Zero-Day Attacks Mitigation: Guide for Enterprises
Zero-day attacks can disrupt your company’s operations and impact your business. Learn how to address this issue from our Zero-Day Attacks Mitigation Guide.
There are many cybersecurity risks and vulnerabilities that organizations must protect against today. Unfortunately, new vulnerabilities and exploits each week can jeopardize business-critical data. In addition, businesses must be on guard against new attacks targeting specific vulnerabilities in systems, both on-premises and in the cloud. Arguably, one of the most dangerous types of attacks is known as a zero-day attack. So what is a zero-day attack, and why are they so dangerous? What can organizations do to protect their business-critical data? Can zero-day attacks affect your cloud data?
What is a zero-day attack?
Zero-day is a broad term covering multiple aspects of a vulnerability leveraged to attack business-critical systems. Intuitively, the term zero-day refers to newly discovered vulnerabilities that developers and maintainers of the software have “zero days” to fix. During this zero-day period, hackers have a golden opportunity to make their move and compromise systems containing zero-day flaws.
The terms zero-day vulnerability and zero-day attack are connected. The zero-day vulnerability is the actual software flaw allowing for a zero-day attack to be carried out on a critical system. You may also hear the term zero-day exploit. The zero-day exploit refers to the process or methods attackers use to exploit the zero-day vulnerability, leading to a zero-day attack.
Software companies are constantly testing and running new software releases through tests and code reviews to spot or discover vulnerabilities, flaws, and other inconsistencies leading to code instability, unreliability, and security issues. While, by in large, software vendors find critical security flaws internally, there are times when attackers or other “bad guys” discover the flaw before the software vendor. It leads to a worst-case scenario where attackers have the upper hand in time and opportunity to exploit systems before the software vendor can patch the security vulnerability.
The malicious code attackers develop to take advantage of the zero-day vulnerability is called “exploit code” and can allow the attacker to carry out a wide range of nefarious activities. For example, users of the vulnerable software may be targeted by the exploit code, leading to compromised systems, stolen data, ransomware infection, supply chain attacks, identity theft, etc.
Attackers take advantage of zero-day vulnerabilities to attack critical systems
Realistically, it may take days, weeks, or even months for very complex or complicated zero-day vulnerabilities to be adequately patched. It is further complicated because once the patch or updated version is released resolving the issue, it takes additional time before all the affected critical systems can be patched and remediated.
The dark web plays a large role in zero-day exploits and attack code used against organizations. Like Initial Access Brokers’ services in selling legitimate access credentials to attackers, threat actors sell zero-day exploits on the dark web for large sums of money. In addition, it provides attackers even quicker access to exploit code to compromise systems affected by the zero-day vulnerability.
What can zero-day vulnerabilities affect?
The landscape of software code that a zero-day vulnerability can exploit includes anything and everything. Unfortunately, new types of attacks and flaws in software can be discovered and exploited at any time. Zero-day attacks can be discovered and used soon after the software vulnerability is discovered. A quick list of favorite targets of zero-day attacks include:
- Business productivity software (Microsoft Office, etc.)
- Operating system exploits (Microsoft Windows Server and client operating systems, Linux, macOS, etc.)
- Web Servers and web-related technologies (Microsoft IIS, Apache, Tomcat, Nginx, Java, etc.)
- Encryption and security code (OpenSSL, SSL, and encryption algorithms)
- Hardware, firmware, and other hardware components
Zero-day attacks mitigation
Security is best described as layers and requires organizations to rely on various protective mechanisms to bolster their security posture. However, there are several best practices for zero-day attacks mitigation that helps businesses to have a strong posture against zero-day attacks and the damage they can inflict.
- Stay current with security and software patches, including third-party software
- Monitor user and system access
- Use role-based access control
- Use endpoint security solutions, a good firewall, and network segmentation
- Backup your data
1. Stay current with security and software patches, including third-party software
One of the best zero-day attack mitigation strategies is keeping your software patched with the latest security and software patches, including third-party software. It is essential to patch all software, not just core operating systems, web server technologies, etc. Many organizations may be blind-sided by a zero-day attack due to unpatched third-party software, even though they regularly patch critical systems such as operating systems with the latest security patches.
Even if an operating system is fully up-to-date with the latest patches and security remediations, if it is running out-of-date third-party software, the unpatched software application can easily lead to compromise, regardless of the underlying patches to the operating system. It illustrates just how thorough patching strategies need to be to keep pace with the growing threat landscape.
2. Monitor user and system access
Another effective tool to help with zero-day attacks mitigation is monitoring user and system access. Monitoring helps to know who and what applications are accessing your critical data. In addition, detecting anomalous access and activities plays a vital role in protecting against zero-day threats.
3. Use role-based access control (RBAC)
Limiting users’ privileges and access to only the systems and data they absolutely need to carry out business-critical tasks helps minimize the damage that an attacker can do by compromising a user’s system with zero-day exploit code. This strategy is generally referred to as role-based access control (RBAC).
Defining roles and assigning users to roles helps to create an effective framework for giving permissions to resources without granting too much access to a user.
4. Use endpoint security solutions, a good firewall, and network segmentation
Another effective security layer that organizations can utilize is using effective endpoint security solutions. This security layer provides a layer of protection against malware and other known malicious code that may be used in conjunction with a zero-day vulnerability. Often attackers use known malware and ransomware variants to attack once they have gained access using a zero-day vulnerability.
A good firewall and network segmentation strategies also help to minimize the damage of zero-day attacks by containing the “blast radius.”
5. Backup your data
While leveraging backups generally means an attacker has compromised business-critical systems, it is a necessary security layer that organizations must use to protect their data. This is because backups allow completely recreating data destroyed, encrypted, or otherwise corrupted by the activities of an attacker who may have used a zero-day attack against your business.
It is essential to also backup data contained in cloud Software-as-a-Service (SaaS) environments, as zero-day attacks may allow hackers to access critical cloud environments and on-premises data.
Can zero-day attacks affect cloud environments?
Organizations today using cloud Software-as-a-Service (SaaS) environments may think they are totally protected against zero-day attacks since the hyperscale cloud provider is responsible for patching and remediating security vulnerabilities in the underlying infrastructure and systems.
However, there are two crucial considerations regarding zero-day vulnerabilities in cloud SaaS environments like Google Workspace and Microsoft 365. First, both cloud SaaS providers operate in a shared responsibility model, meaning you are totally responsible for your data. Even though the cloud SaaS provider has a large degree of responsibility for the security of the infrastructure, they are still not responsible for the security of your data.
Second, as we mentioned earlier, zero-day attacks can target third-party software applications. One of the selling points for cloud SaaS environments is the rich integration and extensibility provided by third-party cloud SaaS applications found in the marketplaces of Google Workspace and Microsoft 365. While these can add powerful features to your cloud SaaS environment, they can increase the likelihood of a zero-day attack.
When you integrate the third-party software application into your cloud SaaS environment, you rely on the software vendor to thoroughly test and secure their software. As a result, each new third-party application integrated and used in your cloud SaaS environment increases the risk of a zero-day attack affecting the application’s specific software or underlying technologies.
What becomes even more concerning is that by default, cloud SaaS users can install any third-party application found in the marketplace of the cloud SaaS environment. As a result, it opens the door to tremendous risk for shadow IT activities and, by extension, zero-day vulnerabilities that may be likely with questionable or outright nefarious third-party apps that may have known dubious questionable practices.
SpinOne helps with zero-day attacks mitigation
Protecting your cloud SaaS environments from security vulnerabilities and other security risks are essential. As businesses are using cloud SaaS solutions more than ever, critical data is increasingly stored and used in the cloud. In addition to cloud data storage, third-party applications are easily integrated into cloud SaaS solutions with the default permissions provided to users in those environments. Shadow IT is a growing problem and it is difficult for companies to know how data is accessed in the cloud.
SpinOne is a robust cybersecurity and cloud SaaS security posture management solution that provides organizations with the tools to mitigate zero-day attacks and other security threats. It uses advanced artificial intelligence (AI) and machine learning (ML) to detect and automatically remediate threats in cloud SaaS environments.
Note the following features as part of the solution:
- Ransomware protection – SpinOne helps businesses to reduce downtime resulting from a ransomware attack from an average of 21 days to 2 hours. It can reduce recovery costs by over 90%. In addition, Spin helps companies add proactive AI-driven ransomware monitoring and protection to their business-critical cloud SaaS data.
- Apps risk assessment – As mentioned, cloud SaaS applications can introduce tremendous risk in the cloud SaaS environment and elevate the risk of zero-day attacks on third-party software. Users may use cloud SaaS apps not sanctioned by the business. Spin enables enterprises to have the ability to identify risky or leaky apps and cloud-integrated browser extensions with an artificial intelligence (AI) driven automated risk assessment. With Spin, companies can decide which apps are allowed in their cloud SaaS organization, preventing users from installing any app they choose without approval.
- Data leak prevention – With Spin, you can meet compliance requirements and prevent your data from being accessed in an unsanctioned way. The Office 365 DLP and Google DLP controls in Spin give visibility to where data is shared, both inside and outside the organization. It also provides powerful policy-driven controls, preventing data leakage.
- Backup and recovery – Spin provides a feature for businesses and their critical data not found in cloud SaaS environments – enterprise backup & recovery. Spin’s built-in backup and recovery functionality enable organizations to have versioned, granular backups to recover data as needed, even deleted items. In addition, admins can export data and migrate data between accounts as needed.
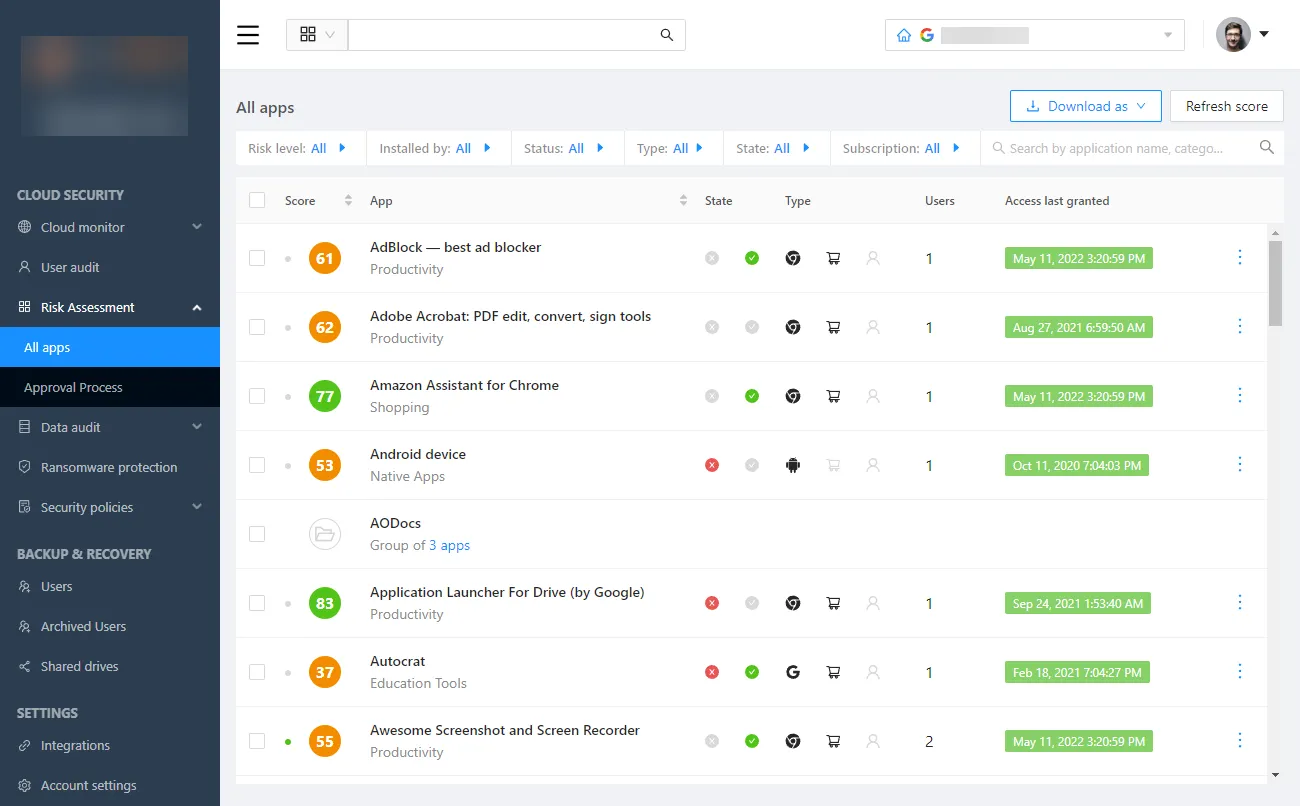
Spin provides automated risk assessments for cloud SaaS applications
Leveraging the cutting-edge features in SpinOne, businesses have the capabilities to effectively mitigate zero-day attacks, even in their mission-critical cloud SaaS environments. Businesses must protect their environments with multiple layers of security. Spin helps companies from numerous points of view, including providing the controls needed to disallow just any app from being installed in the cloud SaaS environment. In this way, IT teams can properly scrutinize third-party applications with security audits and code reviews to bolster their security posture.
Learn more about SpinOne application security here:
Zero-day attacks mitigation FAQs
What are zero-day attacks?
Zero-day attacks are attacks based on newly found zero-day vulnerabilities in which the software vendor has “zero days” to patch them. As a result, it allows hackers to exploit the vulnerability and compromise critical systems.
Can zero-day attacks affect cloud SaaS environments?
Yes, they can. While zero-day attacks could potentially affect the underlying infrastructure of cloud SaaS environments, integrated third-party applications often introduce the most significant risk of zero-day attacks in your cloud SaaS environment. Therefore, organizations must perform risk assessments of cloud SaaS applications and control which apps users can install.
How can businesses protect their cloud SaaS environment from zero-day attacks?
Organizations can properly scrutinize and control third-party apps installed in their cloud SaaS environments using modern cybersecurity tools and risk assessment capabilities such as those provided by SpinOne. SpinOne provides the cybersecurity tools and automation needed for zero-day attacks mitigation.
Google Workspace Backup Solution Comparison Table
View our competitive pricing chart
*Contact Us for current pricing.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...
Data Loss Prevention Techniques for 2025 and Beyond
It’s painstakingly clear that data loss is a major challenge facing businesses today. Our experts...
What is SaaS Security? Challenges & Best Practices
Businesses increasingly rely on Software as a Service (SaaS) for increased efficiency, collaborativeness, and scalability....



