Best Practices: Mitigating Insider Threats & Misuse of Data
When businesses think about cybersecurity threats, often the focus is on cybersecurity risks from the outside. For example, hackers operating alone or “ransomware gangs” often target large businesses with the end goal of holding business-critical data hostage. While these and other external threats are some of the most alarming, another kind of threat that is equally insidious is insider threats. What constitutes an insider threat? How can businesses protect against these types of attacks?
What are insider threats?
Insider threats are cybersecurity threats that come from an organization’s employees inside the sanctioned environment. So, this is not a threat at the hands of malicious attackers but rather end-users. So, how can a company’s users threaten business-critical data?
Quite often, it comes down to human error. For example, some of the most disruptive data loss events are often a user deleting the wrong data. In addition, there is intentional data deletion of business-critical data resulting from an employee who, with innocent intent, accidentally deletes data they assumed they could safely delete that turned out to be critical to business continuity.
The other kind of intentional data deletion is with malicious intent. In this data loss event, the employee knows the data they are deleting is essential to the business. However, due to malicious intent or after receiving notice of termination, the unscrupulous employee deletes data they know will negatively affect business continuity.
In both cases, the result of the data loss can be the same – disrupted business continuity. However, it can be true when data is deleted with malicious intent or other unscrupulous reasons, the scope of the data loss can be greater than in the case of accidental data deletion.
Insider Threats, regardless of the intent, can quickly cause a business to lose continuity of operations. For example, think of a scenario where an employee uses a shared Google Workspace Team Drive. The files that exist inside the shared Team Drive are shared between numerous employees.
Any files that are accidentally or intentionally deleted in the team drive by a single employee can disrupt all other employees accessing the Team Drive. In addition, if many business-critical files are deleted, it may potentially lead to the business invoking disaster recovery procedures.
Work from home (WFH) era
Since the onset of the pandemic in early 2020, many businesses have shifted to a largely “work from home” configuration for end-user employees. This now highly distributed workforce may work from many geographic regions, networks, and locations. As a result, businesses leveraging a new distributed workforce can see increased insider threats. How is this the case?
Employees now working from home bring new risks as they connect to business-critical environments on-premises and in the cloud. Home-based employees are often working from less secure networks with weak WiFi security and insecure IoT devices. They may even be using personal BYOD devices as a client to connect to sanctioned enterprise environments.
These factors increase insider threats to your organization as the risk of cybersecurity compromises due to work-from-home environments is increased. An attacker who compromises the user’s device can harvest credentials and can easily access data stored in cloud SaaS environments with those credentials. This type of compromise can be difficult to detect since the attacker can seemingly access data from the user’s client, making network traffic and other access characteristics appear legitimate.
Another concern for businesses as employees are working from home is the increased distractions. More distracted employees lead to more potential for accidental data deletion and other data mishaps that disrupt business operations. Distracted employees are also more vulnerable to accidentally sharing data and falling victim to phishing attacks. With these concerns and many others with the new hybrid workforce, organizations must monitor and remediate insider threats in the environment.
Data audits are crucial for remediating insider threats
Visibility to insider threats is vital. Statistics show insider threats are responsible for more than 34% of data breaches worldwide. The cost of a data breach to your business can be high in terms of immediate financial impacts and long-term damage as a result. The penalties and cost of data breach events will continue to grow for organizations and must be taken seriously.
Data is arguably the most valuable asset of today’s businesses as it now drives all modern processes. T
Therefore, one of the fundamental safeguards against data breach events and insider threats is regular data audits. Data audits are the foundation of a strong cybersecurity posture and help prevent insider threats and data breaches.
Effective cloud SaaS data audits and solutions that provide data audits in the cloud should be able to deliver the following capabilities:
- Data audits provide the ability to track cloud SaaS data and with whom data is shared. Cloud SaaS data sharing allows sharing within the organization with members of the same team, different departments, or even external third parties.
- They provide visibility to the permissions levels granted to users and offer the ability to manage those permissions. In addition, proper audits of cloud SaaS data ensure adequate security is in place and makes users accountable for their interactions with business-critical data.
- Allows organizations the ability to see if data is downloaded from the sanctioned cloud SaaS environment.
SpinOne protects against insider threats and data misuse
The SpinOne platform is a cybersecurity solution that monitors your cloud data, detects abnormal behavior, and notifies your security team or cloud SaaS administrator. Using SpinOne in your cloud SaaS environments provides quick visibility to insider threats and anomalous end-user behavior, such as abnormal data downloads, inappropriate data sharing, and other user actions.
It provides robust data auditing and cybersecurity features that allow businesses to have the visibility and controls needed to protect cloud SaaS environments. The data audit features found in SpinOne allow IT admins to have the following features available to perform a data audit checklist:
- View all data shared in the cloud SaaS environment
- View ownership of files
- Audit users with whom data has been shared
- Apply rules to files based on SpinOne security policies
- Quickly see files that are shared externally to the public
- Discover sensitive information such as credit card numbers (CCNs) shared using email
- View and sort data by an individual
- Generate data audit reports and export the audit reports as needed
SpinOne provides all the features listed above in a simple and easy-to-use Data Audit dashboard.
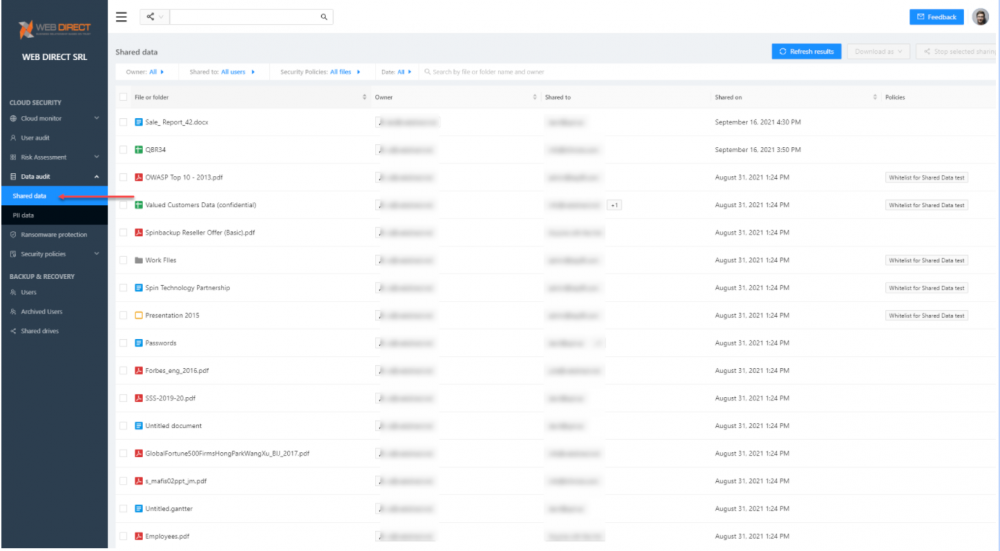
In addition to the Data Audit dashboard, SpinOne provides businesses the ability to control third-party applications, protect against ransomware, and perform automated business-critical backups.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...

