CASB: Decisive Role of Cloud Access Security Brokers
The importance of Cloud Access Security Broker (CASB) grows as businesses rapidly adopt new cloud collaboration technologies and platforms.
Enterprise security professionals need to thoroughly assess the risks, communicate those to business leaders, and develop practical cybersecurity, risk management, and compliance strategies. These strategies aim to build a secure and resilient digital business environment.
Cloud computing has greatly changed the way businesses operate. According to the Morgan Stanley 2016 CIO Survey, it was predicted that by 2018, about 30% of all applications would be moved to the Public Cloud.
Cloud is approaching 20% penetration of workloads which is an important inflection point in technology. When a structural trend hits 20% penetration, adoption tends to accelerate until it reaches 50% penetration. This is a function of customers becoming more aware and comfortable with the technology. Additionally, initial hurdles like network speed in the case of smartphones and security in the case of cloud tend to be addressed in the early years. Source: Morgan Stanley 2016 CIO Survey
Organizations now need to collaborate and communicate more effectively with customers, partners, and employees. Companies look for cloud security solutions that can support enterprise productivity and enhance secure sharing of information. They also seek solutions that can protect valuable data and meet regulatory compliance requirements, such as CASB cybersecurity solutions.
It allows them to take advantage of cost-effective and easy-to-use cloud-based applications such as G Suite, Office 365, Salesforce, and others. As businesses adopt of new technologies, drive innovation, and navigate complex environments to achieve their digital goals, the cyber threat landscape continually evolves.
This is accompanied by a rise in compliance and regulatory expectations for enterprise-grade companies.
Cloud security practitioners keep exploring new mechanisms capable to make a smooth and secure transition to the cloud and adjusting existing digital risk management practices.
Cloud adoption is continuously growing: currently, 40% of IT budgets are spent on cloud-based solutions. Many organizations now have a “Cloud First” mentality, and SaaS is projected by Gartner to grow to 75 billion dollars by 2022 at a 19,2% compound annual growth rate. Large-scale cloud migrations and continuous transition of applications to the Cloud absolutely change the digital future, products, services, sales and delivery models, partner strategies, and customer interactions. The Cloud is changing, and cloud security solutions must evolve to keep pace.
In this article, we will explore how to anticipate unexpected emerging cyber risks and establish proactive cyber-resilience for effective IT operations and business continuity.
Top 15 Cloud Applications Security Challenges
When moving legacy applications to the cloud companies need to consider evolving cloud applications security threats to fully benefit from the Cloud. The cloud adopting companies are facing the following cybersecurity challenges.
- Security gaps due to lowered visibility in the cloud
- Gaps in coverage from traditional security tools
- The rise of Shadow IT and unsanctioned applications
- A sharp increase of both managed and unmanaged endpoints
- Compromised privileged users and malicious insiders
- Identity management in the Cloud
- Underdeveloped or lacking cloud standards
- Cloud Service Providers’ non-transparent internal security practices
- Convenient ubiquitous cloud access increases cyber risks
- Location of digital assets is hard to track and verify CASB solutions can ease cloud
- Risk of exposure compliance-related data including Personally Identifiable Information (PII), Payment Card Information (PCI), Protected Health Information (PHI)
- Threats from malicious employees and hackers
- Unauthorized data transfer
- Brute-force attacks
- Human error
What are CASBs?
According to Gartner, Cloud access security brokers (CASBs) are on-premises, or cloud-based security policy enforcement points, placed between cloud service consumers and cloud service providers to combine and interject enterprise cloud security policies as the cloud-based resources are accessed.
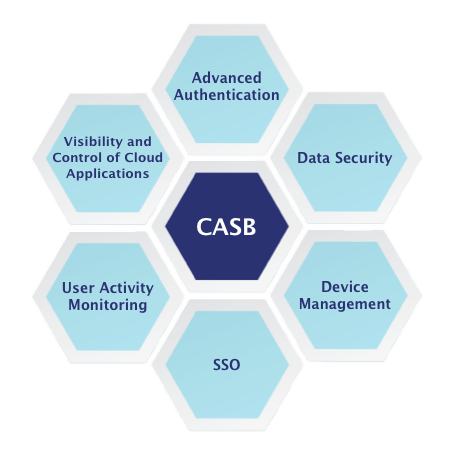
The critical role of CASBs is strengthening the information security strategy. CASBs aggregate the following key Cloud Access Security requirements into a single interface:
- Visibility into Cloud Apps Use
- CSP Threat / Risk Analysis
- Malware Prevention
- Cloud Data Protection
- Access Control (including adaptive access) provides additional degrees of security based on the context of the employee, trying to access the cloud application
- Identity Management Services
- User Provisioning/Deprovisioning
- Prevent jailbreaks and malware
- Control access to corporate data and networks.
Key-Value Drivers of API-driven CASB
- Increasing regulatory risks and legal pressure on organizations.
- Maturing cloud service markets.
- Demand for smarter mobile apps continues to rise, and developers embrace artificial intelligence, augmented reality, and more robust security models to fill that gap in 2018.
- Growth of smartphone and tablet markets with larger screens and new services available, and their wide use by the workforce.
- Expansion of cloud services to new industries, for example, in healthcare, automotive, home, and retail.
- Growth of automated and sophisticated cyber attacks.
How API CASB Allows Organizations to Enforce Their Security Policies
Cloud platforms are introducing new and intricate business models for small and midsize businesses, who are quickly adopting Software as a Service (SaaS) but may encounter security gaps. In this scenario, Cloud Access Security Brokers (CASBs) serve as security policy enforcement agents that protect your cloud applications and sensitive corporate data. CASBs are capable of safeguarding your data from any device, user, or application, whether it is accessed on-premises or off-premises.
According to Gartner, there are 4 pillars of CASBs (Cloud Access Security Brokers), such as:
- Visibility
- Data Security
- Compliance
- Threat Prevention
Learn how to prevent cloud apps threats with the SpinOne app monitoring and control tool.
Let’s review cloud access security concerns and risks. Primarily, visibility, threat detection, data loss, and data leak prevention. Since customers deploying cloud solutions do not actually have physical control of the infrastructure, they need to make sure that the cloud service providers are following appropriate physical, logical and legal controls, including identity management, access control, patching, resilience, and malware, and Ransomware protection.
When CSPs (Cloud Service Solution Providers) are engaged outside the information risk management and legal function, you need to be at least aware of the major risks you are accepting from the CSP vendors. Since cloud apps are evolving faster than ever, and customers of CSPs need to continuously monitor and govern access to all the new apps becoming available on the market.
Your Comprehensive Cloud Data Governance and Access Checklist
Here’s the Comprehensive Cloud Data Governance and Access Checklist, which includes questions you should consider to minimize the risks of you PII and valuable corporate data leaks.
- How do you provide access to the right people in your organizations?
- When people change jobs or an employee leaves the company, how do you ensure the access is adjusted or revoked?
- What mechanisms do you use to ensure that the access provided complies to enterprise security policies?
- How do you implement attestation from asset owners for the users of the cloud apps that are housing regulated data?
- How are users authenticated into those cloud apps?
- Do you control the user identity store or is it at the CSPs?
- How do you ensure that only authorized personnel is sanctioned to cloud apps?
- How do you control the implementation of the appropriate authentication mechanisms outside your corporate perimeter?
- Is confidential or regulated data being stored in the CSP’s data centers? If so, is it encrypted and who holds the keys?
- Is any of that data replicated to local devices for offline access?
- Have your enterprise security policies been reviewed and updated in the last two years?
- Does your policy address data protection or vulnerability scanning policy when faced with the realities of the cloud?
- Have your standards been analyzed to corporate cloud access requirements’ constraints?
- Is anyone watching over what cloud apps are allowed and blocked? Who is managing those processes?
- What are the minimum insurance requirements with your CSP vendor: physical control, logical control, visibility; what about incident handling between the two organizations?
- How are cloud applications currently provisioned and de-provisioned? Do you have identity management solutions, such as user access provisioning and single sign-on? Is it in place already?
- What are the top corporate information assets that are at the highest risk at the cloud? Do you know if they are presently stored in the cloud? What regulatory mandates are of concern to your organization in this area?
- What gaps exist in security architecture technologies and processes for Cloud?
- Do you have SIEM (Security Information and Event Management)? Is it actually doing something of value? What about enterprise mobility management?
- Are automated tools deployed to provide deep shadow IT visibility within your organization? other cloud service providers or other vendors.
Enterprises are now scrambling to detect what cloud apps are in use, and working to plug holes as to where corporate information is flowing out to other cloud service providers or other vendors.
Now let’s take a closer look at how Cloud Access Security Brokers work. There are different deployment mode options for cloud access security brokers. In the previous article dedicated to Spinbackup’s API-based CASB, we explored in detail the various ways that a CASB can integrate into a cloud application.
The most efficient and advanced option is API-based CASB, as API gives you ultimate visibility and allows CASB to tap into API framework from various cloud apps hosted by different cloud service providers. (G Suite, Office 365, Salesforce, and others). The API-based CASB solution is capable to analyze traffic and detect which applications might be in use or in the future it can detect new or up-and-coming cloud apps your IT security team was not previously aware of.
Since the CASB knows what applications are in use, they can also provide decision support regarding the risk relevant to each CSP. When the user accesses the cloud app the CASB sits between the user and the cloud, at the highest level the CASB can determine if the application is sanctioned and the person is authorized to use it. At the deeper level, it can determine if the user is authorized based on a device, user behavior, location, time, and other user-related factors.
Ephemeral cloud infrastructure makes threat modeling expensive and cumbersome. Cloud access control solutions limit employees’ access but are not capable to to detect unauthorized access of cloud applications through the use of compromised credentials. Thus, manual forensic methods are not scalable given the tremendous cloud usage increase and threats arising.
API-based CASB is the only solution to re-calibrate the human dependency for security by automating threat modeling, detection, and remediation, combined with ultimate predictive analysis and threat prevention tools.
API-based CASB is capable to consolidate multiple types of enterprise security policy enforcement, including:
- Authentication
- Single Sign-on
- Authorization
- Credential mapping
- Device profiling
- Encryption
- Logging
- Alerting
- Malware and Ransomware detection and prevention.
API-based CASB deployment option has also several prominent advantages:
- quick time to value
- no internal politics
- certified by a cloud provider
- no end-user impact
And more importantly, API-based CASB can integrate directly with numerous cloud applications without requiring a gateway. This feature makes it well-suited for collaboration tools used by users in any location.
Shadow IT Risk Assessment
Unsanctioned cloud applications increasing cyber risks: Shadow IT is not always about users accessing the risky cloud applications. Instead, business departments very often adopt cloud apps for legitimate reasons but neglect to let the IT and security team members know. Thus, getting visibility is a primary data protection requirement.
As the “big” CSP vendors are slow to provide cloud access security mechanisms CASB is the solution that can help you extend your DLP policies to the cloud by:
- detecting and monitoring the constantly growing and changing cloud app use by personnel including third parties;
- controlling access to specific sanctioned cloud apps and preventing access to unsanctioned cloud apps;
- providing data protection to regulated data to support compliance requirements;
- protecting against cloud app vendors’ compromises and cloud malware threats.
CASBs can also provide compliance services by showing what data and where is being stored in the cloud.
In the next post, we will introduce you to Spinbackup’s API-based CASB and our cloud security expertise. Explore Spinbackup’s GDRP Compliance and stay tuned!
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...
Data Loss Prevention Techniques for 2025 and Beyond
It’s painstakingly clear that data loss is a major challenge facing businesses today. Our experts...
What is SaaS Security? Challenges & Best Practices
Businesses increasingly rely on Software as a Service (SaaS) for increased efficiency, collaborativeness, and scalability....


