Compliance Management Challenges in Enterprise SaaS Environments
Cloud Software-as-a-Service (SaaS) environments allow businesses today to do things that would not have been possible even five years ago. With the modern capabilities of cloud SaaS, organizations can empower end-users with the tools and solutions needed for effective communication, collaboration, and business productivity, no matter where employees are located. However, a growing challenge for organizations migrating to cloud SaaS environments is compliance management. What compliance management challenges do businesses face today? How can these be overcome effectively?
Compliance management challenges in enterprise SaaS environments
Compliance management is the ongoing process of monitoring and assessing systems to ensure they meet industry and security standards, and corporate and regulatory policy requirements. There are many compliance management challenges for organizations that are heavily using hybrid infrastructure environments, including cloud SaaS. Let’s look at the following areas that create significant compliance challenges:
- Cloud Ransomware
- SaaS Data loss
- SaaS Data leak
- Insider Threat
- Shadow IT
- Unauthorized Access
- Lack of Visibility
- Third-party apps
- SaaS Downtime / API Limitations/Throttling
- Remote Workforce Risks
1. Cloud ransomware
There is arguably no greater threat to the security of business-critical data today than ransomware. Ransomware represents one of the most sinister threats that can lead to data loss, data leak, lost customer confidence, regulatory fines, and many other consequences.
Ransomware is not only a threat to on-premises environments. Modern ransomware is becoming very “cloud-aware” and can target cloud resources effectively. It means the assumption that your data is safer in the cloud from ransomware is unfortunately not true.
Cloud ransomware is becoming more common
Attackers are commonly using a combination of phishing emails and cloud SaaS OAuth abuse to infiltrate and infect your business-critical data. An unsuspecting end-user who grants access to a malicious cloud SaaS application unwittingly grants the ransomware the access it needs to start the encryption process of cloud data, including cloud email and cloud file storage.
Modern ransomware variants are increasingly using the threat of data leaks on top of data encryption. Even when organizations have backups of their data, ransomware operators can leverage the threat of leaking sensitive or customer data to the dark web.
Ransomware is a compliance nightmare. As shown in the major ransomware attack on Colonial Pipeline, data leak often ensues, and the fallout can last for years.
2. Data breaches and data leaks
Data breaches can cause tremendous damage to organizations. For one, they are extremely costly. According to the IBM Cost of a Data Breach Report 2021, the average total cost of a data breach increased by nearly 10% year over year, the largest single-year cost increase in the last seven years.
As stated in the report:
Data breach costs rose from USD 3.86 million to USD 4.24 million, the highest average total cost in the 17-year history of the report.
As organizations migrate to cloud SaaS environments, data sharing controls are often one of the least understood. As a result, many organizations migrate to cloud SaaS deployments without policies preventing the default sharing of data outside the organization, resulting in tremendous risk for accidental or deliberate data leaks.
Companies must understand the risk data breaches pose to the security and compliance of their cloud SaaS environments and implement the tools needed for visibility and control of cloud SaaS data sharing.
Data leaks involving sensitive information or customer personally identifiable information (PII) data can easily happen in cloud SaaS environments due to ransomware or user activities. Organizations may have no visibility to PII or other sensitive information transmitted in their environment and no visibility to data sharing.
3. Insider threats
All too often, organizations concentrate their security efforts on threats from the outside and neglect those within their organization – their own users. Unfortunately, end-users can be the most dangerous risk to your business-critical data and constitute a serious threat to the overall security and compliance of data.
Insider threats include:
- Users who accidentally delete data
- Users who intentionally perform malicious activities
- Users who unscrupulously download business data to personal storage
- Users involved in shadow IT operations
- Users who fall victim to a phishing attack leading to stolen credentials
Any of the insider threats mentioned above constitute tremendous risks to your environment leading to threats that exist within your organization. Therefore, businesses must closely monitor user activities in cloud SaaS environments to spot the signs of unscrupulous, malicious, or compromised accounts.
4. Shadow IT
Shadow IT is any hardware, software, service, application, or otherwise, the user is using to access or interact with sanctioned business-critical data without the consent or approval from IT. Unfortunately for security and compliance, modern cloud SaaS environments make it easy for users to access thousands of applications, browser plugins, share data, and become involved in shadow IT.
Users may not be fully aware they are breaking any security or compliance rules as they may simply want to install a third-party cloud SaaS application that helps them do their job better. However, unsanctioned third-party software installation can lead to many security and compliance concerns. These may include, but are not limited to the following:
- Ransomware
- Malicious applications
- Leaky applications
- Data locality issues
- Exposed customer information
As it has been called, Shadow SaaS opens an organization up for tremendous risks from a compliance and security perspective. Users who install and use unsanctioned third-party cloud applications bypass the defined compliance governance for the business. Additionally, unsanctioned third-party apps may have security and privacy policies that open the company up to the potential for fines and other regulatory implications.
Businesses must continuously monitor, audit, and discover all third-party applications integrated into the cloud SaaS environment. In addition, technical solutions need to be in place to prevent the installation of unsanctioned cloud SaaS applications and close the gap on this compliance and security risk.
5. Unauthorized access
One of the pillars of compliance and privacy laws is preventing unauthorized access to information and data. For example, the HIPAA Security Rule contains four directives for covered entities. These are:
- Ensure the confidentiality, integrity, and availability of all e-PHI (electronic Protected Health Information) they create, receive, maintain or transmit
- Identify and protect against reasonably anticipated threats to the security or integrity of the information
- Protect against reasonably anticipated, impermissible uses or disclosures
- Ensure compliance by their workforce
In the HIPAA Security Rule, “confidentiality” means that e-PHI is not available or disclosed to unauthorized persons. “Integrity” means that e-PHI is not altered or destroyed in an unauthorized manner. Finally, the “Availability” aspect means that e-PHI is accessible and usable on demand by authorized persons.
This HIPAA Security Rule is one example of the need to monitor data access and ensure only authorized users access your sensitive or critical cloud SaaS data. In addition, businesses must monitor data sharing and prevent sensitive information shared improperly outside the organization.
Failure to do this leads to many legal and regulatory compliance implications that ultimately can lead to fines and other serious consequences for the business.
6. Lack of visibility
In the world of security and compliance, “what you can’t see CAN hurt you.” Unfortunately, after migrating business-critical data to cloud SaaS environments, businesses often find they no longer have the visibility of their data as they did on-premises. Since cloud SaaS environments make it so easy for users to take advantage of many cloud services and data storage locations, organizations can quickly lose track and ultimately all visibility to critical and even sensitive data.
A lack of visibility in cloud SaaS is one of the significant challenges businesses face after migrating. In a report on the state of cloud monitoring:
Thirty-eight percent of participants cited insufficient visibility as a factor in application outages and 31percent in network outages. Other issues, such as delays resolving a security alert (26 percent), problems with compliance (18 percent), and an inability to prevent security attacks (17 percent), underscore the significant consequences that respondents have experienced from a lack of cloud visibility.
The statistics are clear. There is a direct link between a lack of visibility in cloud SaaS and security and compliance challenges in the cloud. To prevent compliance and security disasters, organizations must have the tools and technical solutions available to gain visibility into cloud SaaS data and activities.
7. Third-party apps
As we touched on in the shadow IT section, third-party apps introduce a dangerous risk to security and compliance in your organization. Users with carte blanche access to install all applications in the third-party cloud SaaS marketplaces can wreck an organization’s efforts to align with regulatory compliance and security governance.
Google Workspace Marketplace
The default settings for cloud SaaS environments are highly permissive. For example, in Google Workspace, the default setting allows users to install any app available in the Google Workspace Marketplace. As a result, organizations must control which apps can be installed to prevent users from installing unsanctioned and even risky apps from cloud SaaS marketplaces. It also helps prevent attackers from successfully using phishing to lure unsuspecting end-users into installing malicious cloud applications containing threats, such as ransomware.
8. Downtime. API Limitations. Throttling
Lax security and compliance controls in cloud SaaS lead to a “domino effect” of increased downtime, API limitations, and throttling. Without the proper controls in place, organizations are much more likely to fall victim to threats such as ransomware. Ransomware attacks lead to downtime and the need to restore data.
Cloud service providers like Google and Microsoft have API throttling limitations that limit the speed and amount of data that can be processed using the cloud SaaS API. These limitations prevent the “noisy neighbor” scenario of one tenant affecting the performance of other cloud SaaS tenants.
However, when an organization’s cloud SaaS data has been encrypted by ransomware, the clock is ticking. Even if proper backups of cloud SaaS data are in place, the throttling of cloud SaaS API access will drastically affect restore time objectives (RTOs).
- See Microsoft’s guidance here: Microsoft Graph throttling guidance – Microsoft Graph | Microsoft Docs
It means organizations must proactively contain ransomware attacks and other malicious activity as quickly as possible to reduce the amount of data that must be recovered.
9. Remote workforce risks
Note the findings in the IBM Cost of a Data Breach Report 2021 related to remote working and how this affects the risk to your business:
The average cost was $1.07 million higher in breaches where remote work was a factor in causing the breach, compared to those where remote work was not a factor. The percentage of companies where remote work was a factor in the breach was 17.5%. Additionally, organizations that had more than 50% of their workforce working remotely took 58 days longer to identify and contain breaches than those with 50% or less working remotely. IT changes such as cloud migration and remote work increased costs, yet organizations that did not implement any digital transformation changes as a result of COVID-19 experienced $750,000 higher costs compared to the global average, a difference of 16.6%.
Cloud SaaS empowers the remote workforce. However, as shown in the report, remote work also increases the risk to your business-critical data from a security and compliance perspective. So again, your business needs the visibility, control, and guardrails in place to prevent activities that compromise your cloud SaaS environment.
The right compliance management tool for cloud SaaS
In the above list of compliance management risks to your organization, it becomes apparent that having the right tools to gain visibility to cloud SaaS risks and enforcing the security and compliance governance needed is essential. The SaaS Security Posture Management (SSPM) and compliance functionality offered by SpinOne helps businesses overcome the compliance management challenges in cloud SaaS.
SpinOne provides the following vital features for compliance, visibility, and security:
- The risk level of an application
- Review user activities across your domain
- Review how your data is being accessed and shared
- Blacklist/Whitelist applications
- Implement security policies
- Identify connected devices
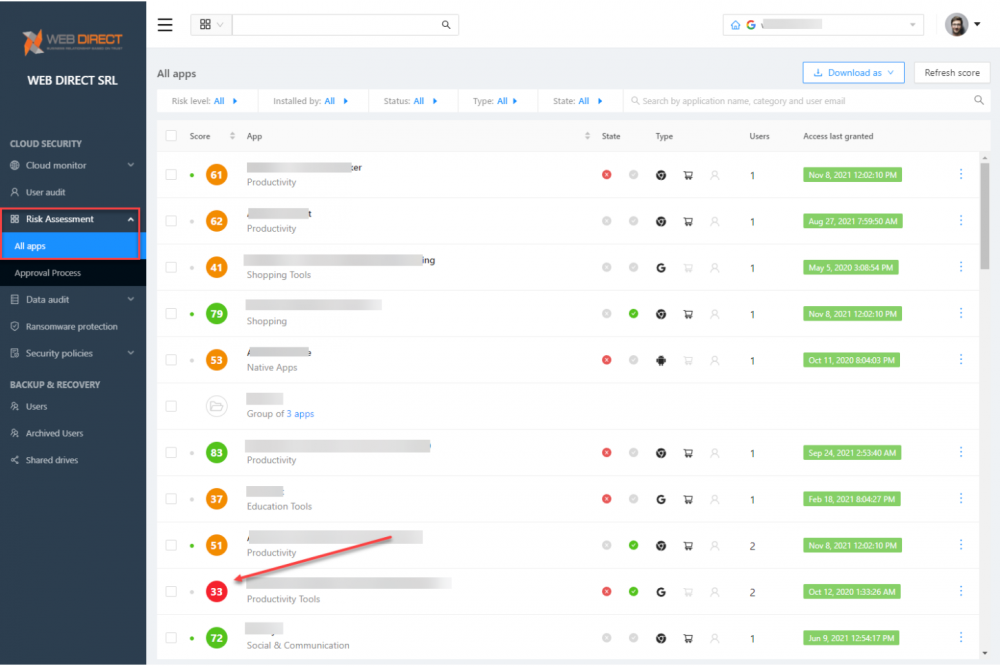
Using SpinOne artificial intelligence (AI) and machine learning (ML) algorithms, cloud SaaS applications are automatically scored based on behavior and reputation metrics. Quickly see which third-party apps pose risks to your organization.
SpinOne Risk automated risk assessment of third-party cloud SaaS apps
Learn more about the security and compliance benefits that SpinOne provides to your organization and see how SpinOne’s proactive, automated compliance and security features can bolster your cloud SaaS environment.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...