,% are classified as low-risk apps. Many applications with high permission scopes are able to read, update, create, and delete content. Applications frequently receive full mailbox access permissions, enabling them to send emails on behalf of the user. For example, 43% of applications have access to read, see, edit, compose, send, and permanently delete all user email from Gmail.
For example, an employee working at a company with a BYOD (bring your own device) policy may use his iPhone to regularly access emails and documents via Gmail and Google Drive. The employee may then install a 3rd-party app onto his phone that requests permission to access his Google account during the installation process.
It is important to note that many of the riskiest third-party apps are games and applications that have nothing to do with work. For example, earlier versions of the popular Pokémon Go game requested full access to the user’s Google account.
Even though many third-party apps are installed via the official iTunes and Google Play stores, they may well have software vulnerabilities that could be taken advantage of by hackers, even several years after the software is originally installed. Neither Google, nor any other cloud platform cannot guarantee the safety of any third-party applications and all are installed at the user’s own risk.
This creates a significant risk of data loss or leakage that could impact your entire organization. To address this concern, Spin.ai has introduced the Risky Third-Party Applications Audit feature, aimed at helping you prevent or mitigate these risks.
Protecting against Insecure Third-Party Apps
1. Provide Employee Security Training
Employees are often not aware that third-party apps they install could cause a serious risk to corporate data and systems. Providing detailed security training for all employees, and explaining the risks associated with 3rd-party apps and how they can compromise corporate data, should be the core for combating insecure third-party apps for any company. In 2023, 68% of organizations have drastically increased their investment in training staff on SaaS security, underlining the importance of human capital in safeguarding their SaaS ecosystems.
Training is particularly important for senior and management-level staff, who are likely to have accounts with access to sensitive corporate data. Employees at this level often assume that computer security is dealt with by the IT department and do not realize they have a personal responsibility to help ensure company data is not compromised.
2. Implement a Robust Security Policy. Your corporate security policy should include clear guidelines for employees at all levels in regards to using personal devices at work, installing 3rd-party apps, permissions that may or may not be granted, and the type of data that is allowed to be accessed or downloaded onto personal devices or 3rd-party backup and storage solutions. Unfortunately, setting up a robust security policy is among the top (32%) operational security headaches surpassed by the lack of skilled staff (43%), ensuring compliance (37%), and visibility into their infrastructure security (32%). Thus, organizations must spend more time and resources on setting up and communicating proper security policies regarding third-party cloud app usage.
At the same time, there is a promising trend for increased reliance on the right security tools focused on SaaS security. According to the Ponemon Institute survey, 71% of organizations have increased their investment in security tools for SaaS, demonstrating a growing commitment to protecting their digital assets. Moreover, 66% of companies have raised their investment in essential SaaS applications, underscoring the increasing dependence on these platforms for fundamental business operations.
3. Run Regular Third-Party Security Audits
The best way to deal with any potential security problems that may occur via 3rd-party apps is to develop an awareness of the apps that are installed and being used by employees on a daily basis. Using SpinOne cybersecurity service with third-party application audit allows administrators to easily monitor apps that have access to corporate data and quickly disable apps that may cause a security threat.
How Spinbackup Third-Party Applications Audit Works
Google apps auditing runs a daily automated scan of all apps installed by users within the organization. As a result, it produces a report, listing all the apps with an at-a-glance color-coded view of their level of risk.
Google Workspace Administrators have the option either to block apps directly from this screen or can click through to see a more detailed report for each individual app. The report includes:
- The risk level of the app and a detailed description of possible risks (assessed by Spinbackup’s own criteria);
- The type and description of the app;
- Employees having access to;
- List of permissions granted to the app.
Each application is rated based on its level of authority and any potential security risks are listed in more detail. Google Workspace Administrators then have the option to mark the app as trusted or to remove access for all users within the organization.
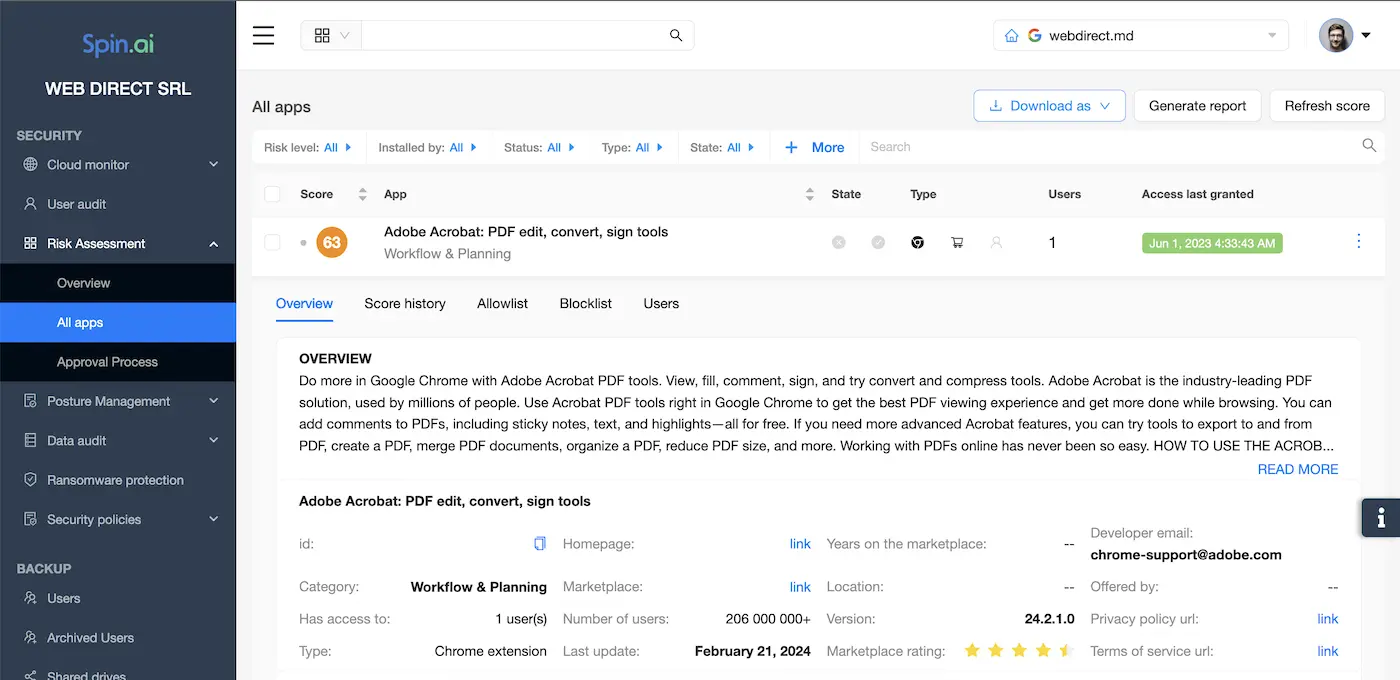
In addition to the daily scan, the app audit can be run manually at any time.
Along with providing a quick and easy way to block risky apps, the third-party apps audit also enables Google Workspace administrators to monitor apps that have access to corporate data and discover immediately if there have been any violations of data access or company policy (for example, downloading data to a private account).
Google apps auditing now also has a new “auto-remove” feature for blacklisting apps, reinforcing robust security measures. When Spinbackup detects the installation or authorization of a third-party app, it automatically checks it against the blacklist. If the app is found in the blacklist, Spinbackup removes the permissions associated with it. The Spinbackup third-party apps daily audit has discovered over 300,000 apps to date via our smart algorithms and our analytic department. This has helped Google Workspace administrators save a tremendous amount of time that would normally be spent analyzing each application separately. You can request a demo of Spinbackup cloud-to-cloud backup and Google Workspace security, including the 3rd-party apps audit, and try it out for yourself.
Frequently Asked Questions
How do I manage third-party apps in Google Workspace?
You have two options for managing your third-party apps in Google Workforce.
First, you can review the access a third party has to your Google Account and the Google services you use on your own. To do this:
- sign in to your Google Account;
- view the apps & services that have access to your Google Account;
- Select the app or service you want to review.
If you no longer trust a third-party app or service, you can remove its access to your Google Account.
Second, you can use a Spinbackup for Business for Google Workspace – automated solutions to conduct a third-party applications audit on a daily basis listing all the apps with an at-a-glance color-coded view of their level of risk.
What is a solution for third-party application audit?
The Spinbackup for Business for Google Workspace is an automated solution for conducting a third-party application audit that runs a daily automated scan of all application users installed within the organization and produces a report, listing all the apps that may pose a threat.
After the audit, G Suite Administrators can either block apps directly from the screen or click through to see a more detailed report for each app.
Why conduct a third-party application audit?
A third-party application audit allows monitoring apps that have access to corporate data and quickly disabling apps that may cause a security threat.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...
Data Loss Prevention Techniques for 2025 and Beyond
It’s painstakingly clear that data loss is a major challenge facing businesses today. Our experts...
What is SaaS Security? Challenges & Best Practices
Businesses increasingly rely on Software as a Service (SaaS) for increased efficiency, collaborativeness, and scalability....


