What to Do During Ransomware Attack and After?

It is arguably the most dreaded phrase that IT admins and business leaders can hear – “ransomware attack.” Unfortunately, however, more and more organizations are falling victim to ransomware and new extortion tactics attackers are using. While protecting and securing critical data from ransomware is vital, organizations need to have a plan of action to handle an attack and their security response. This article answers the question: “What to do during ransomware attack and after?”
What is ransomware? What happens in an attack?
First of all, what is ransomware? What happens during a ransomware attack? Ransomware is a malicious program that uses a public/private key pair to encrypt business-critical data. Encryption is a process that uses a cryptographic key to scramble data so that you cannot read, consume, or otherwise use it without first decrypting it.
Ironically, encryption technology was developed to protect critical data from falling into the wrong hands. The good guys encrypt data as it is stored or before it is transmitted. This encryption process ensures the data is unreadable if it falls into the wrong hands.
However, cybercriminals have maliciously turned the tables on the protection provided by encryption. They use it to encrypt data with an encryption key unknown to the legitimate data owner. You can think of it this way. It is similar to allowing a criminal to reset the password on your computer and not tell you the new password. Only if you pay them money will they give you the new password.
Ransomware groups perpetrate this same insidious scheme as they break into organizations and encrypt their critical data. Then, they demand a ransom payment after they lock up your data with an unknown encryption key. Ransomware attackers generally compromise the network in some way, either by compromised credentials, unpatched vulnerabilities, etc.
After they gain unauthorized access, they usually snoop around the network, discovering valuable data and information that can be held hostage.
New attack methods
In a new attack technique called double extortion, ransomware groups also resort to exfiltrating data (copying data outside the sanctioned business environment) to an external location. Generally, they exfiltrate data and then encrypt it. Exfiltrating sensitive data gives them the additional leverage they need to help ensure ransom payment.
Even if an organization has adequate backups to restore encrypted data to its pre-encrypted state, criminals threaten to release sensitive data to the dark web if the business does not pay the ransom. Often, the consequences of a data leak can be more damaging than the ransomware attack itself.
What to Do During Ransomware Attack and After?
Failing to prepare for a ransomware attack is preparing for failure and disaster. Unfortunately, the odds are that most businesses will be affected by ransomware at some point.
Note the following statistics from Cybersecurity Ventures:
- By 2021 there will be a ransomware attack on businesses every 11 seconds
- Cybercrime costs will hit $10.5 trillion USD annually by 2025
- Damage inflicted will be more than natural disasters
- It will be more profitable than the global trade of all major illegal drugs combined
The moral of the story is that it is not if a business will be hit with ransomware but when it will. It emphasizes the need to be prepared for the fallout of an attack. Is preparation and having the right tools in place beforehand important? The IBM Cost of a Data Breach Report 2022 makes this observation:
Breaches at organizations with fully deployed security AI and automation cost USD 3.05 million less than breaches at organizations with no security AI and automation deployed. This 65.2% difference in average breach cost — between USD 3.15 million for fully deployed versus USD 6.20 million for not deployed — represented the largest cost savings in the study. Companies with fully deployed security AI and automation also experienced on average a 74-day shorter time to identify and contain the breach, known as the breach lifecycle, than those without security AI and automation — 249 days versus 323 days.
As detailed in the report, preparation and the right tools are essential. Let’s consider tips for organizations that have been attacked with ransomware. What needs to happen to recover successfully?
- Contain
- Secure
- Remediate
1. Contain
After an attack, the first step is to contain the attack. While there will likely be damage to critical systems and data, quick action to contain the spread of ransomware during an attack can pay exponential dividends in terms of recovery and protecting data from further damage.
Containing a ransomware attack often involves isolating infected hosts on the network from other hosts. It may mean separating select hosts or entire networks from the rest of the organization. However, disconnecting an infected host or network can prevent the spread of ransomware from the rest of the environment. Quick thinking by a savvy end-user or an IT admin can stop the spread of ransomware through the network.
It was the case with one Florida hospital:
Tips to contain ransomware:
- IT should have a plan of action on how segments of the network can be quickly isolated
- Having playbooks ready for execution is helpful during the stressful initial moments of discovering a ransomware attack
- As found in the IBM Cost of a Data Breach Report 2022, use cybersecurity automation where possible
Artificial intelligence security automation helps to reduce the fallout of a ransomware attack
2. Secure
After containment, quickly securing the environment is vital. Securing the environment involves several key steps. First, it is essential to roll through a mass password reset across the organization. This step helps to ensure that any compromised passwords used to gain entry into the organization are reset.
It may also be necessary to take down Internet-facing systems to analyze these for compromise and understand how security may need to be bolstered. For example, if specific locations or sites are infected with ransomware, site-to-site VPNs may need to be disconnected while containment continues in the affected sites. In addition, firewall rules may require reevaluating, and traffic may need further scrutiny for nefarious activities and network traffic.
Tips to secure environments after a ransomware attack
- Have processes in place for mass password changes in the environment
- Understand network topologies and have these documented for quick remediation
- Document and understand firewall rules and what types of traffic are allowed
- Audit firewall rules regularly to ensure these are scoped appropriately
Google Workspace Backup Solution Comparison Table
View our competitive pricing chart
*Contact Us for current pricing.
3. Remediate
Organizations remediate the breach in the final phase of responding to a ransomware attack. Remediation involves resolving the underlying issue leading to the attack, such as compromised credentials, unpatched systems, or zero-day vulnerabilities.
During the remediation process, businesses should quickly work to analyze all systems and implement the security safeguards necessary to finish securing the environment and return it to an operational and reasonably secure state. In addition, performing a post-mortem of the attack and the steps carried out helps businesses understand what can be done to bolster their security posture for future attacks.
In this stage, organizations work on understanding how to avoid the same kind of attack in the future and implement the additional safeguards, security solutions, or process changes needed to help introduce additional security.
Tips for remediating the environment after an attack:
- Document everything – changes made, processes introduced, technical systems and configurations settings introduced
- Each new system, software, or application introduced into an environment, should prompt a new risk analysis of the environment as a whole
- Remediating security threats and new vulnerabilities is a continual and ongoing process
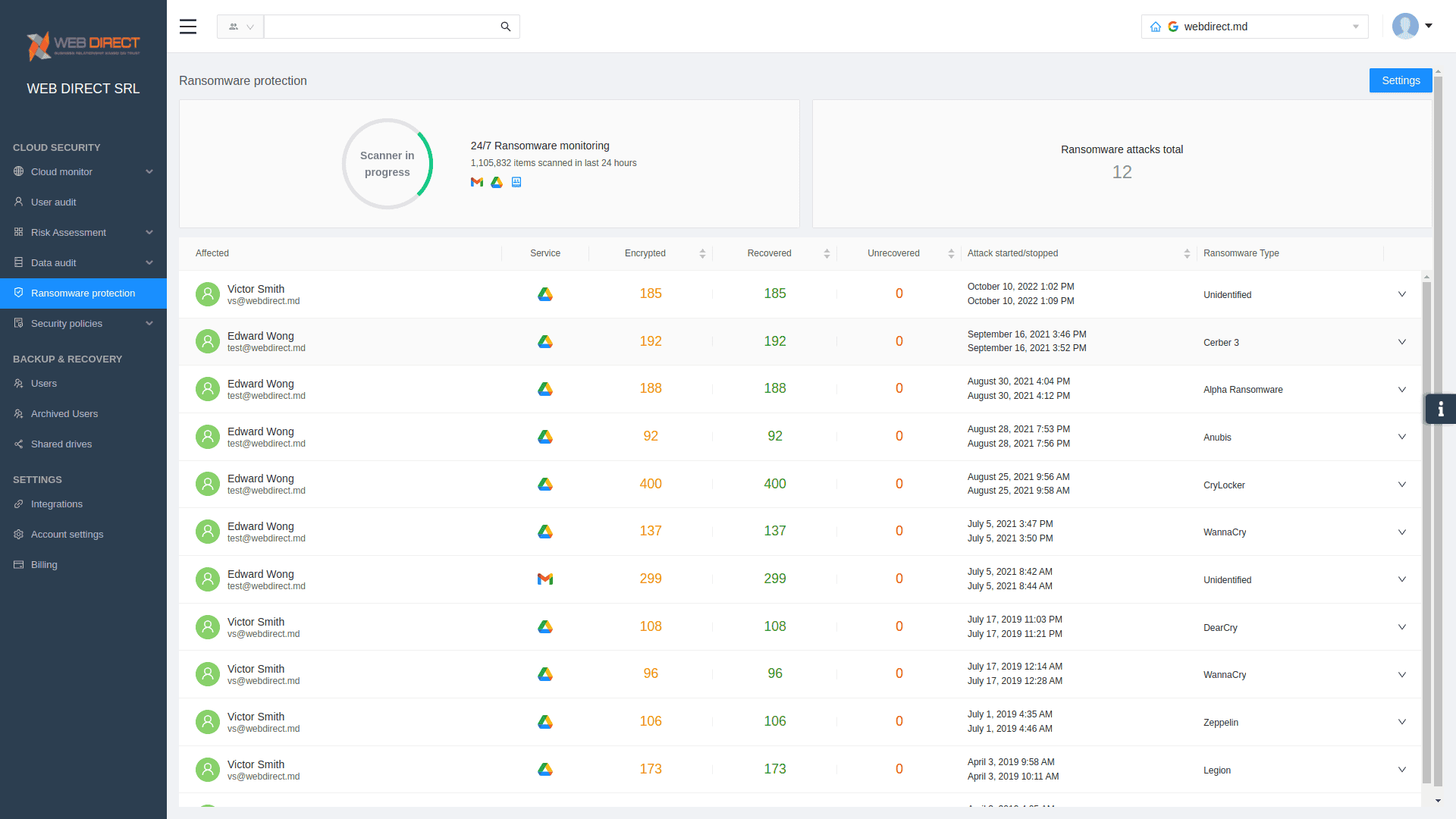
SpinOne cybersecurity automation
SpinOne enables organizations to have the technical capabilities and features needed to protect and secure cloud SaaS data to meet the challenge of ransomware. With SpinOne, you get proactive, automated ransomware protection:
- Monitors cloud SaaS environments for signs of ransomware 24/7/365
- If ransomware is detected, SpinOne blocks the ransomware source
- Automatically isolates assets affected by the ransomware attack
- Automatically restores affected files to the latest backed-up version
- It Immediately notifies IT admins of incidents in real-time
If you would like to speak with a Spin Solution Engineer to discuss how SpinOne can help you meet your ransomware protection challenges, click here to book a demo: Request a Demo of SpinOne
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Best Google Drive Backup Solution
In today’s digital-first world, protecting your company’s data is crucial. If you’re like many businesses,...
SpinBackup vs. Spanning: Comparing Popular Backup Solutions
You’ll see SpinBackup and Spanning pop up in many online searches for leading backup solutions...
Expert Insights: SaaS Backup and Application Governance (Part 3)
Welcome back to our blog series on SaaS data protection. Part 1 focused on data...



