Data Leak Prevention Checklist for Employee Leave Case
One of our customers, a company that is the leading CRM solutions provider, faced a problem when an employee left the company and tried to get access to corporate data. Thanks to SpinOne’s innovative security tools, the company could safely transfer the employee’s data to another account as well as monitor the employee’s behavior until his departure. Learn the best strategy for data leak prevention.
Dealing properly with departing employees is important for any business to prevent data leaks, particularly if that employee has had access to sensitive corporate data.
This company had a policy of providing employees with a laptop and a smartphone for use at work. These devices were a gift, so the employee could keep them, even after leaving the company.
However, the question of how to make data secure soon came up. Management realized after the employee leaves the company, the devices will still be in his possession, so he could easily delete everything or make copies of data from the corporate account from home.
The first solution everybody would guess is to migrate the leaving employee’s G Suite data to another account. Though this step is vital and important, it cannot provide thorough deep data leak prevention. Sensitive information can be kept not only in Gmail, Google Drive, and other G Suite applications but also in the risky third-party apps that were granted access to corporate data or shared with third-party people outside the organization. Leaving these aspects without attention may turn out to be a huge breach in corporate data.
Fortunately, Spinbackup provides an easy solution for sensitive data protection. Spinbackup data migration and Data Loss Protection services provide secure employee exit with G Suite.
Data Leak Prevention Checklist when an employee is leaving a company:
1. Remove all third-party apps with access to corporate data for the departing employee
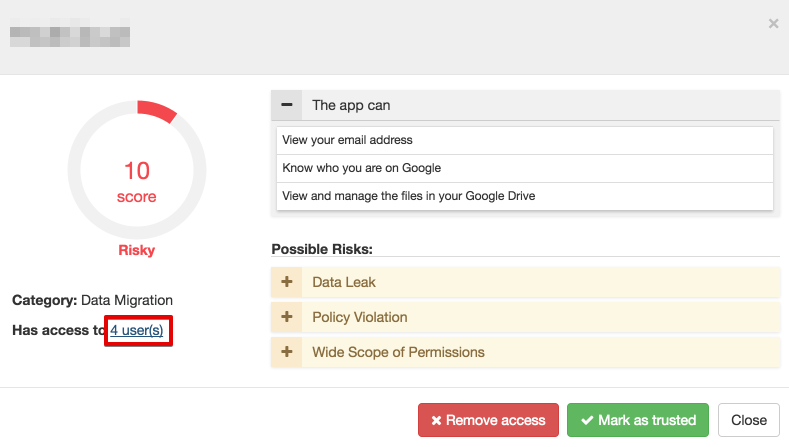
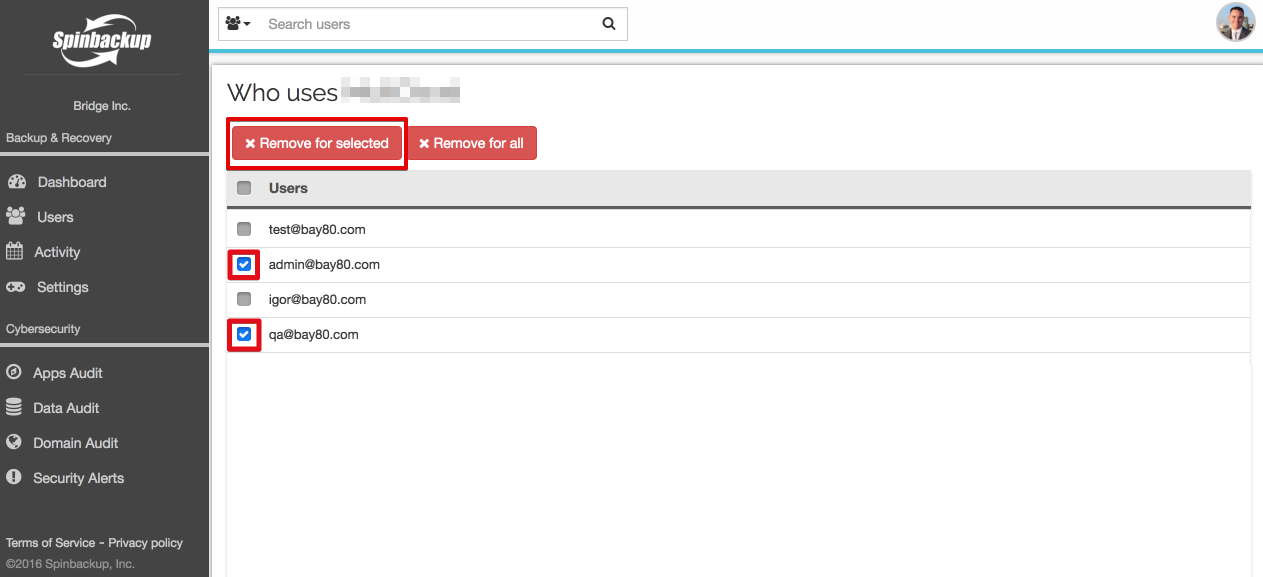
The Spinbackup 3rd-party apps audit security service gives the G Suite administrator full visibility over all applications that have access to corporate data, with the list of employees using each application.
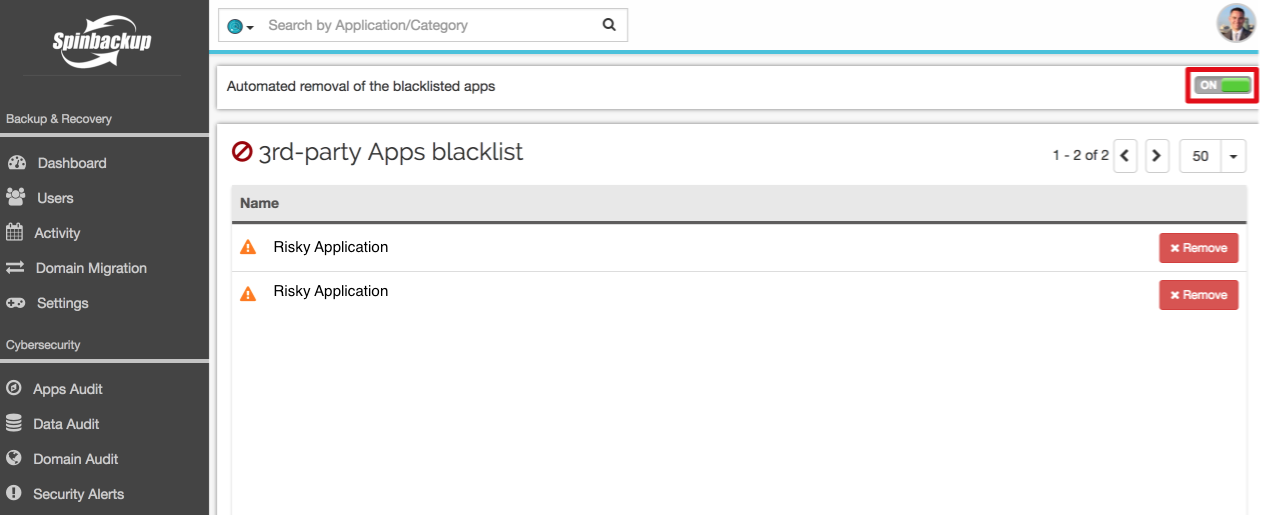
Some migration applications may be dangerous since they allow download data from corporate cloud storage to a private one. We strongly recommend you pay special attention to all applications marked risky and remove their access to corporate data, adding them to black list.
You should immediately revoke access to the corporate data for all applications the departing employee uses. For the riskiest apps, delete them from the user’s devices by turning on the automated removal of the blacklisted apps.
You can do this easily with the 3rd-party apps audit within SpinSPM Google Workspace security service:
You can find step-by-step instructions on using the 3rd-party apps audit in our Knowledge Base.
2. Check the files shared by the departing employee outside the organization
Every employee understands, after he leaves the company, he will have no access to an enterprise G Suite account. However, an alarming cyber security fact is 59% of employees steal proprietary corporate data when they quit or are fired. Many do this in an unsophisticated way by sharing confidential document with users outside the organization. Many organizations overlook this when planning an employee exit with G Suite.
We strongly recommend using the Spinbackup Data Audit to see files shared with third-party users by the departing employee and revoke this access and/or take ownership of the files if necessary.
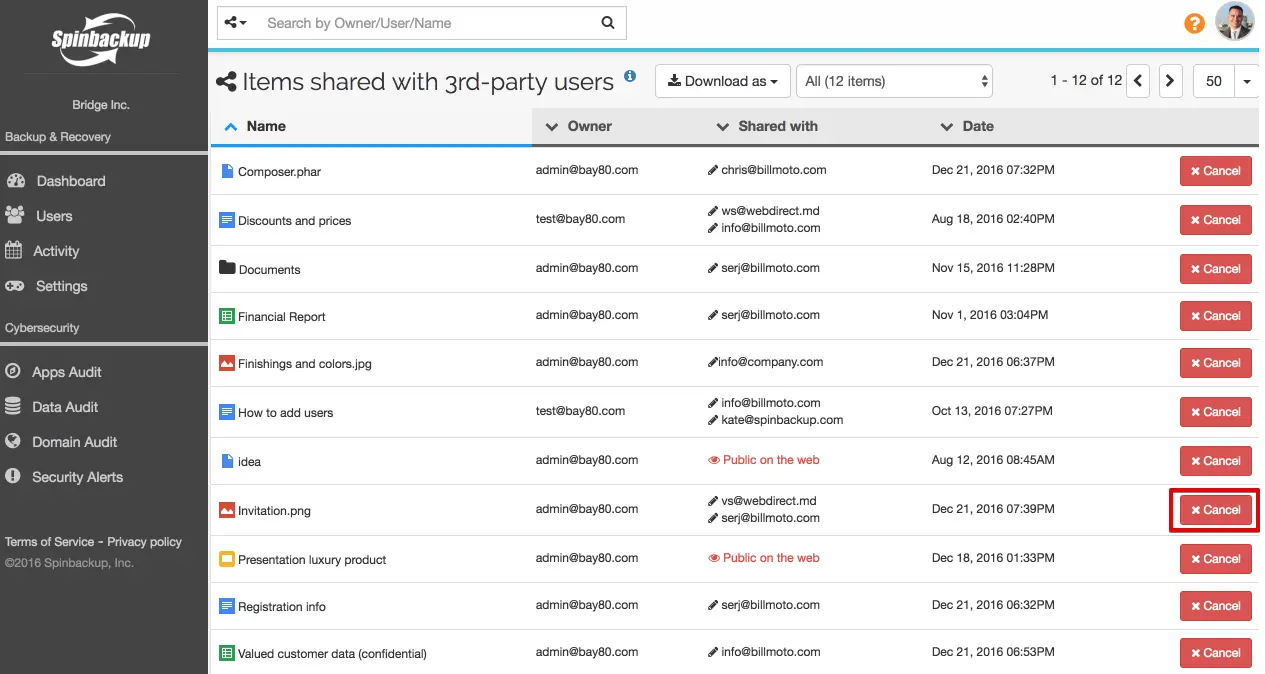
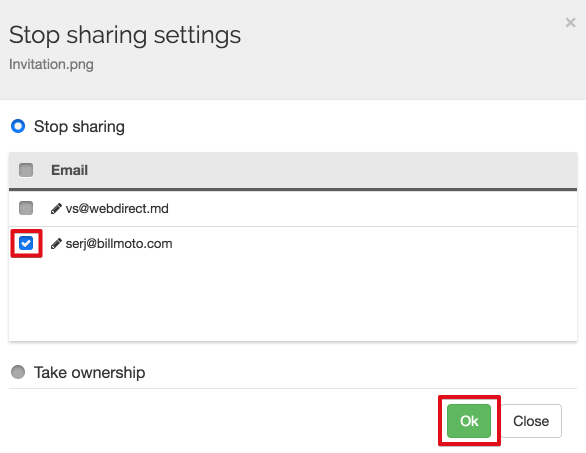
3. Transfer the data out of the G Suite account
The data should be moved to the account where it can be managed, backed up, and accessed.
Migrating data from one G Suite account to another allows you to keep all the data, with no need to pay for an additional license for an employee who has left the company.
This is possible with the data migration functionality of Spinbackup:
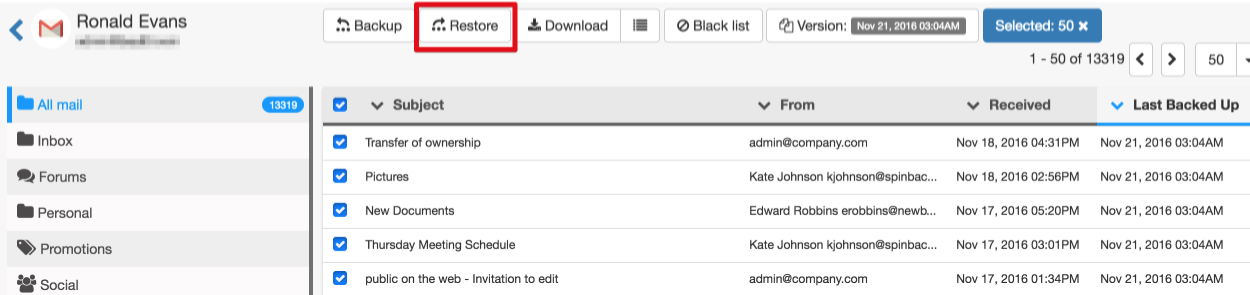
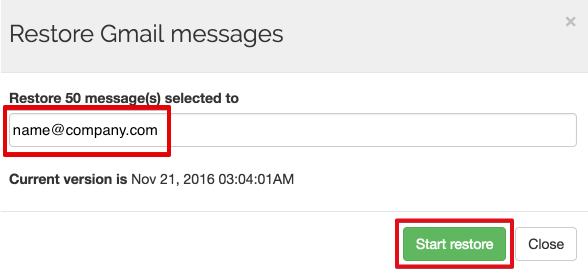
You can read more information about how to migrate data between G Suite accounts in our Spinbackup Knowledge Base.
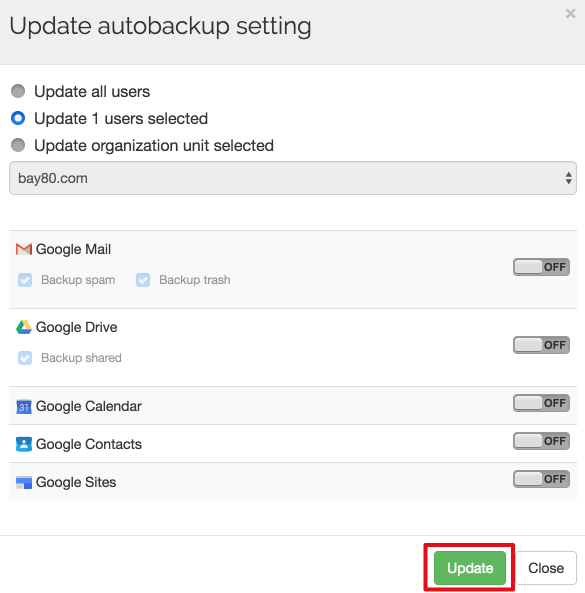
4. Deactivate all backed up services for that user
The user management console in Spinbackup allows administrators to activate or deactivate auto-backup for any or all G Suite services for a specific user. Backup can be turned off, once the data has been migrated to another account:
5. Delete the user from SpinOne
The user can then be deleted entirely from the backup account via the management console:
After the company remotely backed up the user data to a different user account, the data was safe from deletion by the user. The additional security steps were then completed to ensure corporate data was not accessible by the user by deactivating any third-party apps and reassigning file ownership. All the data was safely secured and the entire user account could be deleted without the risk of any loss of important data.
The Importance of Data Protection Services for Companies Using the BYOD Policy
Many organizations have no formal BYOD policy in place or do not consider the consequences for a policy similar to this one, where an employee retains devices after leaving the company. Often, this is not realized until it is too late. You can protect your company from data loss and leak disasters due to BYOD by using the cybersecurity and data migration tools provided by Spinbackup.
Spinbackup is a useful tool for cases like this, as it allows organizations to migrate and secure G Suite data quickly and safely. Without Spinbackup, had the company wanted to retain a copy of all the user data, the easiest way to do it would be by taking ownership of the employee’s G Suite account and changing the password. However, this would mean the company continued to pay a $10 a month license fee for an employee no longer at the company. Using Spinbackup to securely migrate G Suite data in this way is not only quick and easy, but it can also save a lot of money in the long term.
If your company has experienced a similar situation, or you are concerned about employee data use and BYOD, please share your thoughts and experiences in the comment section. Your feedback can help Spinbackup in developing future product updates and may help prevent other businesses from repeating the same mistakes.
Check out Spinbackup’s GDPR compliance and keep your data fully protected!
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...

