How to Secure Cloud Data: CISO Checklist 2023
- How to Secure Cloud Data: CISO Checklist
- 1. Identity and Access Control in the Cloud
- 2. Enforce Current On-Premises Policies in the Cloud
- 3. Cloud Cybersecurity
- 4. Insider Threats
- 5. Protect Against Data Leak
- 6. Auditing and Alerting
- 7. Business Continuity and Disaster Recovery – Backups and Recovery
- Cloud Security Checklist – Bringing it All Together with SpinOne
- Takeaways
Cloud technologies have become an inalienable part of an efficient business. For CISOs, however, they present an enormous attack surface with multiple vulnerabilities to be exploited by criminals. The key question now is how to secure cloud data efficiently.
Many organizations are rapidly moving to cloud environments, making it clear that cloud infrastructure is an effective solution for modern production workloads. The cloud has certainly matured as a platform and solution for today’s business-critical applications.
Businesses have opted to leverage cloud infrastructure for more than just running production virtual machines. They have also recognized the benefits of using the cloud for hosting critical business services such as email and file storage. The cloud revolution has brought about significant changes in the way that businesses today think about provisioning infrastructure. It has also changed the methodologies used in traditional infrastructure that exists on-premises.
A concern with literally all technical infrastructure today, whether it exists on-premises or in the cloud, is security. Cybersecurity has been a major concern with cloud infrastructure since its inception. It was the primary barrier to entry for most organizations with cloud infrastructure in the early days.
Cloud security remains a significant concern across all types of cloud infrastructure, despite notable advancements in technology and improved security measures by public cloud vendors. Even though customer confidence in cloud security is at an all-time high, it must be at the forefront of the overall cloud migration plan and ongoing “day 2” operations.
Businesses today do not want to be among the growing list of victims of data compromise, data leakage, or other cybersecurity events. Businesses today need to take a strong stance on cloud security. A cloud security checklist is an excellent starting point for implementing security in the cloud and incorporating proper security measures into ongoing operations. Let’s take a look at an effective cloud security checklist and see how it can assist organizations in securing their cloud infrastructure.
How to Secure Cloud Data: CISO Checklist
One of the critical mistakes organizations make when migrating workloads and data to the cloud is neglecting to prioritize security. Security should be a paramount consideration when contemplating cloud migration to avoid potential pitfalls. Starting beta-testing cloud as a potential solution can lead to a significant problem for businesses. If they transition from beta to production without considering or incorporating security into the solution, the problem can snowball.
It is extremely valuable for businesses to follow a cloud security checklist when migrating to cloud environments as well as carrying on “day 2” operations. This helps organizations to cover the major areas that need to be considered when thinking about cloud migration. What are the items on an effective cloud security checklist?
- Cloud Identity and Access Control
- Insider threats elimination (including ones from the employees that leave)
- Enforcing current on-premises policies in the cloud
- Cybersecurity Protection
- Data Leak Prevention
- Auditing and Alerting
- Business Continuity and Disaster Recovery – Backups and Recovery
Let’s take a look at each of these critical areas of cloud security and why organizations need to carefully consider each as they make plans and execute a plan to migrate to the cloud.
1. Identity and Access Control in the Cloud
One of the most often-overlooked areas of security is access permissions. All too often businesses assign more permissions or system rights to user accounts than the accounts need to have. Why does this create problems with security?
One of the lowest-hanging fruits that attackers generally try to exploit is user credentials. User accounts need to have appropriate permissions to only the resources they should have access to. This lessens the security scope of those credentials. For example, when a user account is assigned administrative privileges far beyond what is actually necessary, it creates a significant risk. In the event of a compromise, such as a successful attack on that account, the attacker would obtain full control over the system. This would give the attacker excessive administrative privileges granted to the account.
Cloud Identity and Access Control are central to an effective cloud security strategy and overall cloud security checklist. Cloud IAM is extremely important in that it is the mechanism that defines “who” has “what” access for “which” resource. The who are members, the what is roles and the resources are anything we want to grant permissions on in the public cloud.
User identity management and verification are extremely important when it comes to public cloud environments. Since users connect from any number of devices and networks, Cloud Identity and Access Control play a key role in verifying that users are who they say they are. Cloud Identity and Access Management play a key role in the cloud security checklist. It allows organizations to have the following capabilities in regard to identity, access control, and security:
- Identity and Access control
- Permissions and roles
- Policy-Based Access
- The intuitive, single-management interface
- Auditing
- Automation
Going back to the idea of “least privilege” discussed earlier, Cloud Identity and Access Control enable organizations to successfully implement this principle by creating roles, assigning appropriate permissions to those roles, and then assigning users to those roles. This approach ensures that users have only the necessary privileges required for their specific responsibilities.
Best Practices for Cloud Identity and Access Control:
- Use Predefined roles over Primitive roles which are much more granular
- Treat each part of an application controlled by Identity and Access Management as a separate trust boundary
- Grant roles at the smallest scope needed – “least privilege”
- Restrict the number and specifics of who can operate as a service account as these types of accounts generally have more permissions
- Restrict who can create service accounts
- Be restrictive on granting owner role to members as this allows the modifying and managing of the Identity and Access Control policy for that resource
Organizations migrating to or already housed in the cloud, need to closely consider the management of identity and access permissions and understand the different identity tools and offerings from various public cloud vendors. Cloud Access and Identity and Access Control allows managing permissions and assigning users to roles that can then be assigned to resources. The idea of least privilege should certainly be among the top priorities when architecting permissions and access control methodology.
2. Enforce Current On-Premises Policies in the Cloud
A great place to start with creating access and other usage policies with cloud environments is to look at the current policies that are in place with on-premises environments if these have been effectively implemented.
Many organizations may struggle to understand how usage and other access policies can be implemented in the cloud in a standardized way that is homogeneous to end-users. By using a technology called a Cloud Access Security Broker or CASB, organizations can implement and enforce policies across the organization in the cloud, effectively and efficiently.
The best CASB solution is based on an API-based CASB approach. API-based CASBs offer numerous advantages with very few limitations. They provide standardized access to end users, regardless of the network they are coming from or the type of device they are using to access cloud resources.
API-based CASB solutions are a much more seamlessly integrated approach to CASB technology in the cloud as opposed to a firewall-based approach. Using the API-based integration, the solution scales and performs extremely well despite changing end-user load and requirements. Additionally, no additional network configuration is required from an end-user/device perspective such as VPN configuration.
API-based CASBs allows for the following 9 benefits in regards to enforcing policy in the cloud:
- Intelligent, machine-learning enabled algorithms that scan and protect cloud environments
- Discovering risky applications interacting with the cloud environment
- Scans and discovers user accounts that may involved with high-risk behavior or possibly have been compromised by an attacker based on pattern analysis
- Protects cloud environments from “Shadow IT” operations
- Can enforce encryption and device-based profiles
- Allows aligning cloud usage and activity policies with on-premises policies
- Helps to protect against data leak activities such as the unsanctioned downloading of data from organization’s public cloud environment and copying that data to a personal public cloud environment
- Scans for and remediates sensitive data exposure such as credit card or social security numbers
- Scans and protects against ransomware and other malware that may infect cloud environment data
These and other powerful benefits make the API-based CASB technology a solution that organizations will want to strongly consider when looking at their cloud security checklist to ensure their data is secure. Policy enforcement is a great way to strengthen the overall security posture and plays into the next area that organizations want to consider for their cloud security checklist, cybersecurity.
3. Cloud Cybersecurity
Cybersecurity is the methodology that protects electronic data from cybercriminals. Today’s threats to digital resources come from a wide range of attack vectors. However, criminals today are looking to steal very valuable data that is potentially housed either on-premises or in the public cloud. Businesses that are in the infancy of locating data and services in the cloud may be under the misconception that having data or services in the cloud is inherently more secure.
However, this is not true. A simple misconfiguration of permissions or accidental exposure of data to the public Internet can serve up very sensitive data that is wide open for consumption. Even if businesses do not misconfigure or mistakenly make data openly available, this is the prize that is sought out by hackers.
A true security concern with housing data and services in the public cloud can simply be the lack of proper knowledge on how to secure cloud resources when compared to on-premises resources. Moving from on-premises to the cloud can require a new level of expertise and skillset that may take time to acquire or potentially hire the person with that expertise. Therein lies the danger of moving forward with a cloud implementation that may not be architected correctly from a security perspective.
Cloud cybersecurity is an essential operation that must be taken seriously from all levels of the organization. Most of today’s businesses operate digitally at least at some level. Protecting those digital resources and data is now a key business-critical process.
What aspects are involved with cybersecurity? Like security in general, proper cybersecurity initiatives are multi-layered. They require various aspects all working together harmoniously to be successful.
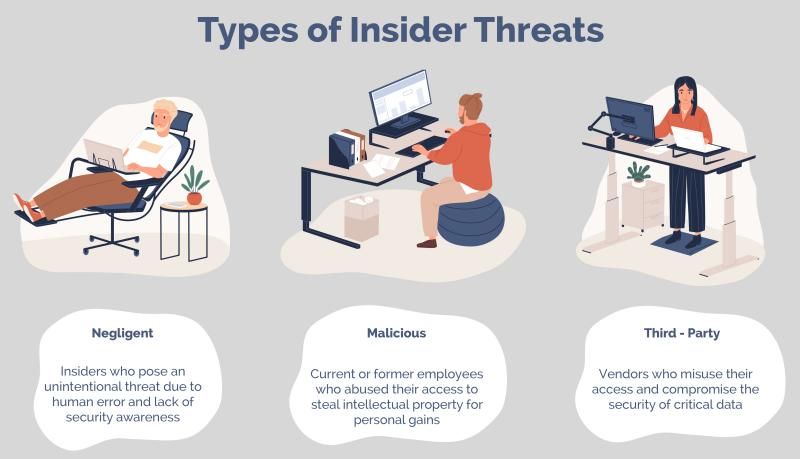
4. Insider Threats
- People – Personnel need to be trained with security as a thought process. We live in a new world that must be focused on security. Training personnel to understand the security implications and necessity of creating strong passwords, screening attachments in email, and other behavioral security benefits.
- Processes – Organizations must have the policies and processes in play that allow successfully dealing with both cybersecurity attacks that are successful and those that only attempt. Learning from each event plays a major role in successful cybersecurity.
- Technology – In today’s very complex and technology-centric environments, businesses must use powerful technology solutions to solidify security solutions that secure computers, mobile devices, network equipment, servers, etc. This includes cloud environments.
With cloud environments, having a technology solution that is capable of utilizing powerful machine learning “intelligence” can be a huge benefit. Machine learning plays a crucial role in establishing a baseline of regular activity and subsequently identifying anomalies that deviate from this norm. By continuously learning and recognizing patterns, machine learning algorithms can pinpoint potential behaviors or activities that are not typical or characteristic of normal usage. This helps to quickly identify activities that may otherwise be undetected.
For cloud environments, this may be extremely difficult to do manually with the distributed nature of the cloud and access coming from any variety of networks and devices. API-based CASBs as discussed earlier, are a powerful mechanism to implement technology utilizing machine learning. When thinking about cybersecurity, these solutions can watch cloud environments 24x7x365 and ensure electronic information in the form of your data is kept safe.
Cybersecurity encompasses the training of personnel, implementing processes, and technology that allow securing digital infrastructure. Today’s environments both on-premises and in the cloud have to be vigilant to new and existing threats both externally and internally. An extremely important part of securing cloud environments and that should be a major consideration on a cloud security checklist is protecting against data leak. What is data leak and why is it an important component of the cloud security checklist?
5. Protect Against Data Leak
Of all the cybersecurity events that generally affect organizations today, arguably the most damaging is data leak. What is data leak and why is it an important part of the cloud security checklist? Data leak is any sharing or transmission of data in an unauthorized way, outside of sanctioned use. Data leaks pose significant risks to businesses, resulting in severe long-term effects, loss of customer confidence, and damage to brand reputation. Safeguarding against data leaks is paramount to maintaining trust and protecting the organization’s integrity.
Data leak events are generally the events that lead to businesses making headlines in the news for all the wrong reasons. All too often, we hear about organizations that leaked credit card information unintentionally or had a data breach that led to the dissemination of millions of customer names and sensitive information. Data leak events can be the result of actions both unintentional and intentional.
Data leak can happen unintentionally when an employee attaches a spreadsheet with sensitive information to an email and accidentally sends the email outside the organization to an untold number of recipients, or sends the email to the wrong distribution group internally. A disgruntled employee may intentionally disseminate customer information to a competitor or attempt to leak data for a sum of money to a malicious third-party.
Malware can be used by attackers to leak data outside the organization by running malicious code on an end user system and compromising data locally or housed on the network. Phishing attacks via emails are still highly successful, even though they have been around for quite some time. By tricking end users to click links embedded in email, they are able to “phish” information from end-users, including even user credentials and other sensitive information.
With more information stored in the cloud now than ever before, organizations considering moving to the cloud or already housed there need to seriously consider what measures they have in place to prevent data leakage in the cloud. The lack of direct control in the cloud vs. the control that organizations are able to maintain on-premises can be a challenge.
Not only do businesses need to control general data leakage and loss from the cloud for unsanctioned use, but they also need to be especially concerned about data leakage of sensitive information. Sensitive information can include information that violates compliance regulations, etc.
This type of information can include credit card numbers, social security numbers, HIPAA or other information that should be treated as sensitive. It should be a priority on the cloud security checklist to have the processes and technology in place to prevent data leaks in general as well as sensitive data control.
6. Auditing and Alerting
All too often when dealing with security, the response to security events is reactive instead of proactive. Generally, a security breach or cybersecurity event is discovered and then responsive action takes place as a result. When thinking about either migrating to the cloud or for those organizations who have already begun their migrations, the cloud security checklist must contain items related to auditing and alerting.
Unfortunately, for most, a breach is only learned about when the damage is already done or data has already been leaked in mass. What can help prevent these types of cybersecurity disasters? Proper auditing and alerting are powerful tools against security compromise that can happen both on-premises and in the cloud. These actions should be proactive in nature.
Proper auditing and alerting are mechanisms when done right that can detect the breach event when it happens, and then proactively alert administrators to the events that have unfolded. With API-based CASBs there can also be a series of proactive remediation actions that get triggered in response to the events.
Again, let’s consider the advantage here of machine learning-enabled API-CASB technology that can constantly monitor the cloud environment, 24x7x365. It creates a baseline of normal behavior and activities. When those fall outside the normal thresholds for the cloud environment for a particular user or activity, administrators can be proactively alerted.
What if there are dozens of failed login attempts or a particular user? This could indicate a brute force attempt to compromise user credentials. What if successful logins come from unusual geolocation for a particular user?
This could indicate the credentials have been compromised by an attacker coming from outside the normal geolocation for the legitimate user. These are merely a couple of examples of how normal traffic and activity can be audited and used to indicate potential cybersecurity events. Then appropriate alerting can take place based on the event.
Proper auditing and alerting are essential to a successful cloud security checklist. They allow organizations to have visibility and appropriate responses to activities that may otherwise go unnoticed. However, it can be challenging to implement this type of effective auditing and alerting for businesses attempting to utilize the native tools and other features offered by their public cloud vendor./p>
7. Business Continuity and Disaster Recovery – Backups and Recovery
One of the most often overlooked areas in security is business continuity and disaster recovery. In fact, many do not even consider or list out business continuity and disaster recovery as items included with security. However, not considering BC/DR as part of any successful security checklist can be a grave mistake.
When a security event leaves data destroyed or missing, when ransomware corrupts massive amounts of data, and when a disgruntled employee intentionally deletes business-critical files, the only mechanism that can allow data to be recovered at that point is data backups.
While backups are traditionally considered in on-premises IT infrastructure and have been a staple of normal daily operations for most companies, thinking about backups seemingly get missed in the cloud. There has long been a mystical idea that cloud environments make thinking about backups and protecting your data obsolete. This could not be further from the truth.
While the major public cloud vendors today have impressive high availability and hardware and network redundancy that most enterprise environments could only dream of, this does not mean your data is indestructible in the public cloud. Public cloud data is still subject to many of the same dangers as on-premises data. These include ransomware, intentional deletion, accidental deletion, data leak, and many other concerns.
The problem for some time now has been that public cloud vendors do not provide a native data protection mechanism for businesses to protect data and resources housed in the public cloud. This means that many businesses are rolling the dice and either do not have backups implemented in the cloud at all or have only minimal data protection configured by using a third party that may not natively integrate with their public cloud environment.
With more and more data and services moving to the cloud, businesses have to be able to restore data or services that may be affected or lost. Data backups need to be a versioned copy of files and data that allow businesses to have an effective way to roll back in time to a particular version or recover files or other data that have been deleted altogether.
Cloud data backups, backup strategy, and restores are an essential part of the cloud security checklist in that data are able to be both protected and recovered as needed. Making use of a technology solution that allows having multiple versions of data stored in the cloud, the ability to recover deleted items, the ability to protect not only files but also other services such as email that are commonly stored in the public cloud, is essential.
In today’s cloud-centric world, businesses must ensure their ability to maintain uninterrupted operations and withstand failures or disasters, regardless of the location of their data. Prioritizing business continuity is crucial in navigating the challenges posed by reliance on cloud technologies.
Cloud Security Checklist – Bringing it All Together with SpinOne
One of the challenges in looking at the above list of important items found on the cloud security checklist is the ability to bring all of these items together contiguously and harmoniously and in a way that can be successfully managed. One can easily envision a number of different solutions to successfully implement all of the recommended items.
Most public cloud vendors have come a long way in recent years in providing better tooling and built-in security mechanisms. However, these have a long way to go and, in some cases, still have components and functionality that are lacking altogether. SpinOne provides the all-in-one management, technology, cybersecurity, data protection, and data security platform that allows meeting these cloud security checklist items and many others. Briefly, let’s consider the various aspects of the Spinbackup solution that allows meeting your cloud security checklist objectives.
Cloud Identity and Access Control
Spinbackup provides exciting technology that combines the best of both certificate authentication and blockchain technology to allow for ultra-secure single-sign-on to cloud environments. The Spinbackup Blockchain Single Sign-On technology acts as a bridge between the public cloud services provided by the likes of Google Workspace and Microsoft Microsoft 365 and the Blockchain community.
Built on the block verification mechanisms found in the blockchain and the proven security of security certificate authentication, they have introduced a world-class mechanism for organizations to secure their public cloud services and data.
Enforcing current on-premises policies in the cloud
Spinbackup delivers a powerful API-based machine learning-enabled CASB platform that allows organizations to enforce the same on-premises policies in their public cloud environments.
Google Workspace and Office 365 Cybersecurity
Not only does Spinbackup provide cloud data backups, but it is also a state-of-the-art cybersecurity provider for public cloud environments. It uses the machine learning intelligence in the CASB engine to constantly scan and note any anomalies and active protection such as the ransomware protection module that automatically kills the ransomware process and restores any affected files by automatically restoring them to a good state from its backups!
Data Leak Protection
Spinbackup provides real-time alerting and auditing of the cloud. By utilizing the machine learning algorithms that constantly watch user behavior and activity, any anomalies can be quickly noted. Real-time alerts send alerts to administrators when activity triggers and thresholds are met. Daily security reports allow quick reviews of daily security information of interest.
Business Continuity and Disaster Recovery – Backups and Recovery
Spinbackup provides powerful data protection for both Google Workspace and Microsoft Office 365 environments. By offering automatic 1x or 3x daily backups, encrypted data during transfer and at rest, and multiple options for storing your data in your cloud of choice, Spinbackup provides data protection that is secure, reliable, meet compliance, and allows businesses to have true confidence in their data security.
Takeaways
Don’t be intimidated by security in the cloud. Using a cloud security checklist helps to prioritize items that need to be seriously considered from a cloud security perspective. Trying to meet the objectives in the cloud security best practices checklist by using native tools provided by public cloud vendors can be challenging.
Spinbackup provides the ultimate solution to allow businesses today to have the tools and capabilities they need to meet today’s stringent security objectives found on the this checklist. It does this in a simple to use, single-pane-of-glass interface, intuitive, and powerful solution for either Google Workspace or Microsoft Office 365 environments. With Spinbackup, the cloud security checklist will easily be met with a powerful and capable solution that secures your data, your way, and with your standards and policies.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...

