Understanding the Risks of Browser Extensions
- What Is a Browser Extension?
- Why Browser Extensions Are Risky
- Understanding permissions risk
- Protect Yourself from Malicious Extensions
- Use Case: Safeguarding Patient Data from Malicious Browser Extensions in Healthcare
- Use Case: Managing Browser Extension Risks in Automotive Dealerships
- Use Case: Browser Extension Risks in Software Companies
- SaaS Apps and Browser Extension Security with SpinOne
- Wrapping up
Browser extensions have become an essential part of our daily lives and work environments. But have you ever considered how many extensions you use and how many have direct access to your data? While there are literally hundreds of thousands of browser extensions that offer enhanced functionality, control, and productivity, they also pose significant privacy and security risks. In this guide, we’ll explore the dangers associated with browser extensions, why they matter, and how organizations can protect their sensitive data from malicious extensions.
What Is a Browser Extension?
First of all, what is a browser extension? It is a piece of software that integrates with modern web browsers to enhance user experience and adds new functionality or features to the browser, often to enhance a particular service or application. Most browser vendors have an official “browser extension store” where extensions can be downloaded and installed for free.
Usually browser extensions request permissions that may give them dangerous levels of access to critical and even sensitive data. It means that malicious attackers can target extensions and even create malicious extensions to compromise business environments.
Why Browser Extensions Are Risky
There are several different reasons that browser extensions can be risky. One of the first things to think about is what type of access browser extensions are granted to your data. When installing browser extensions, especially those that integrate with cloud SaaS environments, most users commonly accept permission requests without questioning the level of permissions being requested.
Like admins who are guilty of overprovisioning user account permissions, developers of extensions often request more permissions than are absolutely needed. This practice helps ensure that extensions work across the board, under all conditions, and it is easier to code extensions this way than to meticulously manage only the needed permissions.For example, an ad blocker might request permission to ‘read and change’ all data on websites you visit. While this might seem justified for blocking ads, it also means the extension could alter web page content or intercept sensitive data.
In addition to the level of the permissions requested, many extensions request permission across a wide range of areas. For example, many extensions require permissions, allowing them to access things like browsing history, bookmark data, and even website history.
As a case in point, a password manager extension needs access to login forms to fill in passwords automatically. However, this same type of permissions access could be exploited by malicious extensions to steal. Malicious extensions are growing in popularity, and attackers are also looking at extensions that have vulnerabilities or weaknesses in the code that they can exploit for unauthorized access.
Additional reasons browser extensions can be risky:
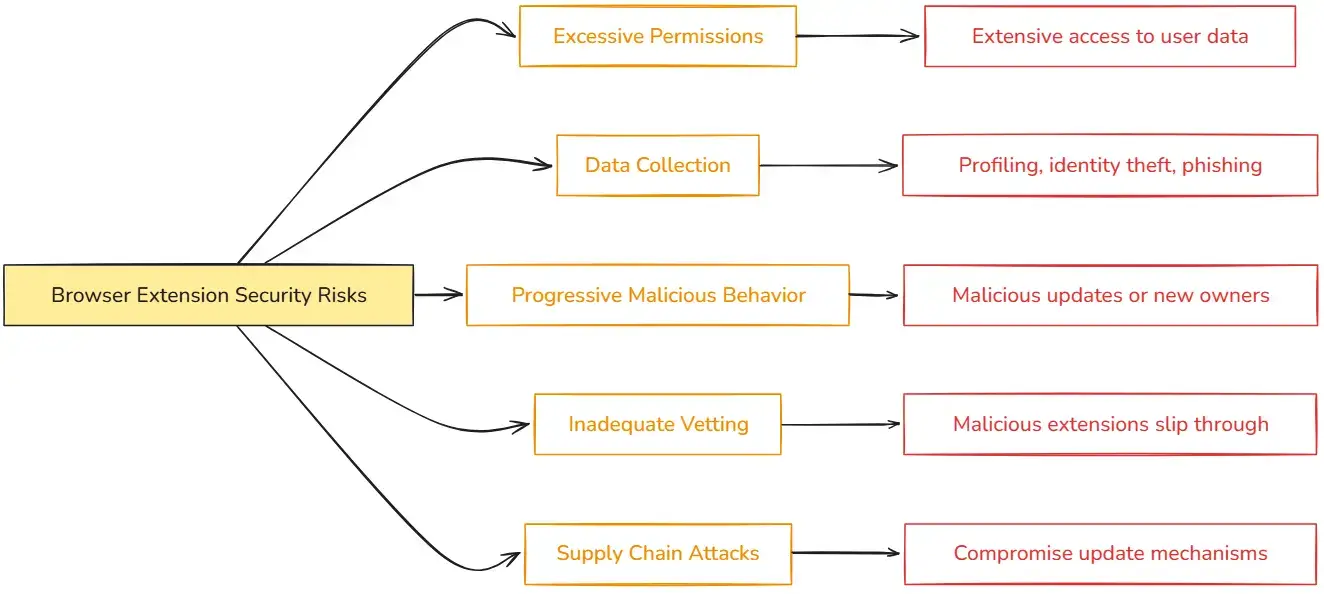
- Data collection – Some extensions gather information about a user’s browsing habits and which websites they have visited. This data can be sold to third parties for advertising or other purposes. In most cases, extensions do not disclose that they are collecting and selling your data. Users can be “profiled” to understand their activities, so malicious attempts at compromise, such as identity theft, phishing attacks, or surveillance, can be more effective.
- Progressive malicious behavior – There have been cases of extensions turning malicious after an update or after being sold to less reputable developers. For example, a previously harmless extension that provides some useful function or capability might start suddenly injecting malware or displaying unwanted ads once it gains a user base. Since users often install browser extensions and even forget these are installed, it can lead to malicious code running on a client machine for a long time.
- Inadequate vetting – Even though browser vendors have their own vetting process to make sure extensions are not malicious, risky or malicious extensions can slip through the cracks from time to time. Extensions that were once harmless may later become malicious. This can happen if a developer sells their extension to another developer or company that can push an update that turns the extension into malware.
- Supply chain attacks – In a supply chain attack, updates can be “poisoned” by injecting malware into the update itself and then pushing the malicious update to users. This type of attack was seen in the infamous SolarWinds attack, where hackers were able to inject malware into a popular sysadmin tool.
Case Studies of Browser Extension Risks
Let’s look at some real-world examples of browser extensions that turned malicious and the fallout from the malicious code.
- The Great Suspender extension – This extension was once a respected tool for managing browser tabs. It was coded by a reputable developer, but then it was sold to an unknown third party. After the sale of the extension, users began to notice unusual behavior on their systems. The extension started injecting malicious code capable of tracking user activity, and it was likely exposing sensitive information. Google eventually removed the extension from the Chrome Web Store, but many users were affected by the malicious extension.
- Data privacy violations – Another example involves a collection of data privacy violations discovered in 2019. A common group of extensions was found collecting large amounts of browsing history data and transmitting it back to a server. Millions of users installed these extensions. So, it is worrying to think how much user data was harvested by these seemingly harmless extensions. What was collected? The detailed browsing habits of users were harvested by the group of extensions, which may have been sold to advertisers or even used for more nefarious purposes, like profiling users for social engineering attacks.
- Honey browser extension – The Honey browser extension has raised the eyebrows of security advocates since it requests a broad range of permissions. The Honey extension is a popular extension for finding coupon codes. It requests access to “read and change all your data on the websites you visit.” The core functionality may depend on this level of permissions, but these could certainly be used or exploited if the extension was compromised. Again, broad permissions and high-level permissions can lead to data leaks and other malicious activities.
Understanding permissions risk
The problem with most permission requests of browser extensions is they can be hard to understand for most users, confusing to interpret, and even hide permissions being requested in clever ways. It is absolutely critical, though, to consider the level of permissions requested by third-party browser extensions.
Note the following table summarizing the permissions requested by browser extensions. Also, note the data access they provide and the possible attacks these could lead to:
| Permission | Description | Potential Malicious Attacks |
| FullAccess | Can read, write, edit, delete, and encrypt your data. | Data theft, ransomware attacks, unauthorized data changes, deleting or encrypting data which can lead to data loss |
| History | Gets full access to your browser history. | Tracking user activity, profiling users, targeted phishing, or social engineering attacks |
| LocalDrive | Gets access to your local files on your hard drive. | Theft of sensitive data, malware installation, ransomware attacks, or unauthorized data access |
| PageCapture | Gets access to your desktop and can take screenshots of your desktop every second without permission. | Surveillance of activities, capturing of sensitive information, scraping web pages you view and stealing passwords |
| Tabs | Grants the ability to interact with browser tabs (query, create, close, modify). | Tab hijacking, injecting malicious code in your browser page, phishing attacks or redirecting to malicious sites and opening tabs |
| Cookies | Gets access to your cookies; can steal login and password information. | Session hijacking, unauthorized access to accounts, identity theft, tracking sessions |
| WebRequest | Can sniff web requests, including sensitive data (e.g., credit card information). | Man-in-the-middle attacks, intercepting your data, theft of sensitive data like financial or personal information, and data exfiltration |
| WebNavigation | It collects information on every website the user navigates. | Tracking browsing habits, profiling your activities for phishing or malware installation, unauthorized surveillance. |
| Keylogger | Can capture input fields, including sensitive information from password managers. | Credential theft, capturing sensitive data like passwords, credit card numbers, social security numbers, etc |
| Certificate | Allows an extension to act as a certificate provider, potentially manipulating certificates. | Man-in-the-middle attacks, unauthorized encryption/decryption, fake digital signatures, compromising security based on certificates |
| Cookies | Grants the ability to read and write browser cookies. | Session hijacking, unauthorized access, tracking, or identity theft |
| Identity | Access to Chrome Identity API for OAuth2 authentication. | Unauthorized access to your accounts, exposing personal information, abuse of authentication |
| platform Keys | Provides access to cryptographic keys for signing and verifying data. | Unauthorized signing or verifying your data, compromising data integrity, and any type of abuse for malicious purposes |
Protect Yourself from Malicious Extensions
With the risks that come from browser extensions, organizations must protect themselves from risky or all-out malicious extensions. The first line of defense against these types of extensions is being selective about which ones are installed.
| Name | Users | Reason |
| Adblocker for YouTube — Youtube Adblocker | 2,000,000+ users on the Chrome Web Store | The extension initially loads a harmless script from fly-analytics.com, which later updates to check search results and inject steganography-encoded ads from a rogue image into the search results page. |
| uBlocker — #1 Adblock Tool for Chrome | 1,000,000+ users on the Chrome Web Store | The extension commits ad fraud through cookie stuffing, setting affiliate cookies via commands from an attacker’s server, so that when users make purchases on sites like Booking.com, the extension’s owner earns a commission |
| Adblocker for YouTube™ | 5,000,000+ users, 86 reviews on the Chrome Web Store | The extension loads ‘Google Tag Manager’ code, allowing the account owner to replace it with new code, which was then used to send SPAM |
| Chat GPT For Google | 9,000+ users on the Chrome Web Store | A fake ChatGPT application mimicking the “ChatGPT For Google” extension hijacks Facebook accounts by stealing session cookies via AES-encrypted data sent in the ‘X-Cached-Key’ HTTP header. |
Make sure you are installing browser extensions from a reputable or official source. It is recommended to only install extensions from sources like the Chrome Web Store or Firefox Add-ons. As explained earlier, these official sources get a decent amount of vetting to make sure extensions are not malicious. However, remember that even these platforms are not immune to malicious software slipping through, especially those extensions that might get weaponized after they make it to the store.
Also, reviewing permissions is extremely important. Be sure to take the time to review the permissions requested by browser extensions. Do the permissions seem reasonable given what the extension is supposed to do? If an extension seems to be requesting more permissions than are really necessary, it’s a red flag. For example, a weather browser extension does not need to access your web browser history to give you local forecasts.
Look at the recent user reviews and check the ratings of the extension before installing it. Are the latest reviews mostly negative? Are there also comments about privacy concerns or unusual behavior from the extension? Pay attention to these reviews, as these can be red flags and indicate possible security issues. Avoid poorly rated extensions and look for alternate extensions that have the same functionality.
Also, review extensions on your client system often. Many users install extensions and then forget about them, which means that risky or even malicious software may be active on your system long term. Periodically check installed extensions and get rid of any that you no longer use or recognize. This helps to reduce the potential attack surface by minimizing the number of extensions that have permissions and access to your browser.
Use security extensions that monitor other extensions for malicious behavior. These types of tools can help alert you if an installed extension starts behaving suspiciously or requests permissions that it shouldn’t. These security extensions can act as an additional layer of defense to protect privacy and security.
Keep up with security news related to vulnerabilities or other types of attacks, especially if these involve browser technologies, SaaS vulnerabilities, or other web-related cyber attacks.
Use Case: Safeguarding Patient Data from Malicious Browser Extensions in Healthcare
Doctors frequently use laptops during consultations and surgeries, capturing sensitive patient information. While browser extensions can enhance productivity, they pose significant risks, including data breaches, non-compliance, and patient safety concerns.
Key Risks:
- Data Security: Malicious extensions can expose or transmit protected patient information, leading to data breaches and serious regulatory violations, such as those under HIPAA.
- Compliance Challenges: Non-compliant extensions can result in HIPAA breaches, resulting in hefty fines and damage to the organization’s reputation.
- System Performance: Resource-intensive extensions can slow down critical systems, disrupting patient care and overall hospital operations.
- Data Leakage: Unauthorized data sharing by extensions can lead to sensitive patient data being transmitted to third parties without proper consent.
Solution:
Healthcare organizations must carefully manage browser extensions to safeguard patient data, ensure regulatory compliance, and maintain system performance. Implementing strict extension policies, conducting regular audits, and educating staff on the risks associated with unapproved extensions are crucial steps to mitigate these risks.
Use Case: Managing Browser Extension Risks in Automotive Dealerships
Automotive dealerships often use browser extensions for collaboration, particularly under BYOD policies, but minimal risk assessment introduces significant challenges.
Key Challenges:
- Data Security Risks: Malicious extensions can lead to intellectual property theft and serve as entry points for malware, jeopardizing sensitive data and operational security.
- Compliance and Legal Issues: Unvetted extensions may cause non-compliance with regulations like ISO/TS 16949, risking fines, certification loss, and data privacy violations.
- Operational Challenges: Extensions might disrupt critical software, causing performance issues and inconsistent user experiences that hinder productivity.
- Supply Chain Risks: Malicious extensions can expose vulnerabilities across the supply chain, potentially leading to data leaks.
- Product Development Risks: Extensions can interfere with R&D tools, delaying product development and compromising confidential design data.
Solution:
To mitigate these risks, automotive companies should implement controls such as allowlists and blocklists, conduct regular audits to identify unauthorized software, and educate employees on the dangers of unapproved extensions. These steps help protect sensitive data, ensure regulatory compliance, and maintain operational integrity.
Use Case: Browser Extension Risks in Software Companies
Software companies frequently use browser extensions to boost efficiency, but these tools introduce significant risks to development environments and intellectual property.
Key Challenges:
- Security Vulnerabilities: Malicious extensions can lead to data breaches, source code theft, and supply chain attacks, compromising client and partner safety.
- Intellectual Property Risks: Extensions may leak valuable code and undermine proprietary tools, leading to competitive losses.
- Compliance and Legal Issues: Unregulated extensions can result in data mishandling, regulatory violations, and complicated audits.
- Operational Disruptions: Extensions can interfere with critical tools, cause software compatibility issues, and reduce system performance.
- Quality and Productivity Issues: Extensions might introduce bugs or slow down systems, negatively impacting software quality and developer efficiency.
- Reputational Damage: Security incidents caused by extensions can harm the company’s image.
Solution:
To mitigate these risks, companies should enforce strict browser extension usage policies, conduct regular security assessments, and train employees on the dangers of unapproved extensions. These measures help protect intellectual property and ensure operational continuity.
SaaS Apps and Browser Extension Security with SpinOne
SpinOne is a SaaS security platform that provides robust solutions to protect SaaS data from data leaks and loss. It helps organizations perform misconfiguration gaps analysis and continuous risk assessments of SaaS apps and browser extensions integrated with the SaaS environment.
Key SpinOne Risk Assessment features
- Security Risk Score: Apps and browser extensions receive a risk score that is based on Spin.AI’s extensive database of metrics and behavioral analysis. The risk score includes the threats that the app or browser extension may bring to your SaaS data.
- Automated Risk Assessments: SpinOne’s Risk Assessment provides fully automated, continuous evaluations of apps and extensions in your environment, eliminating the need for manual oversight. It empowers admins and SecOps teams to quickly assess permissions, access levels, developer reputation, vulnerability history, and compliance with leading security standards. Additionally, you can monitor the risk score history to track changes in the security posture of apps and extensions over time.
- Compliance:It also supports compliance with regulations such as GDPR, HIPAA, and CCPA. The risk assessment tool enables organizations to evaluate how well an app or extension aligns with essential data protection standards and certifications, including ISO 27001 and SOC 2
- AI-driven: The SpinOne Risk Assessment tool leverages advanced machine learning algorithms to identify risks more accurately and proactively than traditional manual assessments. With access to a database of over 400,000 apps and extensions already evaluated and cataloged by Spin, the tool provides comprehensive coverage. Its GenAI component quickly generates summaries of assessments, highlighting key security gaps and vulnerabilities to support rapid incident response.
- Fast Incident Response: The SpinOne Risk Assessment solution is policy-driven, allowing admins and SecOps teams to create custom policies to allow or block apps and extensions based on their risk scores. Continuous risk assessments ensure that all apps and extensions are regularly monitored from a security perspective, enabling fast, fully automated incident response.
- Misconfiguration detection: Cloud misconfigurations pose a significant risk for organizations today. SpinOne’s Risk Assessment solution includes internal misconfiguration detection and is fully API-based and agentless, ensuring seamless integration and security.
SpinOne’s Risk Assessment for apps and browser extensions is available for free—no registration required. Simply enter the name of the app or extension, and you’ll receive a detailed risk report within seconds!
Wrapping up
Browser extensions are a great resource for enhancing the capabilities, features, and usability of modern web browsers. However, with these additional capabilities come added risks to security and privacy in the environment. Risky or malicious SaaS apps or browser extensions can steal data, launch ransomware attacks, and even lead to compliance violations.
SpinOne offers a solution that helps organizations meet the challenges of using these integrations in a way that is controlled, governed, and secure.
To learn more, connect with Spin.AI’s representatives or schedule a demo of the SpinOne platform here: Demo SpinOne SaaS Security Platform.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Obsidian Security vs. Spin.AI: Comparing Popular SSPM Solutions
Partnering with third-party applications and browser extensions have clear benefits to increasing the efficiency of...
Adaptive Shield vs. Spin.AI: Comparing Popular SSPM Solutions
As organizations increasingly rely on third-party applications to enhance productivity and streamline operations, the risks...
How Malicious Browser Extensions Steal Your Data and Security Risks
Many organizations are now focused on using cloud SaaS environments for many different things, including...



