Google Drive Ransomware Protection | CISO’s Guide
Despite multilayered security, Google Workspace is vulnerable to ransomware attacks. Every once in a while we hear a dramatic story about yet another enterprise hit by this type of malware. In this guide for CISOs, we explain how it hits the cloud and talk about actionable Google Drive ransomware protection.
How does cloud ransomware prevent authorized users from accessing their own data?
Ransomware is a specific type of malware that maliciously uses file encryption to “lock” your files so they cannot be accessed without the attacker “unlocking” the files for you. Access to your data will only be returned by the attacker when the ransom is paid, but paying the ransom doesn’t give you a 100% guarantee.
How is it possible for file encryption to be used on your own data without your consent?
Under normal circumstances, file encryption is a security operation implemented by a trusted system administrator to protect access to business-critical or sensitive data. Ransomware uses this legitimate security tool against you. It is malicious software that infects an end-user, often under the guise of legitimate software installation, that assumes the permissions and rights of the user and encrypts all files the user has access to. Once user permissions are “hi-jacked”, it allows ransomware to encrypt files stored locally, on a network share, and even cloud storage, all without the end-user consent.
How does ransomware encrypt Google Drive?
Data stored in the cloud such as in Google Drive can easily be encrypted by ransomware via file synchronization. With file synchronization, files that are modified or created locally are synchronized to cloud storage. File changes are the trigger that initiates the synchronization process. When the ransomware encrypts local files stored on an end-user device, the malicious encryption process triggers file synchronization to cloud storage. Once files that are encrypted by ransomware are synchronized to cloud storage, both the local and the cloud copies of the files are now encrypted or “locked” by the ransomware.
What are the impacts of cloud ransomware?
Impacts of cloud ransomware are extremely costly. There are additional best practices and recommendations per Microsoft that can help protect your Google Drive environment from the threat of ransomware.
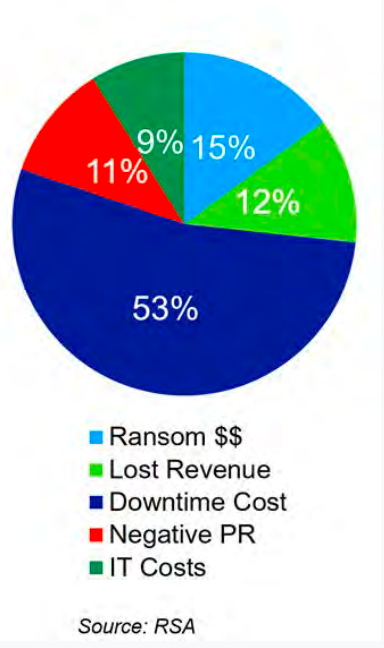
Current methods cannot detect, stop or remediate from Ransomware attacks Recovery, at best, can take many days Failures to recover/restore attacked files are very common Impact to organizations: millions of dollars in cost, lost operational time, lost data.
Ransomcloud: the emerging cloud security threat
An alarming new variant of ransomware that has been demonstrated by security researcher Kevin Mitnick is called “Ransomcloud”. With a ransomcloud attack, it is not simply file storage that is the target of the ransomware, but rather cloud-based email. In a ransomcloud infection, an unsuspecting end-user receives an email requesting permissions to perform “security” updates. When the end-user grants permissions to the link contained in the email, ransomware begins encrypting the emails contained in the user’s inbox in real-time. Ransomware that can encrypt a user’s cloud-based email is a dangerous threat to your data.
“While cloud providers are beginning to introduce features and services to help prevent or remediate a ransomware infection with file storage, very few if any of these protect cloud-based email.”
How Google Workspace Protects Google Drive and Other Services from Ransomware
How can native tools help to reduce the risk of ransomware infecting your Google Workspace cloud environment?
Several preventative measures can be taken from a Google Workspace perspective that can help protect your Google Workspace environment from ransomware. These include the following:
- Banning email attachments
- Preventing third-party apps installation
- Prohibiting access to Google Drive sync client
Prohibiting access to Google Drive sync client
File synchronization between local files stored on end-user clients and your Google Workspace environment can be dangerous as noted earlier. File synchronization between on-premises clients and the cloud provides a fast path that can allow ransomware to easily destroy data in Google Drive storage.
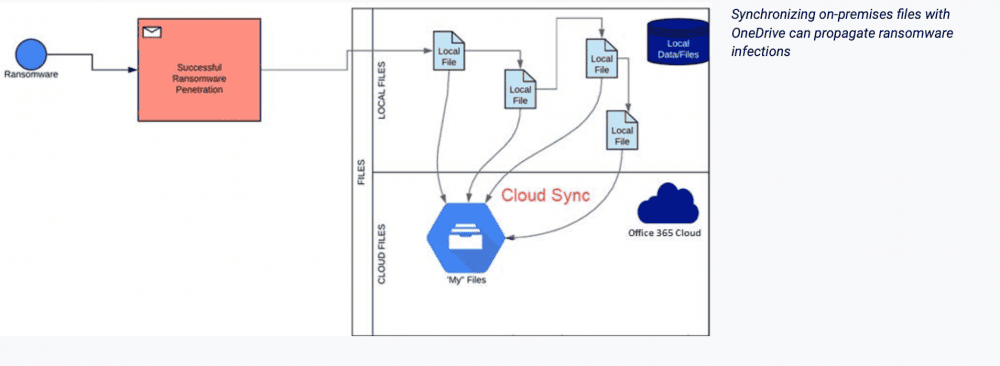
Synchronizing on-premises files to Google Workspace can propagate ransomware
However, this risk can be minimized by prohibiting access to Google Drive sync clients so that end users cannot download and configure synchronization between their client and Google Drive storage in Google Workspace. By managing and controlling sync access for your organization, the threat of an on-premises ransomware infection overwriting files in Google Drive is greatly reduced.
Check out Google’s official guidelines on turning on/off sync for your Google Workspace organization
Banning email attachments
Email is one of the most common threat vectors for ransomware. It continues to be a favorite among attackers to infect end users with ransomware. Ransomware payloads are dropped via malicious/infected email attachments. A malicious attachment generally masquerades as a legitimate file download. An end-user who unknowingly previews, downloads, or executes the malicious attachment, activates the malicious code and begins the ransomware infection.
An effective way for a Google Workspace administrator to eliminate malicious attachments as a possible attack vector for ransomware is to ban email attachments altogether. Banning Google Workspace email attachments prevent the possibility that an end-user receives a malicious attachment, opens it, and is infected with ransomware. You may wonder – does Google not scrutinize and scan emails that you received into your Google Workspace environment? They do.
However, there are ways that ransomware can still make it past malware scans and other security mechanisms. Attachments that are encrypted or compressed can often bypass security scanning measures. While banning email attachments may present challenges for end-users accustomed to using email to send files back and forth, end users can be trained to use Google Drive to share files directly which eliminates the need to send attachments via email.
Native Google solutions don’t protect from emerging threats and deteriorate the user experience
While using the native tools found in Google Workspace for protecting your environment from ransomware is a good start, the native tools are not enough in themselves for completely protecting business-critical data from ransomware. There are a couple of reasons for this:
- Ransomware is becoming much more sophisticated
- Google Workspace administrative user interface design issues lead to configuration vulnerabilities
Ransomware is becoming increasingly more sophisticated and robust. It is finding new ways to infiltrate cloud environments like Google Workspace and prey upon end-user actions (blindly granting permissions requests and others) to allow unauthorized access to your data. Shortly, attacks will initiate with Apps connected to Google Workspace. These are 100% cloud-to-cloud attack pathways. Current native Google Workspace tools do not protect you 100% when it comes to these new cloud-to-cloud attack vectors.
Businesses must match sophisticated ransomware with tools that employ machine learning and other “intelligence” to remain effective in the battle to protect cloud SaaS environments like Google Workspace effectively.
Bad user interface design is another vulnerability to native tooling. This is a challenge with Google Workspace and other public cloud environments where UX design and administrative workflows are constantly changing. Google has had UX design issues blamed for customers inadvertently leaking company data in times past.
Even if built-in tools can help organizations protect against ransomware and other security threats, UX design implementation issues and misconfiguration by customers due to those design flaws can prevent native tools from being implemented effectively. More protection is needed, and this often means making use of effective third-party security tools.
Google Drive Ransomware Protection & Security Best Practices
Since native Google Workspace tools alone may come up short in the fight against ransomware, Google Workspace administrators need to implement other best practices and security tools to secure Google Drive and protect from ransomware. These include:
- Make use of an API-based CASB – Cloud Access Security Brokers allow implementing and enforcing the same organizational policies you have in place on-premises, in the cloud. API-based CASB is the preferred way to implement CASB technology in public cloud environments like Google Workspace as they provide seamless and powerful capabilities to secure the cloud.
- Control risky third-party apps – Aside from blocking third-party applications, organizations today must scrutinize the behavior of third-party applications integrated into their Google Workspace environments. If a once trusted third-party app starts to exhibit risky behavior, you want to have visibility to those behaviors and prevent malicious actions on your data.
- Prevent sensitive data leak with role-based access controls – Modern ransomware variants are beginning to use the threat of data leak and data deletion as a means to force paying of the ransom demanded. The Maze ransomware releases hostage data to the Internet at specified intervals if the ransom is not paid. Jigsaw ransomware deletes data at intervals leading up to 72 hours when all data is deleted. By using Google Workspace’s role-based access control and API-driven CASB controls, policies to prevent data from leaking outside of your Google Workspace environment can be enforced and prevent your data from falling into the wrong hands.
- Use Google Workspace security policies – Google Workspace security policies provide a specific scope of rules, exceptions, and notification settings applied to specific users, departments, and business entities. This provides a customized security approach to different groups of users.
- Enforce compliance and regulatory standards – Regulatory and compliance concerns are becoming an increasingly critical aspect of doing business. You must comply with regulations such as GDPR, CCPA, PCI-DSS, and others. This is accomplished by leveraging the right security tools to protect, backup, and secure your data.
Ransomware Protection Solution for Google Drive: Meet SpinOne
When the very livelihood of your business is at stake (your business-critical data), you need to use the best solution available to safeguard your data from attack by ransomware. SpinOne from SpinAI is a “best-in-class” solution that provides the tools and capabilities needed to safeguard your data from the dangers of ransomware.
SpinOne is a modern API-driven CASB solution that makes use of machine learning to provide automated intelligence to fight today’s security threats such as ransomware. It does this by using a powerful two-fold ransomware protection architecture that can detect and remediate 99% of all ransomware infections.
Google Drive Ransomware Protection by SpinOne includes the following four stages:
Detect Cloud Ransomware
AI-powered algorithms monitor Google Drive for any anomalies that indicate a ransomware attack.
Stop Cloud Ransomware
SpinOne provides a quick and effective attack response. The attack source is identified and stopped immediately by blocking the ransomware process.
Remediate the Damage caused by Cloud Ransomware
Once the attack is identified and stopped, any files affected by the ransomware attack are identified.
Recover Files Damaged by Cloud Ransomware
SpinOne automatically restores the files that have been identified as affected by the ransomware attack. Google Workspace administrators are notified of the attack and the automatic recovery.
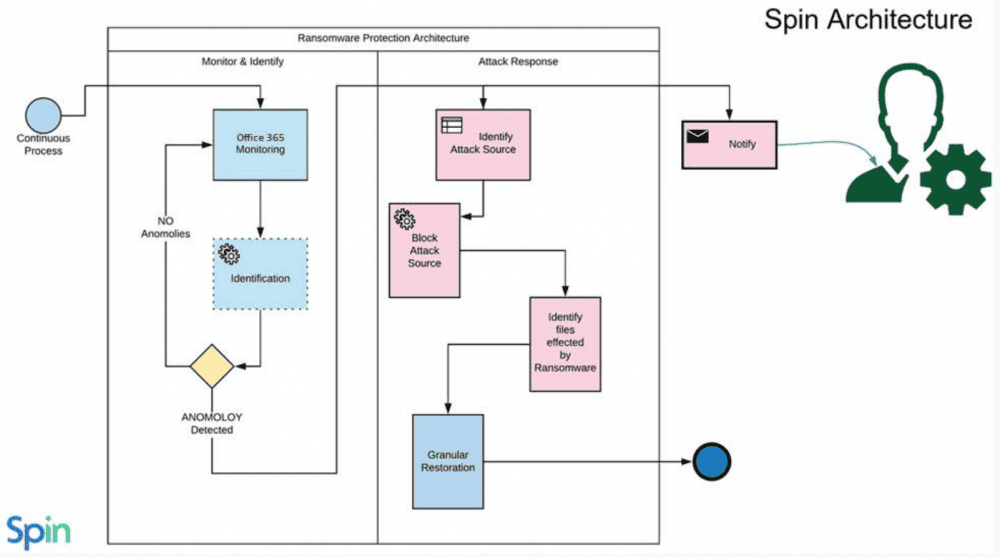
SpinOne provides automated ransomware protection and remediation
SpinOne’s two-fold, automated ransomware protection is unique among its competitors. Not only does SpinOne backup your business-critical data, it proactively monitors and secures your data against the very threats that often require data recovery such as ransomware.
Heightened Threat – What organizations can do
It is imperative for organizations worldwide and in every business sector to take the threat of ransomware seriously. Ransomware can not only lock down files. It can disrupt lives, as shown with recent ransomware attacks such as the Colonial Pipeline. Businesses need to give rapt attention to their cybersecurity strategies, tooling, and other cybersecurity processes and procedures. Giving attention to the basics is essential. It includes such things as:
- Securing email against phishing attacks
- Implementing two-factor authentication
- Securing perimeter networks
Aside from securing email, identity, and the network perimeter, the reactive, traditional approach to cybersecurity with manual processes is no longer effective in dealing with modern ransomware variants. New techniques and cybersecurity defenses such as security automation help organizations to give attention to their security posture and limit the scope of damage that ransomware can inflict on business-critical environments.
While security automation is not 100% effective against preventing a ransomware attack, it can much more rapidly contain and stop an attack as it unfolds. Security automation helps to quickly disarm the hackers using ransomware as they cannot encrypt enough data leading to any consequence.
Security automation solutions use next-generation artificial intelligence (AI) and machine learning (ML) to recognize the anomalies in the environment, either in user-level or file-level behavior, indicating a ransomware infection is underway. After a ransomware attack is discovered, the same AI and ML processes can block the attack source and remediate the environment based on predefined “playbooks” of tasks.
SpinOne is a cloud SaaS Security Posture Management (SSPM) Platform for enterprise organizations that uses security automation in the fight against ransomware in cloud SaaS environments such as Google Workspace and Microsoft 365. SpinOne uses a four-step process to remediate ransomware, including:
- SpinOne detects the ransomware attack using AI and ML-driven processes
- It automatically blocks the network source of the ransomware attack
- It identifies the number of damaged files
- SpinOne automatically recovers files infected by ransomware.
It is a great example of proactive security automation in action that allows countering the massive threat vectors, including ransomware, on the horizon.
Wrapping Up
SpinOne is a multi-tenant platform created by Spin Technology and designed to simplify the complexity of cloud data security. SpinOne combines three solutions that make business data bulletproof from security breaches and insider threats as an all-in-one platform. SpinOne is trusted by over 1,500 organizations worldwide including HubSpot, Vopak, IBT Industrial Solutions. We have more than 1,200,000 business users in more than 100 countries.
FAQs
What should I do if my Google Drive files are compromised by ransomware?
Find the source (an OAuth app or extension) and revoke access. Try check if the previous versions are intact. If not, recover from backup. If you do not have a backup try finding a decryption key online.
Can Google Drive recover files that have been encrypted by ransomware?
No. Google Drive doesn’t have an inbuilt native backup.
How can I spot suspicious activity or potential ransomware threats in my Google Drive?
The most obvious sign is the file encryption. Another possible sign is when you open a document and see another “you” in it. Hackers sometimes would study your data before encrypting it.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...

