Top Challenges in Securing SaaS Applications and How SSPM Can Help
Recent vulnerability exploits have caused massive data leaks in large companies and government organizations – demonstrating the importance of SaaS app control. In this article, we’ll discuss the key challenges in securing SaaS applications and how SaaS Security Posture Management tools can help.
Challenge 1: Lack of Visibility and Control
Shadow IT problems skyrocketed with the rapid adoption of cloud technologies, further fueled by OAuth technology. The number of applications used on a regular basis by a single person is steadily growing, and using one account for credentials is convenient.
The same is true for applications we use at work- some of your employees can mistakenly use their working account in Google Workspace or Microsoft 365 to access apps intended for personal use. When people stop using applications, they rarely return to disable their account and revoke any access or permissions they gave in the past. Truth be told, not all applications have such functionality.
As a result, the ever-increasing amount of applications used by your employees gain access to your sensitive business data – often without your IT knowledge.
How do you get full visibility and control over your SaaS environment?
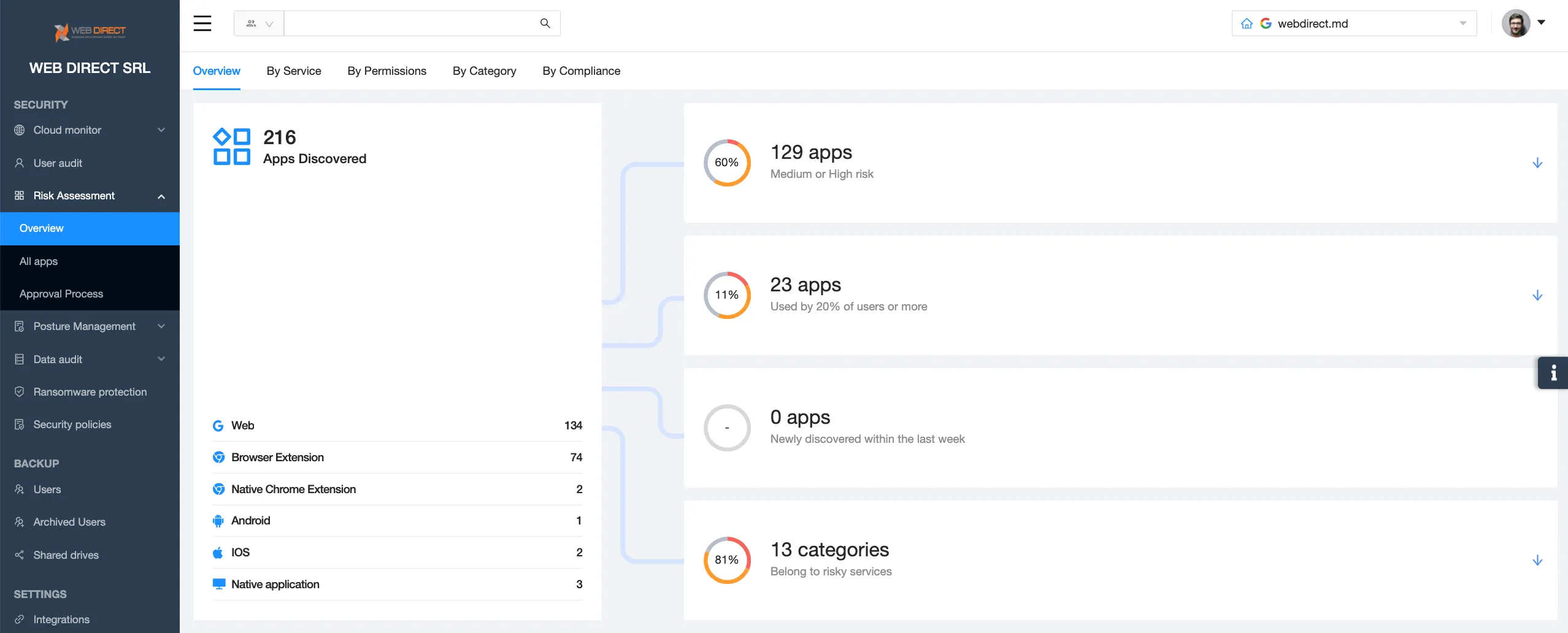
How SSPM provides visibility and centralized control over SaaS security
SSPMs work like SaaS tools. They integrate with your Google Workspace or Microsoft 365 and provide the functionality to establish control over the apps:
- detect all applications that have OAuth access to your SaaS environment
- app risk assessment to help your team understand the security risks
- allow-listing and block-listing
- revoke application access to your data
- security policy to control how users add apps in the future
- request section to automate the app approval process.
Challenge 2: Lack of Access Management
File sharing option has revolutionized the way we work, but at the same time it has opened up more opportunities for data theft. We’ve seen several major scandals around terabytes of customer or employee data that were shared with public. However, even within your organization, sharing all the data with all the employees is a slippery slope.
How SSPM helps you manage access
SSPM functionality enables you to see all the files that are improperly shared within and outside the organization. They specifically highlight those data entries that aren’t shared in keeping with your security rules.
Furthermore, these tools enable you to step in and change sharing settings to comply with the regulations and even take over certain files if you suspect foul play. Finally, they provide security policies that prevent improper sharing and notify security teams of such incidents.
Challenge 3: Misconfigurations and Vulnerabilities
Misconfigurations of SaaS environments can lead to data breaches or non-compliance. Google Workspace and Microsoft 365 have complex systems of security controls.
Meanwhile, the IT teams suffer from talent and skill gaps. They are often overwhelmed by the number of tasks they need to do and the vulnerabilities they have to address. As a result, teams can make mistakes when configuring the SaaS environment.
At the same time, new cyber threats and vulnerability exploits emerge on a regular basis. Countries change legislation, or companies decide to change the model of business, causing the need for new security measures to comply with the new rules. Keeping up with all these changes and configuring the complex environments (often, there are several SaaS tools used simultaneously) is difficult.
All these factors contribute to the mistakes in configurations that can lead to data breaches or legal fines.
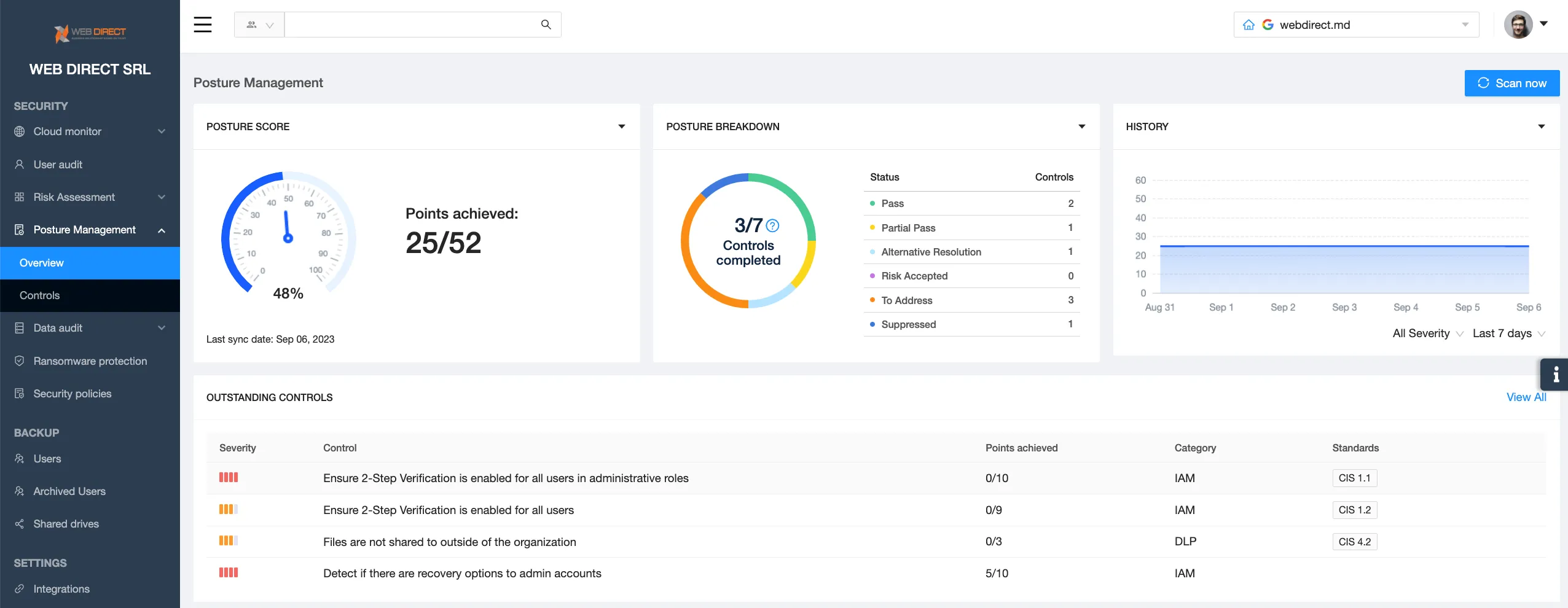
How SSPMs help businesses tackle misconfigurations
SSPMs can detect all the incorrect configurations and alert the IT security team about them. They help automate the most tedious process of checking every security control. SSPMs also have the functionality to reconfigure these settings in accordance with the company’s security policies. The 24/7 monitoring is great, especially in case of a man-in-the-middle attack.
Challenge 4: Insider Threats and User Behavior Monitoring
Users make errors. And it’s one of the key problems when it comes to the security of SaaS applications. Accidental deletion of critical information or falling victim to a social engineering attack are the most common human errors. These mistakes can be solved with a good backup or ransomware protection tool.
However, there are other problems. Let’s say a person disregards security policies on a regular basis. Or an account has been hijacked, and the hacker is now trying to copy all the data they can lay their hands on. Without SSPM, your IT security team is blind and helpless against such incidents.
How SSPMs help you tackle insider threats
SSPMs collect the logs of events within Google Workspace or Microsoft 365 environment. Then IT security can filter these logs to get certain information into the spotlight. They can pick just one user and see the risky actions this user has been doing, for example, mass downloads or improper sharing.
With this information, the IT Security team can initiate an investigation against the user to understand whether they are trying to damage the company or they are just very reluctant to comply with security rules.
Wrapping up, SSPMs help you tackle the main security challenges in SaaS environments. They automate many mundane tasks that would otherwise overload your team. Moreover, they provide the functionality that can help you take the security vulnerabilities under your control and take other timely actions necessary to secure your SaaS environment.
FAQs
Are there any real-world use cases that demonstrate how SSPM addresses security challenges in SaaS applications?
There are. However, companies aren’t that willing to share their experience with the public. If you want to see if SSPM really works, you can try our free App Risk Assessment. Our platform SpinOne will reveal all the apps that have access to your data and evaluate their risk.
How can SSPM help in safeguarding sensitive data and ensuring regulatory compliance?
There are several ways SSPM can help safeguard sensitive data. First, it detects access to this data by unauthorized users. Second, it finds and reports anomalies in data behavior. Third, it provides security policies to prevent unauthorized access and other security incidents. As concerns regulatory compliance, SSPM can detect misconfigurations and report them to your team.
How can the lack of visibility and control over multiple SaaS applications be addressed?
Using SSPM can help you get visibility and control over multiple SaaS applications. Alternatively, you can allocate several IT security team members to do the detection and monitoring.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...

