Top 5 Industries Most Targeted by Ransomware Attacks in 2024
If you could name a single threat that targets all businesses today, what would it be? There is a security threat to businesses that do not discriminate. It can affect literally all organizations across all industries. It is ransomware. These days, ransomware gangs don’t leave any organization unthreatened. We will see the top 5 industries for ransomware attacks and how businesses can protect themselves.
1. Government
Government agencies topped the list of ransomware attacks so far in 2024. They may be the victim of a Nation State attack, or be attacked simply for the large amount of sensitive data they manage and process. They also generally perform critical services for communities, cities, states, and national governments. Disruptions in this sector can also have negative impacts on public safety and even national security.
According to the statistics compiled so far this year, there have been over 280 attacks on government agencies.State and local government and federal government entities were also found to pay more than the original ransom demanded to get their data back, at 104% and 103% respectively.
Ransom payments:
- Mean: $7.4M
- Median: $6.6M
Recent Attacks:
- City of Flint (USA): On August 14, 2024, the City of Flint in Michigan suffered a major ransomware attack that took down many critical public services. The services affected included the water management systems and emergency services. Officials struggled to bring essential services back online. Flint has been a high-profile target due to past issues with water contamination.
- North Miami City Hall (USA): North Miami City Hall experienced a ransomware attack on August 9, 2024, that locked down city records and systems. The cybercriminals encrypted data and were successful in keeping the city government from functioning effectively. Residents experienced delays in getting essential services that included permits and licenses.
2. Healthcare
Healthcare still tops the list of the costliest industries for breaches due to a cyber attack. According to the IBM Cost of a Data Breach report in 2024, it is still the costliest industry for a data breach and interestingly it has held this spot since 2011.
Healthcare organizations have seen over 240 attacks so far in 2024 and also have one of the highest percentages of paying a higher ransom than originally demanded (paying 111% of the original demand). It is also one of only five business sectors that reported an increase in attack rate, from 60% to 67%. One report notes that healthcare will spend $125 billion annually from 2020 to 2025 to defend against cyber breaches.
Why are healthcare organizations such a popular target for ransomware attacks? For one thing, healthcare organizations hold very sensitive types of data and personal information of millions of individuals. These types of information are very valuable on the dark web.
Also, many healthcare organizations are still using legacy systems as part of their core infrastructure that have vulnerabilities or can’t be patched. Disrupted operations in health care leads to real-life consequences, sometimes life threatening consequences. Ransomware gangs use all of these factors to their advantage to help ensure ransoms will be paid.
Ransom payments:
- Mean: $4.4M
- Median: $1.5M
Recent Attacks:
- Access Sports Medicine & Orthopedics (USA): Access Sports Medicine & Orthopedics in New Hampshire U.S.A was hit with a ransomware attack. The attack on critical systems impacted more than 88,000 patients. Also, attackers were able to encrypt and access sensitive information that contained medical records, billing statements, and insurance data.
- Planned Parenthood (USA): Planned Parenthood’s Montana branch was hit by a ransomware attack on August 28, 2024. The attackers threatened double extortion as they would release confidential patient data if the ransom was not paid. The attack disrupted services and also led to privacy concerns for thousands of patients.

3. Education
The education sector is very often targeted by ransomware gangs looking to effectively capture, steal, and encrypt data for a quick profit. Universities and public schools have seen a huge increase in attacks in 2024 among other industries.
The education sector has seen a tremendous spike in ransomware attacks. It had a staggering 70% surge in ransomware attacks in 2023 and is still a prime target of attacks in 2024 with 195 attacks tallied so far.These statistics include a 105% increase in ransomware attacks against K-12 and higher education.
Interestingly, the education sector is most likely to pay more than the original ransom demanded. In higher education, 67% paid more and was also noted as the least likely sector to pay less than the original demand (20% paid less). The education sector also has one of the highest rates of attackers being able to successfully compromise their victims’ backups at 71% success rate.
There are good reasons that education institutions are a prime target. They typically lack the cybersecurity tools and protections that are needed and they have budget constraints that make training and investment in cybersecurity difficult.
Ransom payments:
- Mean: $7.5M
- Median: $6.6M
Recent Attacks:
- Fylde Coast Academy Trust (UK): On September 18, 2024, the Fylde Coast Academy Trust was the victim of a major ransomware attack. The attack was extremely effective and affected a large quantity of data. The attack caused the shutdown of most of their IT systems across several schools. Hackers were responsible for encrypting files and then demanding a ransom for the school to regain access to their data. As you can imagine, classes and other activities were disrupted and it also caused many to have concerns about the privacy of their data and also the security of student information.
- Rurtal-Gymnasium (Germany): On September 17, 2024, the servers at two schools in Germany went offline due to ransomware. In an effort to keep the ransomware from spreading, the servers at all schools in the municipal school district were taken offline. This caused widespread issues with school IT systems and student activities.
4. Manufacturing
The manufacturing sector is an industry that is increasingly relying on technology and digital systems for business-critical operations. Industrial control systems, IoT devices, and manufacturing sensors all rely on data driven processes. Often, many of these devices have vulnerabilities and may even contain legacy software and hardware that can be easily compromised. A lack of network segmentation and other factors can lead to attackers being able to compromise these very critical environments.
Number 4 on the list, with over 160 attacks, manufacturing industries have one of the highest rates of being able to negotiate down ransom payments at 67% saying they paid less than the original demand. However, manufacturing industries have a fairly high rate of data encryption in an attack at 74%.
Ransom payments:
- Mean: $2.3M
- Median: $1.2M
Recent Attacks:
- Microchip Technology (USA): Microchip Technology company, a major semiconductor company in Arizona, was hit with a ransomware attack on August 27, 2024. The ransomware gang encrypted the company’s production and design systems. The attack caused delays in development tasks and supply chain operations. The ransom demanded was high. Even working to recover its data the financial losses were significant due to the disruptions.
- Regent Caravans (Australia): Regent Caravans, a well-known Australian caravan manufacturer, experienced a ransomware attack on August 21, 2024. The attack disrupted production activities and it also impacted their ability to process and ship orders. This resulted in a significant financial loss to the company and delayed shipments to customers.
5. Energy
Very similar to manufacturing, the energy sector is a critical sector that plays an important role in the overall national infrastructure. It makes these a very high-value target for ransomware gangs looking to disrupt these critical services for a large payout. This high-value target can be seen in the fact that the energy sector has seen 35 attacks so far this year and 67% of all ransomware attacks since 2023.
The extreme disruption these types of attacks can have can be seen in what happened on May 7, 2021 when the Colonial Pipeline was the victim of a ransomware attack. It caused widespread fuel shortages in the North Eastern United States.
Ransom payments:
- Mean: $3.2M
- Median: $2.5M
Recent Attacks:
- Arkansas City Water Plant (USA): As mentioned earlier, this energy-related facility experienced a ransomware attack on September 24, 2024. The attackers encrypted control systems and demanded a ransom to prevent potential water supply contamination. Source.
- Air-e (Brazil): Air-e, a Brazilian energy provider, fell victim to a ransomware attack that affected its electrical distribution systems on September 2, 2024. The ransomware gang demanded the company pay a ransom to decrypt their systems. By extension, this attack affected energy distribution to thousands of customers, leading to power outages and delays.
Trends looking towards 2025
Ransomware attacks are hard to predict as ransomware gangs continue to change and shift as needed to avoid detection and to cause the most damage as possible to ensure ransom payments. However, there are certain trends that we can establish looking at ransomware attack data so far in 2024.
Government, healthcare, and education will likely continue to be in the top list of targets moving into 2025 as these industries prove to be lucrative targets with high success rates for attackers. Recovery costs continue to go up as 2024 has seen an overall increase from $1.82M reported on average in 2023 to $2.73M in 2024. In 2025, this trend will likely continue as businesses more heavily rely on technology and data-driven solutions, with increasing daily operational costs.
Data theft will also continue to increase in priority for attackers moving into 2025 in addition to encryption, as this is often used in double extortion tactics and increased leverage to receive ransom payments.
Note a few other takeaways:
- Ransom demands and payments will continue to rise in 2025 as 2024 saw an increase of $400,000 from 2023
- Larger organizations will continue to be targeted (those with $5+ billion revenue) as these are consistently in the top list of attack victims and they consistently pay more in ransom payments
- The average time to recover continues to grow longer with 34% of organizations taking a month or longer to recover in 2024, which is up from 24% in 2023. Likely, this trend will continue in 2025 as attacks grow more complex and effective.
- Backups also continue to be a target of ransomware gangs as 94% or organizations saw attempts to compromise backups during an attack
Spin.AI’s Ransomware Protection Solution
Spin.AI is a modern and very sophisticated cybersecurity solution that provides protection to critical cloud SaaS environments. One of the center pieces of the solution is the ransomware protection solution. SpinRDR offers a rapid 2-hour incident response SLA for cloud ransomware attacks, drastically reducing downtime from 21 days to just 2 hours. Leveraging advanced technologies like artificial intelligence (AI) and machine learning (ML), SpinRDR detects early signs of ransomware threats to safeguard your critical data.
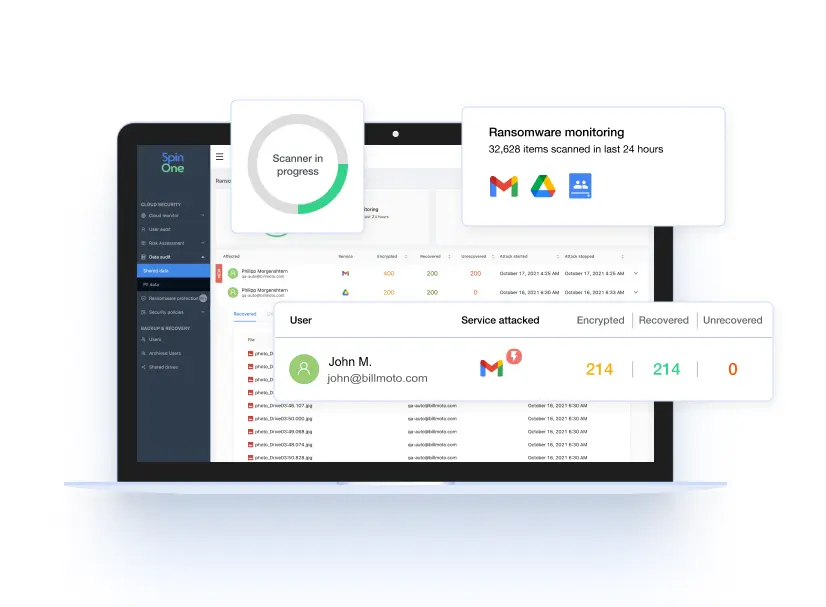
Key Features of Spin.AI’s Ransomware Protection Module:
- Real-Time Threat Detection: The Spin.AI module monitors and identifies abnormal file access in your cloud data and can quickly spot abnormal encryption activities. It can also spot anomalies like unauthorized data modifications that allow it to provide instant alerts to SecOps teams.
- Automated Response Actions: Spin.AI provides a totally automated cybersecurity response to a ransomware attack. It 1) isolates affected systems, (2) blocks further malicious activities, (3) scans all files in the cloud repository to find any affected files, (4) initiates recovery of any affected data, and (5) alerts admins of the ransomware attack and the files recovered.
- Data Encryption Detection: It helps to quickly identify encryption patterns that are likely used in ransomware attacks and initiates a strong security response to protect your vital data.
- Machine learning: Machine learning algorithms are incorporated to detect unusual behaviors and file access patterns that are typical in a ransomware attack.
- Audit Logs: Spin.AI creates detailed logs and reports of all activities that take place in the cloud tenant. It enables SecOps and admins to align cloud environments with compliance and governance requirements.
Mitigating ransomware attacks with Spin.AI
In each of the ransomware attacks that we have covered, let’s look at how the Ransomware Protection module of Spin.AI could have helped to minimize the damage in similar types of attacks. For instance, in attacks like those on the Arkansas City Water Plant and Fylde Coast Academy Trust, Spin.AI’s Real-Time Threat Detection could have helped to identify abnormal file access and encryption activities.
The automated system isolation capabilities of Spin.AI could have helped to stop the extensive damage to critical systems and data, preventing large-scale service disruptions. In an attack like the one on the Australian Health Network, Spin.AI’s Anomaly Based Monitoring would have helped detect the unusual data access activities in the financial transactions and patient record management systems and could have helped trigger proactive defenses before ransomware could fully encrypt sensitive information.
Spin.AI’s Data Encryption Detection would alert administrators about encryption activities and immediately go to work to contain the attack. Spin.AI also has granular audit logs for comprehensive data trails so SecOps and IT ops have visibility into the attack vectors used which will help with compliance audits and post-incident reporting.
Wrapping up
As ransomware attacks continue to become more sophisticated and attack businesses across all sectors, organizations are going to have to use modern tools to help secure their infrastructure, including cloud SaaS.
Each business sector has specific risks that may lend themselves to different types of security being needed. However, it is extremely important that organizations need to be proactive about cybersecurity and take the needed preventative steps to strengthen their defenses.
Spin.AI’s Ransomware Protection module provides a great layer of defense in detecting and mitigating ransomware threats in cloud SaaS. It helps businesses stay one step ahead of cybercriminals. To learn more about the latest ransomware trends and how to protect your organization, visit the Spin.AI Ransomware Tracker.Get a Free Demo to upgrade your ransomware defense strategy with SpinRDR!
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...
American Water Ransomware Attack: What Happened and How Critical In...
On October 3, 2024, American Water company was targeted by a ransomware attack that disrupted...
How Halliburton’s Ransomware Attack Highlights the Need for A...
No industry or organization is immune or safe from the possibility of falling victim to...


