Understanding Shadow IT: Risks, Strategies, and Emerging Trends
Since the early adoption of digital technology in business, companies have been struggling to build secure environments. Shadow IT has become one of the major security issues. It provides entry points for criminals to work on IT systems. It also causes major cybersecurity events (like data loss).
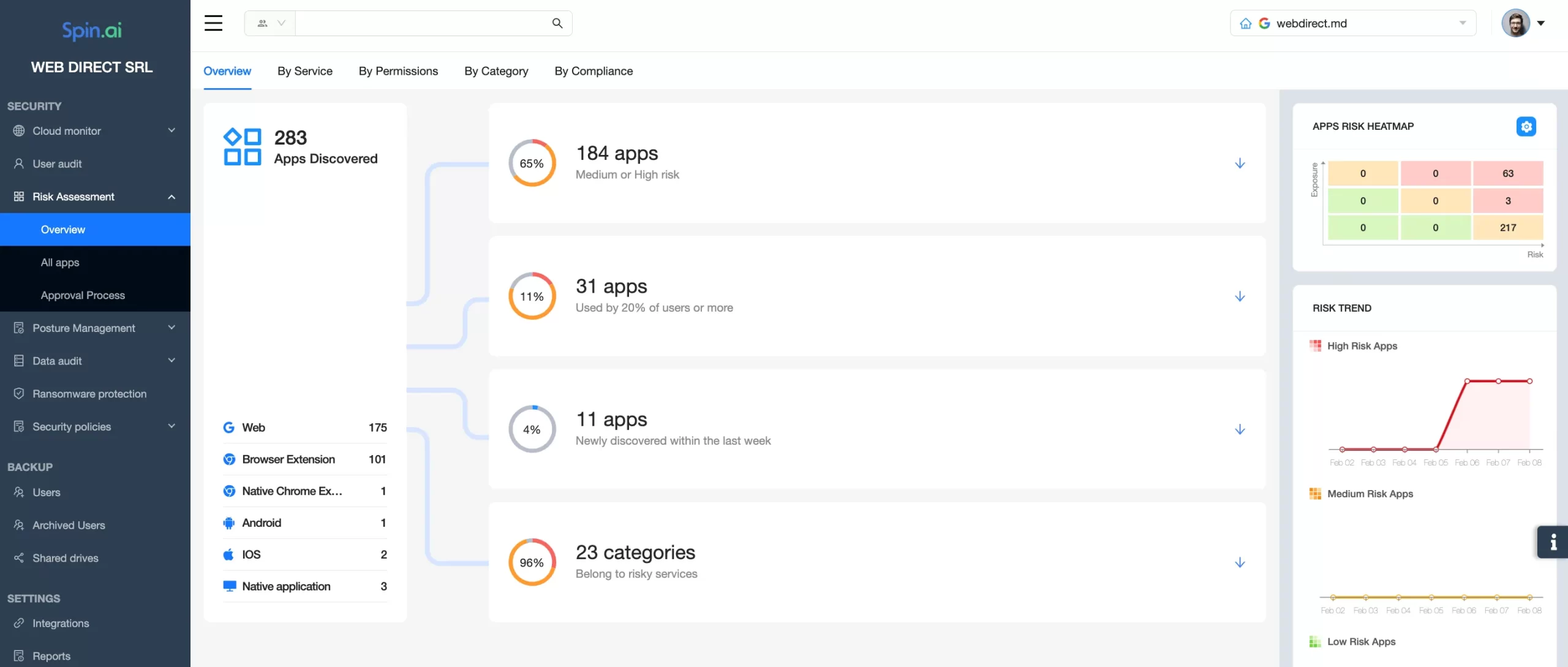
There are many different types of Shadow IT. In this article, we mainly focus on unauthorized SaaS applications and explain how companies can regain visibility and control over these apps.
Introduction to Shadow IT
In 1989, over 20,000 medical researchers around the world received a diskette with the first ransomware virus. Most of them used the diskette on their working computers resulting in the first mass ransomware attack. At the time computer viruses were a relative novelty and the first antiviruses were largely unknown. That’s why panicked researchers wiped all the data on their working computers deleting years of research.
This incident is also regarded as one of the earliest examples of Shadow IT since it had one of its key features. The employees used the unknown diskette without consulting the IT team first.
Shadow IT is the use of unauthorized technology in the working IT environment. The IT security team has no knowledge of this technology and cannot control its impact on the system. Usually, the employees do not ask for permission to use the technology. In the worst-case scenario, they deliberately use it against the company policy.
Shadow IT can be boiled down to two main categories:
1. The use of unauthorized IT systems from working IT environments like:
- Portable data storage devices on working computers.
- Mobile devices (smartphones, tablets) to read/edit corporate data.
- Personal Computers and Public Computers for remote work.
- Public WiFi networks.
- Computer Software installed on workstations.
- SaaS applications and browser Extensions with work accounts.
- Personal IoT devices (smartwatches, medical equipment).
- Gaming, gambling, adult content on work devices.
The main outcomes are data loss, data leakage, system infection (e.g., with ransomware), credential theft, and zero-day attacks.
2. The storing of corporate data on unauthorized IT systems:
- Personal cloud or on-prem storage
- SaaS applications
- Portable and stationary personal, semi-personal (e.g., used by family), or public devices
The main outcomes are non-compliance and data leakage.
The Root Causes of Shadow IT
There are several root causes of Shadow IT. Let’s take a look at the major ones.
1. “Technological abundance”
Today, most people around the world can easily access technology. For example, in 2022 alone, over 1.3B smartphones were sold globally, and currently three-quarters of the world, roughly 6B people use the mobile network.
Up to 80% of US companies use BYOD policy. Bring Your Own Device practice can help companies cut expenses on buying and maintaining IT stack. However, it creates many vulnerabilities. This practice can work for small companies that are low on tech budget and can be of little to no interest to hackers. However, it doesn’t work for medium and large businesses.
Finally, there’s the adoption of the cloud with its easy access from any device and a SaaS boom.
These developments have blurred the boundaries between working and personal IT systems and created perfect conditions for the uncontrolled proliferation of Shadow IT.
2. Lack of cybersecurity awareness
Technological abundance doesn’t translate into technological literacy. Most people have little or small knowledge of cybersecurity risks.
3. Optimism bias
Many people have the false belief that negative events are unlikely to happen to them. They perceive cybersecurity attacks almost as a fairy tale that happens in movies and games rather than real life.
4. Productivity race
Our culture emphasizes the importance of productivity for modern humans. It is one of the main markers of success in highly competitive working environments. The desire of employees to boost their productivity with automation is understandable. Some go as far as purchasing productivity tools necessary for their work with their own money as they don’t wish to wait for the company’s approval or the price is too low to bother.
Apart from that, many strive to decrease their overload with automation. They can abandon mundane tasks and focus only on the most important and creative assignments.
5. Lack of legitimate solutions
Often employees turn to unauthorized tools because the ones that the company allows do not have all the cutting-edge features that they need for their work.
Some would do it because the purchasing or approval process is too long and the outcomes are uncertain and they choose not to wait.
6. Lack of attention
Some people use their working accounts for personal matters by mistake. For example, if one has several Google accounts logged in on the same computer, one can use the wrong account to sign in to an app or a website.
SaaS – The New Emerging Trend in Shadow IT
With cloud adoption, the new Shadow IT trend is SaaS Shadow IT. This type includes the following instances.
First, the employees use their working accounts (e.g., Google Workspace or Microsoft 365) to sign in to unauthorized productivity applications and browser extensions.
For example, a company has an authorized task manager. However, a certain team within the organization decides to use a task manager that is more convenient to them. They share not only their project plans and statuses but also some sensitive information there.
Second, employees use their working accounts to access non-work-related apps and extensions. Examples include gaming applications, online shopping websites, browser wallpapers, text-to-speech converters, ChatGPT, etc.
Third, employees use their personal accounts in cloud office suites, SaaS applications, and browser extensions to perform working tasks.
For example, a company doesn’t allow to use of AI solutions. An employee wants to benefit from a tool that transcribes online meetings and then summarizes the transcription. They sign in to the work meetings using their personal Google account and transcribe all the meetings they participate in. Now, this tool has sensitive data about the meetings.
Fourth, the employee thinks that they are signing in to the legitimate application. However, it is a malicious SaaS app that stoles their credentials.
How SaaS Shadow IT works
SaaS applications and browser extensions use OAuth to simplify access to their environments. Indeed, instead of memorizing credentials to dozens of applications, a person can simply use one account to sign into them all.
It’s also convenient to just give these apps access to your cloud data rather than transfer data to the app. For example, Grammarly began as an online application where users could check the spelling of their documents.
Today, most people use it as a browser extension that automatically spellchecks in many Google Services, social networking websites, and even some designer tools (e.g., Canva). This simple browser extension saves a lot of time for marketers, salespeople, and other employees.
On the flip side, OAuth access poses serious risks as applications gain uncontrollable access to your corporate data. Some even have editing rights. In the next chapter, we’ll be discussing how these access and rights can be abused.
The Risks of Shadow IT
Shadow IT has multiple risks for an organization’s IT security. In this section, we’ll be exclusively discussing the risks of SaaS Shadow IT.
1. Zero-day attack
Google and Microsoft have put much effort into their image and reputation. The trust they enjoy is immense. This trust is transferred automatically to the applications that the IT giants feature on their marketplaces.
The reality is slightly different. Neither Google nor Microsoft does a solid check of all the apps available on their marketplaces. The amount of work it would require would significantly decrease the revenue of both companies.
That’s why, many applications with OAuth access to Google Workspace and Microsoft 365 have bugs. Hackers are constantly looking for vulnerabilities in apps, extensions, and websites. Once they’ve found such a vulnerability they can use it for a zero-day attack. For example, to steal data, gain unauthorized access to the cloud environment of a company, or infect it with ransomware.
Furthermore, there’s a category of SaaS apps and browser extensions that were created with the sole purpose of collecting data and/or using them for a cyber attack.
Not all apps are equally prone to zero-day attacks. For example, apps created by a single person are more likely to have some sort of vulnerability.
2. Data leak
In the previous section, we discussed a case when an employee used their personal Google account to transcribe and summarize all meetings they participated in.
As a result, the meeting tool had all the conversations and most likely a lot of sensitive information stored in their data storage. This information included all the coworkers’ names, email addresses, and photos, as well as discussions of past and ongoing projects, possible trade secrets, strategies, and plans.
Some time later a group of hackers found the vulnerability in the meeting tool and were able to access all the above-mentioned sensitive information.
The criminals can now sell this data to competitors, on the Dark Web, or to the company itself.
3. Account hijack
Some malicious applications can be disguised as legitimate ones and thereby lure out the credentials of a person. However, even legitimate apps can contribute to the account hijack either through vulnerability exploits or by providing hackers with lots of personal information about the user. This information can then be used to blackmail an employee or steal their credentials (e.g., answering security questions).
4. Ransomware attack
Cloud ransomware uses the same principle of OAuth access as other SaaS apps to access cloud office suites like Google Workspace or Microsoft 365.
Ransomware often disguises itself as a legitimate SaaS application. An employee receives a social engineering letter (e.g., for the “bank”) with the request to confirm something (e.g., payment transactions). They click on the link and get the “sign-in page.” Proceeding with sign-in will literally give the OAuth access to their GW or MSO 365 environment to the hacker.
5. Data Loss
Shadow IT can also result in data loss in case an application has a bug and accidentally wipes out all the data. This is a frequent case in the Salesforce environment, as there’s a class of third-party apps that have mass edit functionality. This feature boosts productivity significantly but can also cause a major loss of client database and impede the work of a revenue-generating team for weeks or even months.
6. Non-compliance
All the above cases can cause a breach of compliance by the company. However, there’s an additional aspect to Shadow IT and compliance. There’s a category of regulations mandating certain companies where they are allowed to store their data. Storing data in unauthorized SaaS applications can break these regulations. As a result, the company can be subject to legal fines or even a lawsuit.
7. Slow incident response
The very nature of Shadow IT impedes the prompt response to related cyber incidents. Since IT team requires additional time to investigate the source of the attack.
Strategies for Managing Shadow IT
The prevalence of Shadow IT and its risks to business operations prompt modern organizations to take steps to combat Shadow IT. In this section, we discuss some of the successful strategies. Learn more about the topic here.
1. Create Shadow IT policies
Shadow IT policy is a company-wide document that provides the rules for using various types of technologies. It should list:
- All the allowed technologies and/or all the banned technologies
- Rules on how to use technologies and how not to use them
- Rules on how and where to use corporate data
- Outcomes in case of non-compliance.
2. Work with cybersecurity awareness
As we mentioned in one of the previous sections, most people do not understand the risks of technology and believe they are somewhat invincible. Thorough cybersecurity awareness training can help them realize the risks and understand that they are more prevalent.
3. Purchase tools
Automation is the easiest way to combat Shadow IT. SSPM tools can help your IT security team detect all the apps that have access to your cloud environments. These tools also assess the risks of unauthorized applications to your security. They also have the functionality to revoke app access and create allow and block lists.
FAQ
Why does Shadow IT occur?
Shadow IT occurs for several reasons. First, employees blur the line between personal and working devices and some companies encourage it with BYOD policies. Second, employees strive to be better at their work and use additional IT technologies. Third, companies do not have tools and policies to control it,
What are the implications of Shadow IT?
The implications of Shadow IT include zero-day attacks, data loss, data leak, ransomware attacks, non-compliance, and financial losses
How can Shadow IT be managed?
Shadow IT can be managed with security policies and tools that detect and provide controls over Shadow IT to IT security teams.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...


