API-based CASB: Bridging the Gaps in Cloud Security
In today’s hybrid cloud world, organizations are using both on-premise resources and public cloud services like IaaS or SaaS. This blurs the security boundaries for those using public cloud resources.
As a result, we see an increasing number of gaps in cloud security that modern IT teams are struggling to close.
Organizations need to address cyber security concerns and ensure compliance when using both on-premise and public cloud hosting infrastructure. This includes enforcing network security policies for on-premise systems in the cloud.
Cloud Access Security Brokers or CASBs are often used to sit between on-premise infrastructure and cloud infrastructure and enforce enterprise security policies. There are many different implementations and types of Cloud Access Security Brokers (CASBs). Two different approaches to implementing CASBs involve using API CASB and also Firewall/proxy-based CASBs. What are the differences between the two? Which is the more scalable, modern solution? Let’s take a closer look at CASBs in general as well as look at these different implementations.
What is CASB?
CASB Architecture, Security and Policy Enforcement
According to Gartner, CASB or Cloud access security brokers, are security points that are placed between cloud service users and providers. Their purpose is to enforce enterprise security policies when accessing cloud resources. These security points can either be on-premises or cloud-based.
CASBs consolidate multiple types of security policy enforcement.
Example security policies include:
- Authentication
- Single sign-on
- Authorization
- Credential mapping
- Secure Google Workspace exit plan
- Device profiling
- Encryption
- Tokenization
- Logging
- Alerting
- Malware & Ransomware detection/prevention
- and more
A CASB helps organizations secure and control user access to public cloud resources. CASB implementation offers numerous benefits for those utilizing public cloud services. To complicate matters, today’s organizations may be using multiple public cloud vendors, and employees may be accessing those resources from several different devices both on the corporate network and from public Internet connections.
CASBs scrutinize and make sure that network traffic that is traversing between on-premise networks and public cloud networks is in line with sanctioned company use.
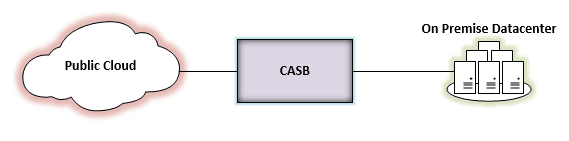
CASB’s sit between the on-premise organization and public cloud resources
Organizations today consider CASB implementations to be a crucial aspect of their security posture with their public cloud infrastructure, and rely on CASBs to perform many of the following important security functions:
- Many company employees may have personal public cloud accounts that are accessible from company networks. CASBs can help prevent any data sharing between approved company public cloud resources and personal public cloud resources
- Prevent upload and download functions
- Monitor privileged account usage and prevent any unauthorized access using those accounts
- Enforce a certain policy set for an end-user accessing public cloud resources based on the device or user account they are accessing
- Enforcement of encryption policy – both in-flight and at-rest data encryption
- Application audit of approved or potentially unwanted applications that may have access or have been linked to company-approved public cloud resources
- Confidential information detection and scrubbing – Such information as credit card numbers or social security numbers are information that organizations treat as sensitive. CASBs can detect and remediate confidential information being shared across
- Malware/Ransomware detection and protection against threats – Generic malware and especially Ransomware are huge concerns for organizations today and these concerns now extend to cloud resources such as cloud storage. CASB implementations must be able to protect against these threats
- Proactive security alerting that actively alerts when certain security events are triggered, including sensitive data detection
API CASB vs Proxy/Firewall? How to Choose the Best CASB Deployment Model?
There are basically two ways that Cloud Access Security Brokers can be implemented – using an API-based CASB vs a proxy/firewall-based approach. In taking a look at both approaches, there are definitely differences between the two methods. However, we will see why the API-based approach to CASB implementation is the more powerful approach between the two CASB implementations.
What is Firewall/Proxy-based CASB?
The firewall or proxy-based CASB approach, which scrutinizes web-based traffic to cloud services as well as passes additional network traffic, provides a single gateway or “inline” mechanism that users access to reach cloud resources. As you can imagine, this approach doesn’t scale very well and can impact the performance of users accessing public cloud resources by adding additional network latency.
While a firewall/proxy-based CASB can detect security, policy, or other violation in real time, it is only effective if users are traversing the proxy to access cloud resources. If users are not configured to access public cloud resources through the firewall/proxy-based CASB or have unsupported devices which cannot take advantage of the firewall/proxy-based CASB, the traffic which could be out of compliance would be unseen or unfiltered by the CASB.
Despite the quick response of a firewall/proxy-based CASB, the lack of visibility into unsupported traffic, and the performance impact seen by end-users are major disadvantages in security and scale.
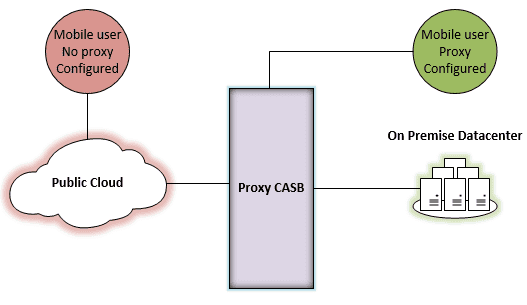
Devices not routed through the inline CASB are able to bypass security and policy
How API-based CASB Address Gaps in Cloud Security
API-based CASB platform is the most powerful and modern approach to instantiating a CASB. Before we look at how an API-based CASB works, let’s first discuss what APIs are in general, as it is a term seen a lot in today’s “Dev Ops” world of infrastructure and public cloud.
RESTful APIs are all the rage in today’s highly automated infrastructure world. Restful APIs are application programming interfaces that are client/server architecture based; they are stateless, and they have a uniform interface. RESTful APIs do not rely on any requirement of state information being shared between the server and client. Most of today’s software and public cloud resources from the major vendors are coded with automation in mind, which allows interacting with infrastructure systems in a programmatic way that allows for running infrastructure with code-based mechanisms. In basic terms, APIs are programmatic endpoints that allow us to interact with the software by sending commands to those endpoints.
Using the modern API-based approach to interacting with public cloud resources, the API-based CASB can integrate seamlessly with the public cloud vendor open APIs made available for consumption. This allows the API-based CASB to natively enforce security and policy baselines assigned by organizations. It becomes part of the public cloud resources, as opposed to being a standalone single gateway or “add-on” that must be traversed before security and policy are applied. It allows for dynamic “learning” so data can be analyzed retroactively and actions can be taken based on analysis.
Additionally, no matter which network path an end-user takes to reach company public cloud resources, those policies and security enforcement protocols are applied regardless. No proxy must be configured on the end-user device and there is no performance impact for the end-user since the CASB integrates natively with the public cloud vendor. It cannot be bypassed by VPNs or other network means. The API-based CASB solution integrates and scales much better than the firewall/proxy-based CASB solution.
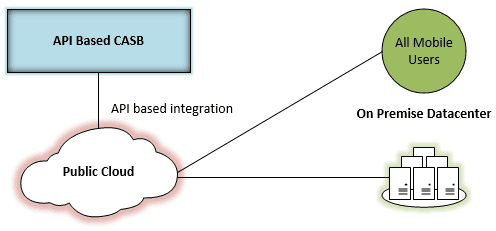
All mobile and on-premise users get same security and policies
In thinking about considering firewall/proxy-based CASB vs API based, Google, in their “Networking Best Practices for Large Deployments” stated the following regarding Google Workspace implementations:
- “Avoid routing Google Workspace data through a proxy that inspects the content of HTTP traffic, because this will reduce performance, and a great deal of Google Workspace content is dynamic or encrypted”
It’s readily apparent that large-scale public cloud vendors like Google are steering organizations toward API-based integrations. When organizations utilize API-driven CASBs, the results are a device-agnostic CASB platform seamlessly integrated with your organization’s public cloud offering that doesn’t require specific firewall/proxy settings to access resources securely. No matter which network an end-user is coming from, either company-provisioned or the public Internet, cloud access is seamlessly secured with the API-based approach.
API-based CASB solutions
A great example of this seamless API-based CASB integration with the public cloud is SpinOne for Google Workspace. SpinOne API integration offers powerful features to monitor, prevents data leakage, and protects cloud resources from malware/ransomware threats.
The tight integration of features regardless of which device or network the data is being accessed from means there is zero config that needs to happen for end-users, and the security and policies cannot be bypassed. As soon as SpinOne is configured for Google Workspace, those settings, policies, and security templates are implemented at the cloud level via API integration, and not configured based on a proxy setting.
The dashboard integration with Google Workspace provides a single pane of glass and very much feels like a native part of the Google Workspace public cloud.
Learn more about how Spin controls third-party apps and defines the risky ones.
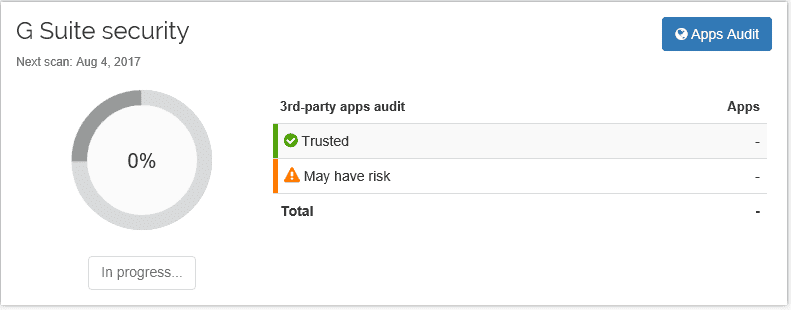
Google Workspace Security 3rd-party apps audit Dashboard
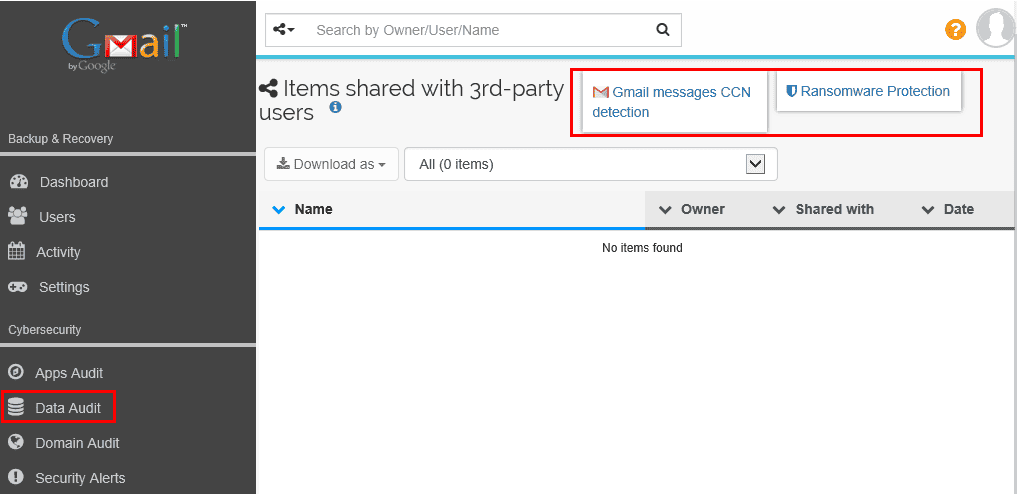
Credit Card Number Detection and Ransomware Protection
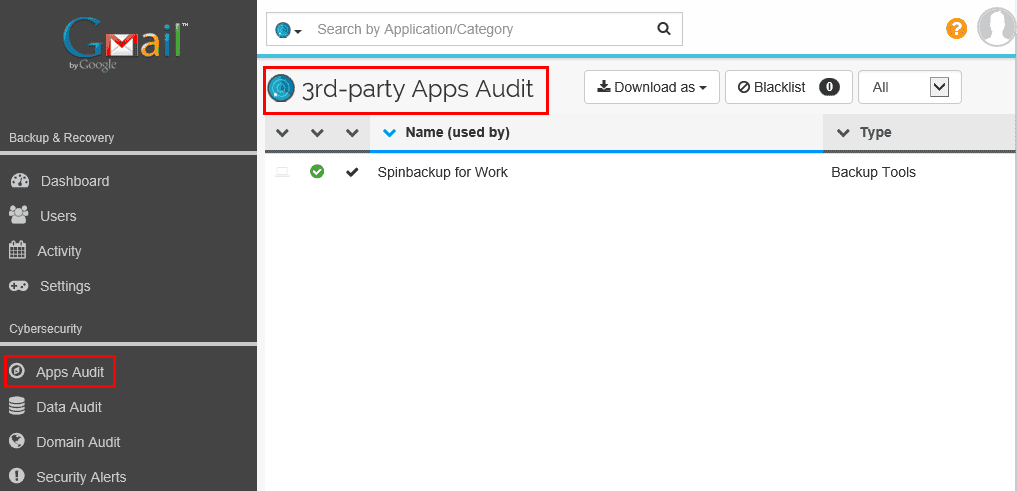
3rd-party Apps Audit Dashboard to configure Apps Audit
Thoughts
More and more organizations are moving resources to the public cloud if they have not done so already. Cybersecurity, compliance (including GDPR compliance), data leakage, and malware concerns require organizations to proactively secure data not only on-premise, but also within the realm of their public cloud resources. Cloud Access Security Brokers or CASBs allow organizations to enforce company policies that exist inside corporate networks within their public cloud environments. The two approaches to implementing CASBs in today’s hybrid cloud environments, firewall/proxy-based and API-based, both offer protection for organizations.
However, API-based CASB implementations work more seamlessly with public cloud vendors, and are much more scalable from a performance perspective. Additionally, they require no configuration from an end-user perspective such as proxy settings, and they are source network and device agnostic. API-driven CASBs can examine data dynamically and retroactively take action. In today’s modern world of hybrid networks melding on-premise and public cloud resources, API-driven CASBs are the way to achieve the best scalability, cloud cybersecurity, and integration.
Explore SpinOne API-based CASB Cloud Security Expertise!